The latest update to iOS Forensic Toolkit brought t 2024-2-1 14:59:18 Author: blog.elcomsoft.com(查看原文) 阅读量:17 收藏
The latest update to iOS Forensic Toolkit brought the ability to mount HFS disk images extracted from legacy Apple devices as drive letters on Windows systems. This new capability to mount HFS images on Windows empowers experts to efficiently process and analyze digital evidence extracted from legacy Apple devices on Windows-based computers. This article provides detailed instructions on using the new feature.
Why HFS images?
When performing low-level extraction of legacy Apple devices built with 32-bit architecture, iOS Forensic Toolkit employs a forensically sound process called perfect HFS acquisition. During this process (which is only available if you are using a Mac or Linux edition of iOS Forensic Toolkit), the tool produces a full, bit-precise image of the data partition. The image can be decrypted by using the keys that are also extracted during the process.
These older devices use HFS as a file system. While mounting HFS images in macOS can be done seamlessly, Windows does not support such disk images or even recognize HFS as a file system. The integration of HFS support into Windows requires a custom implementation of a fused file system, which we are now supplying as a licensed version of WinFsp runtime. Notably, WinFsp is not a ready-made tool that would allow mounting a disk image via a graphical user interface; instead, it is a set of free open-source libraries for mounting filesystems on Windows that had to be integrated into iOS Forensic Toolkit to work. While it’s primarily used for non-commercial purposes, a license is required for commercial products, which we have obtained for our toolkit. WinFsp’s installer is now supplied with our software, enabling users to easily utilize the mounting feature on Windows. However, if WinFsp is not installed, this feature will not work. To install WinFsp, launch its installer from the folder where EIFT is installed. Note that the feature is native on macOS and is also available in the Linux edition via FUSE (requires libfuse dependence).
Mounting DMG files on Windows serves several purposes. First, many commonly used forensic tools are incompatible with DMG files, but can easily work with extracted folders instead. This makes it simpler to manually explore and analyze the contents of DMG files, checking various databases and settings within the extracted folders. Third-party commercial tools such as Paragon HFS+ for Windows, HFSExplorer, and DMGExtractor are available, offering alternative solutions for handling HFS files on Windows systems.
Overall, while DMG files can only be created on macOS (and Linux), the ability to analyze them using various tools, including UFED, is now greatly simplified.
Forensically sound read-only mounting
iOS Forensic Toolkit mounts HFS images in read-only mode, which is the only forensically sound mode. While read-only is the safest mode, you may experience some hiccups when using certain tools such as some SQLite editors to examine SQLite databases found in the file system. Some of such tools will fail to open a SQLite database as they will try creating temporary files alongside with the main database, and fail due to read-only mode. If you need to use such tools, we strongly recommend copying the files off the mounted disk image to your computer and opening them there; otherwise one would inevitably modify the original disk image and thus accidentally tamper with evidence.
Walkthrough
You will have two options when mounting HFS images with iOS Forensic Toolkit. The first option mounts the original, encrypted image; the second mounts the already decrypted image.
To mount the original, encrypted disk image use the following command:
eift_cmd hfstool --mount -i data.dmg -k keys.plist
Note that you will need to provide the full path to both the DMG file and the keys unless you are running the command from the same folder where they are located. Please refer to Perfect Acquisition Part 4: The Practical Part for more information about the disk images, encryption keys, and decryption process.
To mount an already decrypted image use the following command:
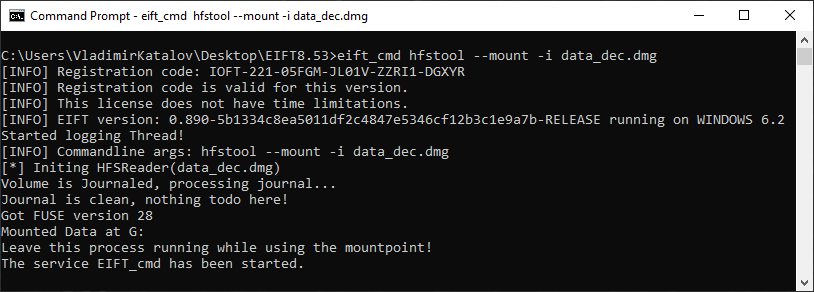
eift_cmd hfstool --mount -i data_dec.dmg
Once you execute one of the two commands, a console window will open:
Do not close this window while working with the mounted image. Closing iOS Forensic Toolkit will automatically dismount the disk image.
