
2024-2-6 01:58:41 Author: securityboulevard.com(查看原文) 阅读量:22 收藏
In a not-so-surprising turn of events, one of the victims in Okta’s supply chain attack reveals further exploits. Cloudflare recently reported that their entire Atlassian suite – Bitbucket, Jira and Confluence were breached back in November by the same threat actor that breached Okta’s support systems.
In this article we will cover what happened in this breach, and how Astrix can help with such attacks.
Register for the live workshop: How attackers exploit non-human access
A classic case of vendor supply chain attack
Supply chain attacks involve a compromised vendor that’s been breached, and the data stolen is then used to compromise the vendors’ customers. In this case, attackers breached Okta’s support ticket system using a compromised service account. From there the attackers stole HAR files uploaded by Okta’s customers, which contain customers’ credentials.
Cloudflare, being an Okta customer, responded to the initial breach by rotating 5000 exposed credentials. Sadly, their efforts fell short. In an extensive report, Cloudflare describes how a few weeks after the incident, the Okta attackers used two credentials that were not rotated to compromise their Atlassian suite: A token and service account credentials, both belonging to integrations within Cloudflare’s Atlassian environment, and were used to gain administrative access to Cloudflare’s Jira, Confluence and Bitbucket.
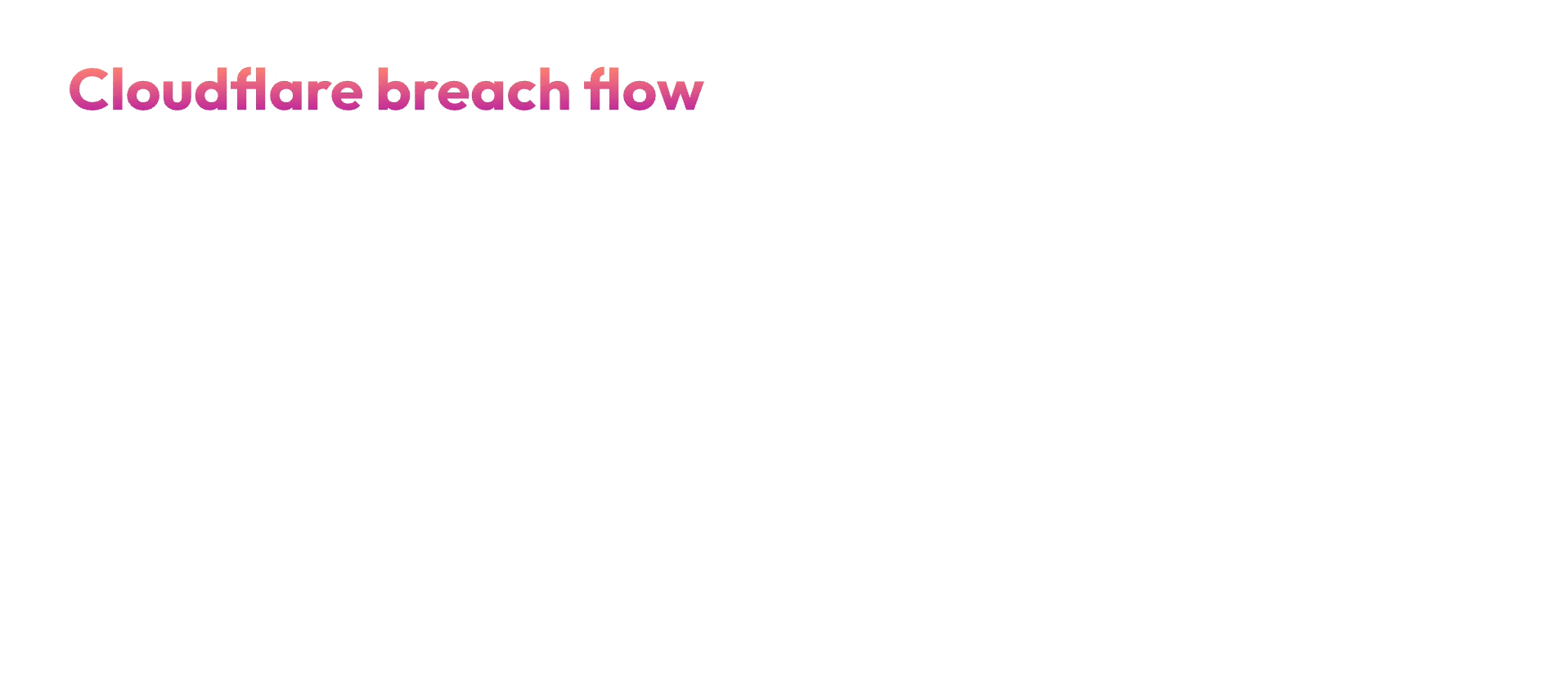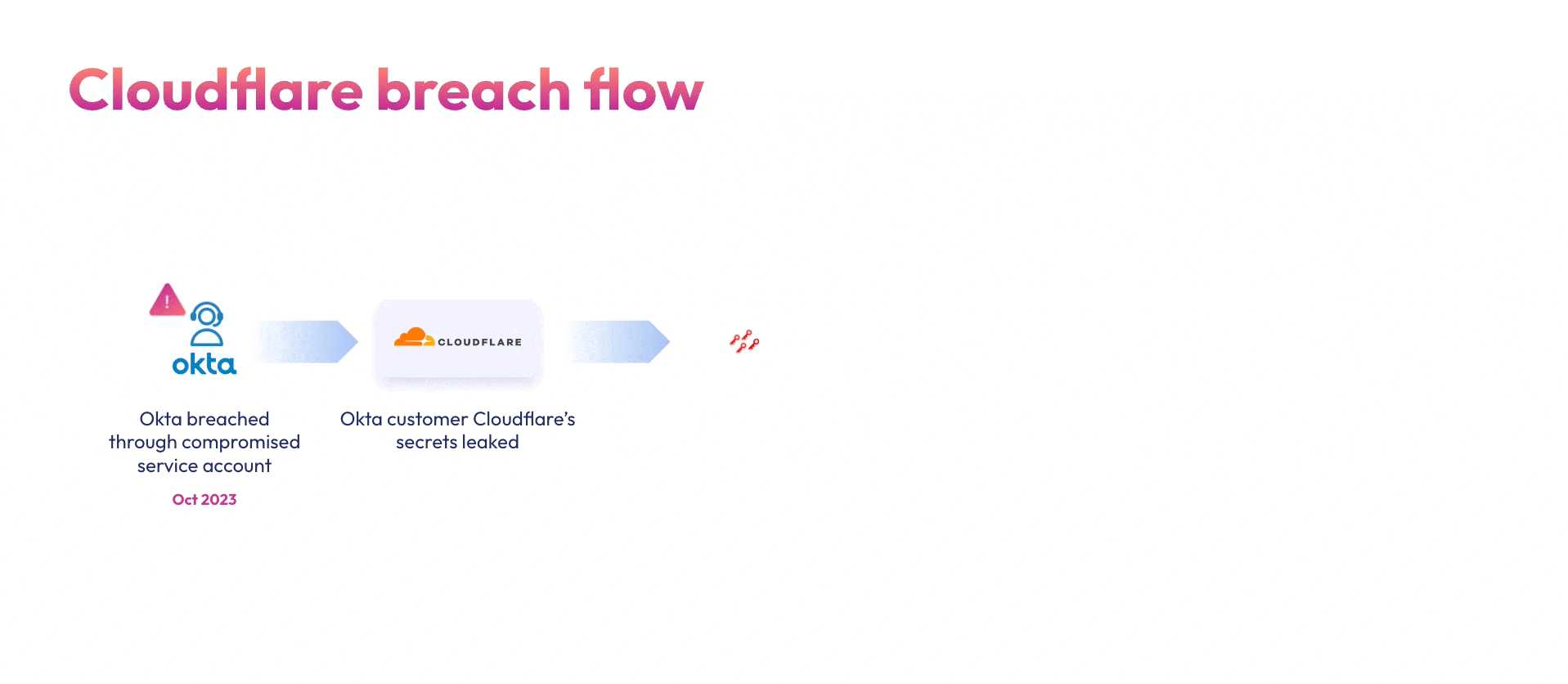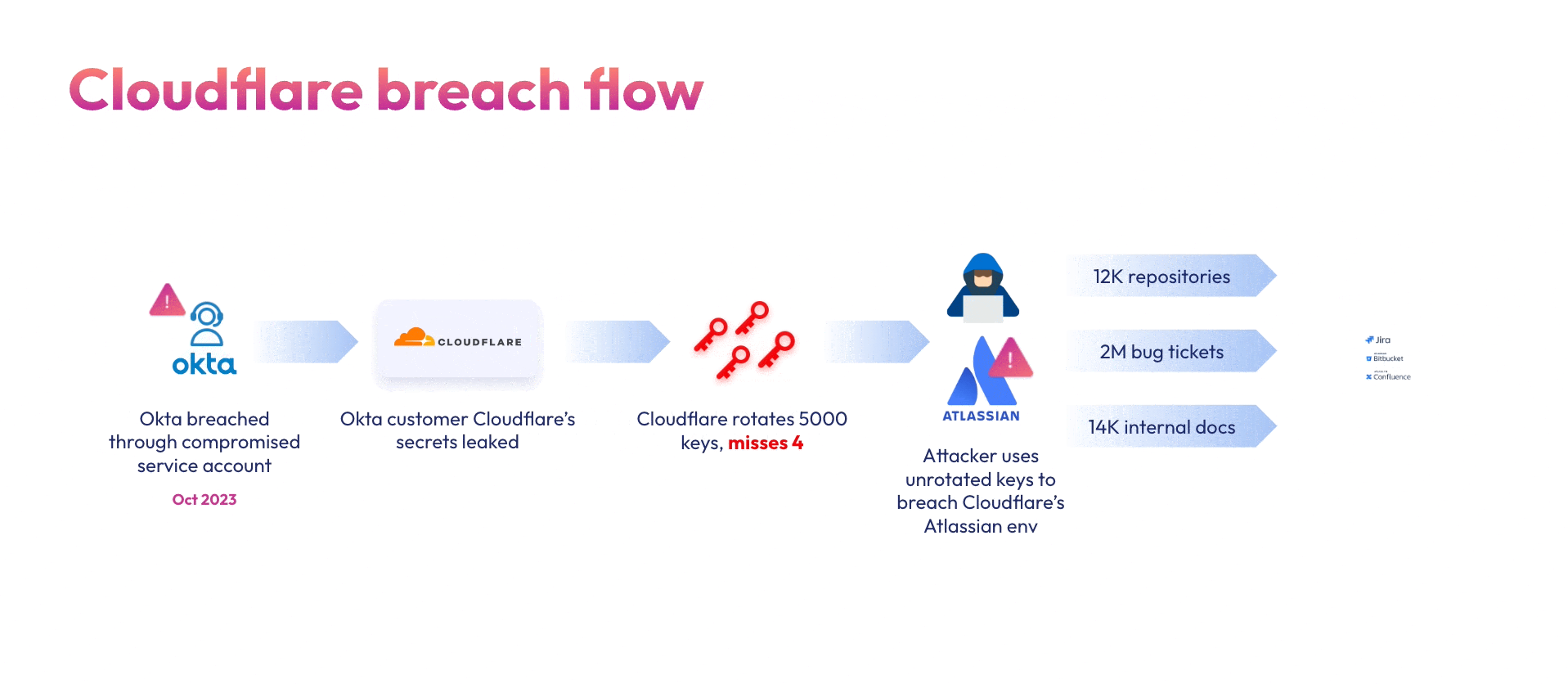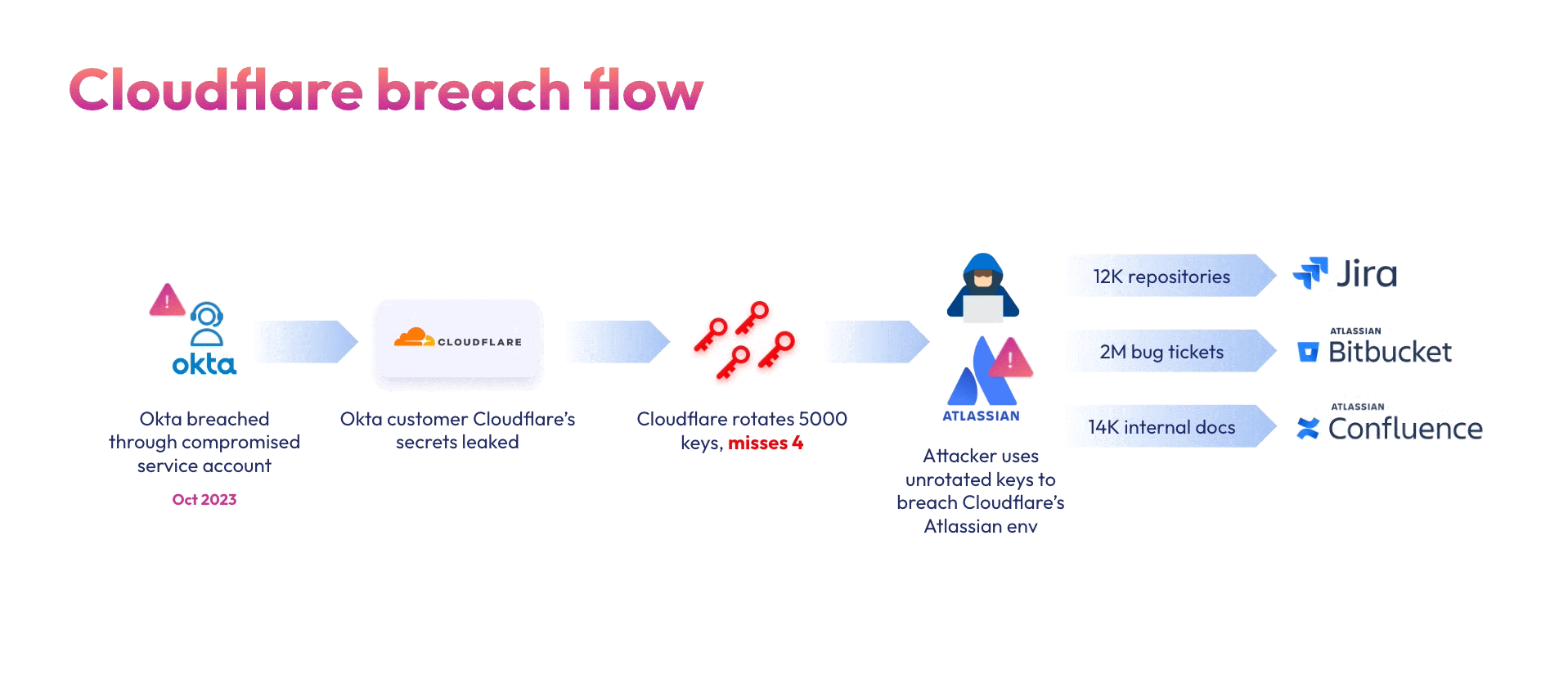
The compromised production Atlassian suite contained Cloudflare’s internal Confluence wiki (14,099 pages), Jira bug tracking (2M tickets) and Bitbucket source code (11,904 repositories), all of which the attackers had access to. Cloudflare shares how the attackers tried using the information about Cloudflare’s internal systems, as well as credentials leaked through production source code to laterally move within their systems into AWS tenants and on-premise servers. Thankfully, Cloudflare’s Zero-Trust policy successfully blocked these efforts.
