
2024-1-18 18:59:59 Author: www.tenable.com(查看原文) 阅读量:19 收藏

The new capability is designed to make it more efficient for security teams to pass remediation recommendations on to the infrastructure team to implement. Here’s how it works.
What often determines how quickly a security issue is remediated (if at all) is the efficiency with which the security team can generate the finding and provide guidance to the infrastructure team on the proposed remediation.
This is because the security team responsible for determining whether or not there’s a security issue is usually focused on different goals than the infrastructure team responsible for environment availability and administration. While the security team wants any security issue to be repaired, the infrastructure team is often (and very justifiably) focused on ensuring that the remediation doesn’t cause more damage and that the infrastructure can continue supporting the required business logic. The infrastructure team, therefore, is very careful in applying any changes — especially to a production environment. Production has the most sensitive resources, as well as the resources that need to be most available, making it essential for teams to perform remediation responsibly without breaking anything.
Our understanding of these unique operational challenges facing cloud security teams was a major driver in our efforts to enhance the Tenable Cloud Security user experience with the ability to generate pull requests for remediation suggestions.
Tenable Cloud Security integrates with infrastructure-as-code repositories by allowing workflows to retrieve and send relevant information from state files to its API, as such:
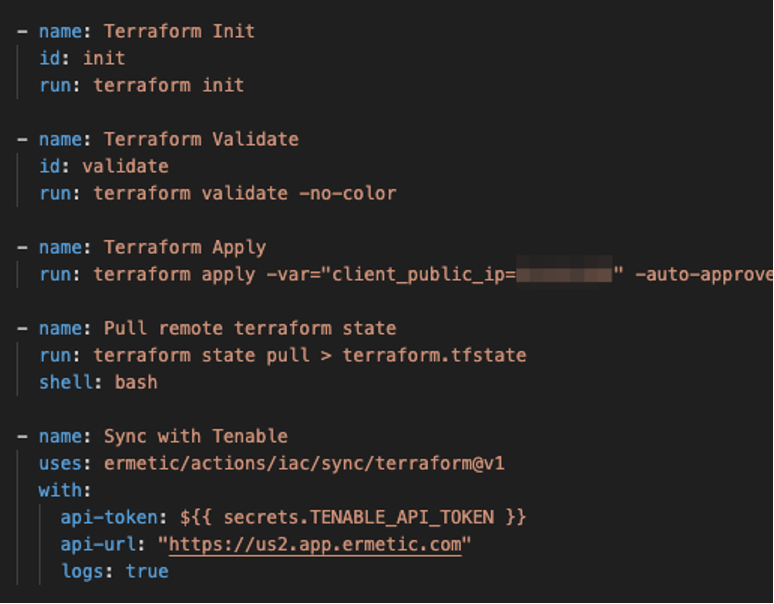
In Figure 1, we can see an example of a GitHub Actions workflow where Terraform state files are being retrieved as part of the provisioning process and then sent to the Tenable Cloud Security API.
Processing the state files allows Tenable to map the resources it scans for misconfigurations and other security-related findings to the line of code that provisioned them. As an important note, we don’t take state files as is in their entirety, but only within the parameters needed to perform this task.
An example of the end result of this operation can be seen below:
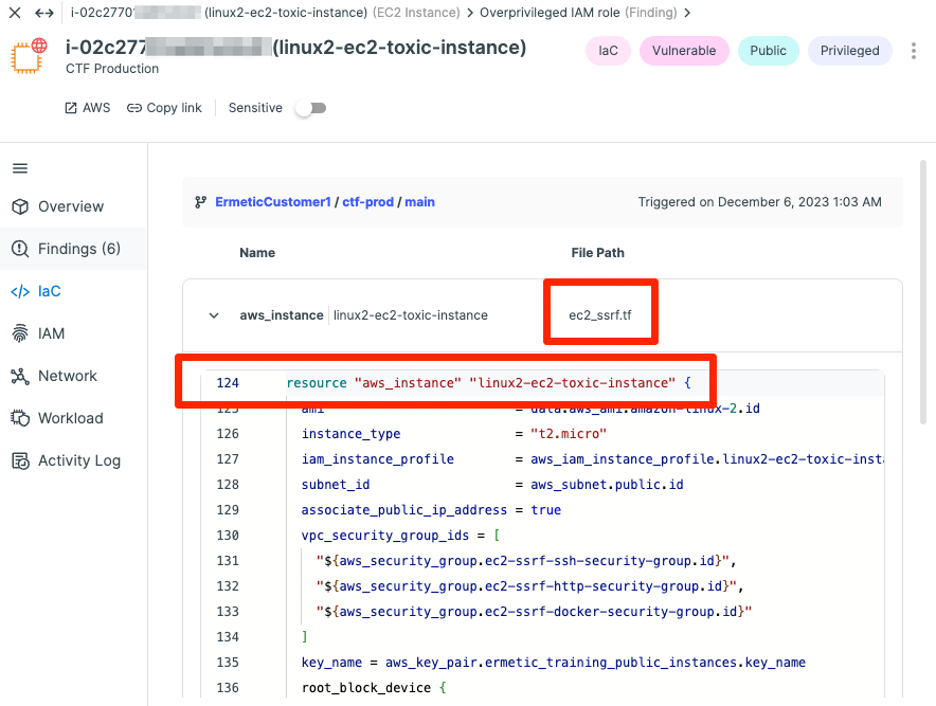
We dub this cutting-edge ability “cloud-to-code,” as it creates an invaluable connection between security findings that can sometimes only be detected once the resource is already provisioned and running to the code.
One such finding is over-privileged identity and access management (IAM) roles — you can identify an IAM role by analyzing its actual activity and detecting discrepancies between what it’s allowed to do and what it actually utilizes. This is, of course, not something that can be done before the resource is up and running.
Tenable Cloud Security, as a pioneer in right-sizing permissions, happens to perform this kind of analysis, and, even better, it not only indicates if an IAM role is over-privileged, it also produces a right-sized policy for it, as can be seen in Figure 3:
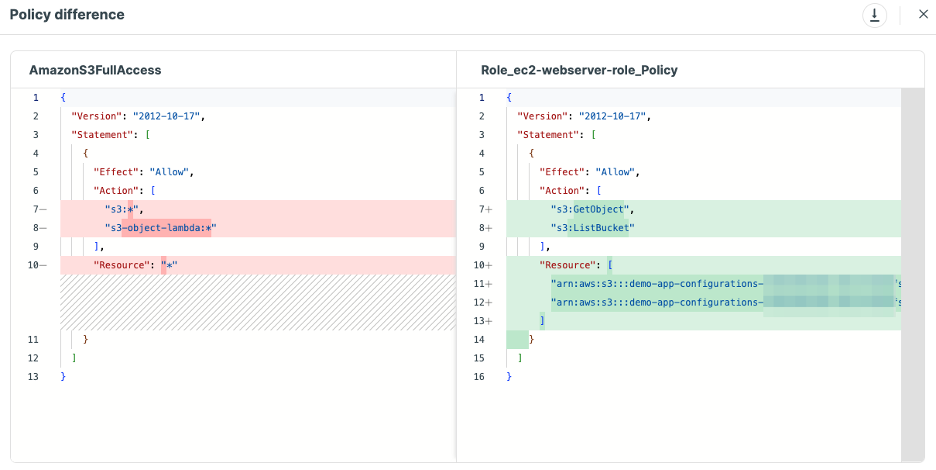
Now here’s the fun part: leveraging cloud-to-code and an integration with the code repository itself, Tenable Cloud Security now supports creating a pull request directly from the console, allowing the security team using it to easily suggest modifications to the infrastructure to make it more secure.
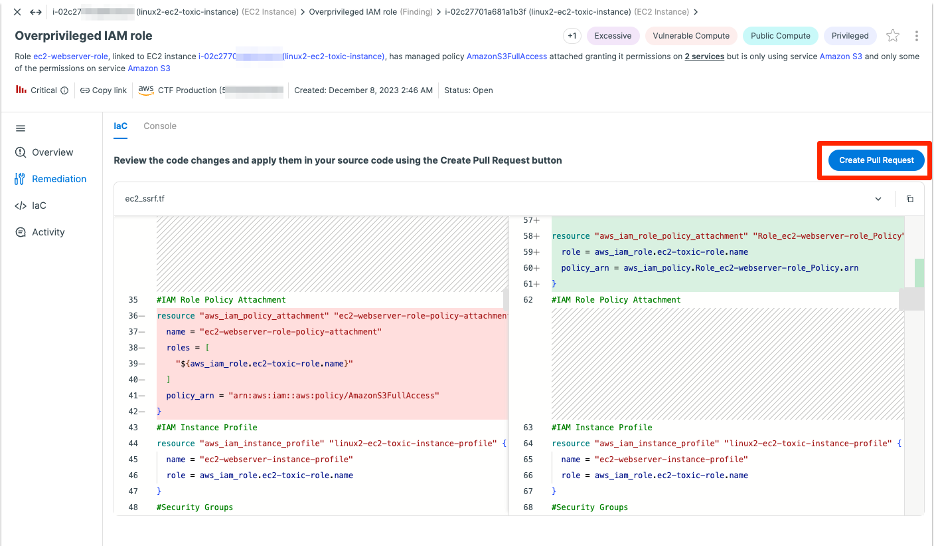
So what does this mean? In order to actually apply the change, the infrastructure team needs to simply review (and hopefully test) the modification. Once it’s approved, they can push it to production.
This is arguably the most effective method of communication between security and infrastructure teams around the remediation of findings; it’s safe, fast, accurate — and requires very little specialized expertise to be applied.
Want to learn more about Tenable Cloud Security or request a demo? Visit https://www.tenable.com/products/tenable-cloud-security

Lior Zatlavi
Lior Zatlavi has more than 15 years of experience in cyber security, with most of that time as a security architect, product manager and developer for the Israeli government. Lior served in an elite cyber security unit of the Israel Defense Forces (retired with the rank of Major), after which he worked in a cyber security division of Israel's Prime Minister's Office. After leaving the public sector, Lior worked as an independent consultant, specializing in cloud security and identity management. Lior holds an M.Sc in Electrical Engineering from Tel Aviv University and a B.Sc in Applied Mathematics (cum laude) from Bar Ilan University, Israel.
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh