The Good | US Bans Sale Of Personal Data To China & OthersThe Biden administration this week took 2024-3-1 22:0:46 Author: www.sentinelone.com(查看原文) 阅读量:20 收藏
The Good | US Bans Sale Of Personal Data To China & Others
The Biden administration this week took steps to ban data brokers from trading personal information of U.S. citizens to nations on a list of ‘countries of concern’, currently expected to be China, Russia, Iran, North Korea, Cuba and Venezuela. The Executive Order to protect Americans’ sensitive personal data was issued on Wednesday.
The government says that hostile foreign powers are leveraging AI to weaponize sensitive data bought in bulk from commercial data brokers. The data is then used for surveillance, scams, blackmail and privacy violations. Authoritarian governments can make use of such data to target journalists, dissidents and political activists.
AG Merrick Garland said that the EO will allow the Justice Department to block countries that pose a threat to U.S. national security and prevent them from harvesting sensitive personal data such as personal health and financial data, biometrics and genomic data. However, critics say the EO doesn’t go far enough and fails to prevent other countries from harvesting the same data and exposing it to those in the prescribed list.
Yesterday, the Biden admin announced a new EO limiting data brokers’ bulk sale of personal data to "countries of concern." @peterswire and @SammSacks explain why the order may be counterproductive to its admirable goals. https://t.co/63RQIGOVQx
— Lawfare (@lawfare) February 29, 2024
The Justice Department says the EO is a ‘targeted national security measure’ aimed at blocking specific adversaries. The EO also allows the program to exempt certain categories of data from the transfer ban, “such as those ordinarily incident to financial services, in order to allow low-risk commercial activity to continue unimpeded”.
The exact scope of the regulations will be worked out in an ANPRM, which is open to public comment
The Bad | BlackCat is Back, LockBit Lingers On
Law enforcement action to take down ransomware operators looks to have taken a setback this week as authorities warn that BlackCat RaaS has embarked on a new campaign targeting the healthcare sector. Meanwhile, despite last week’s high-profile raid on LockBit, the gang appear to be still in business.
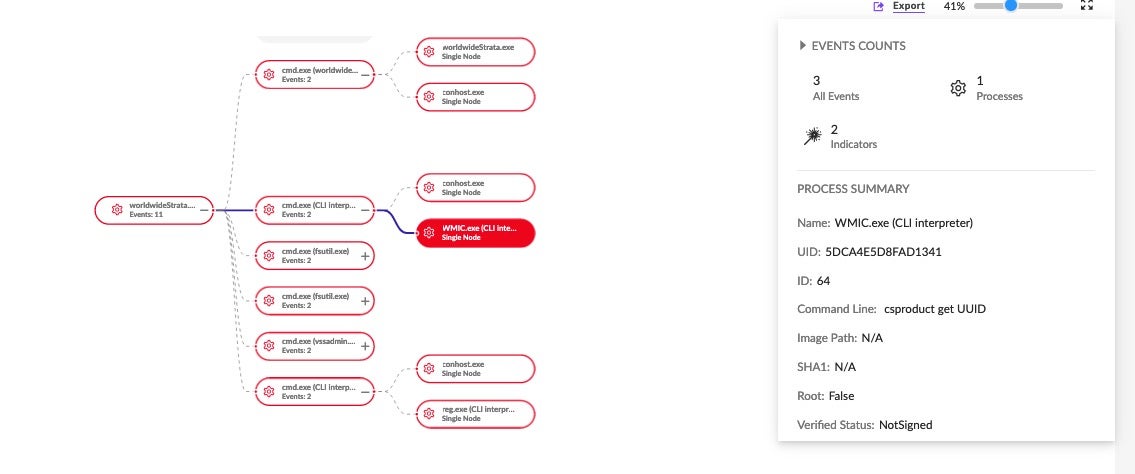
First appearing in November 2021, BlackCat has established itself as one of the most prolific ransomware threats today. The advisory describes how BlackCat (aka ALPHV) affiliates use advanced social engineering techniques to gain initial access. These include posing as helpdesk or IT and staff and using phone calls and smishing techniques to steal credentials from employees.
Once inside the target network, the threat actors use remote access software such as AnyDesk and Splashtop to facilitate data exfiltration. Dropbox and Mega have also been observed as vehicles to move or download victim data. CobaltStrike and Brute Ratel C4 are used to beacon out to the attackers C2.
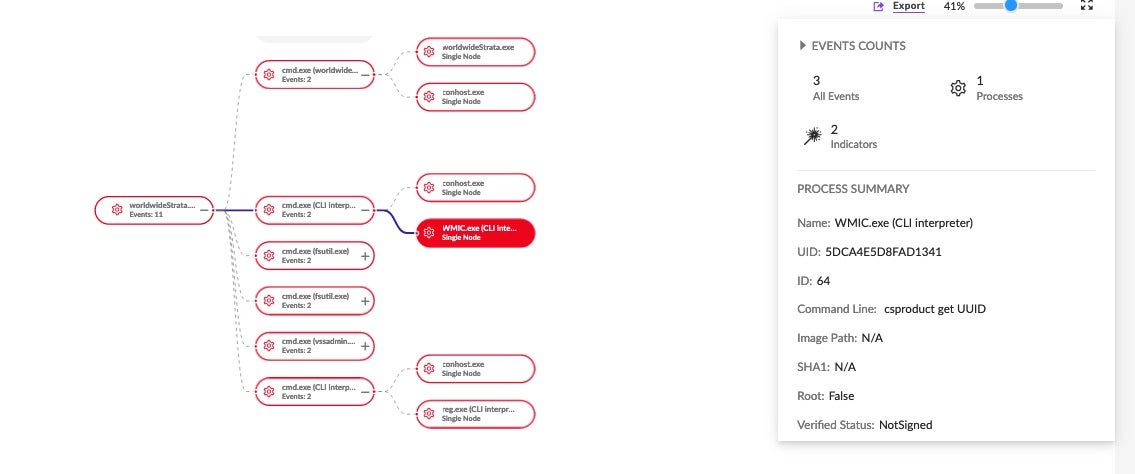
According to CISA, some affiliates extort victims solely through threats to expose stolen data, while others deploy ransomware to lock files and systems as well. In both cases, data is either deleted or destroyed unless the victims have backups or rollback systems in place.
In December, the Justice Department announced that it had severely disrupted BlackCat/ALPHV by seizing its infrastructure and releasing a decryptor; however, it appears the gang have been able to recover. Similarly, LockBit operators have this week responded to last week’s seizure of its infrastructure by publishing links to a new blog and data leak site and issuing a rambling rebuttal of claims that it was no longer operational.
The cat-and-mouse will inevitably continue; meanwhile, organizations can take proactive steps to exempt themselves from the cybercrime cycle by implementing recommended security controls.
The Ugly | APT29 Targeting Cloud for Initial Access
The advanced threat actor behind the SolarWinds breach among others, Russian intelligence agency SVR (aka APT 29, NobleBaron, The Dukes), is now targeting cloud services for initial access, the U.K.’s National Cyber Security Centre warned this week.
In a move that mirrors the wider enterprise trend away from on-prem servers in favor of cloud infrastructure, the Russian-backed threat actor has looked to supplement its traditional means of initial access such as exploiting software vulnerabilities with cloud-specific techniques and tactics.
The NCSC says these tactics include targeting service accounts with brute force and password spraying attacks. Service accounts with weak or default credentials are attractive since they cannot be protected with MFA as there is no human user to authenticate them. Dormant or inactive accounts, such as when an employee has left but the account has not been deactivated, have also been targeted.
Other tactics observed include stealing cloud-based authentication tokens. Once authenticated, these tokens remain valid for a period of time without needing further authentication. Once the SVR operators have gained initial access, they will frequently enroll new devices on the cloud tenant.
| Tactic | ID | Technique | Procedure |
| Credential Access | T1110 | Brute forcing | The SVR use password spraying and brute forcing as an initial infection vector. |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts | The SVR use compromised credentials to gain access to accounts for cloud services, including system and dormant accounts. |
| Credential Access | T1528 | Steal Application Access Token | The SVR use stolen access tokens to login to accounts without the need for passwords. |
| Credential Access | T1621 | Multi-Factor Authentication Request Generation | The SVR repeatedly push MFA requests to a victim’s device until the victim accepts the notification, providing SVR access to the account. |
| Command and Control | T1090.002 | Proxy: External Proxy | The SVR use open proxies in residential IP ranges to blend in with expected IP address pools in access logs. |
| Persistence | T1098.005 | Account Manipulation: Device Registration | The SVR attempt to register their own device on the cloud tenant after acquiring access to accounts. |
In light of these tactical changes, defenders are advised to ensure that MFA and 2SV (two-step verification) are used wherever possible; that token validity periods are set to a minimum, and that user and system accounts are regularly reviewed and dormant or inactive accounts removed. Further detailed mitigations are provided by NCSC here.
如有侵权请联系:admin#unsafe.sh