This is a devastating attack on one of the largest SaaS companies, and severely highlights the risks of supply chain attacks. Although not initially their fault, Cloudflare’s most sensitive data was leaked.
In this attack, we see again how attackers abuse non-human access, which usually goes unmonitored, to achieve high privilege access to internal systems. Another noteworthy point is that the attackers targeted Cloud, SaaS and also on-prem solutions to expand their access. This emphasizes the growing need for a holistic approach to securing non-human identities across the entire organization.
How Astrix could have helped prevent the Cloudflare exploit
As part of the IR efforts after the Okta breach, the Cloudflare security team worked extensively to identify and rotate all compromised credentials. Alas, they missed 4 credentials – one access token and three service accounts credentials, which the threat actors used to exfiltrate Cloudflare’s Atalssian environments. Cloudflare mentions in their report that their existing solutions failed to find these unrotated credentials, which is a testament to our age-old saying – current solutions are simply not built for NHI threats.
So here is how Astrix can help with such supply chain exploits:
- Inventory. One of the most challenging things to do after a breach is to discover and inventory all the non-human access credentials that were provided to the breached third-party (Okta in this case). This is something we’ve seen before in different attack scenarios like the CircleCI and SumoLogic breaches, where it took companies more than a year to find and rotate all the compromised vendor’s credentials. In this case, Cloudflare, while trying to rotate all 5000 keys and service accounts, missed 4 of them – and that’s all it takes. The Astrix platform is able to identify and correlate non-human identities that are used by a specific third party, even if it’s not a marketplace or a “known” application. The identification is based on static and dynamic metadata. This correlation allows SOC teams to easily find all compromised credentials with a click of a button.
- Behavior analysis. Flagging anomalous behavior of access tokens can help SOC teams understand there is a potential exploit before it is too late. Astrix’s behavior analysis monitors the activity of all access tokens and flags suspicious behavior based on different parameters such as IP, user agent, actions etc. In Cloudflrae’s case, the abused service account credentials and integration access token were used from foreign IPs, and behaved in a suspicious manner (such as scanning the entire Confluence wiki and Bitbucket source code). Astrix would have flagged this as an anomalous event, allowing the SOC team to realize something bad is happening earlier on. Additionally, Astrix would have helped identify the attacker’s IP addresses so that the security team could quickly block them through the firewall – something that took Cloudflare many hours to achieve.
- Secret protection. Another impossible mission that the Cloudflare team most probably spent a huge amount of time on, is trying to find and rotate every secret that might have been exposed. Finding an exposed secret, understanding what it’s connected to, and not less importantly – understanding the consequences of rotating it, is a huge undertaking for security teams. Astrix’s secret security capabilities help security teams not only find exposed secrets, but also provide the complete context necessary to handle each secret – the secret owners, connected services, usage, risk severity and more. This would have helped the Cloudflare team to instantly find all the secrets in the HAR files and correlate them with the exposed connections that are related to Okta’s services, as well as get all the necessary context to be able to quickly rotate them without breaking anything. Using Astrix’s automated workflows, the security team could have rotated the exposed secrets in no time.
To chat with our security experts on how we can help you, schedule a time with us.
The post Breach analysis: Cloudflare falls victim to Okta attack appeared first on Astrix Security.
*** This is a Security Bloggers Network syndicated blog from Astrix Security authored by Danielle Guetta. Read the original post at: https://astrix.security/breach-analysis-cloudflare-falls-victim-to-okta-attack/
如有侵权请联系:admin#unsafe.sh