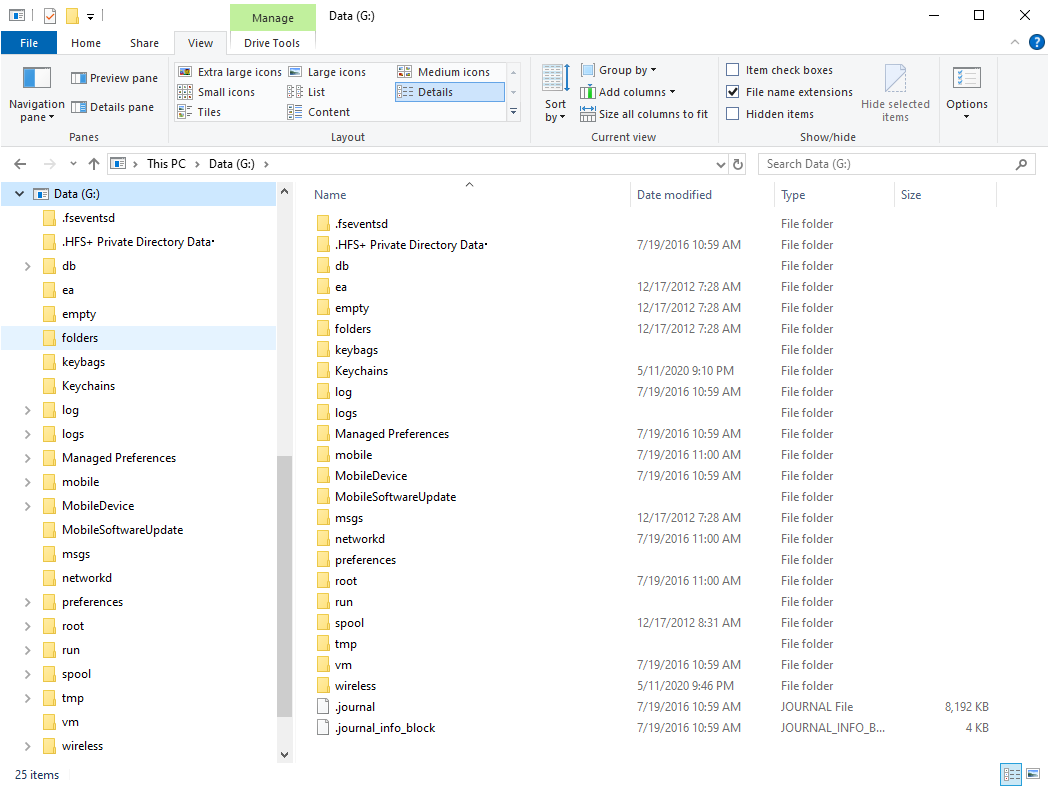
The file system will be mounted as a first available drive letter:
At this point, you can manually examine the content of the file system.
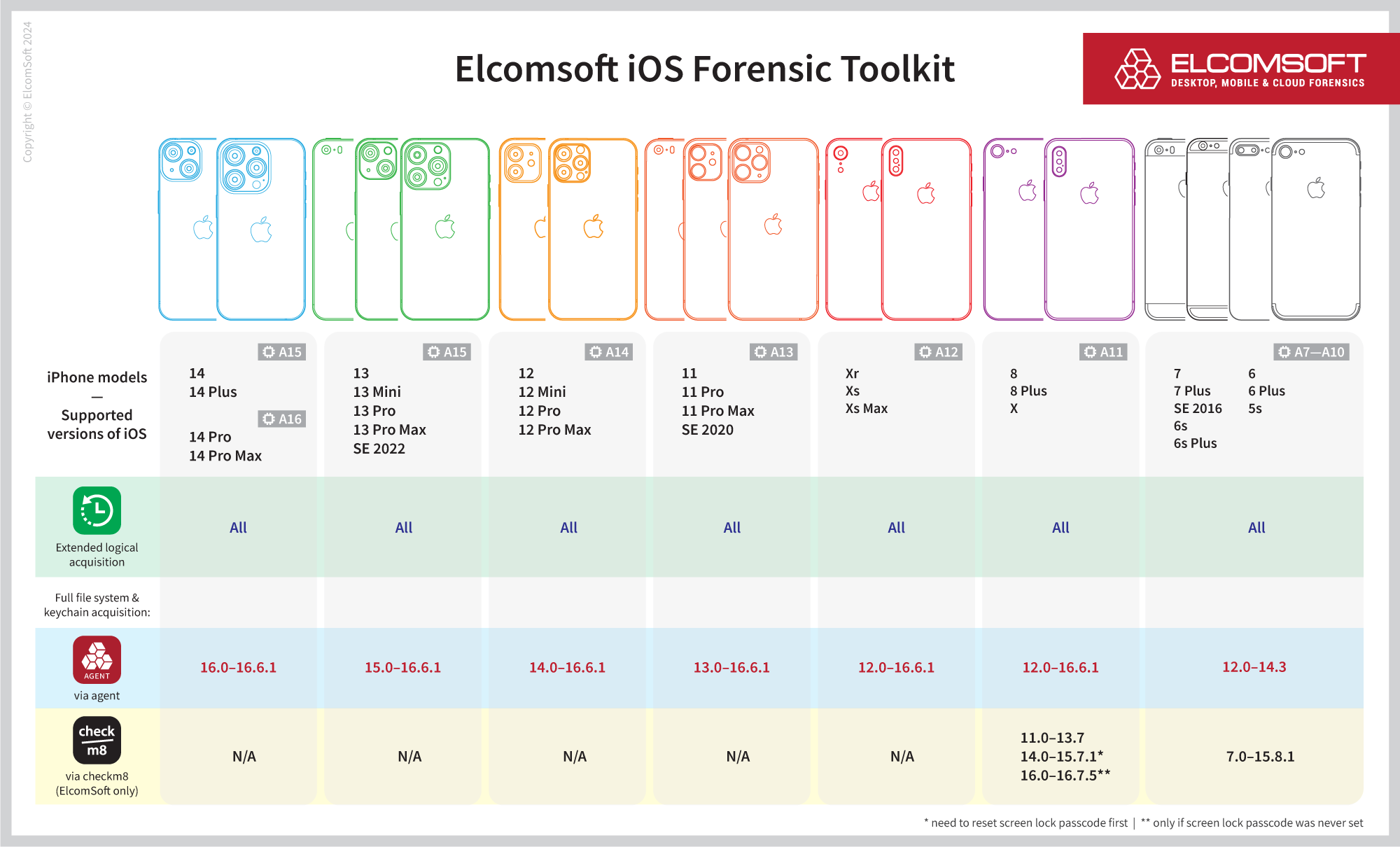
Compatibility
The current version of iOS Forensic Toolkit supports the following devices/OS versions (please note: HFS imaging/mounting is not supported on any devices listed in the table below).
Conclusion
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh