2024-1-18 04:22:23 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
Author:
Kaustubh Jagtap, Product Marketing Director, SafeBreach
On January 16th, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued an urgent advisory to highlight the ongoing malicious activities by threat actors deploying the Androxgh0st Malware. Detailed information about these activities and the associated indicators of compromise (IOCs) and the various tactics, techniques, and procedures (TTPs) is listed in Known Indicators of Compromise Associated with Androxgh0st Malware. According to the advisory, unknown threat actors have leveraged the Androxgh0st malware for its ability to establish a botnet to identify further potential victims and compromise their networks.
Technical Details
Researchers first came across the Androxgh0st malware in December 2022 when it was used in several campaigns to steal credentials. Androxgh0st malware is a python-scripted malware that has been used to target the “.env” files containing sensitive data such as credentials for high-profile applications like Amazon Web Services (AWS), MS Office 365, SendGrid, and Twilio (from the Laravel web application framework. It is also believed that Androxgh0st malware can support several other functions that can abuse the Simple Mail Transfer Protocol (SMTP), including scanning, exploiting exposed credentials and application programming interfaces (APIs), and deploying web shells.
Targeting the PHPUnit – TTPs involved during an Androxgh0st malware attack on vulnerable PHP servers typically include the use of scripts to scan and search for websites with specific vulnerabilities. Threat actors have been observed exploiting CVE-2017-9841 which allows them to remotely run PHP code on vulnerable sites via PHPUnit. Websites using the PHPUnit module that have internet-accessible (exposed) /vendor folders are subject to malicious HTTP POST requests to the /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php uniform resource identifier (URI). This PHP page runs PHP code submitted through a POST request, which allows the threat actors to remotely execute code. Any threat actor leveraging the Androxgh0st malware can download malicious files to the system hosting the vulnerable website. They can even set up a fake page accessible via the uniform resource identifier (URI) to then access the website allowing them to further download malicious files.
Targeting the Laravel Framework – Threat actors have also been observed leveraging Androxgh0st malware to establish a botnet to scan for websites that use the Laravel web application framework. After identifying such websites, threat actors attempt to determine if the domain’s root-level .env file is exposed and contains credentials for accessing additional services. If the .env file is exposed, threat actors will issue a GET request to the /.env URI to attempt to access the data on the page. This method appears to be used for websites in debug mode (i.e., when non-production websites are exposed to the internet). A successful response allows the threat actors to look for usernames, passwords, and/or other credentials pertaining to services such as email (via SMTP) and AWS accounts.
If the threat actors successfully identify the Laravel application key, they will attempt exploitation by using the key to encrypt the PHP code The encrypted code is then passed to the website as a value in the cross-site forgery request (XSRF) token cookie, XSRF-TOKEN, and included in a future GET request to the website. The vulnerability defined in CVE-2018-15133 indicates that on Laravel applications, XSRF token values are subject to an un-serialized call, which can allow for remote code execution. In doing so, the threat actors can upload files to the website via remote access.
Targeting Apache Web Servers – Androxgh0st actors have been observed scanning vulnerable web servers running Apache HTTP Server versions 2.4.49 or 2.4.50. Threat actors can identify uniform resource locators (URLs) for files outside the root directory through a path traversal attack. If these files are not protected by the “request all denied” configuration and Common Gateway Interface (CGI) scripts are enabled, this may allow for remote code execution.
Bottomline – If threat actors obtain credentials for any services using the above methods, they may use these credentials to access sensitive data or use these services to conduct additional malicious operations.
Important Note for SafeBreach Customers – Coverage for AA24-016A (Androxgh0st Malware)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers were already protected against several of the behavioral and IOC-based attacks identified in the advisory. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
NEW IOC-Based Attacks Related to CERT Alert
- XMRIG
- #9465 – Write XMRig (dee066) miner to disk
- #9466 – Pre-execution phase of XMRig (dee066) miner (Linux)
- #9467 – Transfer of XMRig (dee066) miner over HTTP/S
- #9468 – Transfer of XMRig (dee066) miner over HTTP/S
- #9469 – Email XMRig (dee066) miner as a compressed attachment
- #9470 – Email XMRig (dee066) miner as a compressed attachment
- MARIJUANA PHP Webshell
- #9471 – Write MARIJUANA (d317ef) webshell to disk
- #9472 – Transfer of MARIJUANA (d317ef) webshell over HTTP/S
- #9473 – Transfer of MARIJUANA (d317ef) webshell over HTTP/S
- #9474 – Email MARIJUANA (d317ef) webshell as a compressed attachment
- #9475 – Email MARIJUANA (d317ef) webshell as a compressed attachment
- AndroxGh0st Hacktool
- #9476 – Write AndroxGh0st (b5c81a) hacktool to disk
- #9477 – Transfer of AndroxGh0st (b5c81a) hacktool over HTTP/S
- #9478 – Transfer of AndroxGh0st (b5c81a) hacktool over HTTP/S
- #9479 – Email AndroxGh0st (b5c81a) hacktool as a compressed attachment
- #9480 – Email AndroxGh0st (b5c81a) hacktool as a compressed attachment
- New Vulnerability Exploitation Attack (CVE-2017-9841)
- #9481 – Remote exploitation of PHPUnit vulnerability CVE-2017-9841 (WAF)
Existing Behavioral Attacks Mapped to the CERT Alert
- # 232 – WSO2 Webshell- Execute Whoami command
- # 5328 – Collect AWS-CLI credentials (AWS)
- # 5675 – Create an AWS user
- # 5990 – Create EC2 instance (AWS)
- # 6456 – Generate temporary credentials via Security Token Service (STS AWS)
- # 6877 – Path Traversal Attack- GET request
- # 6878 – Path Traversal Attack- POST request
Existing IOC-based Attacks Mapped to the CERT Alert
- # 7153 – Pre-execution phase of XMRIG Cryptominer backdoor
- # 7154 – Write XMRIG Cryptominer backdoor to disk
- # 7155 – Transfer of XMRIG Cryptominer backdoor over HTTP/S
- # 7156 – Transfer of XMRIG Cryptominer backdoor over HTTP/S
- # 7157 – Email XMRIG Cryptominer backdoor as a compressed attachment
- # 7158 – Email XMRIG Cryptominer backdoor as a compressed attachment
- # 7159 – Pre-execution phase of XMRIG Cryptominer-2 backdoor
- # 7160 – Write XMRIG Cryptominer-2 backdoor to disk
- # 7161 – Transfer of XMRIG Cryptominer-2 backdoor over HTTP/S
- # 7162 – Transfer of XMRIG Cryptominer-2 backdoor over HTTP/S
- # 7163 – Email XMRIG Cryptominer-2 backdoor as a compressed attachment
- # 7164 – Email XMRIG Cryptominer-2 backdoor as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
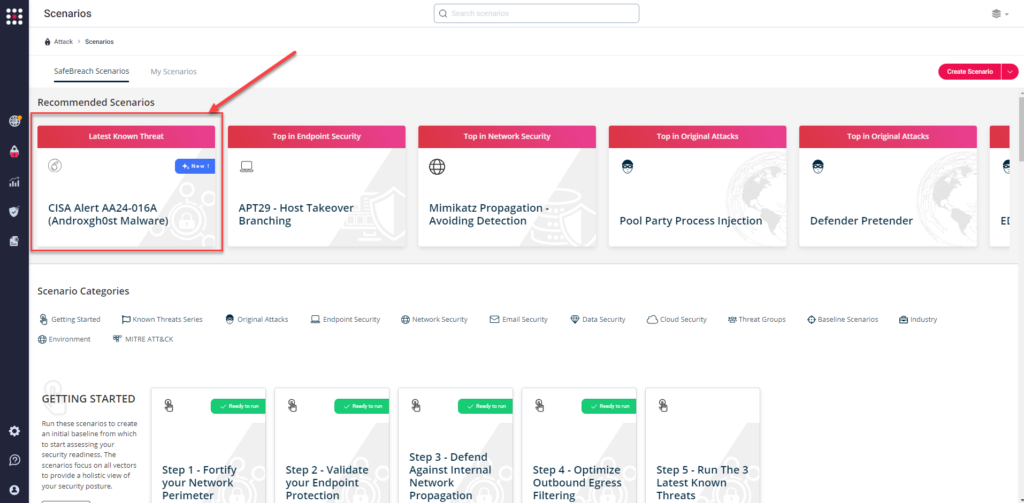
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-016A (Androxgh0st Malware) scenario from the list of available scenarios.
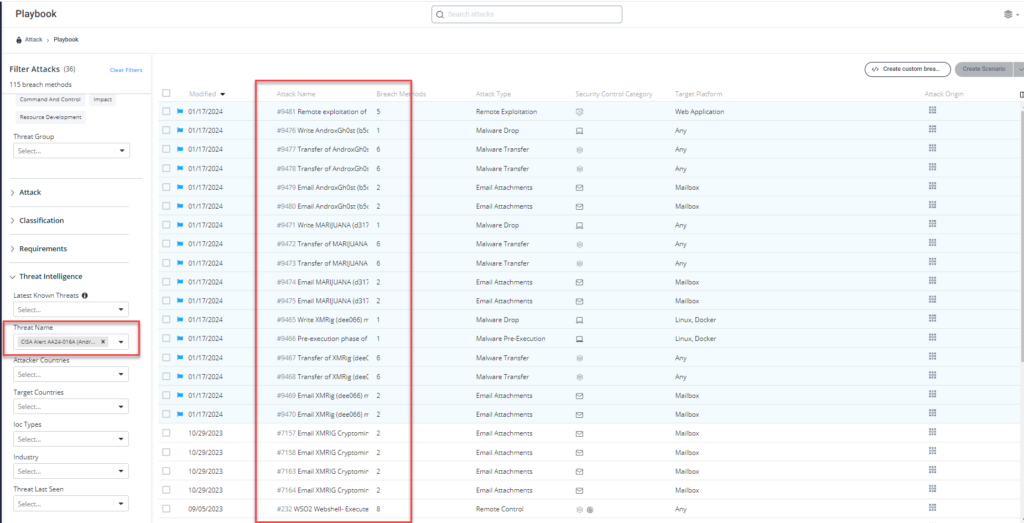
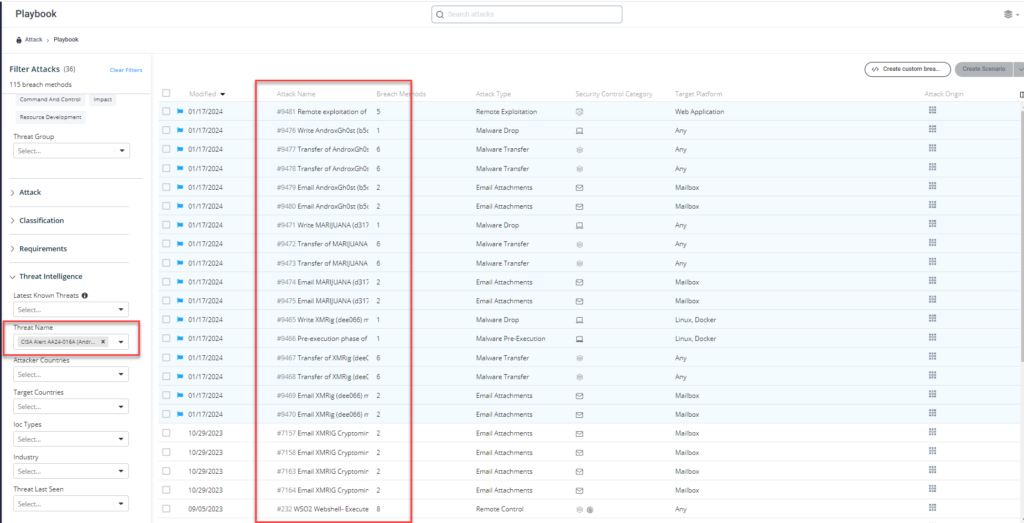
Method 2 – – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA24-016A (Androxgh0st Malware). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
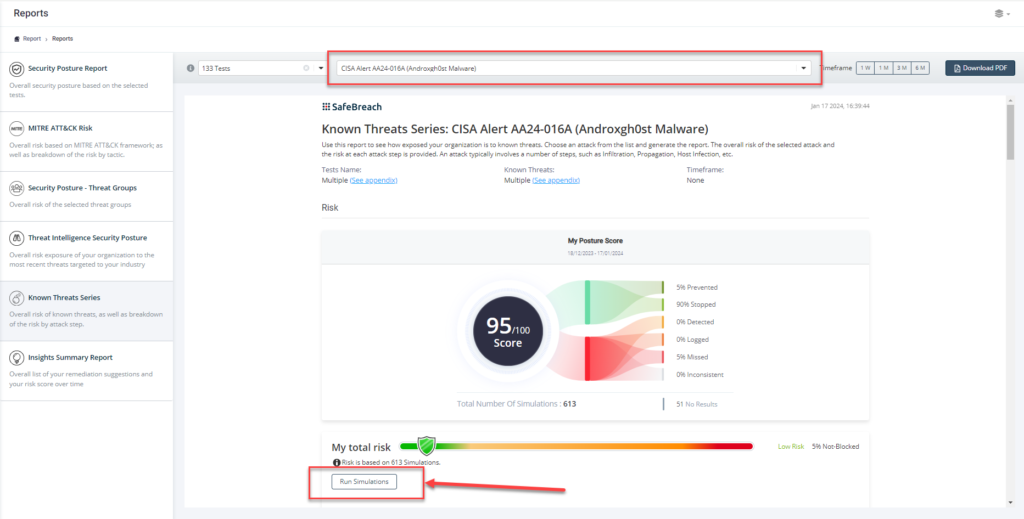
Method 3 – From the Known Attack Series report, select the AA24-016A (Androxgh0st Malware) report and select Run Simulations which will run all attack methods.
NOTE – FBI and CISA recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations include:
- Keep all operating systems, software, and firmware up to date. Specifically, ensure that Apache servers are not running versions 2.4.49 or 2.4.50.
- Verify that the default configuration for all URIs is to deny all requests.
- Ensure that any live Laravel applications are not in “debug” or testing mode. Remove all cloud credentials from .env files and revoke them. All cloud providers have safer ways to provide temporary, frequently rotated credentials to code running inside a web server without storing them in any file.
- On a one-time basis for previously stored cloud credentials, and on an ongoing basis for other types of credentials that cannot be removed, review any platforms or services that have credentials listed in the .env file for unauthorized access or use.
- Scan the server’s file system for unrecognized PHP files.
- Review outgoing GET requests (via cURL command) to file hosting sites.
- For detailed information about mitigations and incident response, please refer to the full advisory.
如有侵权请联系:admin#unsafe.sh