An overview of last year’s predictions
-
Increase in personal data leaks; corporate email at risk
A data leakage is a broad term encompassing various types of information that become publicly available, or published for sale on the dark web or other shadow web sites. Leaked information may include internal corporate documents, databases, personal and work login credentials, and other types of data.
Last year, we predicted that personal data and corporate email would increasingly be at risk, and the prediction proved largely accurate. In 2023, for instance, there was a significant rise in posts offering login credentials and passwords for various personal and work accounts. To be more specific, in 2023, the volume of malware log files containing compromised user data and posted for free on the dark web surged by almost 30% compared to 2022.
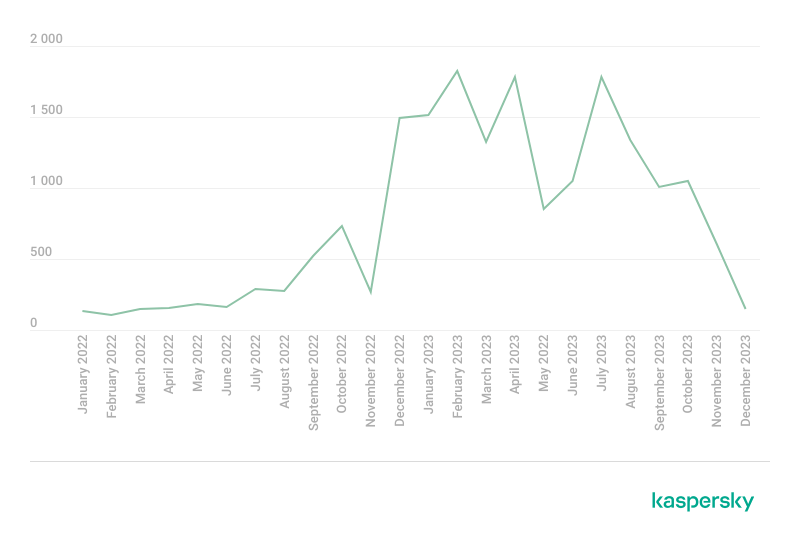
Throughout the past year, various companies were referenced in dark web discussions on leaked internal databases including those containing client information and documents on the darknet—nearly 19,000 posts like that were detected in January–November 2023.
Moreover, since political confrontation now inherently includes cyber-elements, some data breach attacks also occurred amid ongoing conflicts, such as the Israeli-Hamas conflict. For example, the group Cyber Toufan was reported to have claimed dozens of data breaches against Israeli firms. On the opposite side, over 1 million records from Palestine’s healthcare system were posted on the dark web. On the whole, in the digital realm of conflicts, hackers on both sides tend to engage in activities like breaching various services or websites, to expose the data publicly—sometimes not for financial gain but rather with the intent of causing the opponent harm.
Verdict: prediction fulfilled ✅
-
Malware-as-a-service: a greater number of cookie-cutter attacks, more complex tools
The year 2023 saw new malware families offered as a service (MaaS) emerge, contributing to the overall rise in MaaS activity on the dark web. Notable among these was BunnyLoader, inexpensive and feature-rich malware capable of stealing sensitive data and cryptocurrency. Another newcomer in 2023 was Mystic Stealer, subscription-based malware discussed on darknet forums and recognized for its ability to pilfer user credentials and valuable information. It was distributed on cybercriminal forums under the MaaS model with a monthly fee of $150, according to Kaspersky Digital Footprint Intelligence data. Existing malware, typically offered through subscription models, continued to thrive.
The number of posts on the dark web offering logs from RedLine, a widely popular malware family, also significantly increased: from 370 average monthly posts in 2022 to 1200 in 2023.
Last year, we released an in-depth study on MaaS, offering detailed insights into the market landscape and the complexity of toolsets used by attackers.
Verdict: prediction fulfilled ✅
-
Media blackmail: businesses to learn they were hacked from hackers’ public posts with a countdown to release
Ransomware operators create blogs to showcase new successful hacks of businesses and reveal stolen data. In 2022, these blogs, found on both public platforms and the dark web, averaged 386 posts per month. In 2023, this figure surged to 476, hitting a peak of 634 posts in November. This points to a continuous rise in companies falling prey to ransomware.
Not only did the number of posts increase, but we also witnessed the emergence of several new ransomware blogs. They typically emerge when a new ransomware group appears. It is important to note that the blogs of existing groups may not be “fixed in place”: they may change their site address or create multiple addresses simultaneously.
Verdict: prediction fulfilled ✅
-
Enjoying the fun part: cybercriminals to post fake hack reports more often
Last year, we predicted an increase in threat actors producing fake data leak reports, attempting to present them as authentic. In fact, it turned out that genuine data leaks had various motives behind them, such as hacktivism or even “marketing”. The latter means that cybercriminals reposted real data leaks as a means of advertising forums and other dark web sites, trying to enhance the reputation of these platforms.
In the Russian-speaking segment of the shadow market, we noticed numerous fakes published by “no-name” threat actors rather than well-known groups. Threat actors with a reputation refrained from claiming hacks or posting fakes.
Verdict: partially fulfilled 🆗
-
Cloud technology and compromised data sourced on the dark web to become popular attack vectors
In the past year, we did not encounter any investigations into attacks on our clients’ clouds. However, it is important to note that compromised data from the dark web could potentially be utilized for orchestrating attacks. There has been a noticeable rise in the number of leaked user credentials, suggesting growing demand within the community for this kind of information. This demand stems from the fact that it is one of the simplest methods of gaining unauthorized access to infrastructure.
Verdict: partially fulfilled 🆗
Our predictions for 2024
The number of services providing AV evasion for malware (cryptors) will increase
The trend observed in 2023, where services offering antivirus (AV) evasion for malware (cryptors), is expected to persist into 2024. A cryptor is a tool specifically designed to obfuscate the code present in a malware sample. Its purpose is to make the code undetectable by signature-based scanners, thus enhancing its stealthiness.
The dark market is already replete with such services. Some of these offers are very popular on underground forums. The spectrum of cryptors ranges from affordable options, priced between $10–$50 per encryption or $100 for a monthly subscription and catering to mass malware distribution with basic, short-lived protection, to premium cryptors costing between $1000–$20,000 for a monthly subscription. Tailored for targeted infection, these high-end cryptors provide advanced invasive capabilities for bypassing runtime protection by security solutions.
“Loader” malware services will continue to evolve
The landscape of “loader” malware services is anticipated to continue its evolution, offering increasingly stealthy loaders to cybercriminals. These loaders, which act as an initial vector for malware infections, pave the way for deployment of stealers, various remote access Trojans (RATs), and other malicious tools. The key capabilities of these loaders are expected to include robust persistence mechanisms, fileless memory execution, and enhanced resistance to security products. The ongoing evolution of loaders on dark markets is likely to see the introduction of new versions written in modern programming languages like Golang and Rust in 2024. This trend signifies a concerted effort by cybercriminals to enhance evasion techniques and improve the efficacy of initial infection vectors.
Crypto asset draining services will continue to grow on dark web markets
We anticipate a rise and further advancement in crypto asset stealers, leading to a corresponding increase in ads for its development and sale on the underground market. The success of malware like Angel Drainer, reportedly used in the attack on Ledger, combined with continuing interest in cryptocurrencies, NFTs, and related digital assets, is expected to fuel the proliferation of such drainers. This trend reflects the lucrative nature of targeting digital financial assets, making crypto assets an attractive target for cybercriminals. As interest in, and usage of, these assets are growing, so, too, will the sophistication and prevalence of malware designed to exploit them.
Black traffic schemes will be very popular on underground markets
The trend of utilizing Google and Bing ads for fake traffic gathering campaigns is projected to maintain its popularity. Black traffic dealers, who orchestrate these campaigns by promoting landing pages embedded with malware installers, have been effectively infecting users through these deceptive ads. These dealers are likely to step up sales activities on the underground market. At the same time, demand for such services is expected to increase, underscoring the effectiveness of mainstream ad delivery platforms for malware distribution and making it a preferred method among cybercriminals for reaching a wider audience. As a result, we can expect a continued rise in these deceptive practices, posing a persistent threat to online users.
Evolution and market dynamics of Bitcoin mixers and cleaning services
Bitcoin mixers and “cleaning” services are showing signs of a continued rise in prevalence and sophistication. With increased regulatory scrutiny and enhanced transaction tracking capabilities by law enforcement, demand for services that obscure the origin of Bitcoin funds is expected to grow in the underground markets. These services, often referred to as “tumblers” or “mixers”, provide threats actors or other nefarious users with the ability to anonymize their cryptocurrency transactions, making them challenging to trace back to the source.
In 2024, we anticipate an expansion in the variety and complexity of these services. This expansion is likely to be driven by the evolving needs of threat actors seeking to maintain privacy to engage in illicit activities, as well as by the continuous advancement in blockchain analysis tools. Bitcoin mixers and cleaning services will likely incorporate more sophisticated algorithms and techniques to stay ahead of tracking efforts.
Moreover, the rise in the popularity of other cryptocurrencies with enhanced privacy features might also influence the Bitcoin mixer market. Service providers could diversify their offerings to include mixing for these alternative cryptocurrencies, further expanding the scope of their operations.