2024-2-23 01:49:22 Author: securityboulevard.com(查看原文) 阅读量:5 收藏

You may think you’ve covered all your bases, but can modern organizations let their guard down in the face of residual risks? Today’s corporations face increasingly complex risks, including new challenges that can have far-reaching consequences. Awareness is step one, but managing and mitigating each new type requires proactive and strategic risk management efforts.
Residual risk has become even more critical since President Biden signed the Cybersecurity Executive Order. Companies are now expected to significantly reduce residual supply chain risks to limit the impact of third-party breaches by nation-state threat actors. One crucial aspect of risk management is understanding and calculating residual dangers, aka the persistent risks.
This article will explore residual risks, their significance, how to define residual risks, and how to manage and mitigate them best using Hyperproof’s step-by-step guide.
What is residual risk, and why is it important?
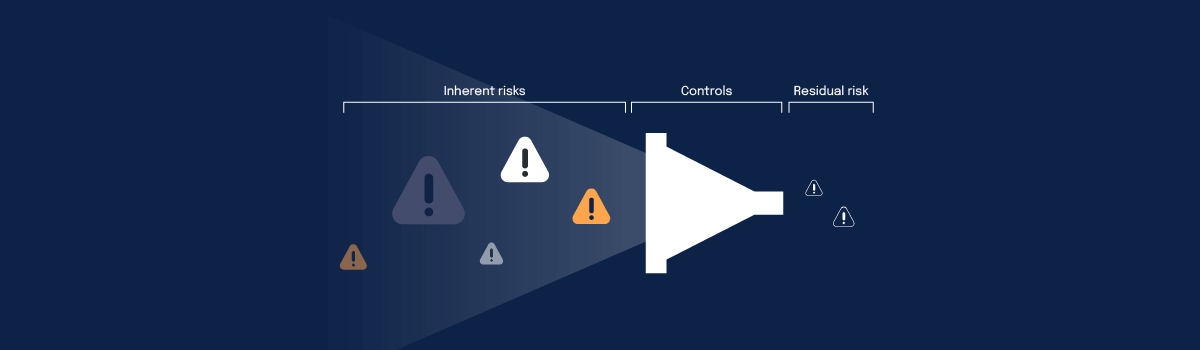
Residual risk is a term that encompasses the risks that linger despite your best efforts to reduce or eliminate them. They are the risks that remain within an organization even after implementing various management measures, controls, and safeguards. Furthermore, it’s important to note that residual risk assessment is not just a best practice — it’s often a mandatory requirement. Regulations such as ISO 27001 demand that organizations assess residual risk to adequately protect their assets and data.
To clearly understand residual risk, it’s essential to differentiate it from inherent risk. Inherent risk represents the baseline level without controls, while residual risk represents what remains after implementing security measures. This differentiation is critical for effective risk management, allowing organizations to concentrate on addressing specific vulnerabilities and minimizing potential damage by comprehending the risks that persist even with controls in place.
4 examples of common residual risks
1. Third-party data breaches
Even after implementing security controls and risk assessments, there remains a residual risk of a data breach through a third-party vendor. This residual risk exists because it is nearly impossible to eliminate all potential vulnerabilities and threats associated with these external partners. To combat this, you can utilize a vendor management tool to assess your vendors’ security and compliance posture and effectively manage third-party risk.
Hyperproof’s vendor management tool has built-in tools for risk assessment, vendor criticality, and risk scoring. Whether you need to conduct one-off assessments on a fixed schedule or both, our platform provides the flexibility you need.
2. Cybersecurity threats in cloud computing
Cloud computing offers various benefits but exposes an organization to cyber threats due to the shared responsibility model with cloud service providers. The residual risk in cloud computing involves the persisting security gaps despite implementing security measures. For instance, an organization may configure its cloud resources securely, but residual risks could still exist due to unforeseen vulnerabilities or the cloud provider’s actions.
3. Insider threats
Insider threats, such as data theft or sabotage by employees or contractors, always represent an inherent risk to organizations, no matter how diligent you are about preemptively addressing these risks with security controls like access restrictions, monitoring, and employee training, you just can’t eliminate the possibility of malicious actions by individuals within the organization. Like both of the above examples, the residual risk persists.
4. Risk in cyber insurance policies
Unfortunately, not all policies cover all liabilities. System upgrades, future financial losses, specific malware attacks, and decreased valuation are examples of what is not typically covered. Most companies opt for first-party coverage, however, in some cases, third-party coverage will be a better fit (and could even be used in addition to first-party coverage.
How to calculate residual risk

Calculating residual risk is a crucial aspect of effective risk management within organizations. To begin this process, one must undertake a comprehensive security risk assessment. This involves a deep dive into the organization’s security landscape, starting with clearly understanding how and where data is stored. Identifying data repositories and understanding their locations and structures is essential in uncovering potential vulnerabilities. Equally important is gaining insight into who within the organization has access to this data. Recognizing the individuals and roles that can interact with sensitive information is a pivotal step in assessing the associated risks.
Once data access points are established, the next step is to review and evaluate various security risks. This includes identifying potential threats, vulnerabilities, and weaknesses that could compromise the security of the data. These findings are then consolidated into a comprehensive risk register, providing a centralized repository of identified risks. To further refine this process, it is crucial to focus on the likelihood that a risk will result in a security incident and the potential impact of such an incident–described in greater detail in the following section.
This two-pronged approach helps organizations prioritize their efforts, concentrating resources on addressing the most critical and potentially harmful risks.
In summary:
- Complete a security risk assessment
- Build a comprehensive risk register
- Assess the risks’ likelihood and potential impact on security incidents
Developing effective residual risk management strategies
Once you understand residual risk and how it is calculated, the next step is to develop effective strategies to manage and mitigate it. Here are three key strategies to consider:
1. Assign weights to controls
As mentioned above, organizations should use a risk register to assign weights to controls based on their importance. Critical controls, such as incident response plans and recovery exercises, should receive higher weights. This weighting system helps prioritize the allocation of resources to manage residual risk effectively.
2. Leverage existing frameworks and best practices
Implementing recognized risk frameworks, such as pre-existing risk assessment templates and FAIR (Factor Analysis of Information Risk), can provide a structured approach to residual risk assessment and management. These frameworks offer valuable methodologies for quantifying risk and prioritizing mitigation efforts. Following industry best practices ensures organizations align their efforts with proven risk reduction and mitigation strategies. You can reference our guide and free template here.
3. Implement continuous risk monitoring
Residual risk management is an ongoing process. It should be proactive, not reactive. While initial controls are essential, organizations must continuously assess and update their risk mitigation measures. Regularly review and enhance your controls to adapt to changing threats and vulnerabilities.
Automate and simplify residual risk management with Hyperproof
Risk management is a complex task that requires strict due diligence and attention to detail. The good news is that you don’t have to tackle it alone. Hyperproof’s compliance operations platform conveniently organizes risk information in a user-friendly dashboard and provides the tools to help you remediate residual risks continuously.
With Hyperproof, you can seamlessly tie a control to the risk and compliance requirements. This integration makes it easy to gauge how much a specific risk has been mitigated by existing controls (inherent risk) and how much residual risk remains. By aligning your risk management and compliance management activities using Hyperproof, you’ll save time and gain operational efficiency– providing your leadership team with a complete picture of your security and compliance posture.
With Hyperproof, you can take your risk management to the next level. Request a demo today, and let us show you how we can support all your risk management needs.
The post Residual Risk Defined: Expert Strategies for Management and Mitigation appeared first on Hyperproof.
*** This is a Security Bloggers Network syndicated blog from Hyperproof authored by Hyperproof Team. Read the original post at: https://hyperproof.io/resource/residual-risk-definition/
如有侵权请联系:admin#unsafe.sh