The State of Stalkerware in 2023 (PDF)The annual Kaspersky State of Stalkerware repor 2024-3-13 16:0:40 Author: securelist.com(查看原文) 阅读量:19 收藏
The State of Stalkerware in 2023 (PDF)
The annual Kaspersky State of Stalkerware report aims to contribute to awareness and a better understanding of how people around the world are impacted by digital stalking. Stalkerware is commercially available software that can be discreetly installed on smartphone devices, enabling a perpetrator to monitor an individual’s private life without their knowledge. Stalkerware requires physical access to be installed, but our report also looks at a range of remote technology that can be used for nefarious purposes.
Once installed, stalkerware makes it possible to access the smartphone from anywhere. Not only can the intruder violate their victim’s privacy by monitoring their activities, but they can also use the software to access huge volumes of personal data. Depending on the software they use, they can monitor anything from device location to text messages, social media chats, photos, browser history and more. Since stalkerware works in the background unseen, most victims are completely unaware that their every step and action is being monitored.
In most countries around the world, use of stalkerware is currently not prohibited, but installing a surveillance application on another person’s smartphone without their consent is illegal and punishable. However, it is the perpetrator who will be held responsible, not the developer.
Along with other related technologies, stalkerware is one element in tech-enabled abuse and is often used in abusive relationships. As this is a digital aspect of a wider, real-world problem, Kaspersky is working with relevant experts and organizations in the field of domestic violence, ranging from victim support services and perpetrator programs through to research and government agencies, to share knowledge and support with professionals and victims alike.
About stalkerware
Stalkerware products are typically marketed as legitimate anti-theft or parental control apps for smartphones, tablets and computers, but in reality, they are something very different. Installed without the knowledge or consent of the person being tracked, these apps operate stealthily and provide a perpetrator with the means to gain control over a victim’s life. They do not typically appear on the list of installed apps in the phone’s configuration, which makes them hard to spot. Stalkerware capabilities vary depending on the application, and whether they have been paid for or downloaded for free.
Below are some of the most common functions found in stalkerware:
- Hiding the app icon
- Reading SMS, MMS and call logs
- Getting lists of contacts
- Tracking geolocation
- Tracking calendar events
- Reading messages from popular instant messaging services and social networks, such as Facebook, WhatsApp, Signal, Telegram, Viber, Instagram, Skype, Google Chat, Line, Kik, WeChat, Tinder, IMO, Gmail, Tango, SnapChat, Hike, TikTok, Kwai, Badoo, BBM, TextMe, Tumblr, Weico, Reddit and others.
- Viewing photos and pictures from phones’ image galleries
- Taking screenshots
- Taking pictures with the front-facing (selfie) camera
Are Android OS and iOS devices equally affected by stalkerware?
Not unlike malware, stalkerware apps are much less frequent on iPhones than on Android devices due to the proprietary and closed nature of iOS. To install such an app and give it enough permissions to monitor the victim’s activities, the perpetrator needs to “jailbreak” the iPhone, which is not that simple and requires direct physical access to the device. Nevertheless, iPhone users fearing surveillance should always keep a close eye on their device. The abuser may also jailbreak a new iPhone to install stalkerware and then give it to the victim.
The data highlights of 2023
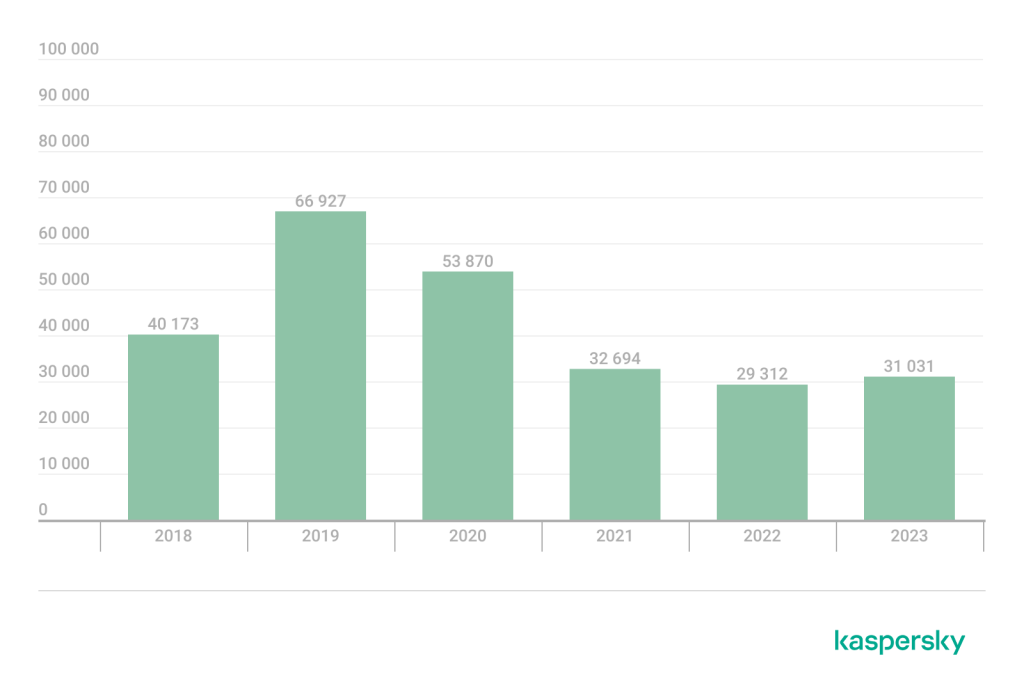
- In 2023, a total of 31,031 unique users were affected by stalkerware, an increase on 2022 (29,312).
- The Kaspersky Security Network revealed that stalkerware was most commonly used in Russia, Brazil and India, and continued to be a global issue, with the largest number of affected users found in the following countries:
- Germany, France and the United Kingdom (Europe)
- Iran, Turkey and Yemen (Middle East and Africa)
- India, Indonesia and Philippines (Asia-Pacific)
- Brazil, Mexico and Colombia (Latin America)
- United States (North America)
- Russian Federation, Belarus and Kazakhstan (Eastern Europe excluding European Union countries, Russia and Central Asia)
- Globally, the most popular stalkerware app was TrackView with 4,049 affected users.
- Twenty-three percent of people worldwide said they had encountered some form of online stalking from someone they had recently started dating.
The trends of 2023 observed by Kaspersky
Methodology
The data in this report was taken from aggregated threat statistics obtained from the Kaspersky Security Network, which is dedicated to processing cybersecurity-related data streams from millions of anonymous volunteer participants around the world. To calculate the statistics, data from the consumer line of Kaspersky’s mobile security solutions was reviewed according to the Coalition Against Stalkerware detection criteria. This means that the affected number of users were targeted by stalkerware only. Other types of monitoring or spyware apps that fall outside of the Coalition’s definition are not included in the statistics found here.
The statistics reflect unique mobile users affected by stalkerware, which is different from the total number of detections. The number of detections can be higher as stalkerware may have been detected several times on the same device belonging to the same unique user if they decided not to remove the app upon receiving a notification. Support organizations often recommend that victims refrain from removing the stalkerware, so as not to alert the perpetrator.
Finally, the statistics reflect only mobile users of Kaspersky’s security solutions. Some users may have another cybersecurity solution installed on their devices, while others have none.
Global detection figures: affected users
Using global and regional statistics, Kaspersky has been able to compare data collected in 2023 with the previous four years. In 2023, a total of 31,031 unique users were affected by stalkerware, an increase compared to 2022 (29,312 unique users). Diagram 1 below shows how this number varied year to year starting in 2018.
Global and regional detection figures: geography of affected users
Stalkerware continued to be a global problem. In 2023, Kaspersky detected affected users in 175 countries.
In 2023, Russia (9,890), Brazil (4,186) and India (2,492) were the top three countries with the most affected users. According to Kaspersky statistics, those three countries had held leading positions since 2019, all with an increase in detected stalkerware infections. Iran entered the top five most affected in the previous year and remains there.
When compared to 2021, there were slight changes to the top 10 affected countries, with most remaining in the same position. While Germany had dropped from seventh to 10th place, Saudi Arabia (ranked eighth in 2022) was not among the most affected countries in 2023.
| Country | Affected users | |
| 1 | Russian Federation | 9,890 |
| 2 | Brazil | 4,186 |
| 3 | India | 2,492 |
| 4 | Iran | 1,578 |
| 5 | Turkey | 1,063 |
| 6 | Indonesia | 871 |
| 7 | United States of America | 799 |
| 8 | Yemen | 624 |
| 9 | Mexico | 592 |
| 10 | Germany | 577 |
Table 1. TOP 10 countries most affected by stalkerware in 2023
The total number of unique affected European users in 2023 was 2,645, a significant decrease compared to 2022 (3,158). The three most affected countries in Europe were Germany (577), France (332) and the United Kingdom (271). Compared to 2021, the countries listed continued to feature as the most affected in Europe except for Greece, which dropped out of the rankings. Unfortunately, Portugal entered the list ranked tenth.
