How Thales and Red Hat Protect Telcos from API Attacks
madhav
Application programming interfaces (APIs) power nearly every aspect of modern applications and have become the backbone of today’s economy. Every time you send a mobile payment, search for airline flight prices, or book a restaurant reservation – you are using an API. Unfortunately, API attacks are increasing as vectors for security incidents. In particular, the Telcom industry has fallen victim to several high-profile API attacks. In this blog, we will explain the unique data security challenges for Telcos and three ways how both Thales and Red Hat can help them protect against future API attacks.
What are APIs?
APIs are software intermediaries that enable two software components to communicate with each other. The information exchanged usually follows a set of definitions and protocols. For example, if you book a restaurant reservation online, you will see enough information exposed to know if certain timeslots and tables are available. However, you would not be able to access the restaurants more sensitive data such as their financial, employee, or tax records. This illustrates how a customer is allowed to access a selected portion of the restaurant’s business information they have chosen to expose via an API.
Why have APIs become ripe attack vectors?
APIs have also become an increasingly popular attack vector for many reasons, including organizational sprawl and an ever-changing attack surface. Most API attacks are the result of credential theft.
When an organization’s APIs are attacked, it can often be difficult to detect for weeks or months. By that point, the threat actors usually have succeeded in exfiltrating data, taking control of systems, and disrupting critical operations often costing millions of dollars in revenue losses. Additionally, companies often incur additional setbacks with reputation damage, steep financial fines, and regulatory penalties.
What are Telcos particularly vulnerable to API attacks?
Over the past year, the Telecom industry has suffered some massive, high-profile data breaches — all of which happened by exploiting unprotected APIs. These include breaches on major operators such as T-Mobile.
Telecoms are particularly vulnerable to API attacks for several reasons.
Massive IT Footprints: Most Telcos usually have very large IT environments to support their subscriber bases, which often ranges from tens of thousands to millions of users. These large subscriber bases in turn generate massive data volumes. These volumes are in turn managed by numerous applications and other IT solutions. As a result, these enormous IT infrastructures are extremely challenging to govern and secure.
Complex Environments: Telcos often have legacy equipment and services they support to run their core, mobile, and access networks. This is further complicated by the variety of vendors, standards, and service-level agreements (SLAs) they also need to support. The more variations in the environment, the more complicated it is to manage.
Legacy Technology Clashes: Most Telcos have very large legacy IT footprints. This unfortunately does not always integrate well with more modern technologies such as containerized or Kubernetes-based cloud-native applications.
Highly Coveted Data: Telcos manage lots of valuable data. This could include Personally Identifiable Information (PII) of their subscribers or even their payment information. Additionally, in some geographies Telecoms are tightly coupled with critical government infrastructure operations. In this capacity, they manage highly sensitive and high-stakes data coveted by cyber-criminals and terrorist organizations.
Security Expertise Deficit: IT security is still very much a learning curve for the Telco sector at large, making it difficult for them to get ahead of the current threat landscape.
Revenue Incentives: Telcos have been rapidly embracing API developments to expose new services, as a new revenue stream for their organizations. However, delivering this value to their customers is a double-edged sword, as this both creates monetization opportunities yet also comes with a new set of inherent security risks by exposing their Network Functionality (NF) and data in new ways.
3 Ways Telcos Can Bolster Data Security
Often the biggest barrier to Telcos protecting their critical data is the lack of security knowledge required and also the need to often re-write application code. Together, both Thales and Red Hat offer solutions to overcome some of these data protection and management challenges.
1 – Encrypt Data at Rest
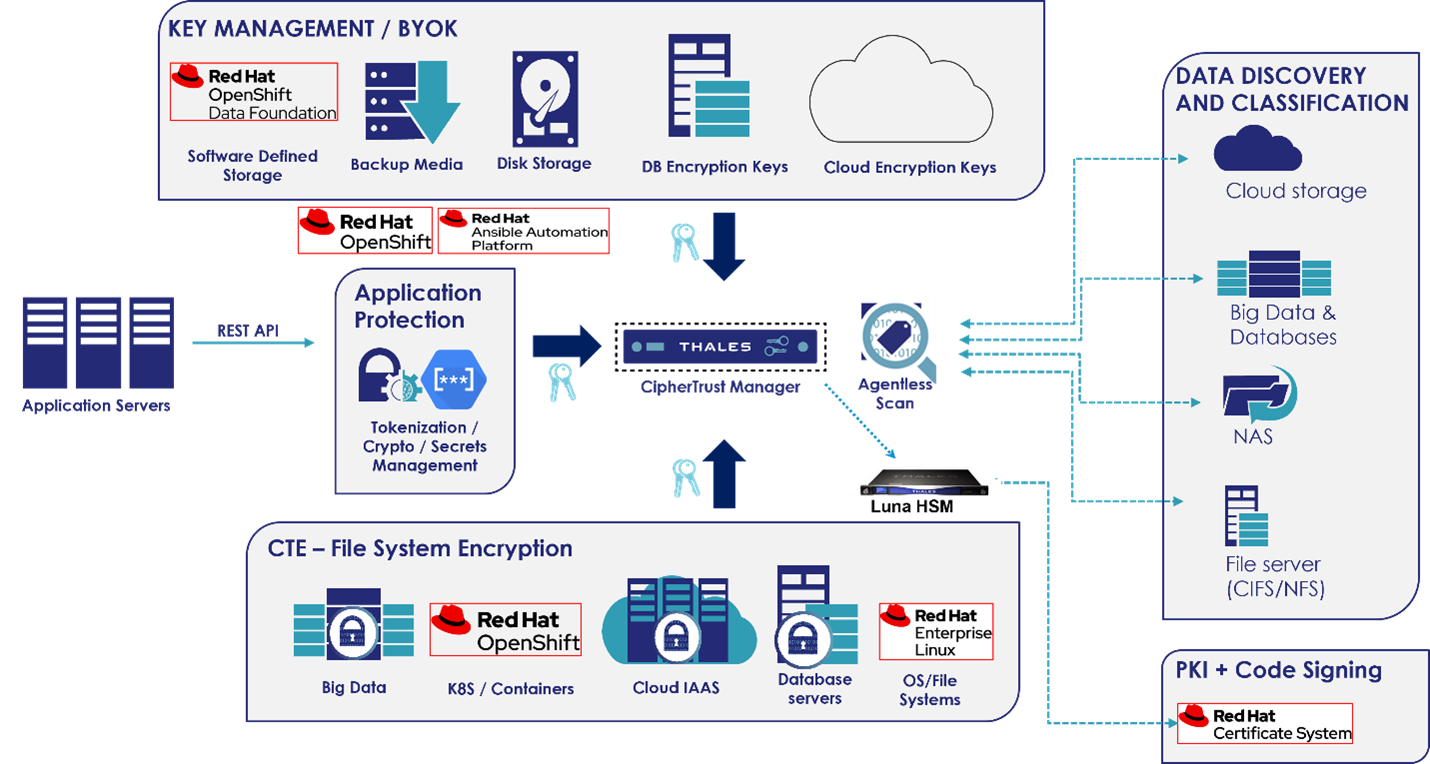
To prevent data leakage, unauthorized access, and physical theft organizations are increasingly looking to secure data at rest. Encrypting this data with Thales CipherTrust Transparent Encryption (CTE) secures files and documents, ensuring that only those with authorized encryption keys can access them. CTE delivers data-at-rest encryption with centralized key management, privileged user access control, and detailed data access audit logging to protect data on premises, across multiple clouds, and in containerized environments. Thales CTE secures data in persistent volumes running on Red Hat OpenShift, a unified platform to build, modernize, and deploy applications at scale. With this integration, both Red Hat and Thales enable telco and cloud service providers to quickly harness the power of 5G across their cloud, edge, and legacy environments while steadfastly protecting sensitive data.
2 – Protect data to any RESTful web service or microservice using REST APIs
The Thales Data Protection Gateway (DPG) protects data passing across TLS channels from Point A to Point B by encrypting the data itself. Encryption ensures the data itself cannot be accessed, even if intercepted during a “Man-in-the-Middle” attack. DPG performs data security operations transparently on behalf of the application, but without changing the application or requiring any code changes. DPG can be easily applied to existing Telco environments using REST API services or micro-services as either a standalone gateway for legacy applications or as a container “sidecar” running in Kubernetes for newer cloud-native applications managed by Red Hat OpenShift.
3 –Secure your encryption keys, the root of trust for applications
Hardware Security Modules (HSMs) tend to work behind the scenes when it comes to protecting APIs or API endpoints. First and foremost, HSMs confirm the legitimacy of the API endpoint by protecting the endpoint’s TLS certificate. This ensures the calling application can trust the API endpoint and that they’re not talking to a rogue API. Secondly, HSMs can also protect code signing keys, to provide confidence that the software or containers deployed are legitimate and from a trusted source.
Both legacy and container-based applications running in Red Hat OpenShift can be secured from credential breaches by protecting their cryptographic keys with Thales Luna HSMs. Using Luna HSMs provide a secure root of trust, for some of the most security-conscious organizations in the world by securely managing, processing, and storing encryption keys inside a FIPs-validated, hardened, and tamper-resistant device. Using Luna HSMs to secure 5G VNFs, protect PKI-based infrastructure, subscriber authentication, identity and privacy can also help Telcos meet industry compliance and government regulatory mandates for data privacy and consumer protection.
Thales and Red Hat Integration Overview
Conclusion
While APIs are the largest and most vulnerable attack surface for Telcos, measures can be taken to protect against breaches and secure their critical data. Together, both Thales and Red Hat can help Telcom providers overcome the security and management obstacles challenging their IT departments. To learn more about how Thales can help protect Telco environments, visit our booth (Hall 2, Stand 2J30) at the upcoming Mobile World Congress in Barcelona , taking place February 26th – 29th.

*** This is a Security Bloggers Network syndicated blog from Thales CPL Blog Feed authored by madhav. Read the original post at: https://cpl.thalesgroup.com/blog/encryption/telco-api-security-thales-red-hat-solutions
