The way businesses operate has changed more in the past forty-eight months than any other fo 2024-3-5 20:53:18 Author: www.forcepoint.com(查看原文) 阅读量:11 收藏
The way businesses operate has changed more in the past forty-eight months than any other four-year period. First, people and data fled the traditional office for home and cloud. Now, people are making their way back (sometimes), but data isn’t. Rather than returning to the way things were before the pandemic, businesses and government agencies are forging a new path in which people are working anywhere with data that’s everywhere. Our mission at Forcepoint is to help simplify their journey through what we call Data Security Everywhere.
There are plenty of cliches about the role data plays in an increasingly digital economy. But there’s no denying to remain competitive, businesses need people to be able to use sensitive data from more places, at more times, and from more devices than ever before. But the explosion of data—in volume and spread—that modern businesses are dealing with is creating new challenges. How do you accurately know what data you have, where it is, who has access, and how they’re able to manipulate it?
In addition, while the motivations for protecting different types of sensitive data vary (theft of intellectual property is a competitive issue whereas breaches of regulated data like PHI and PII triggers compliance mandates), all types of loss are rapidly becoming board-level, existential threats.
Keeping track of data and controlling how it was used was hard enough back when everything was “inside the building.” Now, with more data than ever in the cloud, on the web, and in remote traditional data centers far from where people are working, networks have become key to how sensitive data is accessed. As a result, data security and network security are becoming intertwined. Success depends upon having consistent policies for both, combined with new technologies for automating how the right policies are selected and enforced in any given situation. We call this a “Data-first” approach to security:
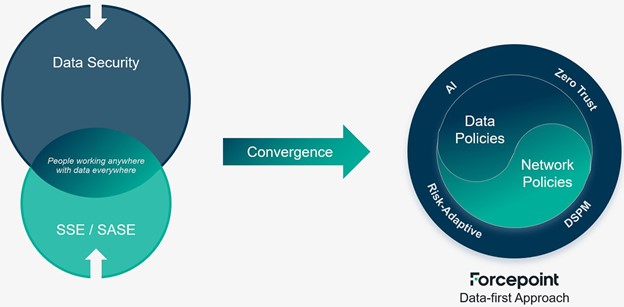
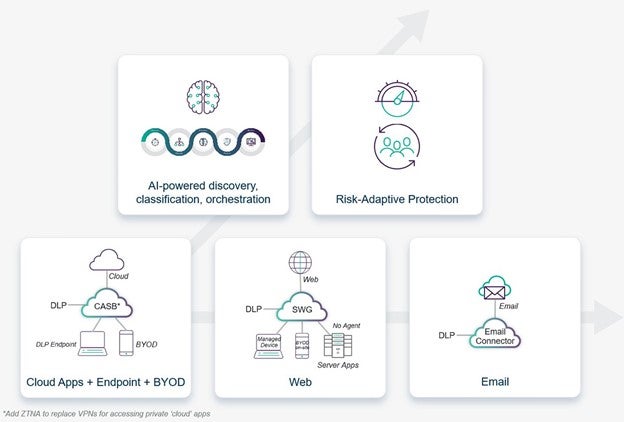
This forms the heart of our Data-first SASE platform, Forcepoint ONE, enabling us to deliver data security consistently across many channels—from cloud apps and the web, to laptops, BYOD, and even email.

The real power in this approach is that it enables organizations to use the platform incrementally tackling immediate challenges now in a way that can be easily extended. To help businesses and government agencies choose their own path in empowering their people to safely use data anywhere, we’ve created a set of guidelines that we call 5 Steps to Data Security Everywhere. They reflect the most common ways that the thousands of organizations we work with around the globe every day are putting Data Security Everywhere into practice.

There’s no set order, but we’ve found many organizations tend to start with having a single set of policies to protect data consistently in cloud apps and on endpoint devices, freeing them from the cost and complexity of running multiple data security systems (which recent research has found can save up to 31%). Then, the same policies can be easily applied over other channels of communication, like the web or email. Or, advanced automation technologies such as AI or our pioneering Risk-Adaptive Protection can be added to further improve productivity, cut costs, reduce risk, and streamline compliance.
Over the coming weeks, we’ll be diving into each of these 5 Steps to Data Security Everywhere, showing examples of how this modern approach makes data security practical. See you then.

Jim Fulton
Jim Fulton serves as VP Product Marketing & Analyst Relations, focused on SASE, SSE and Zero Trust data security. He has been delivering enterprise access and security products for more than 20 years and holds a degree in Computer Science from MIT.
如有侵权请联系:admin#unsafe.sh