2024-1-18 02:41:19 Author: securityboulevard.com(查看原文) 阅读量:13 收藏
Thanks to various 2023 security reports, we know phishing attacks are now the most common form of cybercrime, with an estimated close to 3.5 billion spam emails sent every day. In 2022, reports indicated that the worldwide average cost of a data breach amounted to $4.35 million, with the US experiencing an average data breach cost of $9.44 million.1 But the phishing game is shifting, evolving, and we are now seeing more sophisticated moves like social engineering, quicker attack times, and the use of legitimate services to launch attacks.
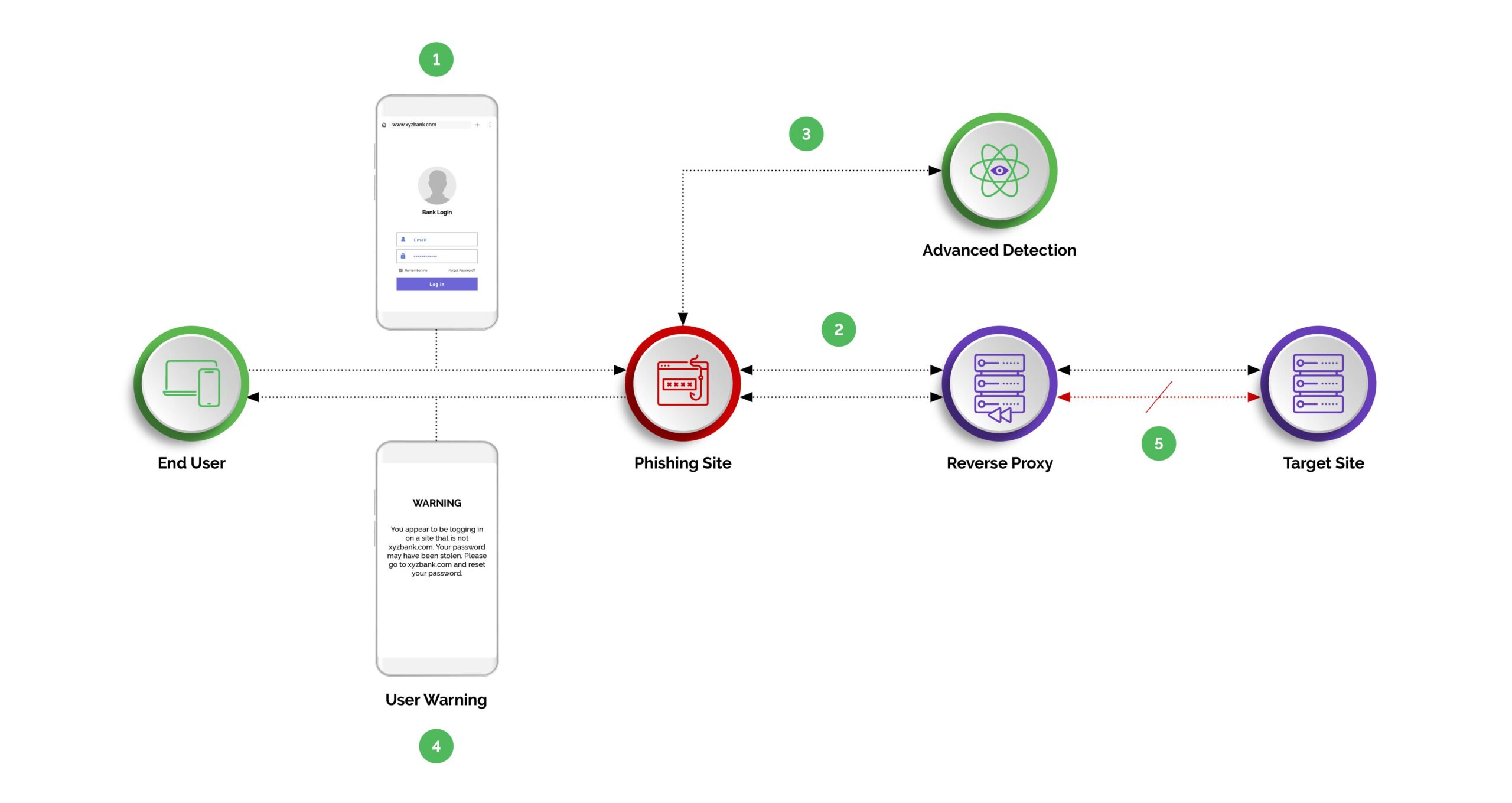
Adversaries are also leveraging reverse proxy phishing tactics to achieve their goals, a type of cyberattack that involves the use of a reverse proxy server to deceive users and collect sensitive information. Reverse proxy attacks exploit vulnerabilities in server infrastructure, while phishing employs tactics to trick users into revealing sensitive information. Reverse proxy phishing is particularly dangerous because it can be difficult to detect. The attackers leverage the trust users have in authentic websites, making it more likely for someone to enter personal information without feeling suspicious.
