2024-3-5 07:0:21 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
A recent successful cyberattack on a large technology provider for hospitals and pharmacies in the US has left patients unable to obtain their medication. This attack is a reminder that healthcare cyberattacks are not stopping, and a successful attack will have severe consequences.
In this blog, we’ll briefly analyze the motivations and reasons behind cybercriminal groups attacking this sector, and share what immediate countermeasures and actions LogRhythm customers can take to prevent similar incidents.
Why Do Threat Actors Attack Healthcare?
Healthcare is a critical function, dealing with the life and death of the people. Not only that, healthcare providers are often privy to extremely sensitive and personal information of the patients. This combination makes healthcare a lucrative target for cybercriminals, as the likelihood of receiving the ransom is higher.
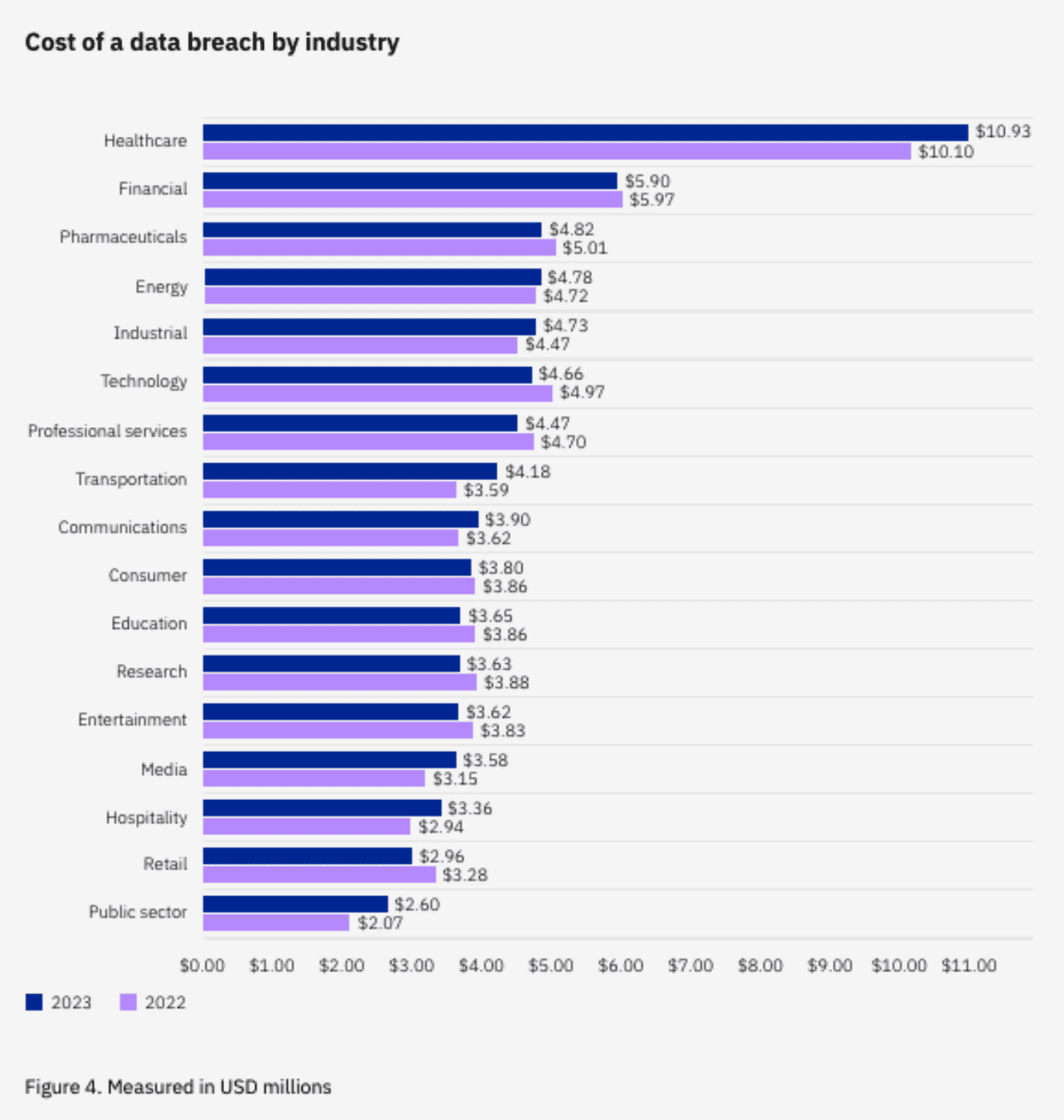
Cost of Data Breach in Healthcare
HC3, Health Sector Cybersecurity Coordination Center recently published a report on February, 15, 2024 where they shared, among other findings, cost of data breach by each industry. Based on the report, the healthcare industry experiences the highest data breach costs of all industries, increasing 8.2% from $10.10 million in 2022 to $10.93 million in 2023.
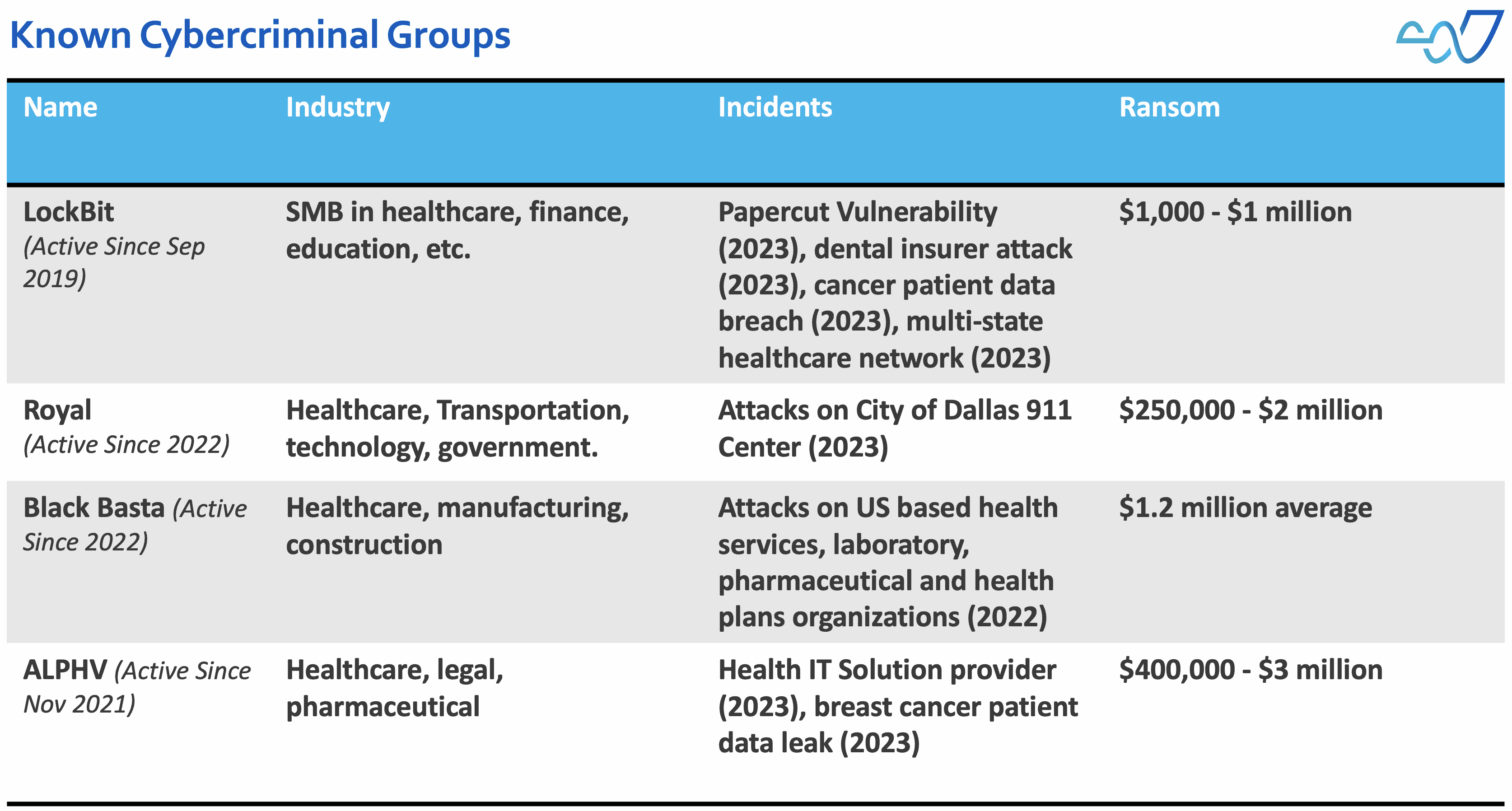
Cybercriminal Groups Attacking Healthcare
Ransomware aside, data exfiltration is also a threat faced by the healthcare sector; Groups like APT28 and APT29 regularly target pharmaceutical companies and clinical researchers to gain access to intellectual property and research data.
Based on a recent HC3 debrief, here are the list of groups currently actively targeting the healthcare sector.
Sample Ransomware Detection Techniques
Using ALPHV Blackcat as an example, we can use the IoCs associated to the group and configure the LogRhythm SIEM to detect potential attacks.
Credential Access TTPs:
ALPHV/Blackcat affiliates obtain passwords from local networks, deleted servers, and domain controllers using following techniques. The LogRhythm MITRE ATT&CK Module has out of box rules that can be enabled to detect these TTPs.
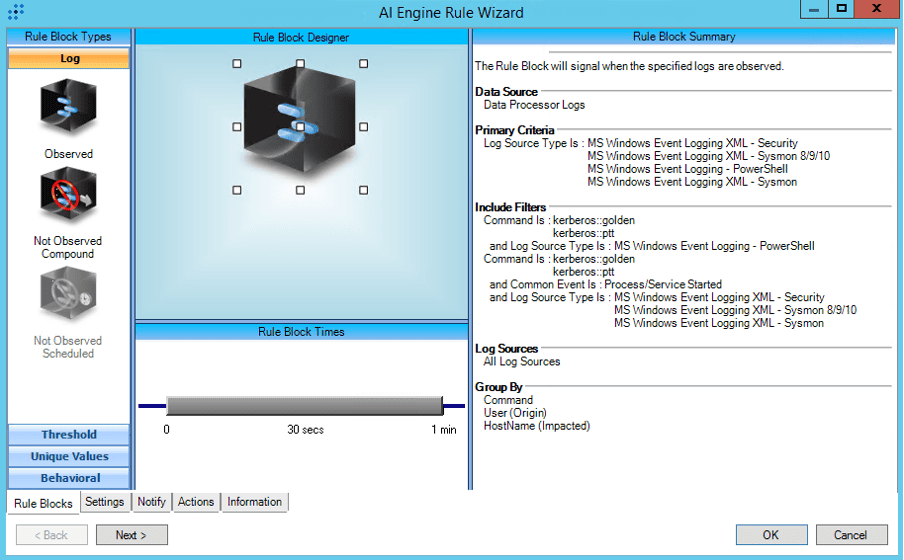
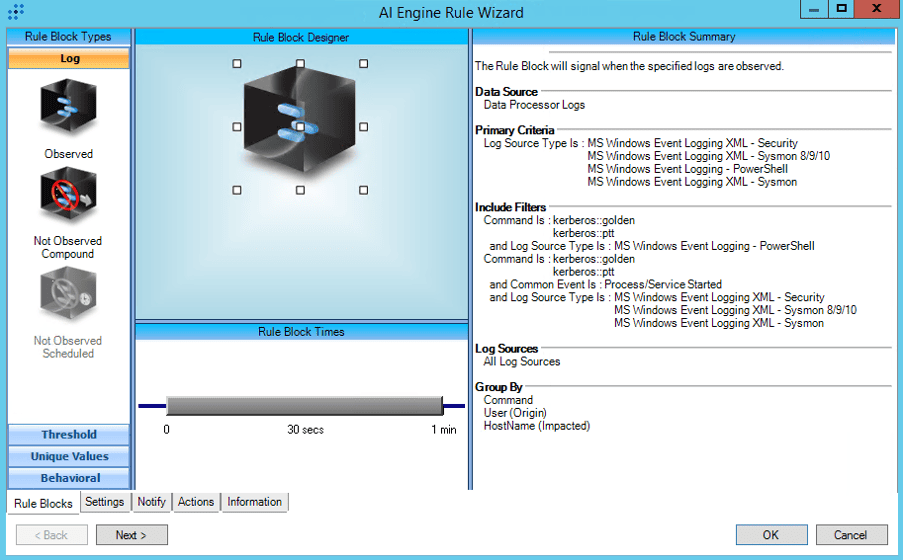
T1558.003:Kerberoasting:TGS Requests for Multiple Services
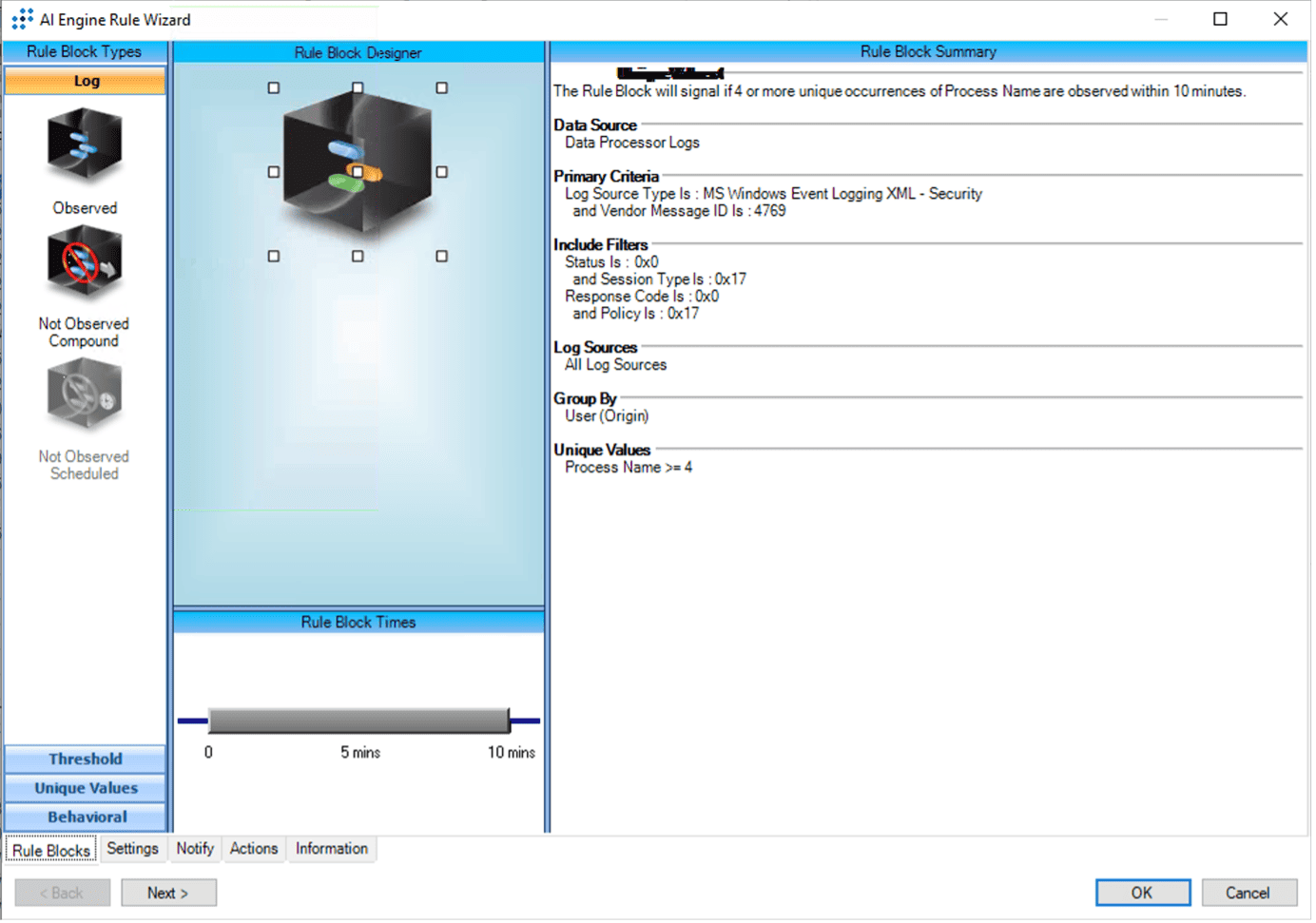
Detecting Ransomware Groups
MITRE provides excellent framework that allows defenders to understand and place detection for various TTPs (Tactics, Techniques and Procedures) used by threat actors. However, some of these TTPs are different between ransomware groups, hence we need a comprehensive approach to fortify our defenses against all of these groups. LogRhythm has released the MITRE ATT&CK® Ransomware Module (v1.0.2), a subset of the MITRE ATT&CK® Module focused on techniques associated with ransomware attacks. The list of techniques included in the module are most frequently used by ransomware groups.
Detect threats in Internet of Medical Things (IoMT):
In an effort to assist healthcare organizations in actively identifying and mitigating cyber risks within their unique Internet of Things (IoT) and the Internet of Medical Things (IoMT) environments, the LogRhythm Healthcare (OT) Module can help alerting on events such as:
- Critical system shutdowns
- Door authentications
- Medical Device firmware Changes
- Medical Device configuration changes
- Known device software vulnerabilities
- Default/weak device passwords
- New hardware and medical device detections,
- Device software installations/updates, and many more
In addition, a web console dashboard, designed around monitoring systems, medical devices, and physical access resources is available, and a report is provided to summarize AI Engine rule alarm activity.
READ MORE: Learn how to detect compromised X-Ray and CT Scan files on our blog here.
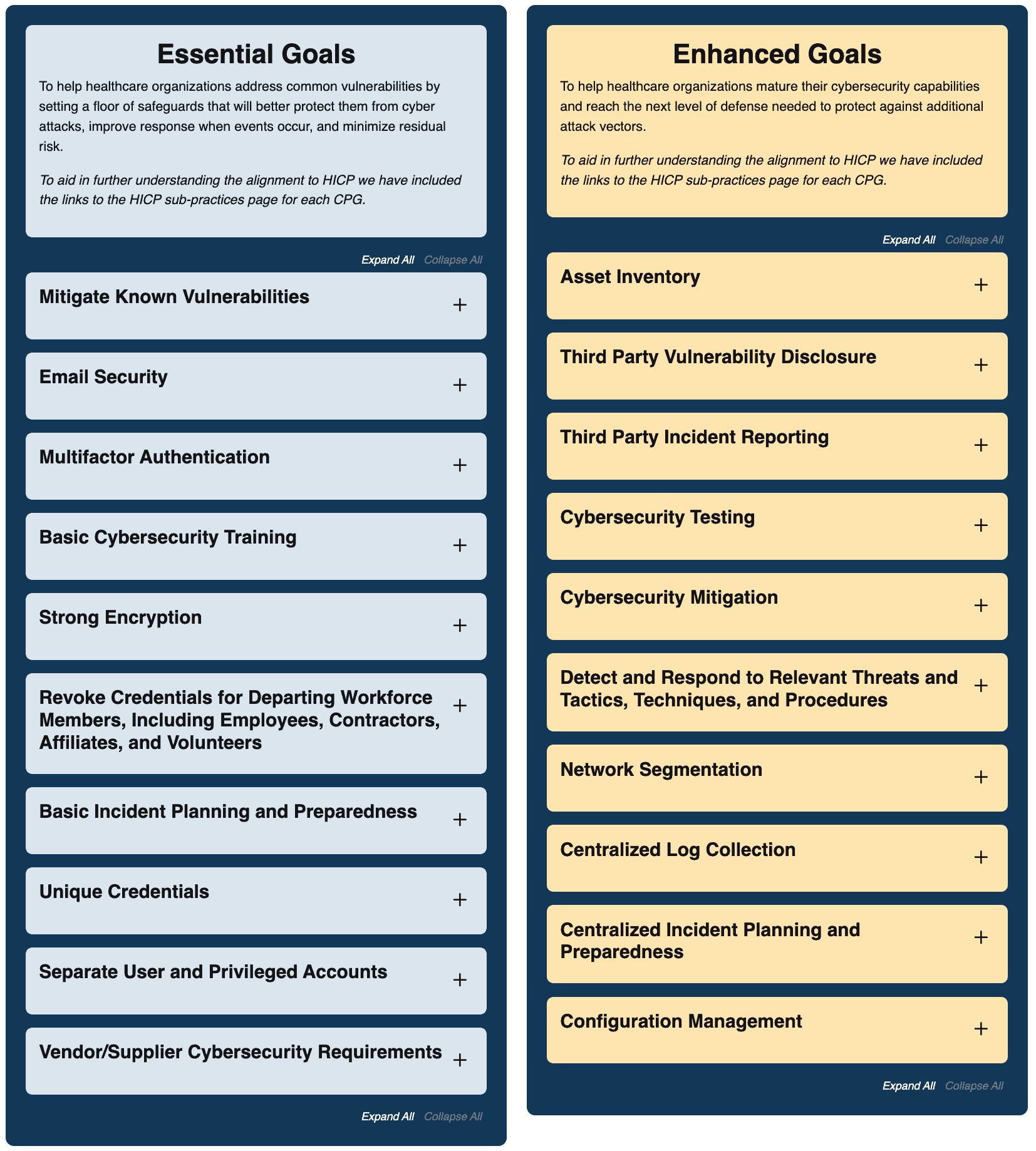
Cybersecurity Performance Goals
To better guide the healthcare sector, the US Department of Health and Human Services has published an easy-to-follow tool called the CPG (Cybersecurity Performance Goals). These CPGs are ‘Essential’ and ‘Enhanced’ categories, and the idea is to implement technologies and solutions in both categories to lower risks of successful cyberattacks faced by the industry. In addition, each goal maps back to NIST, HICP and CISA controls. We recommend CISOs in industry to leverage this tool to benchmark their environments and find gaps.
Given the lucrative nature of healthcare cyberattacks, we can expect attacks to become more frequent and advanced. Healthcare organizations must continue to stay ahead by placing proactive measures to safeguard their intellectual property and patient data from falling into the hands of the cybercriminals.
The post Prevention & Cure: Countermeasures Against Healthcare Cyberattacks appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Nicholas Tan. Read the original post at: https://logrhythm.com/blog/countermeasures-against-healthcare-cyberattacks/
如有侵权请联系:admin#unsafe.sh