On 24 January 2024, the Jenkins team issued a security advisory disclosing a critical vulnerability that affects the Jenkins CI/CD tool. Jenkins is a Java-based open-source automation server run by over 1 million users that helps developers build, test and deploy applications, enabling continuous integration and continuous delivery.
The critical vulnerability is tracked as CVE-2024-23897 and affects Jenkins 2.441 and earlier. LTS 2.426.2 and earlier does not disable a feature of its CLI command parser that replaces the ‘@’ character followed by a file path in an argument with the file’s contents, allowing unauthenticated attackers to read arbitrary files on the Jenkins controller file system that can lead to RCE.
According to security researchers from ShadowServer, there are approximately 45,000 unpatched Jenkins instances, most of which are in China (12,000) and the United States (11,830).
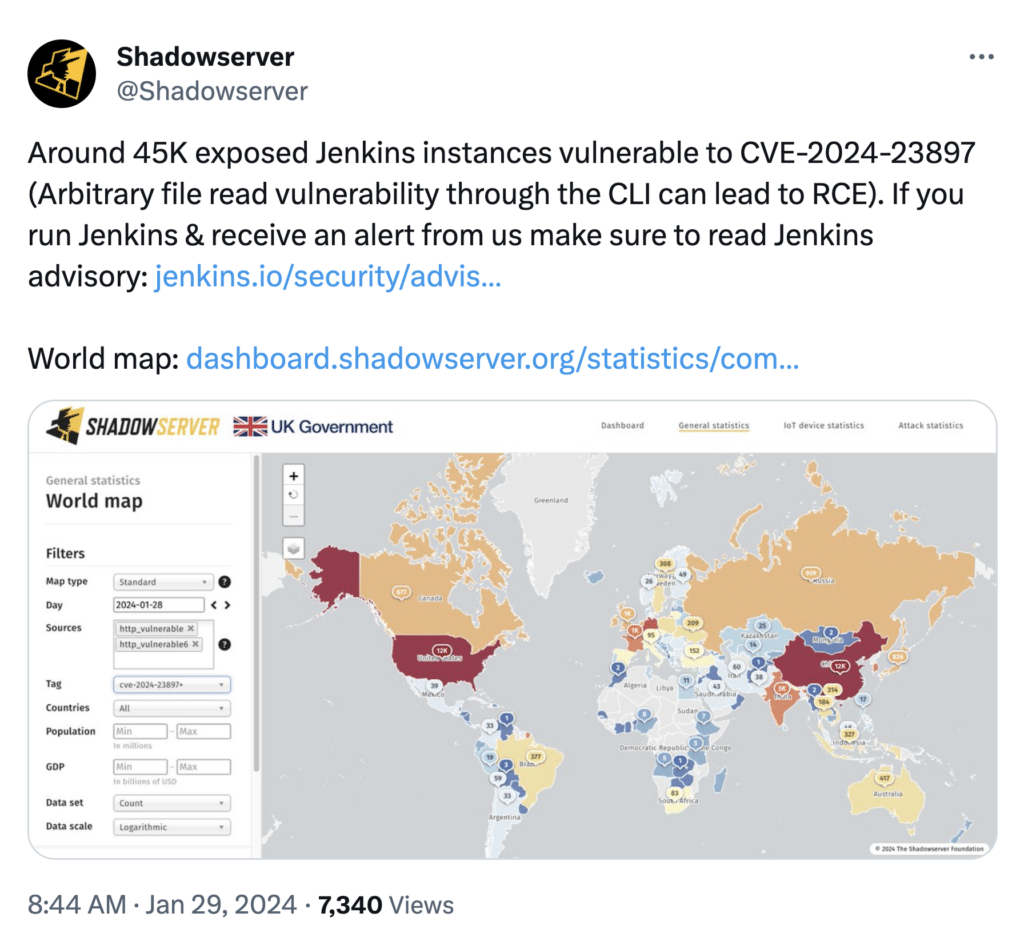
Two Proof of Concepts (PoCs) exploits have been released to the public and could be leveraged by attackers to compromise unpatched Jenkins servers. According to the Cyber Security Agency (CSA) of Singapore, as of 30 January 2024, the vulnerability is reportedly being actively exploited.
Who Is Affected?
Anyone who is running Jenkins 2.441 and earlier is affected by this vulnerability.
How Can I Fix It?
Jenkins users are urged to upgrade to Jenkins 2.442 and LTS 2.426.3.
How Can NodeZero Help?
All NodeZero™️ users can run an autonomous pentest to determine if their systems are vulnerable to the Jenkins vulnerability. We also recommend running a follow-on pentest to verify that any remediation steps taken, such as patching, are effective.
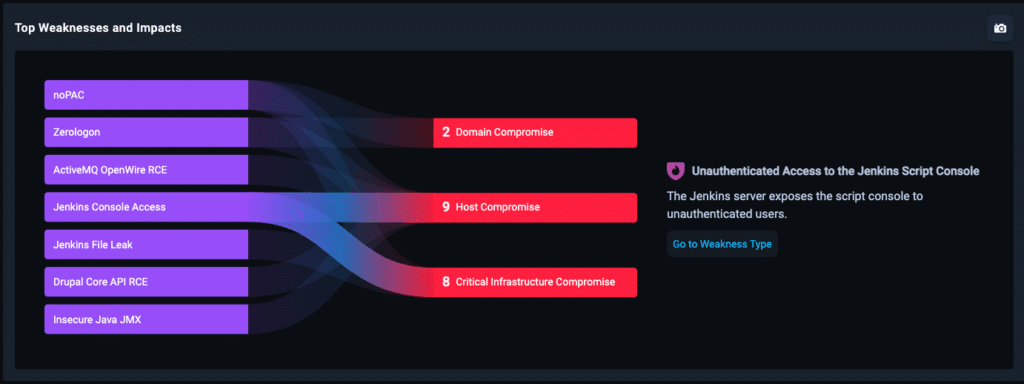
Example Top Weaknesses and Impacts:
Example Attack Path:
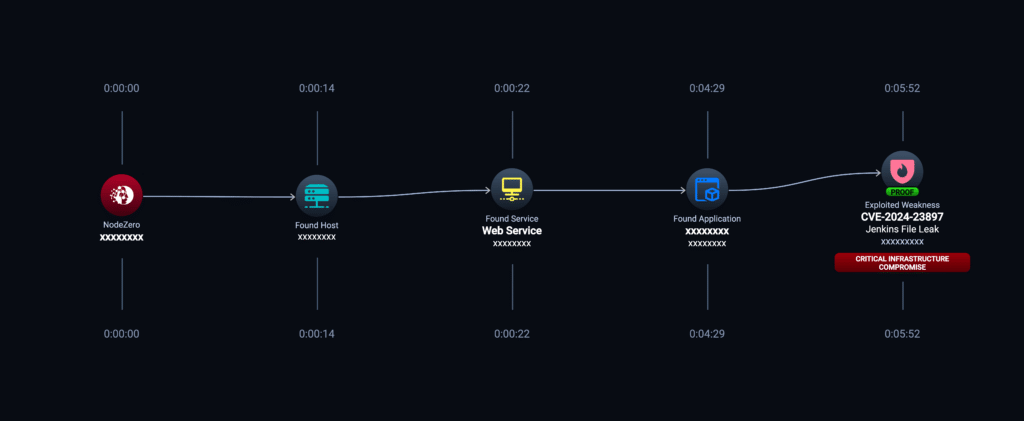
If you want to read more, please read Horizon3.ai’s Attack Team’s blog titled, “CVE-2024-23897: Assessing the Impact of the Jenkins Arbitrary File Leak Vulnerability.”
The post CVE-2024-23897: Check Critical Jenkins Arbitrary File Like Vulnerability Now! appeared first on Horizon3.ai.
*** This is a Security Bloggers Network syndicated blog from Horizon3.ai authored by Corey Sinclair. Read the original post at: https://www.horizon3.ai/cve-2024-23897-check-critical-jenkins-arbitrary-file-like-vulnerability-now/