Let’s dive into these changes, examine the strategies adversaries are using to carry out reverse proxy phishing, and look closely at how phishing protection can help online businesses. From new attack surfaces to professional phishing services, there is a lot to say about this shifting landscape—and how businesses can find protection from the next generation of threats.
RECOMMENDED RESOURCE
Arkose Phishing Protection
Quick Notes on Reverse Proxy Phishing
Here’s how reverse proxy phishing works. Attackers set up the reverse proxy server, which acts as an intermediary between the user and the real company website. The user believes they are interacting directly with the legitimate site, when in fact their requests are passing through to the attack server. Sometimes the attacker registers a domain name that looks similar to the real one.

For example, they might use a slightly misspelled version of the domain name to trick users—but not always. Other times, the domains are different to target the website hostname. Since the phishing URLs are sent via email, users often do not pay attention to the domain name.
To make the reverse proxy attack more believable, the actor may obtain SSL/TLS certificates for their fake domain. This gives the appearance of a secure connection to the user. So, when the user accesses the proxied website, the reverse proxy intercepts their requests and forwards them to the legitimate website. The user sees the content of the real site, but the attacker can manipulate the content or inject malicious elements.
As users interact with the proxied fake site, the attacker collects sensitive information such as usernames, passwords, credit card details, or any other data they’re targeting.

RECOMMENDED RESOURCE
New Details on EvilProxy Attacks and Prevention Steps You Can Take Now
A Shift Into Evil Proxies
Evil Proxy is a reverse proxy phishing kit that signifies a rising trend in the deceitful use of reverse proxies. As websites increasingly incorporate OTP/MFA authentication alongside login credentials, the conventional approach of creating fake websites becomes less effective.
Fraudsters have adapted to this challenge by abandoning the creation of fake websites and, instead, resorting to sending well-crafted phishing emails to individuals. This strategic shift has led to the emergence of a new term, “evil proxies,” reflecting the evolution of evasive techniques in the realm of online fraud.
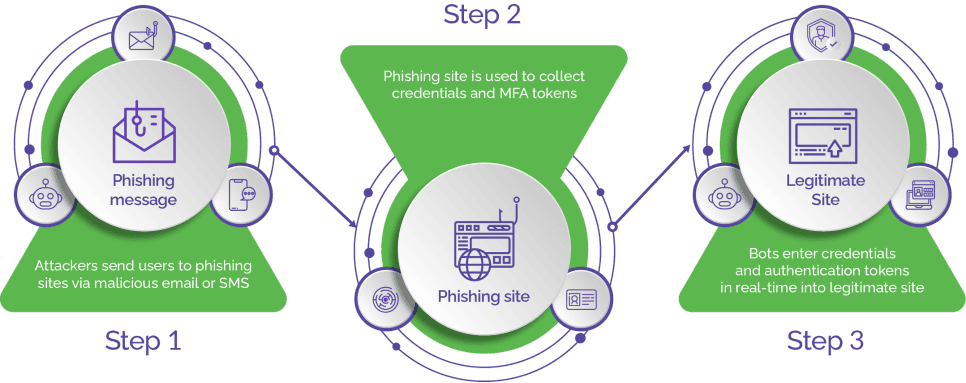
This method allows cybercriminals to operate stealthily, exploiting the trust users place in seemingly genuine websites. It starts with a simple email, like a phishing email. Users click the link and arrive at a seemingly legitimate login page. The user enters their credentials and the workflow kicks in.
Once the user enters the creds, they get the OTP notification. Because the site is still being proxied, the attackers are able to suck the OTP information out as well, taking control of the account. This move can be used to launch larger attacks down the line. Organizations and users must stay vigilant, employing robust cybersecurity measures to detect and mitigate the risks posed by reverse proxy phishing kits like Evil Proxy.
Phishing with EvilProxy
This is where the phishing-as-a-service (PhaaS) model comes in, a subset of the cybercrime-as-service (CaaS) phenomenon. Phishing attack methods have evolved to using pre-packed, pay-per-use phishing kits containing all the infrastructure needed for a campaign, including:
- scripts
- a web server
- storage used to collect credentials
- templates for creating fake emails and websites
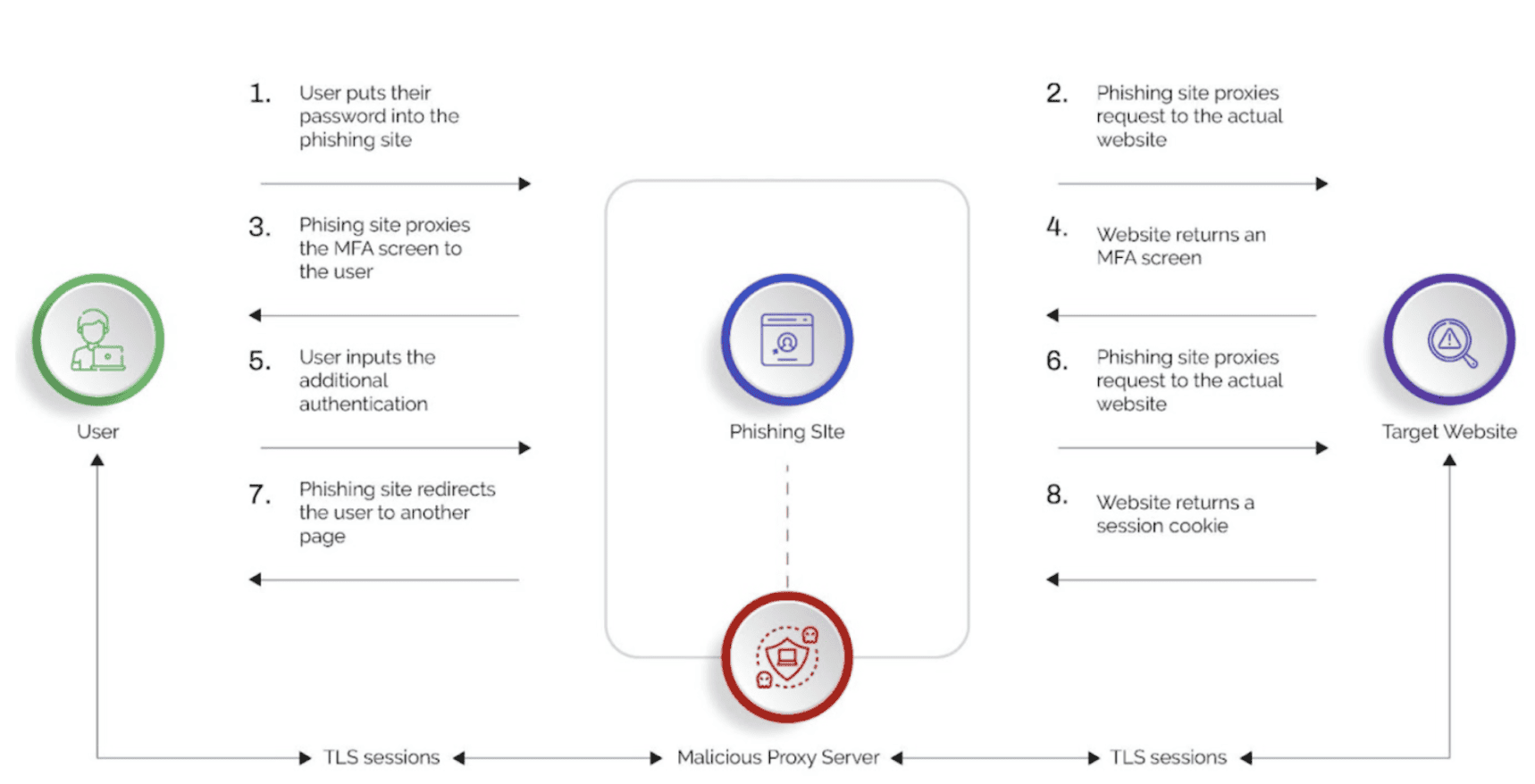
Adversaries have been using the PhaaS toolkit, EvilProxy, to launch attacks since mid-2022. Bad actors lead users onto a phishing page and use the reverse proxy to fetch all the valid content from the site. EvilProxy surveys the web traffic and sniffs out important information like login credentials or even credit card numbers. On the way back, when the response is sent from the customer’s website to the user, attackers rewrite the site URL. This means they are not really hosting a website, just a proxy server.
Arkose Phishing Protection Takes On Evil Proxy
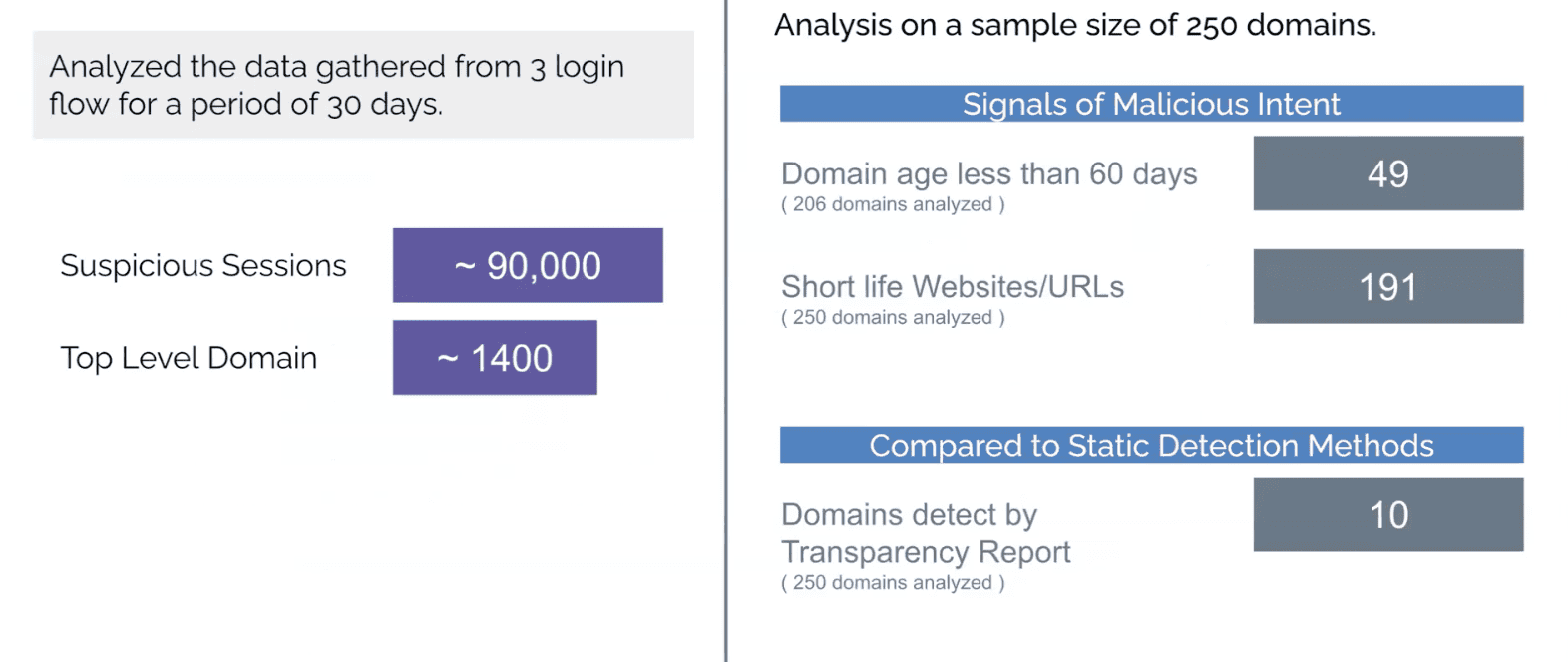
When we first launched Arkose Phishing Protection, we conducted an analysis of requests seen on three login endpoints. We observed about 90,000 suspicious sessions originating from 1,400 domains. Of the 1,400 suspicious domains, we picked a sample of 250 domains for further analysis. Of those 250 domains, 49 were created in less than 60 days, which means they were likely created for attack. 191 domains were short-lived and soon disappeared.
