2024-2-8 09:30:0 Author: securityboulevard.com(查看原文) 阅读量:12 收藏
This article introduces the concept of Continuous Threat Exposure Management (CTEM), delving into the philosophy behind CTEM, its five stages, and exploring key technologies that support its implementation.
I. Introduction
In mid-October 2023, Gartner released the top 10 strategic technology trends for 2024 that enterprises need to explore, as depicted in Figure 1.
Gartner categorized these trends into three themes: “Protect Your Investment,” “Rise of Builders,” and “Deliver the Value.” Notably, over half of these trends are related to artificial intelligence (AI). In addition, the trends of cloud computing and sustainable intelligent applications are key focal points for enterprises. Given the recent surge in popularity of large language models and the steady implementation of cloud computing technologies over the past year, the selection of these technologies comes as no surprise.
Looking back at Gartner’s historical technology trend analyses, asset risk management has always been a focal point, including technologies such as Attack Surface Management (ASM), External Attack Surface Management (EASM), Cyber Asset Attack Surface Management (CAASM), and Digital Risk Protection Services (DRPS). How does CTEM differ from these previous technologies? This post explores this topic.
II. What Is Continuous Threat Exposure Management (CTEM)?
Managing an organization’s attack surface has emerged as a prominent topic in recent years, reflecting a timely and evolving security landscape. While previous years emphasized interconnected networks and relatively singular network assets, today’s enterprises seamlessly integrate various innovative technologies such as cloud computing, big data, the Internet of Things (IoT), mobile security, and smart operations into every aspect of their operations. This undoubtedly significantly expands the attack surface for enterprises. Simultaneously, new types of cyber threats are continually evolving, with an asymmetry between offense and defense. Attackers have ample time and resources to devise strategies, bypass defenses, evade detection, and render the current effectiveness of security products related to asset risk management unsatisfactory.
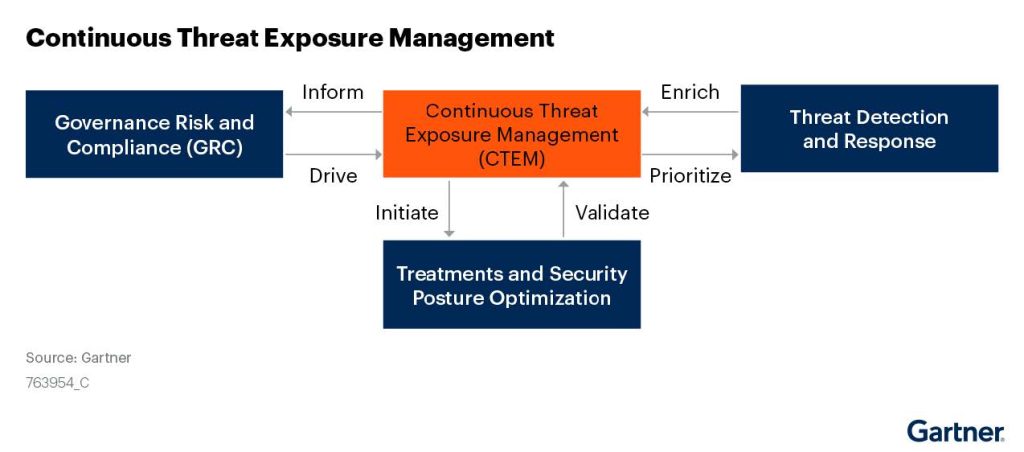
In 2022, Gartner introduced the concept of Continuous Threat Exposure Management (CTEM), aiming to manage enterprise exposure risks from the perspective of attackers. Since most organizations’ attack events stem from an unaware attack surface, CTEM aims to provide actionable, continuous enterprise security repair and improvement plans. Security managers can understand and act according to this plan. The relationship between continuous threat exposure management and other elements is illustrated in Figure 2.
III. Five Stages of CTEM
CTEM is not just a technology but a set of processes and capabilities used to mitigate risks in the digital environment of an organization. By adopting this strategy, organizations of various sizes can enhance their overall security defense capabilities by continuously monitoring and managing potential attacks they face. Gartner divides CTEM into five stages: Scoping, Discovery, Prioritization, Validation, and Mobilization.
3.1 Asset Scoping
In continuous threat exposure management, defining the boundaries of enterprise assets is a crucial step. The main objective of this stage is to determine which systems and assets will be included and identify the stakeholders involved. Defining the scope is challenging, relying not only on technical means but also requiring collaboration from relevant business personnel within the organization.
The asset scope between the offensive and defensive parties is asymmetrical, requiring alignment with attackers to delineate the enterprise’s asset scope, as shown in Figure 4.
The scoping stage aims to identify the terrain that the organization needs to defend by defining the scope, laying the foundation to effectively protect its assets and systems from security risks.
3.2 Asset and Risk Discovery
After determining the scope, the next step is the comprehensive discovery of internal assets and risks within the organization. “Asset management” and “risk management” are familiar faces in the security domain, and while asset and vulnerability management may be yesterday’s issues, Gartner’s trend indicates the ongoing presence of technologies related to attack surface management. This suggests that there is still room for improvement in current practices. Dynamic changes in technology, business, and personnel result in ongoing changes to assets, making it challenging to identify “Shadow IT.” Therefore, CTEM emphasizes a cyclical and iterative operation. Achieving dynamic and comprehensive asset discovery requires an operational system, utilizing AI technology and asset operation platforms. By confirming assets through continuous operational iterations and involving relevant personnel from IT, business, and management, organizations can achieve comprehensive asset discovery.
The implementation of CTEM often fails initially due to confusion between scoping and asset discovery. Success lies not only in the quantity of discovered assets and vulnerabilities but, more crucially, in accurate scoping based on business risks and potential impacts. Many findings go beyond the initial scope, uncovering hidden assets, vulnerabilities, misconfigurations, and other risks. At this point, updating the organization’s asset scope is necessary.
3.3 Risk Prioritization
The goal of this stage is to systematically assess and prioritize the risks. Nearly every organization has numerous cybersecurity risk points, and with the application of modern technologies, risks continue to grow. However, it’s challenging for an organization with limited resources to address all cybersecurity issues. Therefore, prioritizing solutions enhances the effectiveness of risk mitigation. Vulnerability Prioritization Techniques (VPT) can be employed to calculate repair priorities based on actual risk factors. This calculation requires a comprehensive assessment based on factors such as vulnerability severity, vulnerability exploit popularity and asset importance.
Prioritization provides a prioritized to-do list for technical and business teams, ensuring that the most critical issues are addressed first, thereby increasing the return on investment in internal risk mitigation.
3.4 Risk Validation
The purpose of the validation stage is to verify the attack paths and their likelihood. This step utilizes various tools, such as Penetration Testing as a Service and Red Teaming service, to assess whether the high-risk vulnerabilities discovered in the prioritization step are accurate and to provide validation. Risk validation should not rely solely on traditional security assessment techniques; it also requires automated and dynamic security verification solutions. Intrusion and Attack Simulation (BAS) technology can be used for risk validation, offering a comprehensive confirmation of feasible attack paths within the organization and identifying security control weaknesses from an asset, process, and personnel system perspective. This optimization allows for a more holistic perspective on the organization’s security status instead of individual vulnerability.
3.5 Mobilization
The primary purpose of the mobilization stage is to enable stakeholders to formulate repair plans and implement them. Automation primarily deals with common issues, such as patch updates or basic threat detection. However, for complex and subtle vulnerabilities, complete automation is often challenging. Therefore, security teams need to recognize that automated remedies are just a starting point, not a final solution. This stage involves four specific steps:
- Repair Plan: Begin with a risk-prioritized repair plan, identifying at-risk users and bottleneck locations critical to risk. By fixing these areas, the organization can exert minimal effort to solve major problems.
- Repair Review: The organization should review exposed issues, risks, and repair plans collaboratively with key stakeholders to devise the best way to fix the security problem.
- Risk Mitigation: Convey risks and repair methods to relevant teams, driving the implementation of the repair plan. It is easier to implement mobilization by encouraging teams to fix high-risk vulnerabilities instead of fixing all vulnerabilities.
- Repair Validation: The organization should verify that repairs are complete and that the risk has been eliminated.
IV. Conclusion
CTEM is poised to be the trend in enterprise security management for the next five years, offering a dynamic, proactive defense approach to solving security problems. It helps enterprises manage their exposure risks through continuously iterative operations. A significant portion of an enterprise’s risk exposure stems from errors in configuration, weak passwords, and unpatched vulnerabilities. Although many network security management tools can address these issues, the actual results are often unsatisfactory. This is primarily due to the dynamic changes in enterprise risk exposure resulting from the application of new technologies, changes in business, team personnel adjustments, etc. Therefore, Gartner has introduced the concept of Continuous Threat Exposure Management, utilizing a combination of multiple automation technologies to ensure continuity and dynamically address problems from the attacker’s perspective.
In summary, as a flexible and evolving security management strategy, CTEM provides comprehensive and continuous network security protection for enterprises, enhancing their ability to counter evolving network threats. According to Gartner’s strategic planning assumption, organizations prioritizing their security investments based on a continuous threat exposure management program will realize a two-thirds reduction in breaches by 2026. We believe this conclusion is entirely possible, and we eagerly await the developments in the next three years.
If you’re looking to improve your organization’s cybersecurity posture, CTEM is a great place to start. Read the NSFOCUS CTEM Datasheet, or contact us today to schedule a consultation and discover how we can tailor a CTEM program to safeguard your digital assets.
The post CTEM: Navigating the Future of Attack Surface appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/ctem-navigating-the-future-of-attack-surface/
如有侵权请联系:admin#unsafe.sh





