SearchSploit is a powerful command-line tool that is part of the NetHunter system, developed by 2024-2-27 19:2:14 Author: www.mobile-hacker.com(查看原文) 阅读量:19 收藏
![]()
SearchSploit is a powerful command-line tool that is part of the NetHunter system, developed by Offensive Security. It is designed to help security professionals and penetration testers search for known vulnerabilities in software by leveraging a comprehensive database of exploits called Exploit-DB.
Exploit database is a comprehensive and publicly accessible database of exploits, vulnerability information, and related tools. It serves as a valuable resource for security professionals, researchers, and penetration testers to find information about known vulnerabilities in various software and systems. The database holds over 45,000 exploits where over half of them is associated with common vulnerability exposure (CVE).
SearchSploit usage
For the first time, it is necessary to download the exploit database from Exploit Database which might take few minutes as visible on Figure 1.

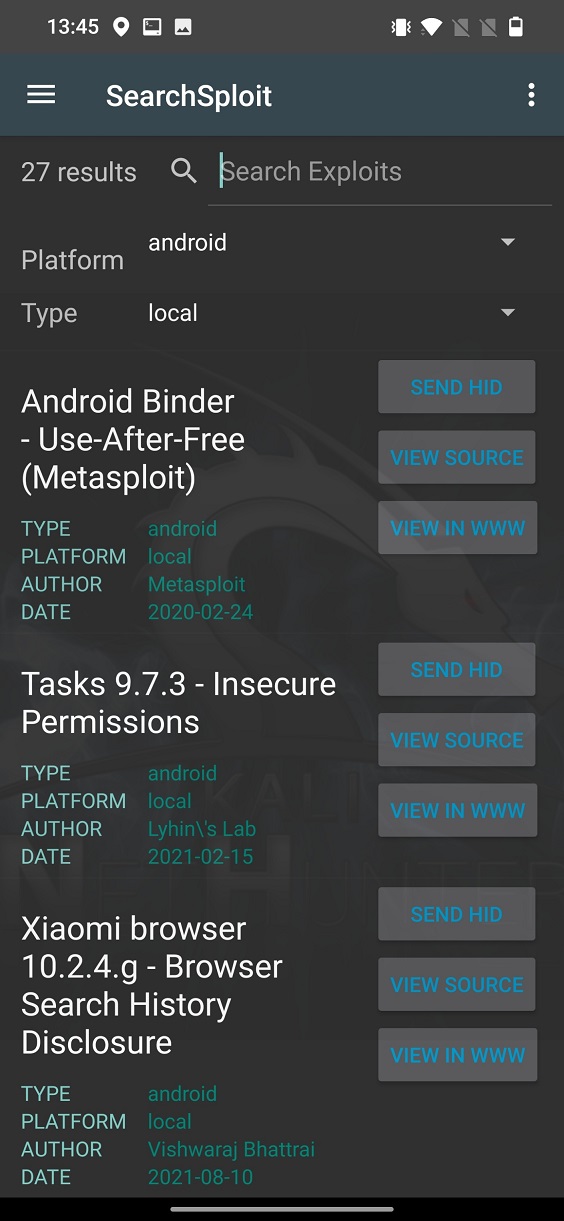
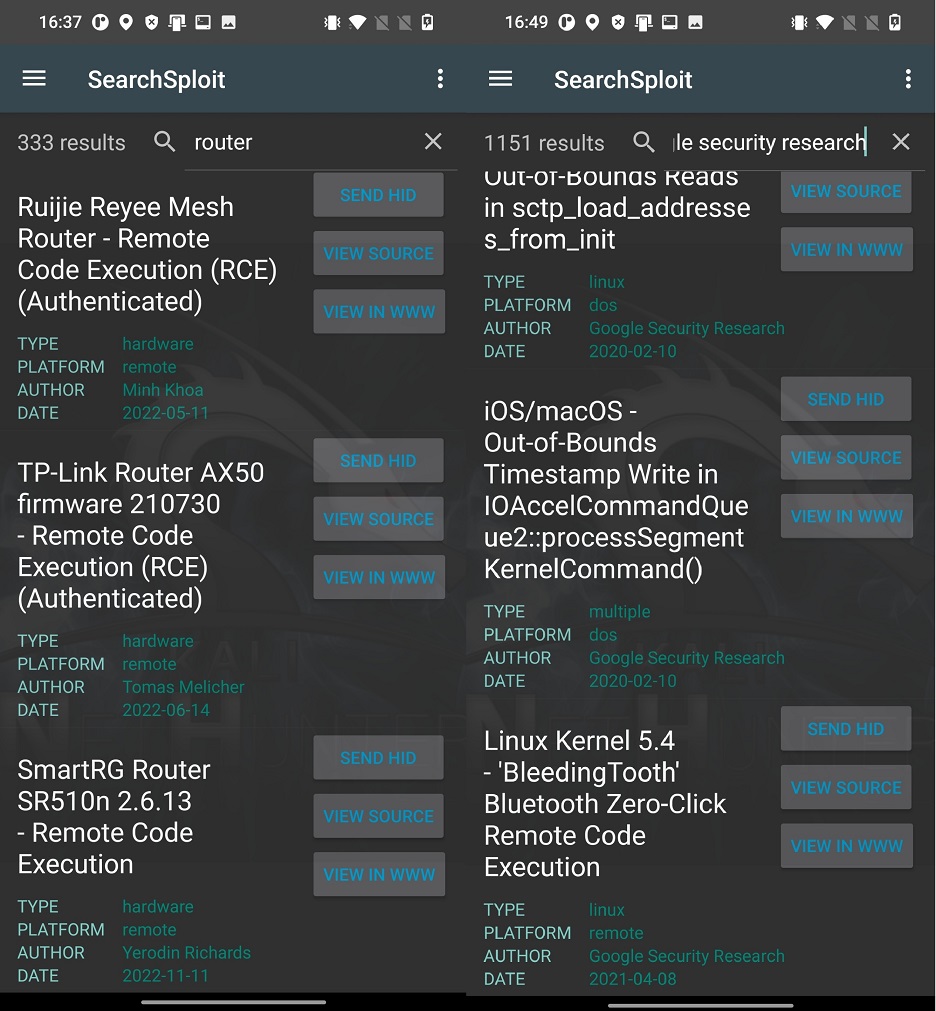
Once database if loaded, you can search exploits either using keywords in Search Exploits edit bar or simply by choosing Platform with exploit Type as displayed on Figure 2.
From Platform option you can pick from over 60 different targeted systems such as:
aix, alpha, android, arm, ashx, asp, aspx, atheos, beos, bsd, bsd_x86, cfm, cgi, freebsd, freebsd_x86, freebsd_x86-64, hardware, hp-ux, immunix, ios, irix, java, json, jsp, linux, linux_misp, linux_sparc, linux_x86, linux_x86-64, lua, macos, minix, multiple, netbsd_x86, netware, nodejs, novel, openbsd, osx, osx_ppc, palm_os, perl, php, plan9, python, qnx, ruby, sco, solaris, solaris_sparc, solaris_x86, tru64, ultrix, unix, unixware, vxworks, watchos, windows, windows_x86, windows_x86-64 and xml.
From exploit Type menu you can select one from four options such as:
dos, local, remote and webapps.
From listed exploits visible in Figure 2. you can see their title with the name of targeted system, author and date of exploit release. On the right side of each exploit are three buttons SEND HID, VIEW SOURCE and VIEW IN WWW. Each of them are responsible for different functionality, as describe below.
SEND HID should conveniently send exploit code as HID to USB connected device (computer) as text. Unfortunately, it doesn’t work. When I checked NetHunter’s app code on GitLab, it is responsible for executing command (su -c /data/data/com.offsec.nethunter/files/scripts/bootkali file2hid-file /usr/share/exploitdb/{path_to_exploit}) that converts input file, in this case our exploit, and print each line to hid device, which as result will be printed to text editor of connected PC. That is and easy way how to transfer exploit code from NetHunter to a computer.
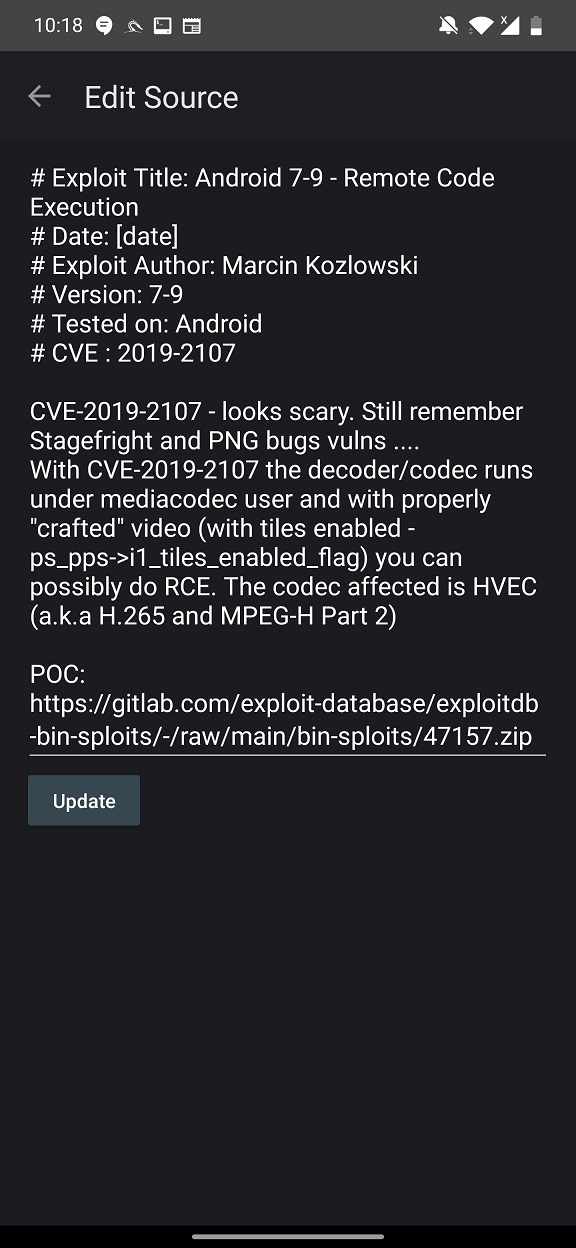
VIEW SOURCE displays exploit details, CVE, and path to download prove of concept exploit code as displayed in Figure 3.
VIEW IN WWW displays detailed information about the exploit in web browser from exploit-db.com where from you can copy the code.
Raw exploit search
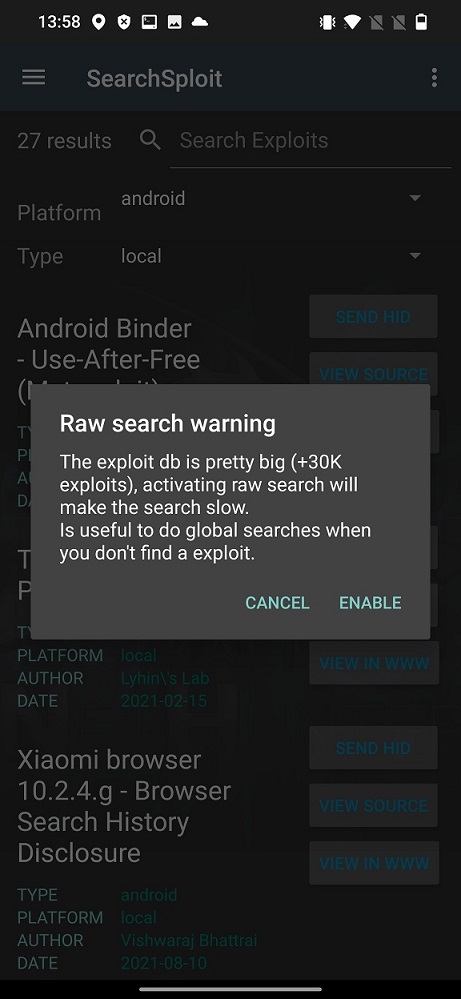
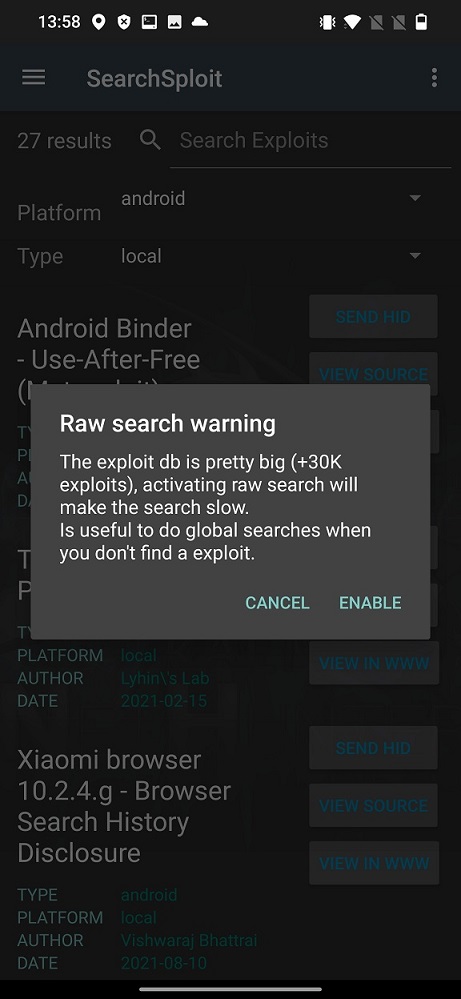
In top right cornet (three dots) your can enable raw database search. The warning pop up will follow to inform you that raw search will be slow as you can see on Figure 4. From my experience, raw database search wasn’t slow at all (OnePlus 7T).
The feature allows you to perform a more flexible and advanced search by directly specifying search parameters using regular expressions. This feature is particularly useful when you want to conduct more specific searches based on patterns or when they need to search for certain strings in description, type, platform and author as you can see in Figure 5.
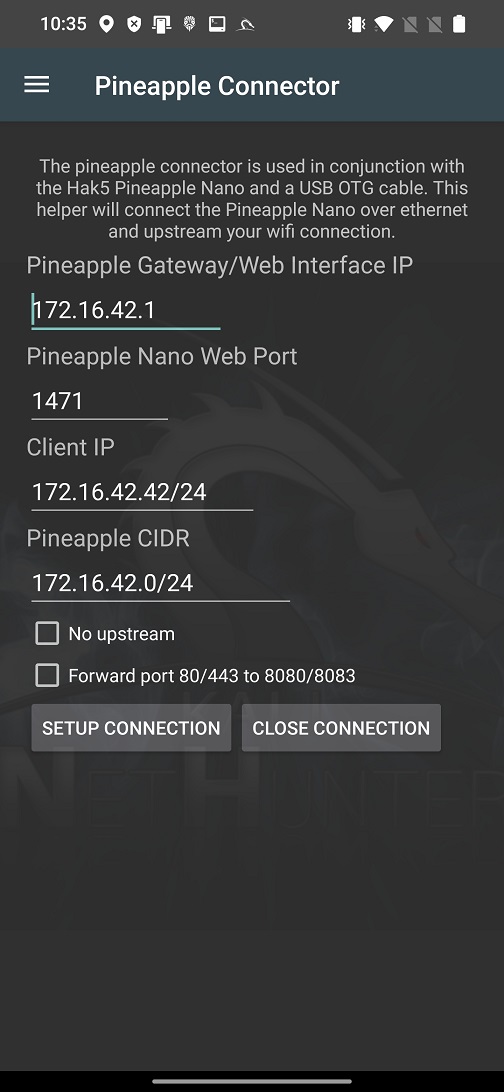
Pineapple Connector
Pineapple Connector is a feature of NetHunter that allows you to connect your Android device to a WiFi Pineapple device using USB cable and OTG adapter as you can see on Figure 6.

The WiFi Pineapple device is a wireless penetration testing tool that can be used to perform various security tests on wireless networks. The Pineapple Connector feature allows you to use your Android device as a network interface for the WiFi Pineapple. This means that you can use your Android device to scan for wireless networks and perform other security tests on them using the WiFi Pineapple.
To use Pineapple Connector, you need to have a rooted Android device with NetHunter (not rootless NetHunter installation). You also need a Y-USB cable with OTG adapter to connect to your Android and external source of power such as battery or wall socket. Once you have all these things, you can connect your Android device to the WiFi Pineapple device and start using Pineapple Connector.
Within Pineapple Connector you can edit your Pineapple Gateway/Web Interface IP, Pineapple Nano Web Port, Client IP, Pineapple CIDR, forward traffic before starting a connection as displayed on Figure 7. Before Setup Connection, you should enable USB tethering on your Android to enable RNDIS.
Unfortunately, I couldn’t replicate the Pineapple Nano setup with NetHunter and play around with it, since currently I don’t have any. If there will be a request from you to go through setup, and usage then we can build one using Raspberry Pi or buy one.
Conclusion
SearchSploit is a valuable tool for security professionals and penetration testers, as it simplifies the process of searching for known vulnerabilities and exploits. By leveraging the Exploit-DB database, it helps identify potential weaknesses in software, enabling users to assess the security of their systems and applications more effectively. However, it is important to note that the tool should be used responsibly and ethically, within the boundaries of applicable laws and permissions, to avoid any illegal or unauthorized activities.
Even though I wasn’t able to fully test it, the Pineapple Nano, a small and portable wireless penetration testing device, can be used with Pineapple Connector to conveniently audit wireless networks. It can be used with Android devices by connecting it via USB tethering to the phone.
如有侵权请联系:admin#unsafe.sh