Apple created post-quantum cryptographic protocol PQ3 for iMessage Pierluigi Paganini February 2024-2-25 07:4:20 Author: securityaffairs.com(查看原文) 阅读量:16 收藏
Apple created post-quantum cryptographic protocol PQ3 for iMessage
Pierluigi Paganini
February 24, 2024

Apple announced the implementation of a post-quantum cryptographic protocol called PQ3 will be integrated into iMessage.
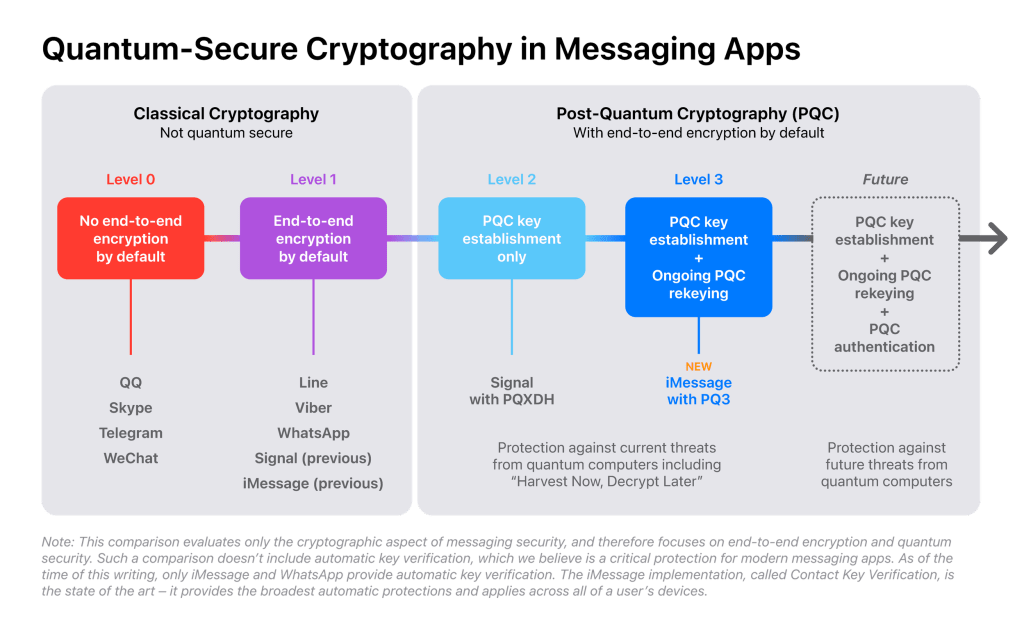
Apple announced a new post-quantum cryptographic protocol called PQ3 that will be integrated into the company messaging application iMessage to secure communications against highly sophisticated quantum attacks.
Apple said that PQ3 is the first messaging protocol to reach what they call Level 3 security, which is the most secure protocol for messaging apps today.
Messaging services use classical public key cryptography, such as RSA, Elliptic Curve signatures, and Diffie-Hellman key exchange, to establish secure end-to-end encrypted connections between devices. However, researchers believe that a sufficiently powerful quantum computer could compromise of end-to-end encrypted communications.
Post-quantum computing refers to events that follow the development of quantum computers. Traditional cryptographic methods, which are widely used to secure data today, rely on mathematical problems that can be solved efficiently by classical computers. However, quantum computers have the potential to solve certain mathematical problems exponentially faster than classical computers, posing a threat to the security of current cryptographic systems.
Post-quantum cryptography refers to cryptographic algorithms and techniques that are designed to remain secure against attacks launched by quantum computers.
“Although quantum computers with this capability don’t exist yet, extremely well-resourced attackers can already prepare for their possible arrival by taking advantage of the steep decrease in modern data storage costs. The premise is simple: such attackers can collect large amounts of today’s encrypted data and file it all away for future reference.” states the announcement. “Even though they can’t decrypt any of this data today, they can retain it until they acquire a quantum computer that can decrypt it in the future, an attack scenario known as Harvest Now, Decrypt Later.”
The company announced it has rebuilt the iMessage cryptographic protocol from the ground up to advance the state of the art in end-to-end encryption.
PQ3 introduces a new post-quantum encryption key in the set of public keys generated locally by each device. The devices send the keys to Apple servers as part of the iMessage registration process. The company used Kyber post-quantum public keys, because the algorithm is recommended by NIST.
This implementation allows sender devices to acquire receiver public keys and generate post-quantum encryption keys for the initial message, even if the receiver is offline, a process referred to as initial key establishment.
PQ3 also incorporates a periodic post-quantum rekeying mechanism within conversations.
PQ3 is designed to implement a hybrid approach, combining Elliptic Curve cryptography with post-quantum encryption during both the initial key establishment and rekeying processes.
“With PQ3, iMessage continues to rely on classical cryptographic algorithms to authenticate the sender and verify the Contact Key Verification account key, because these mechanisms can’t be attacked retroactively with future quantum computers. To attempt to insert themselves in the middle of an iMessage conversation, an adversary would require a quantum computer capable of breaking one of the authentication keys before or at the time the communication takes place. In other words, these attacks cannot be performed in a Harvest Now, Decrypt Later scenario — they require the existence of a quantum computer capable of performing the attacks contemporaneously with the communication being attacked.” concludes the announcement. “We believe any such capability is still many years away, but as the threat of quantum computers evolves, we will continue to assess the need for post-quantum authentication to thwart such attacks.”
Follow me on Twitter: @securityaffairs and Facebook
(SecurityAffairs – hacking, PQ3)
如有侵权请联系:admin#unsafe.sh
