2024-1-19 18:59:59 Author: www.tenable.com(查看原文) 阅读量:9 收藏
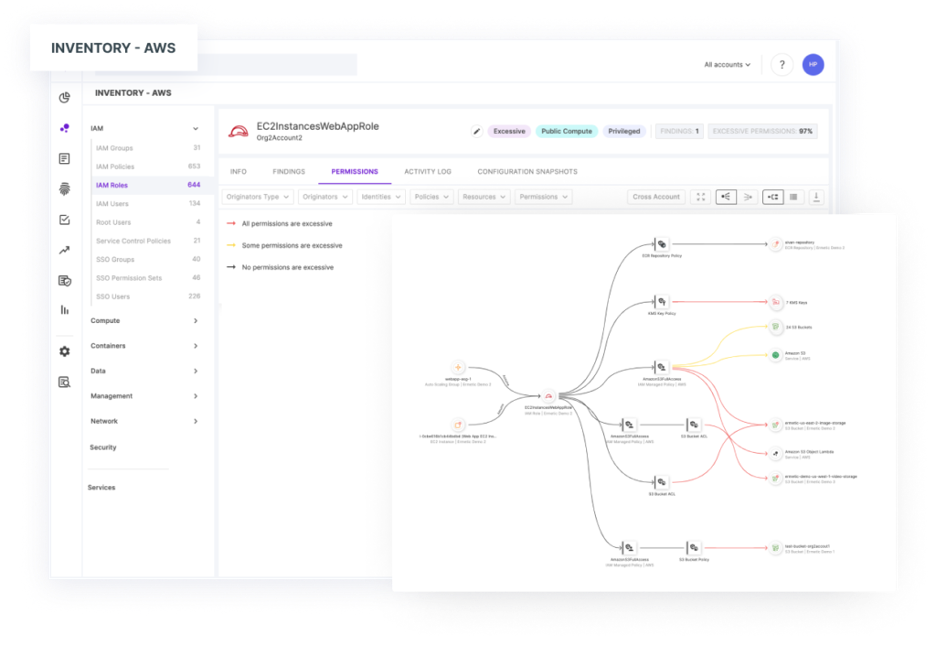
Tenable Cloud Security enriches cloud activity log data to give you the context you need to quickly respond to and remediate cloud risks.
In 2023, it took organizations an average of 204 days to identify a breach, according to the IBM Cost of a Data Breach Report 2023. Perhaps of equal concern: 82% of breaches involved data stored in the cloud. The average total cost of a data breach increased 2.8% in 2023 to $4.45 million.
With so many tools at their disposal, you might wonder why security teams continue to struggle with detection and response times.
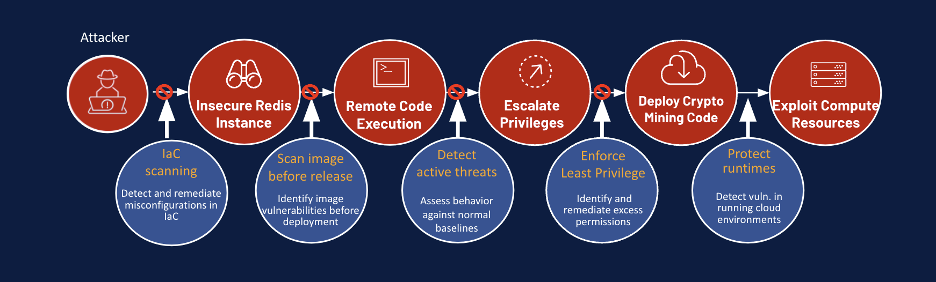
Let’s take a real-life cloud scenario. An organization found that its cloud costs had gone up quickly, without any discernible reason why. As a result, the company started to wonder if it had been breached. A security investigation revealed that the DevOps team had accidentally created an over-privileged Amazon Machine Image (AMI) on a public IP. The privileges were included as part of the DevOps team’s template, so that every time a new AMI was spun up, it was creating an over-privileged and vulnerable instance.
By gaining access to the server, attackers could leverage excessive privileges to run a cryptominer, benefiting from the free compute services, while the attacked entity was charged for the expensive compute utilization.
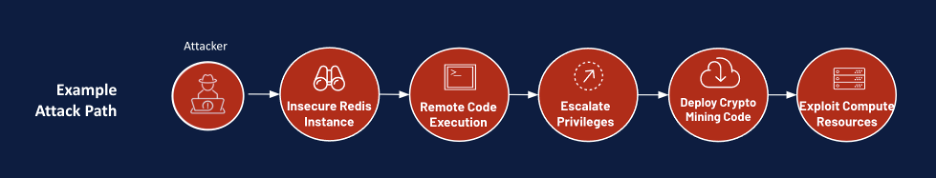
Why wasn’t this breach identified sooner? Traditional security methods failed because the machine logs gave no indication of this misconfiguration on their own. Only a more in-depth investigation could identify and contain the issue in a reactive manner. Several challenges contributed to the delayed detection. Due to costs, detailed data collection that includes management logs, relational database service (RDS) logs and data events are not always collected. Furthermore, even when the data is collected, it can be challenging for incident response teams that lack deep cloud expertise to decipher what it means and where the potential risks are.
Four cloud incident response challenges
Let’s explore why cloud incident detection and response can be so challenging.
1. Gaps in log data
In traditional on-prem infrastructure directly owned and controlled by an organization, robust log data is pretty much at your fingertips. In the cloud, the infrastructure is owned by the Cloud Service Provider (CSP). An incident response team’s ability to investigate attacks is therefore dependent on what data is being collected by the CSP. This is made more challenging by the fact that each CSP has its own defaults and nuances for data collection, which not only can impact what data is collected, but also the cost to access that data and the length of time that data is retained. Without expertise in the details of each CSP’s default settings and an understanding of their unique differences in data capture and retention policies, incident response teams can be left with serious gaps in data, hampering investigation and remediation efforts.
2. Dynamic cloud architectures
Cloud native architectures with microservices, containers and Kubernetes are increasingly the norm. More importantly, they have many more moving parts than traditional virtual machines, making them highly complex. They are also highly distributed and ephemeral in nature, dynamically scaled as resources are needed. The volume of parts and the fact that they are ever-changing, makes it difficult for incident response teams to assess how an attacker may have gained initial access, and what changes they may have made over time — especially if data is only retained for a specific, and limited period of time. Therefore, if an incident is not detected early, accessing the data needed to investigate incidents may be difficult or impossible.
3. Limited asset context
Security teams often have zero or near-zero visibility into the configurations and relationships of cloud assets. This lack of contextual visibility makes it challenging to identify the potential steps that may have been taken by a bad actor to execute a successful attack path. Imagine the police investigating a home burglary without visibility into the layout of internal rooms or the location of the windows and doors of the house. That’s the reality facing security teams in the cloud when analyzing cloud logs.
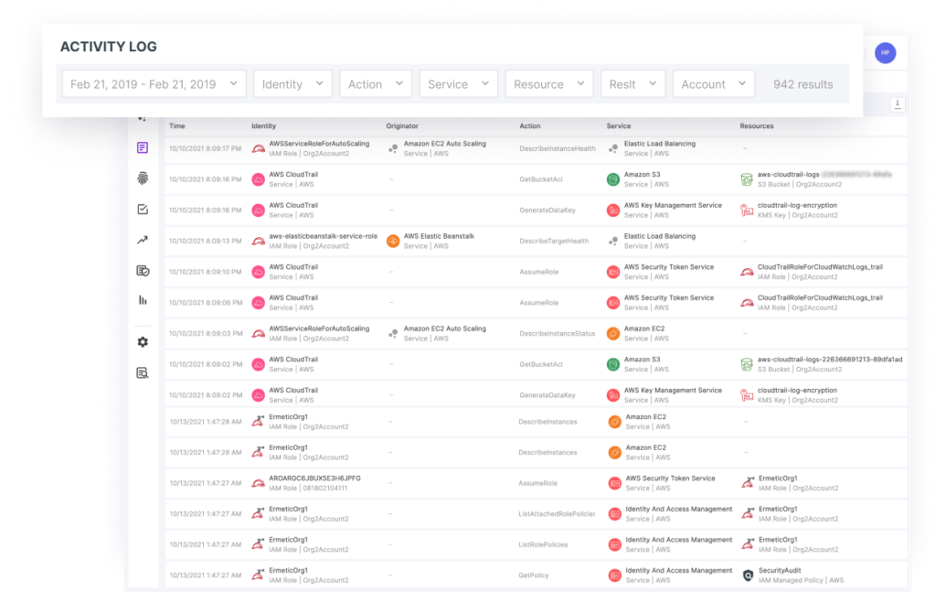
Source: Tenable, January 2024
4. Insufficient insight into privileges
In the cloud, identities and privileges are the new perimeter. And identities are not just limited to people. Machine identities in the cloud can greatly outnumber the volume of human identities. For an attacker, human or machine identity makes little difference. With thousands of digital identities and credentials in cloud environments, it is easy to overlook a weakness an attacker can exploit to access or modify infrastructure. Without an understanding of identities and privileges, the task of understanding the domino chain of events leading to a successful breach can seem impossible.
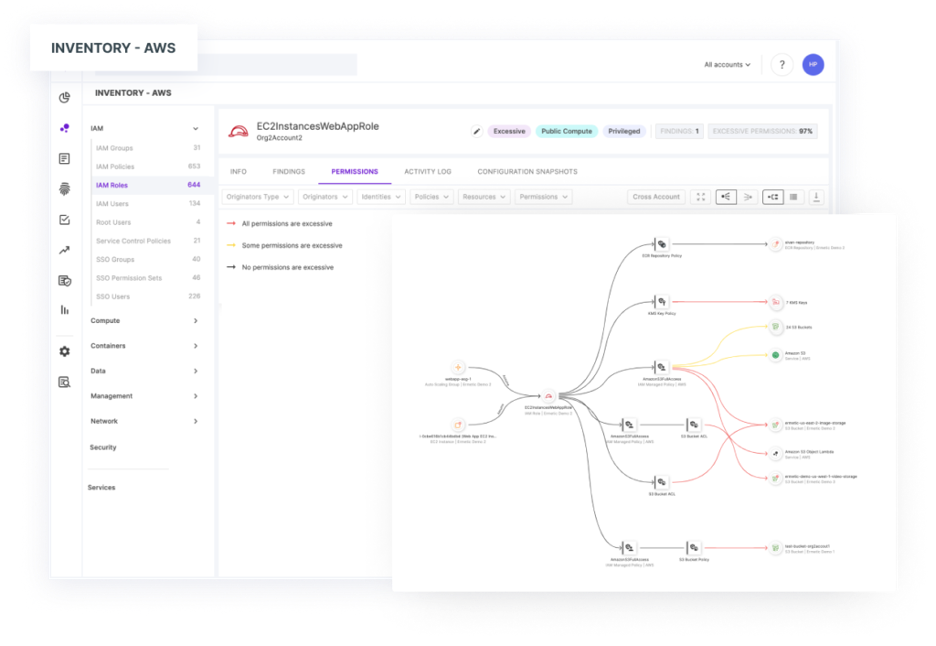
Source: Tenable, January 2024
5. Alert fatigue
Alert fatigue is both a challenge and an outcome of the issues discussed above. The function of logs is to collect data and maintain a record. But data alone is of little value if it is overwhelming. Not all data or activity is relevant. Nor is it malicious. And this is perhaps the biggest challenge for security teams. Many tools have static policies to identify categories of suspicious activity which can result in false alarms when there’s no established baseline for normal vs. abnormal activity to weed out alert noise. But baselines alone are not enough to eliminate noise if we do not understand the relationships between upstream and downstream assets and identities and the privileges that facilitate lateral movement.
What’s needed for better incident response?
Security teams seeking to improve their anomaly detection and incident response need an integrated approach that can address gaps in their incident response data and processes. This starts with centralized visibility across multi-cloud environments. A detailed inventory of assets and identities — including modern cloud architectures such as containers and Kubernetes as well as people and machine identities — lays the foundation for identifying all possible targets and entry points in the attack surface. Mapping of assets and identity relationships, including privileges, provides a contextual understanding of feasible attack paths that may be taken. With this deeper context, it is possible to establish better baselines into normal and abnormal behavior, enrich log data, and significantly reduce alert noise by aggregating and contextualizing related alerts.
Cloud Native Application Protection Platforms (CNAPP) like Tenable Cloud Security enrich cloud activity logs with resource-specific identity threat data. Tenable Cloud Security provides continuous risk analysis that checks for anomalies against behavioral baselines. To accelerate anomaly detection and incident response Tenable Cloud Security taps into a cloud's inner logs to analyze all activity in the environment. By providing insights into escalated privileges, changes to network configuration and unauthorized use or theft of access keys, Tenable Cloud Security speeds anomaly detection and response by giving users contextualized and actionable information.
For more information on how Tenable can enrich CSP data with relevant information, check out our open source tool, AWS Access Undenied or Tenable Cloud Security.
Learn more
- Read the blogs: Beyond the Horizon: Top 5 Cloud Security Trends to Watch in 2024 and Learning to Love Audit and Compliance: It’s Possible
- Visit the Tenable Cloud Security product page to learn more or request a demo: https://www.tenable.com/products/tenable-cloud-security

Pierre Coyne
Pierre Coyne, Tenable's Director of Product Marketing, Cloud Security, is a marketing leader with more than 25 years of experience driving go-to-market (GTM) strategy for rapid growth markets in the high-tech industry, including cloud security, cybersecurity, hybrid cloud, containers and Kubernetes. As a subject matter expert, Pierre develops thought leadership content and best practices to help CIOs, CISOs, security leaders and practitioners improve visibility into cyber risk posture, apply technology to optimize value and retention of skilled resources, and reduce CapEx and OpEx through new efficiencies. Prior to joining Tenable, Pierre held leadership positions at IBM driving GTM for its'multi-billion dollar hybrid multicloud platform. He has also held related roles at other tech innovators, including CA, Platinum Technologies, Armis, Micromuse, RiverSoft, Memco and Cheyenne Software.
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh