Unveiling the Enigma of Path Navigation: An Exhaustive Exploration and InsightPath Navigation 2024-2-6 21:47:58 Author: lab.wallarm.com(查看原文) 阅读量:27 收藏
Unveiling the Enigma of Path Navigation: An Exhaustive Exploration and Insight
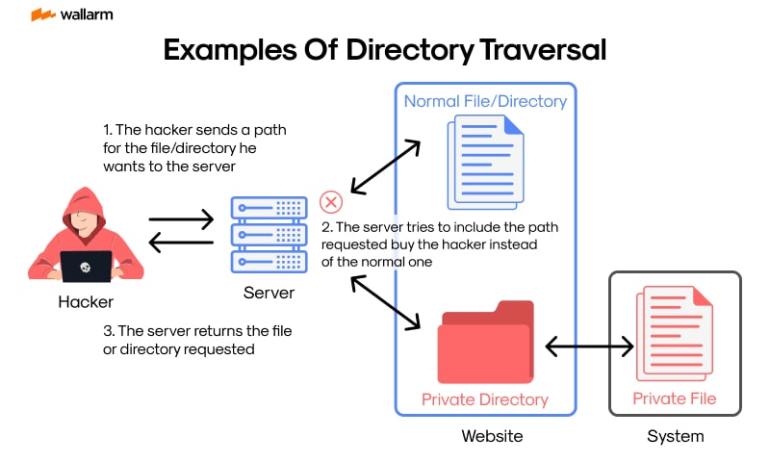
Path Navigation, often referred to as Folder Navigation, symbolizes a kind of security extraction point allowing unauthorized individuals to gain unauthorized access to specific files held within a server's database repository. This susceptability often emerges when user-provided file names are insufficiently sanitized and checked, thereby presenting a gap that ill-intended individuals can exploit, manipulate, and modify the content contained within any data file, eventually circumventing the designed folder system.
Delving into Folder Navigation requires an elementary understanding of the term 'directory' in the context of computing processes. At the core, a directory serves as a sort of organizational tool within a data processing architecture, hosting pointers that lead to various electronic documents and potentially, more directories. To put it in simpler terms, directories can be likened to physical file holders or registration cabinets in a traditional office setting.
App-based solutions with internet connectivity offer the perfect environment for Path Navigation malpractices. User input is usually employed to construct a file path crucial for operations such as data conservation or extraction. Inadequate vetting of these inputs may place a manipulator in a position to modify the path and interfere with files that are normally inaccessible.
For illustration, let's consider an online application that incorporates a function to fetch images from a designated pathway:
<code class="language-python">def fetch_image(pathway):
with open(pathway, 'rb') as content:
return content.read()</code>
If an attacker manages to gain command over the pathway variable, they could easily access critical data files. A pathway like ../../../etc/password could lead them straight into the server's safeguarded password chamber.
Breaches of Folder Navigation can be classified into two categories, namely, absolute and relative.
-
Absolute Path Navigation: Under this category, the attacker will typically inject the actual path directly, to identify and locate the targeted document, for instance,
/etc/password. -
Relative Path Navigation: In this case, the attacker uses relative paths (such as
../../) to navigate across the data architecture, for instance,../../etc/password.
The consequences of a Path Navigation breach can range significantly based on the system setup and the volume of accessible data. In the most extreme case, a violator might assume total control over the system.
The forthcoming sections will illustrate various examples of Path Navigation breaches, in addition to offering potential approaches for their identification and prevention. Expand your understanding to fortify your digital defence efforts!
An In-depth Scrutiny of Path Traversal: A Functional Viewpoint

Shedding light on the horizon of cyber defense, Path Traversal emerges as a significant loophole. This flaw could lead to the exposure of classified data, thus reflecting poorly on the system's credibility concerning security. Let us now explore various real scenarios demonstrating the repercussions of Path Traversal operations.
Model 1: The Primitive Path Traversal Attack
Think of an online interface that uses a URL segment to present a file to its subscribers.
A typical URL at this interface could be:
http://example.com/exhibit?record=hello.html
The 'hello.html' file is retrieved from the interface's native repository and displayed to the viewer. However, a malicious entity might modify this URL to gain entry to files beyond the designated directory, employing ".." (a standard symbol pointing to the superior directory in numerous data systems).
