2024-1-16 23:55:54 Author: securityboulevard.com(查看原文) 阅读量:2 收藏

Software supply chain attacks are now mainstream events — a change in tactics by cyber-attackers that you can measure in headlines, which in recent years have delivered news about attacks on popular software tools including MOVEIt, 3CX, and CircleCI.
What’s behind this change? An explosion in supply chain threats, for one thing. ReversingLabs’ State of Software Supply Chain Security 2024 report finds that incidents of malicious packages found on popular open-source package managers have increased by 1,300% over the past three years. Despite that, however, the software industry at large still hasn’t woken up to the changing landscape of software supply chain security threats. