The bootloader vulnerability affecting several generations 2024-2-9 19:6:0 Author: blog.elcomsoft.com(查看原文) 阅读量:16 收藏
The bootloader vulnerability affecting several generations of Apple devices, known as “checkm8”, allows for forensically sound extraction of a wide range of Apple hardware including several generations of iPhones, iPads, Apple Watch, Apple TV, and even HomePod devices. The exploit is available for chips that range from the Apple A5 found in the iPhone 4s and several iPad models to A11 Bionic empowering the iPhone 8, 8 Plus, and iPhone X; older devices such as the iPhone 4 have other bootloader vulnerabilities that can be exploited to similar effect. In this article, we will go through the different chips and their many variations that are relevant for bootloader-level extractions.
What’s “checkm8”?
checkm8 is a bootloader-level exploit that enables low-level access to the device’s file system, encryption keys, and keychain, making it a valuable tool for security professionals. While the exploit itself does not alter any data on the device’s system or user partitions, its various implementations, including the checkra1n jailbreak and many proprietary implementations in various forensic tools, are not nearly as forensically sound as the underlying exploit.
While checkm8 gained the most attention, older devices (prior to the A5 chip used in the iPhone 4s and several other devices) have similar bootloader exploits known as limera1n, SHAtter, steaks4uce, and Pwnage 2.0. For this reason, we prefer talking about “bootloader exploits” and “bootloader-level extractions” rather than “checkm8”.
Our solution
We strived to make our implementation truly exemplary. Bootloader-level extractions performed with iOS Forensic Toolkit are both repeatable and verifiable, making them fully compliant with the requirements of forensically sound investigations. We have solved all common issues that can occur with this method, and support practically the entire range of iOS versions that can be installed on vulnerable devices starting from iOS 3 all the way up to the currently latest iOS 16 builds supported by these platforms. Our solution is truly universal, supporting most iOS beta versions and over-the-air updates, with a notable exception: at this time, iOS 17 is not supported.
iOS 17 can be installed on the following devices:
- iPad 6, 7, and iPad Pro 1, 2
- Apple TV HD, 4K
- HomePod
We are working hard on adding support for the latest iOS 17 builds for those devices.
Critical to forensic examinations is the precise detection of iOS version installed on the device. We developed a unique method that can reliably determine the exact system version installed on the device based on various bits and pieces available through DFU mode. The latest iteration excels in handling atypical scenarios such as interrupted OTA updates thanks to obtaining the required data directly from the SEP (Secure Enclave Processor).
Furthermore, our bootloader-level extraction method is engineered for cross-platform functionality, available in macOS and Linux editions, with Windows compatibility on the horizon.
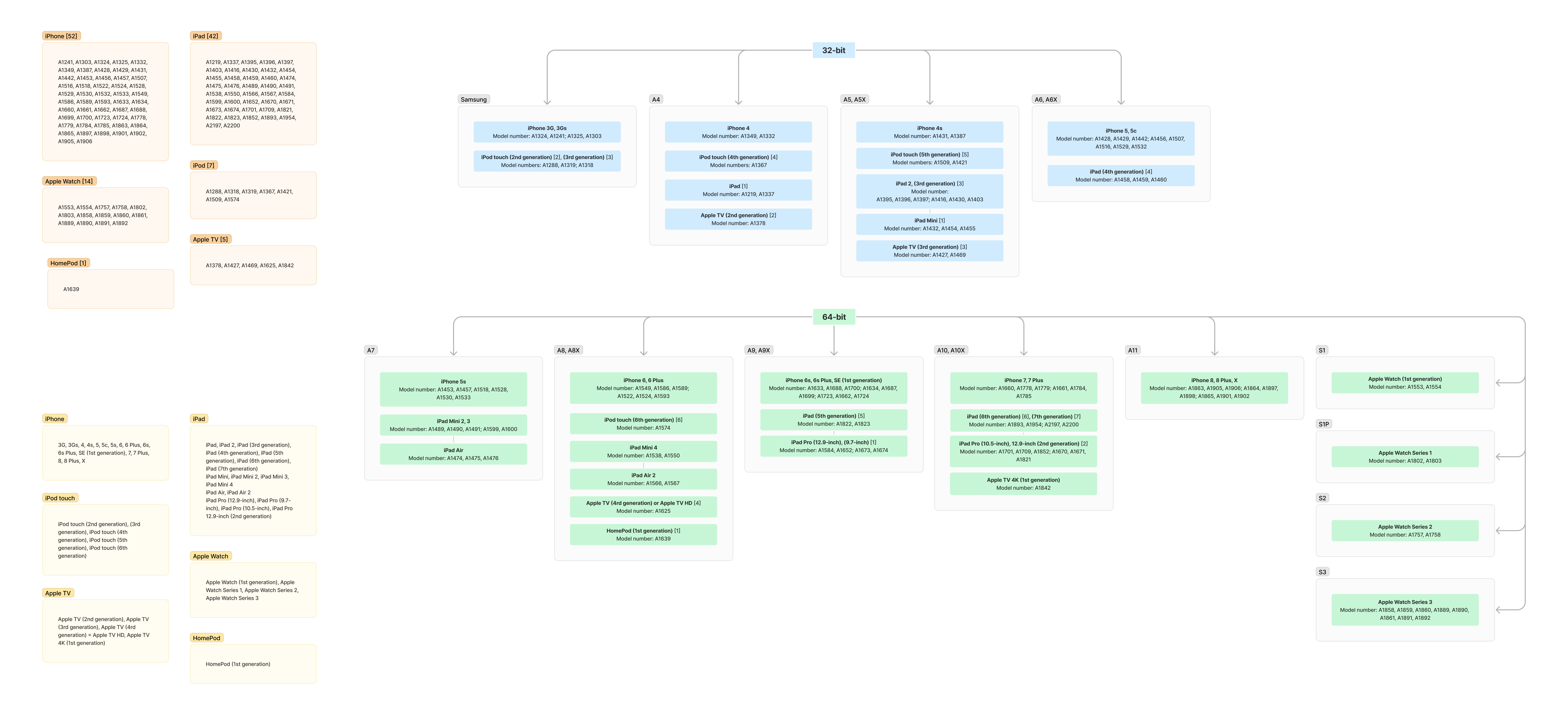
Compatibility matrix
We’ve listed all compatible models in the following graph.
Click to expand
The following are some interesting nuances:
- Low-level extraction with enhanced support for 32-bit models
- Blue indicates 32-bit models: For these devices, we offer comprehensive forensic analysis, including the extraction of full dumps and decryption, with the possibility of passcode unlock.
- Green denotes 64-bit models: While these devices incorporate Secure Enclave, we still provide comprehensive forensic analysis, sans passcode unlock. Notably, devices like Apple TV and HomePod lack Secure Enclave and the passcode.
- Apple Watch chip variants
- Supported Apple Watch devices feature distinct chips: S1, S1P, S2, and S3, each with unique capabilities.
- Apple Watch S0: S1
- Apple Watch S1: S1P
- Apple Watch S2: S2
- Apple Watch S3: S3
- Notably, the S1 chip, akin to A6 on iPhone 5/5c, supports APFS despite 32-bit architecture, which presented a unique challenge. We are currently developing a passcode unlock method for this chip.
- Supported Apple Watch devices feature distinct chips: S1, S1P, S2, and S3, each with unique capabilities.
- File system variations
- 32-bit devices utilize HFS file system, while 64-bit devices typically transition to APFS from iOS 10.3 onwards (and HFS for versions prior to iOS 10.2), with the exception of abovementioned Apple Watch.
- Exploits and vulnerabilities
- We leverage multiple exploits for forensic access, including checkm8, which we use exclusively for devices from A5 onwards. For older devices, we’re using limera1n, SHAtter, steaks4uce, and Pwnage 2.0, ensuring broad device coverage and access.
- Support for X variant chips
- Certain iPad and Apple TV models feature X variant chips, which are modified versions of the corresponding iPhone SoC (e.g. the first-gen Apple TV 4K uses Apple A10X, which is also used in in the 10.5″ iPad Pro and the second-generation 12.9″ iPad Pro). While specifics may vary, we ensure comprehensive support, with tailored exploit implementations where necessary.
- Variants in iPad models
- iPads come in Wi-Fi and 3G/LTE variants, each with its nuances. While some forensic vendors may support only one variant, we offer full support for all configurations with no exceptions.
- Global model versions
- Most device models have regional variations for different markets (e.g., U.S., European, and Asian markets). Our solution provides comprehensive support for all of these versions.
- Challenges with A5 chip
- The A5 chip in its three incarnations used in the iPhone 4s, iPod Touch 5, iPad 2 and 3, the original iPad mini, and Apple TV 3, poses significant challenges for exploit implementation. This chip required us to develop a unique, highly specialized approach based on a Raspberry Pi Pico board with custom firmware.
Conclusion
Our tool’s enhanced capabilities not only overcome common forensic challenges but also delve into the nuances of the many device models, versions, and SoC variations, providing forensic specialists with a comprehensive toolkit for in-depth analysis across a wide range of mobile devices.
如有侵权请联系:admin#unsafe.sh