Subsequently, they could transform the URL into:
http://example.com/exhibit?record=../../etc/passwd
Such manipulation might allow the cyber perpetrator to access '/etc/passwd', a core system file in Unix-based frameworks, usually hosting user validation details.
Model 2: The Camouflaged Path Traversal Attack
Often, web-based applications have built-in shield mechanisms to combat apparent Path Traversal maneuvers. Still, offenders cleverly find ways to bypass these by masking their Path Traversal techniques.
For example, they can URL-encode the ".." string as "%2e%2e", modifying the initial exploit to:
http://example.com/exhibit?record=%2e%2e%2f%2e%2e%2fetc%2fpasswd
Model 3: Sidestepping Protection Filters Intended to Deter Intrusions
Some digital platforms employ protection filters aiming to discourage Path Traversal tactics by blocking or invalidating specific characters or sequences like "..". Yet, ingenious culprits can dodge these precautions using techniques like double encoding, alternative encodings, or null byte infiltrations.
Here's a demonstration of a doubly-encoded Path Traversal operation:
http://example.com/exhibit?record=%252e%252e%252f%252e%252e%252fetc%252fpasswd
In this scenario, "%25" denotes the character '%'. Accordingly, "%252e" translates into "%2e", which eventually becomes '.'.
Model 4: Exploiting Path Traversal to Infuse Custom Code
Instances arise where intruders take advantage of Path Traversal to insert personalized code into the server. Suppose an online interface uses a URL parameter to initiate a PHP script housed in a particular directory. In such cases, an offender could use Path Traversal to access a PHP script from an unauthorized directory, leading to Remote Code Execution (RCE).
For instance:
http://example.com/exhibit?record=../../uploads/malicious_script.php
Here, 'malicious_script.php' could be a script injected by the hacker into the server's 'uploads' directory.
These models distinctly highlight the potential severe consequences of Path Traversal vulnerabilities. Be on the lookout for upcoming chapters that dive deeper into tactics to identify and eliminate these threats.
Unveiling the Subtleties of Directory Navigational Exploits: A Comprehensive Exploration of their Structure

The cyberattack genre known as Directory Navigational Exploits, alternatively identified as path traversal attacks, allows a hacker to tap into files or folders beyond the core directory of a web server. The hacker cleverly tweaks parameters that reference files with notations like backslash or the series ../, gaining unauthorized access into secluded directories. In this chapter, we dissect these cyber onslaughts, presenting an unclouded perspective on how they function.
1. Directory Navigational Exploits: The Basics
The kernel of a directory navigational exploit lies in the malicious manipulation of feeble security examinations or clean-up of filenames presented by the end-user. This concept can be spotlighted with an example:
<code class="language-python">file = open(request.GET['file'], 'r')</code>
Above, the software retrieves a file named by the end-user. If a hacker introduces a pathway like ../etc/passwd, the system unwittingly unveils the contents of the system's password file.
2. The Role of HTTP in Directory Navigational Exploits
HTTP is a substantial contributor to the landscape of these exploits. Perpetrators regularly employ HTTP GET and POST protocols to disclose vulnerabilities. For example, a hacker might distort the URL in the address box to provoke a navigational exploit:
<code class="language-http">http://example.com/get-files?file=../../etc/passwd</code>
In this previous example, by manipulating the file variable in the URL, the rogue seeker aims to bring to light the password file of the server.
3. Significance of Syntactical Elements in Directory Navigational Exploits
Syntactical elements like ../ or ..\ play a vital role in these kinds of attacks, facilitating an upward shift in the directory hierarchy. Unix-based systems can be manipulated using ../, while ..\ is used for Windows counterparts.
4. Outcomes of Directory Navigational Exploits
The ramifications of these types of attacks can be severe and may include the following:
- Unauthorized access into secure files
- Illicit gathering of data
- System disruption
- Disruption of confidentiality, integrity, and availability
5. Common Targets for Directory Navigational Exploits
Offenders often zero in on:
- Web applications equipped with file download or upload capabilities
- Web applications that handle filenames as variables
- Web applications that are vulnerable to unsanitized user input
6. Diverse Types of Directory Navigational Exploits
The spectrum of these attacks comprises:
-
Basic Directory Navigational Exploits: These classic attacks use
../or..\to gain unsanctioned access to directories. -
Obfuscated Directory Navigational Exploits: This implies masked
../or..\sequences to dodge security barriers. For instance, a hacker may utilize URL encoding, Unicode encoding, or double encoding. -
Advanced Unicode Directory Navigational Exploits: These use extended Unicode characters to overwhelm buffers and dodge security filters.
-
Lengthy UTF-8 Directory Navigational Exploits: Here, hackers use abnormally long UTF-8 sequences to bypass security barriers.
Comprehending the subtleties of directory navigational exploits provides a robust basis for effective defense. The following chapters will discuss testing procedures and preventive solutions to fortify your cybersecurity defenses against these cyber threats.
`
`
Prime Tactics for Efficient File Path Navigation Analysis
The role of file path navigation analysis cannot be overlooked in designing a sound cybersecurity blueprint. It assists in spotting potential weak points that malicious entities could exploit, thereby leading to unauthorized data access. This chapter will provide a deep dive into prime tactics for efficient file path navigation analysis.
1. Grasping the Architecture of the System
Prior to initiating the testing process, it is paramount to grasp the system's architecture. This demands comprehension of the operating system, file structure, and the web server software. The vulnerabilities of each system are unique, and understanding these vulnerabilities will set the stage for customizing your testing tactics.
<code class="language-bash"># Command illustration to determine the operating system uname -a # Command illustration to evaluate the web server software curl -I http://localhost</code>
2. Hands-on File Path Navigation Check
This is a hands-on approach where the tester manually feeds the file path navigation payloads into the system to check if the system is potentially at risk. This technique albeit time-consuming, is highly effective.
<code class="language-bash"># Illustration of a hands-on file path navigation payload ../../etc/passwd</code>
3. Mechanized File Path Navigation Analysis
Mechanized analysis involves using software to seek out file path navigation weak points. Software such as OWASP ZAP and Burp Suite can be set up to execute these checks, thus saving time and ensuring meticulousness.
<code class="language-bash"># Illustration of using OWASP ZAP for mechanized checking zap-cli quick-scan --self-contained http://localhost</code>
4. Arbitrary Data Testing
This form of testing includes feeding the system large quantities of arbitrary data to gauge its resilience. This can aid in spotting vulnerabilities that are unforeseen.
<code class="language-bash"># Illustration of an arbitrary data testing command zzuf -r 0.01 -q -C 10 -s 0:10000 -m <command></code>
5. Obscure and Transparent Testing
Obscure testing involves examining the system without any insight into its internal operations, while transparent testing involves full awareness of the system's architecture. Both techniques possess their strengths and should be employed synergistically.
6. Intrusion Assessment
Intrusion assessment replicates a cyber attack aiming to capitalize on vulnerabilities to gain unauthorized access. This can expose real-world vulnerabilities that other forms of testing might not disclose.
<code class="language-bash"># Illustration of an intrusion assessment command nmap -p80 --script http-vuln-cve2017-5638 <target></code>
7. Periodic Revamping of Your Testing Tactics
Since cyber threats continue evolving, your testing tactics should be evolving at the same pace. By consistently upgrading your tactics and software, you ensure to stay a step ahead of potential intruders.
Comparison Chart: Hands-on vs Mechanized Testing
| Hands-on Testing | Mechanized Testing |
|---|---|
| Detailed but time-consuming | More efficient but could miss some weak points |
| Doesn't demand specialized tools | Depends on the use of specific software |
| No profound technical knowledge needed | Requires technological prowess to set up and understand results |
File Path Navigation Analysis Checklist
- Gain comprehension of the system architecture
- Conduct hands-on file path navigation tests
- Employ mechanized tools for file path navigation analysis
- Execute arbitrary data testing
- Carry out both obscure and transparent testing
- Perform intrusion assessments
- Consistently revamp your testing tactics
In summing up, to carry out efficient file path navigation analysis, you require a comprehensive plan that includes various testing methods. By adhering to these tactics, you can notably improve your system's defense and shield it from possible file path navigation attacks.
Comprehensive Instructions on Folder Navigation Assessment: Beneficial for Your Security Plan
Folder Navigation Assessment plays a fundamental role in your blueprint for digital protection. It assists in discovering possible security gaps in your framework, which could become prey to cyber antagonists. This chapter will equip you with an in-depth understanding and appropriate instruments to execute Folder Navigation Assessment and better safeguard your online presences.
Step 1: Grasping the Fundamentals of Folder Navigation
It’s paramount to gain a comprehensive understanding of what Folder Navigation signifies before initiating the test. Plainly speaking, this denotes an HTTP infringement capable of empowering cyber culprits to access limited folders and activate instructions beyond the primary web server's directory. This situation might result in unauthorized infiltration into confidential data or even gaining control over your server.
Step 2: Establish Your Evaluation Platform
To perform a Folder Navigation Assessment, a regulated setting is required, which could either be a simulated machine or a duplicate server mimicking your real-time environment. It’s vitally important to seclude this environment from your principal server to shy away from any unintentional harm or leakage of data.
Step 3: Locate Potential Weak Spots
Following this, your focus will be identifying possible frailties in your framework. This entails a thorough study of your web application's database and folder blueprint, specifically where client contributions are granted.
For instance, if users are permitted to download files in your application, a cyber intruder could exploit the file trajectory to infract limited directories.
Step 4: Initiate the Assessment
At this stage, commence the evaluation. This process encompasses delivering uniquely designed appeals to your server and scrutinizing the feedback.
For instance, a request might resemble this:
<code>GET /download?file=../../etc/passwd </code>
If the server reciprocates with the content of the '/etc/passwd' file, this signals a Folder Navigation vulnerability.
Step 5: Examine the Output
Once the assessment is completed, it's time to scrutinize the results. If your server reciprocated with restricted information or manifested signs of activating instructions outside the primary folder, these vulnerabilities need to be addressed.
Step 6: Apply Remedy and Repeat Test
Upon detecting frailties, you need to initiate corrective actions. This might mean purifying client input, executing fitting access controls, or altering the application's database and folder map. After these remedies are undertaken, conducting the test again is advised to validate the effectiveness of these solutions.
Step 7: Jot Down Your Discoveries
Finally, it's valuable to keep a record of your discoveries. This should encompass specifics of the weaknesses unearthed, the corrective measures employed, and the outcome of repeated tests. Such documentation can play a critical role in guiding future assessments and conveying your dedication towards digital security.
To wrap up, Folder Navigation Assessment is a pivotal element of protecting a secure web application. Adhering to these steps will help you recognize and rectify potential frailties, amplifying your digital protection and safeguarding your online presence.
Reinforcing Digital Safeguards: Thwarting Potential Path Interpolation Threats
In the realm of cyber security, prevention undoubtedly outweighs cure. This way of thinking also applies when dealing with the threat of Path Interpolation attacks. By grasping the intricacies of these penetration tactics and embracing advanced protective technologies, your digital shield can resist potential incursions. This part outlines varying approaches and tactics to counter Path Interpolation procedures.
1. Input Validation:
The first line of defense against Path Interpolation threats lies in the verification of user input. This action involves the careful inspection and confirmation of all data presented by users to ensure there are no destructive letter blends. Consider the following Python code segment:
<code class="language-python">import os
from flask import request
@app.route('/file', methods=['GET'])
def get_file():
file_path = request.args.get('path')
if '..' in file_path or '%' in file_path:
return "Unauthorized file access attempt", 400
return send_from_directory('static', file_path)</code>
In this instance, the script searches for '..' or '%', which are common in Path Interpolation invasions. If these symbols emerge, the system responds with an error message.
2. Adoption of Secure APIs:
A successful tactic to combat Path Interpolation is the utilization of robust APIs that prevent such infringements. For instance, in Java, you could use java.nio.file.Paths and java.nio.file.Path classes that were specifically designed to deter Path Interpolation attacks. Let's consider this example:
<code class="language-java">Path path = Paths.get("/safe/directory", userInput);
if (!path.normalize().startsWith("/safe/directory")) {
throw new SecurityException("Unauthorized file access attempt");
}</code>
In this context, the normalize() function addresses any '..' sequence, and the startsWith() function ensures the output path sticks within the prescribed directory.
3. Least Privilege Policy:
A cardinal principle in cyber security is the Least Privilege Policy (LPP), in which users are allocated minimal permissions necessary to execute their tasks. By curtailing user access, the potential fallout from a Path Interpolation attack is significantly reduced.
4. Regular Systems Update and Enhancement:
Tech firms frequently prescribe upgrades and safety patches for any identified vulnerabilities, including those susceptible to Path Interpolation. By keeping your systems up-to-date, you boost its defenses.
5. Utilization of Web Security Firewalls:
Web Security Firewalls (WSFs) assist in detecting and stopping Path Interpolation by scrutinizing HTTP and HTTPS traffic and identifying harmful activity.
6. Intrusion Alert Systems:
Intrusion Alert Systems (IAS) supervise your data network for suspicious behavior, such as Path Interpolation violations, and alert you when these types of action are observed.
7. Cyber Security Education Schemes:
Preparing your staff with awareness about the possible dangers and signs of Path Interpolation incursions can help to prevent such attacks. Frequent cyber security training schemes should be a vital aspect of your digital security routine.
Comparison of Path Interpolation Evasion Techniques:
| Strategy | Description |
|---|---|
| Input Validation | Reviews and confirms user inputs to ensure no harmful sequences. |
| Use of Secure APIs | Utilizes APIs designed to block Path Interpolation. |
| Least Privilege Policy | Limits user access to lower potential damage. |
| Regular Systems Updates and Enhancements | Regularly updates systems to tackle security vulnerabilities. |
| Web Security Firewalls | Observes HTTP/HTTPS channels to spot and counteract hazardous activity. |
| Intrusion Alert Systems | Monitors network for irregular behavior and alerts when detected. |
| Cyber Security Education Plans | Educates personnel about possible hazards and signs of Path Interpolation invasions. |
Ultimately, deterring Path Interpolation attempts necessitates a holistic plan marrying technical responses such as input validation and adoption of secure APIs, with organizational practices such as adhering to the Least Privilege Policy and providing regular security education schemes. Inculcating these strategies will magnify your digital defense mechanisms, safeguarding your systems from Path Interpolation violations.
`
`
Guarding Against Path Navigations: Your Strategy for Amplified Security
Navigating the terrain of network security, the safeguarding from path navigation exploits forms a crucial aspect. These exploits may unveil confidential details, destabilize infrastructures, and lead to considerable monetary and reputational loss. This chapter delivers a detailed roadmap to bolster your digital fortifications against such path navigation exploits.
1. Scrutinizing User Input: Establishing a sturdy defense against path navigation intrusions begins with rigorous scrutiny of user inputs. This process entails verifying and purifying user inputs to ascertain these do not carry harmful scripts. For example, a defined list of permitting inputs can be made, disallowing any input that doesn't comply.
<code class="language-python">import re
def purify_user_input(input):
accepted_input = re.compile('^[a-zA-Z0-9_]*$')
if not accepted_input.match(input):
return False
return True</code>
In this Python code bit, we employ a regular expression to form an allowed list of characters (alphanumeric and underscore). The purify_user_input function verifies the input against the allowed list. If it doesn't match, it returns False, signifying a possibly harmful input.
2. Minimal Privilege Approach: Constrain your applications' rights to only what's necessary for functioning. Therefore, even a malicious actor exploiting a path navigation flaw can inflict limited damage.
3. Adoption of Chroot Jail: Chroot jail offers a method to segregate a process and its descendants from the rest of the system. It alters a process and its descendants' root directory, restricting them to a fraction of the file system.
<code class="language-bash">chroot /new/root /path/to/program</code>
In this bash command, chroot modifies the root directory to /new/root for the program at /path/to/program.
4. Rigid File System Access Regulations: Enforce rigid regulations for file system access. This involves ensuring proper file privileges and utilizing Access Control Lists (ACLs) to regulate access privileges.
5. Employment of Web Application Firewalls (WAFs): WAFs can locate and obstruct path navigation exploits by evaluating HTTP requests and discovering harmful patterns.
| WAF | Path Navigation Protection |
|---|---|
| ModSecurity | Yes |
| Cloudflare | Yes |
| AWS WAF | Yes |
The table above contrasts the path navigation protection capabilities of three renowned WAFs.
6. Consistent System Updates: Consistently update your infrastructures and software. Numerous path navigation exploits stem from obsolete software with recognized vulnerabilities.
7. Security Awareness Development: Cultivate an understanding of the perils and indicators of path navigation exploits among your team. An enlightened team emerges as your most robust shield.
8. Action Plan for Security Breaches: Prepare an action plan for potential security incidents. This plan should encompass procedures to control the breach, evaluate the influence, and recover from it.
9. Periodical Security Evaluation: Undertake regular security evaluations to detect and mend potential flaws. These evaluations may encompass penetration testing, assessment of code, and automated security scans.
Following this roadmap, securing your infrastructure against path navigation attacks can be significantly improved. Bear in mind, prevention outweighs cure, particularly in relation to network security.
如有侵权请联系:admin#unsafe.sh