We also observed that out of the 250, only 10 were marked as suspicious by traditional phishing detection/scanning methods, meaning if we hadn’t stepped in with protection, 240 suspicious domains would have gone unnoticed and would have been free to do harm to businesses and consumers.
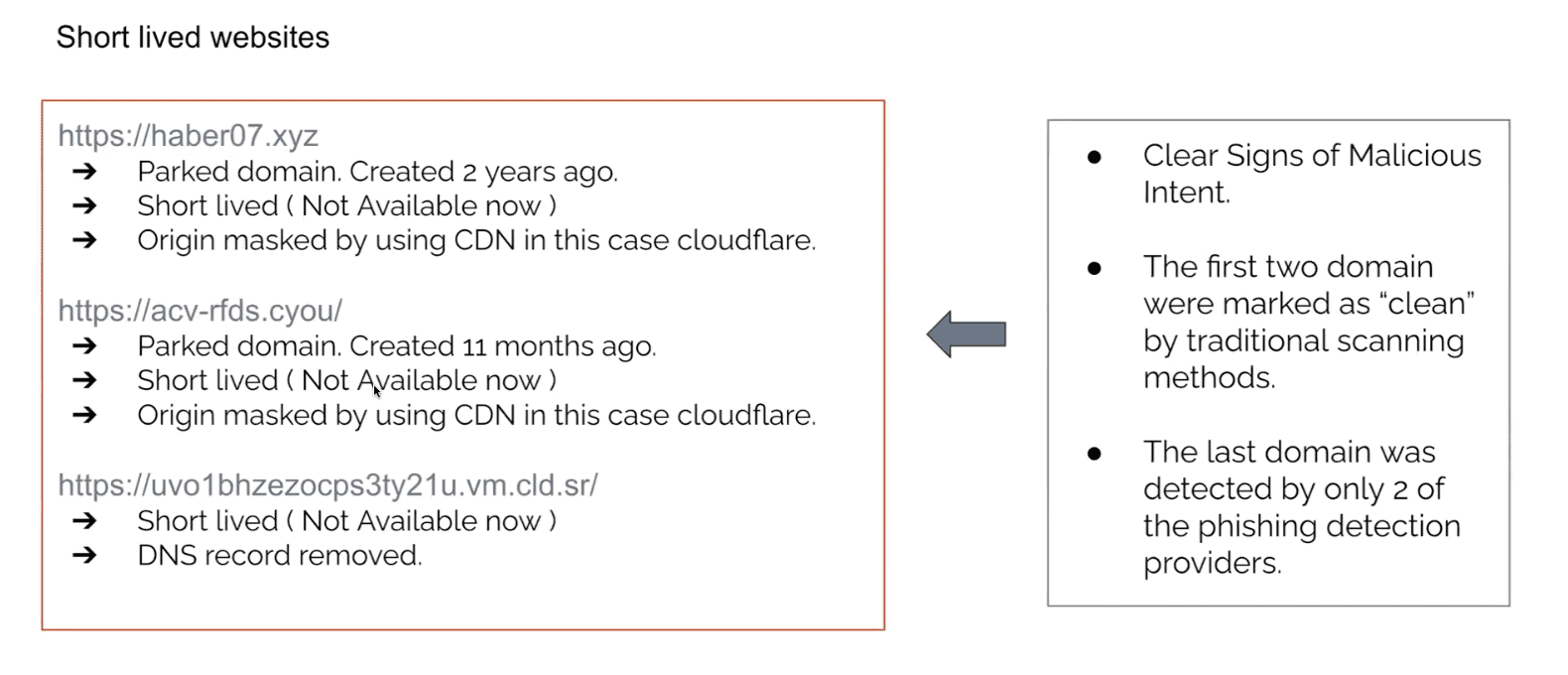
Here’s a use case on how our phishing protection performed on a specific website. We took the analysis from above and switched on Arkose Phishing Protection for an anonymous banking site. Arkose Phishing Protection was able to highlight if sites were short lived, which was not detectable previously. As soon as the solution was implemented, we were able to share rich data with the website owner by quickly identifying the actual sites bearing their look and name. Through a live demo, we showed the website owner all the phishing sites currently running with their brand name.