| Country | Affected users | |
| 1 | Germany | 577 |
| 2 | France | 332 |
| 3 | United Kingdom | 271 |
| 4 | Spain | 257 |
| 5 | Italy | 252 |
| 6 | Poland | 179 |
| 7 | Netherlands | 177 |
| 8 | Switzerland | 116 |
| 9 | Austria | 70 |
| 10 | Portugal | 63 |
Table 2. TOP 10 countries most affected by stalkerware in Europe in 2023
In Eastern Europe (excluding European Union countries), the Russian Federation and Central Asia, the total number of unique affected users in 2023 was 11,210, an increase on the previous year (9,406). The top three countries were Russia, Kazakhstan and Belarus.
| Country | Affected users | |
| 1 | Russian Federation | 9,890 |
| 2 | Belarus | 307 |
| 3 | Kazakhstan | 270 |
| 4 | Ukraine | 268 |
| 5 | Azerbaijan | 243 |
| 6 | Uzbekistan | 100 |
| 7 | Kyrgyzstan | 52 |
| 8 | Moldova | 49 |
| 9 | Armenia | 43 |
| 10 | Tajikistan | 30 |
Table 3. TOP 10 countries most affected by stalkerware in Eastern Europe (excluding EU countries), Russia and Central Asia in 2023
Looking at the Middle East and Africa region, the total number of affected users was 6,561, slightly higher than in 2022 (6,330), but there was a minor change in the top three most affected this year. While in 2022, Iran, Turkey and Saudi Arabia were the most affected countries, it was Iran, Turkey and Yemen in 2023.
| Country | Affected users | |
| 1 | Iran | 1,578 |
| 2 | Turkey | 1,063 |
| 3 | Yemen | 624 |
| 4 | Egypt | 569 |
| 5 | Saudi Arabia | 511 |
| 6 | Algeria | 495 |
| 7 | Morocco | 215 |
| 8 | United Arab Emirates | 184 |
| 9 | Iraq | 127 |
| 10 | South Africa | 126 |
Table 4. TOP 10 countries most affected by stalkerware in the Middle East and Africa in 2023
The Asia-Pacific region saw an increase in the use of stalkerware compared to the previous year, with a total of 4,575 affected users, up from 3,187 in 2022. India remained far ahead of other countries in the region, with 2,492 affected users. Indonesia occupied second place with 871 affected users; the Philippines was third with 323 affected users and Australia, fourth.
| Country/territory | Affected users | |
| 1 | India | 2,492 |
| 2 | Indonesia | 871 |
| 3 | Philippines | 323 |
| 4 | Australia | 168 |
| 5 | Vietnam | 97 |
| 6 | Malaysia | 88 |
| 7 | Japan | 85 |
| 8 | Bangladesh | 66 |
| 9 | Hong Kong | 51 |
| 10 | Sri Lanka | 51 |
Table 5. TOP 10 countries/territories most affected by stalkerware in the Asia-Pacific region in 2023
Brazil dominated the Latin America and the Caribbean region with 4,186 affected users, accounting for approximately 76 percent of the region’s total number of affected users. Brazil was followed by Mexico and Colombia. A total of 5,478 of affected users were recorded in the region, which was a minor decrease compared to 2022 (6,170).
| Country | Affected users | |
| 1 | Brazil | 4,186 |
| 2 | Mexico | 592 |
| 3 | Colombia | 149 |
| 4 | Peru | 138 |
| 5 | Argentina | 95 |
| 6 | Ecuador | 88 |
| 7 | Chile | 63 |
| 8 | Venezuela | 19 |
| 9 | Bolivia | 18 |
| 10 | Paraguay | 17 |
Table 6. TOP 10 countries most affected by stalkerware in Latin America in 2023
Finally, in North America, 77 percent of all affected users were in the United States. This is to be expected given the relative size of the population when compared to Canada. Across the North American region, 1,049 users were affected in total.
| Country | Affected users | |
| 1 | United States of America | 799 |
| 2 | Canada | 250 |
Table 7. Number of users affected by stalkerware in North America in 2023
Global detection figures – stalkerware applications
In 2023, Kaspersky detected 195 different stalkerware apps. The most commonly used stalkerware application to control smartphones around the world was TrackView, which affected 4,049 users.
| Application name | Affected users | |
| 1 | TrackView | 4,049 |
| 2 | Reptilic | 3,089 |
| 3 | SpyPhone | 2,126 |
| 4 | MobileTracker | 2,099 |
| 5 | Cerberus | 1,816 |
| 6 | Wspy | 1,254 |
| 7 | Unisafe | 981 |
| 8 | Mspy | 899 |
| 9 | MonitorMinor | 863 |
| 10 | KeyLog | 852 |
Table 8. TOP 10 stalkerware applications in 2023
Digital stalking, trust and dating
Stalkerware and digital stalking are related but not mutually exclusive. We have noted a rise in the use of legitimate technology and apps for illegitimate or nefarious purposes to track and monitor partners in recent years. To get further insights into the broader topic of digital stalking, Kaspersky commissioned Arlington Research to conduct 21,000 online interviews to get insights into digital stalking and stalkerware worldwide. The marketing research company questioned 1,000 people in each of the following countries: the UK, Germany, Spain, Serbia, Portugal, The Netherlands, Italy, France, Greece, The USA, Brazil, Argentina, Chile, Peru, Colombia, Mexico, China, Singapore, Russia, India and Malaysia. Respondents were aged 16 years and over and were either in a long-term relationship (62 percent), dating someone (16 percent) or not dating / in a relationship at the time but had been in the past (21 percent). The fieldwork took place from January 3–17, 2024.
Overview on stalking and being stalked
Twenty-three percent of respondents revealed they had encountered some form of online stalking from someone they had recently started dating. When describing their online stalking experiences, 16 percent said they had received unwanted emails or messages, 10 percent acknowledged having had their location tracked, another 10 percent had experienced unauthorized access to their social media accounts or email, and seven percent have had had stalkerware surreptitiously installed on their devices. This disconcerting scenario extended globally, with higher occurrences of online stalking reported in parts of South and Central America, and Asia. For instance, 42 percent of respondents in India, 38 percent in Mexico, and 36 percent in Argentina acknowledged having experienced some form of online stalking.
Speaking of technologies the perpetrators used, stalking through a phone app was the most prevalent (20 percent), followed by a laptop app (10 percent) and access via the webcam (10 percent). While a majority of respondents (78 percent) had never faced pressure from a partner to install monitoring apps or use special phone settings, 13 percent reported having had a partner install an app or modify settings (similar to 14 percent in 2021), and 10 percent felt pressured into installing a monitoring app (15 percent in 2021). Meanwhile, 12 percent of respondents admitted to having installed stalkerware or modified settings on a partner’s phone, and nine percent acknowledged having pressured a partner to install monitoring apps.
Awareness of stalkerware varied, with 46 percent having no knowledge, 17 percent being unsure, and only 37 percent feeling confident about knowing what stalkerware was. Among those expressing confidence, less than 10 percent could identify all the surveillance capabilities. Notably, in 2021, the levels of awareness were higher, with 40 percent knowing about stalkerware and 19 percent unsure.
Shifting perspectives on stalking in modern relationships: privacy, consent, and the reality of stalking
Most individuals (54 percent) did not endorse the idea of monitoring a partner without their knowledge, signaling a prevailing disapproval of such actions. However, the period between 2021 and 2024 saw a notable decrease by 16 p.p. from 70 percent. Interestingly, those endorsing the viewpoint that monitoring was always acceptable also had decreased, to eight percent in 2024 from 13 percent in 2021. The nuanced perspective on this matter was evident in the fact that 38 percent in 2024 found secret monitoring acceptable under certain circumstances, a substantial rise from the 17 percent reported in 2021.
When asked about their attitude toward consensual monitoring of a partner’s online activities (where the partner shared information with full knowledge and consent for a purpose such as safety), 45 percent of respondents expressed the belief that it was not acceptable, emphasizing the importance of privacy rights. Meanwhile, 27 percent advocated for full transparency in relationships, deeming consensual monitoring appropriate, and 12 percent found it acceptable only when mutual. Additionally, 12 percent concurred with such monitoring when it concerned physical safety, while four percent reluctantly agreed to it due to a partner’s insistence.
Navigating trust and boundaries: A deep dive into digital privacy issues
Half of the respondents (51 percent) expressed trust in their partners by granting them full access to their phones. Another 19 percent permitted access but with certain apps protected by additional passwords or security measures. One-fifth, while trusting their partners, opted not to provide access to their phones, five percent did not trust their partners enough to grant them access, and four percent chose not to answer. Individuals in ongoing relationships exhibited more hesitancy, with 40 percent agreeing to grant full access compared to 61 percent among those in long-term relationships.
On the flip side, 52 percent of respondents enjoyed full access to their partners’ phones, while an additional 23 percent had access but with specific apps shielded by additional passwords or security measures. Conversely, 18 percent reported not being granted access to their partners’ phones, and seven percent preferred not to disclose that information.
Insights into the complex landscape of information sharing in relationships
While a significant majority (more than 90 percent) of respondents, expressed willingness to share or consider sharing passwords for streaming services like Netflix and their photos, a more cautious approach emerged when it came to certain types of sensitive information. Interestingly, respondents exhibited heightened reluctance to share passwords for security devices, with 18 percent firmly stating they would never share access to these. Similarly, payment information was the type of data 21 percent said they would not share. Among other information respondents were most reluctant to share with partners were accounts, such as iCloud, Amazon and Google (47 percent willing, 29 percent admitting they might consider, and 24 percent unwilling) and browser history (46 percent willing, 34 percent admitting they might consider, and 20 percent unwilling).
Combatting stalkerware together
Stalkerware is not just a sort of software you do not want installed on your devices. It indicates a complex problem, which requires action from all sections of society. Kaspersky not only develops technologies to protect users from this threat but also stays in contact with non-profit organizations, industry, research and public agencies around the world to tackle the issue together.
In 2019, Kaspersky was the first-ever cybersecurity company to develop a new attention-grabbing alert that clearly notified users if stalkerware was found on their device. In 2022, as part of Kaspersky’s launch of a new consumer product portfolio, the Privacy Alert was expanded. Apart from informing the user about the presence of stalkerware on the device, it now warns them that, if stalkerware is removed, the person who installed the app will most likely be alerted. Moreover, by deleting the app, the user risks getting rid of important evidence that could be used for prosecution.
In 2019, Kaspersky also co-founded the Coalition Against Stalkerware, an international working group that brings together private IT companies, NGOs, research institutions and law enforcement agencies to stand against cyberstalking and online abuse. Over 40 organizations contribute to the Coalition, its website available in seven different languages. On this website, a person suspecting that stalkerware is installed on their devices can find help and guidance.
In 2020, Kaspersky developed an open-source tool called TinyCheck and capable of detecting stalkerware on user devices without alerting the perpetrator. In June 2022, Kaspersky launched a website dedicated to this tool. TinyCheck is available for free and can be used by non-profit organizations and police units to help with supporting victims of digital stalking. It runs on a separate device the perpetrator does not have access to, scans outgoing traffic on the user’s device via a regular Wi-Fi connection and identifies interactions with known sources related to stalkerware. Being device independent, it can check for stalkerware on any platform including iOS, Android or any other.
From 2021–2023, Kaspersky was a consortium partner of the EU project DeStalk, co-funded by the Rights, Equality and Citizenship Program of the European Union. The project trained professionals directly involved in women’s support services and perpetrator programs, and public authority representatives on how to combat digital means of gender-based violence including stalkerware. It also aimed at raising general public awareness on this topic.
As part of DeStalk, Kaspersky developed an e-learning course on cyberviolence and stalkerware within its Kaspersky Automated Security Awareness Platform. Although the project has ended, e-learning is still available on its website.
Think you are a victim of stalkerware? Here are a few tips…
Whether you are a victim of stalkerware or not, these tips can help you to better protect yourself:
- Protect your phone with a strong unique password and do not share it with anyone including your partner or other people you trust.
- Do not share your online account passwords with anyone.
- Only download apps from official sources, such as Google Play or the Apple App Store.
- Install a reliable IT security solution like Kaspersky for Android on your devices and scan them regularly. Note: if you suspect that stalkerware may have already been installed on your device, do not install any new security solutions or perform a scan until you have carefully assessed what risks you will face if the app notifies the abuser.
- Reach out to a local support organization: the Coalition Against Stalkerware website can help you to find one.
- Keep an eye out for warning signs. These can include a fast-draining battery, high data usage, newly installed applications with suspicious access to using and tracking your location, sending or receiving text messages, and so on. Also, check if app installation from unknown sources is enabled on the device – this may indicate that unwanted software has been installed from a third-party source. Note that all these warning signs are circumstantial and do not indicate the unequivocal presence of stalkerware on the device.
- Do not try to erase the stalkerware, change any settings or tamper with your phone prior to developing a safety plan. The app may alert the perpetrator, which can lead to an escalation and further aggression. Removing stalkerware also means getting rid of important evidence that could be used for prosecution. Instead, take steps to determine what course of action makes the most sense and is the safest in your current situation.
For more information about our activities on stalkerware or any other request, please write to us at: [email protected].
如有侵权请联系:admin#unsafe.sh