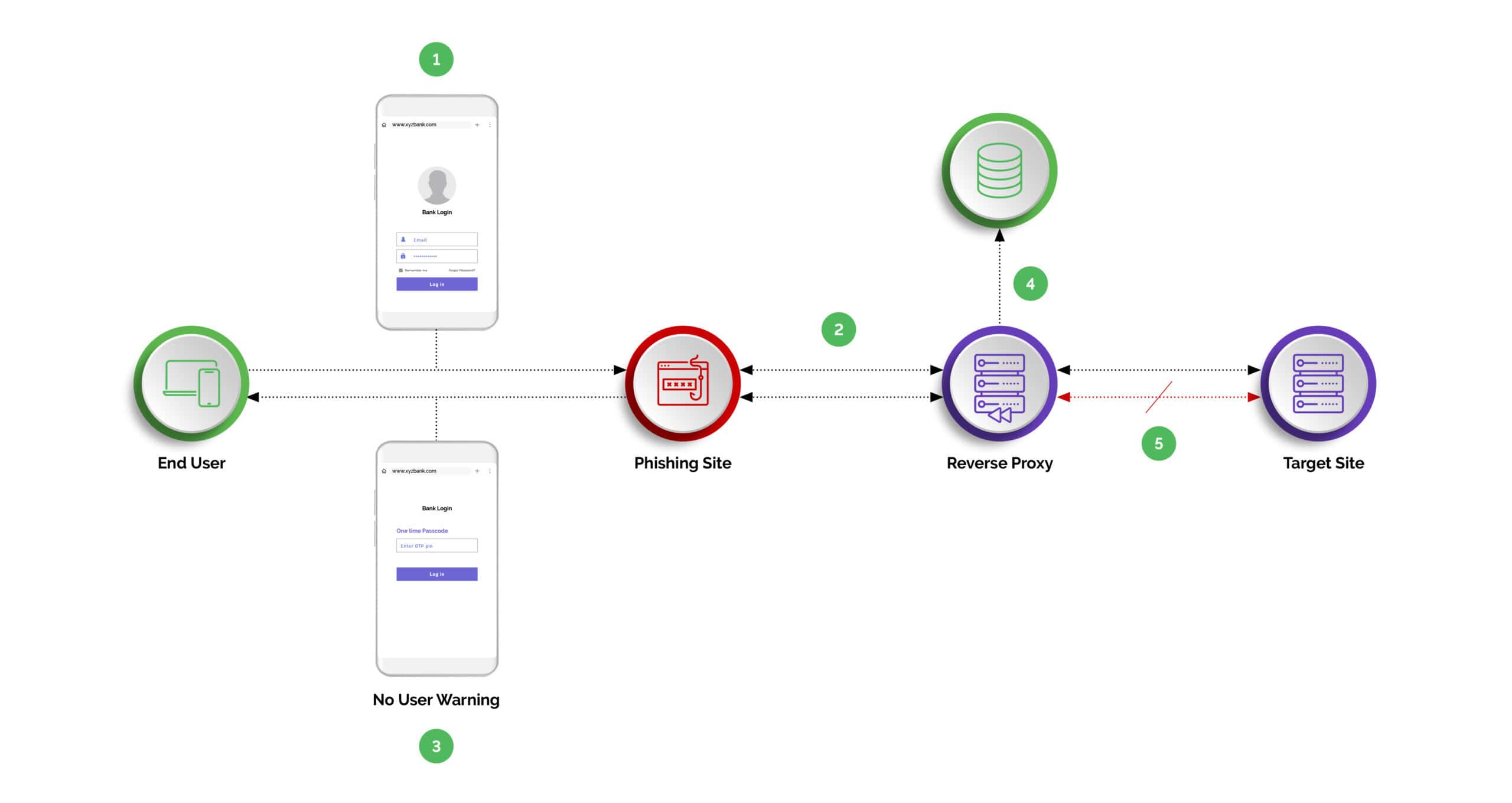
Arkose Labs: Reverse Proxy Protection
Arkose Phishing Protection effectively halts reverse proxy phishing assaults, safeguarding against the compromise of login and MFA credentials. It offers the configurability and intelligence essential for product security teams to safeguard their applications and users.
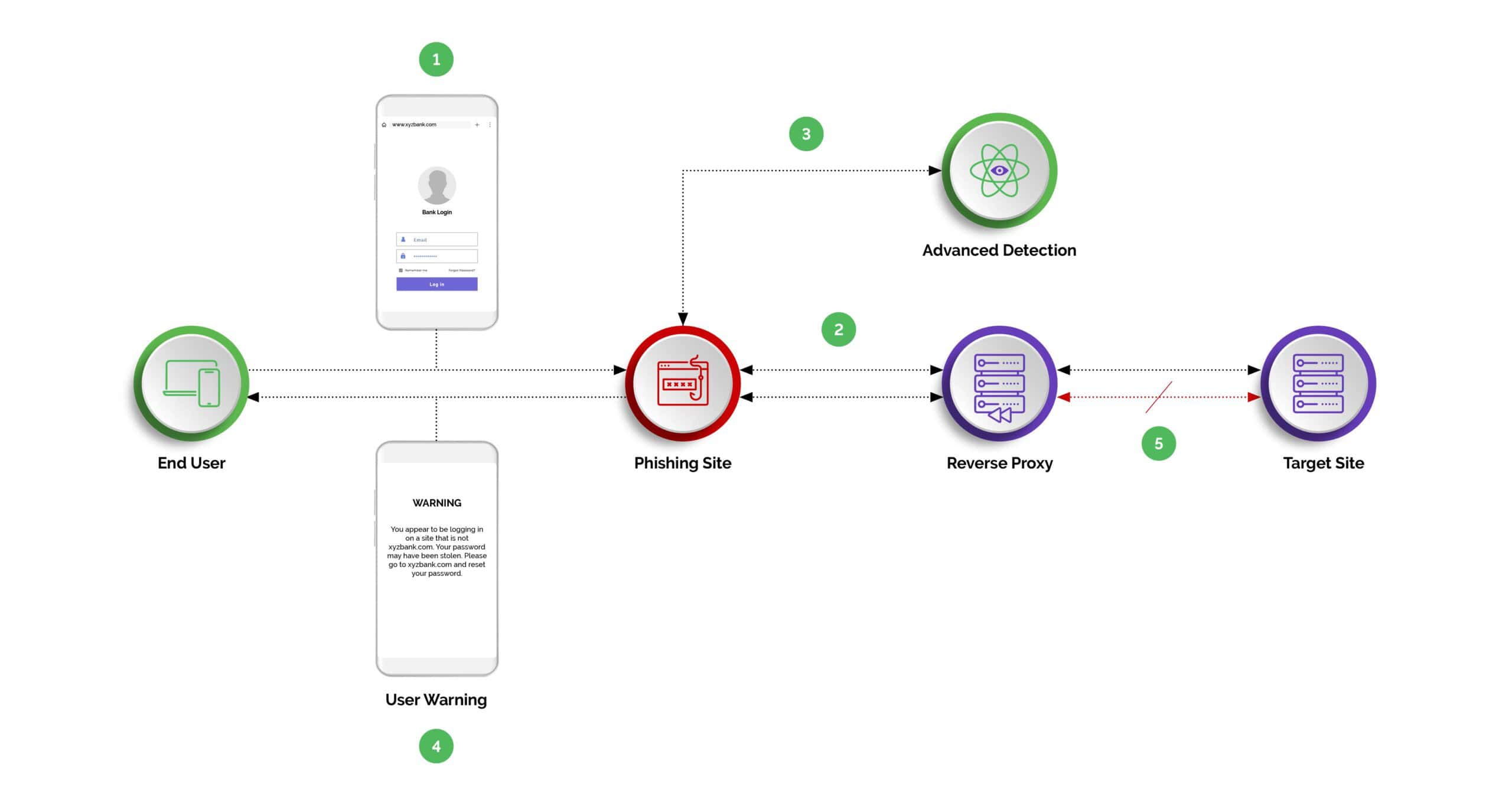
Arkose Bot Manager detects and blocks the reverse proxy, “adversary-in- the-middle” attacks of EvilProxy. Our device fingerprinting technology tracks more than 125 data signals to detect reverse proxies and block them in real-time.
Contact us today to learn more!

RECOMMENDED RESOURCE
New Details on EvilProxy Attacks and Prevention Steps You Can Take Now
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Vikas Shetty. Read the original post at: https://www.arkoselabs.com/blog/taking-on-evilproxy-advancements-in-phishing-protection/
如有侵权请联系:admin#unsafe.sh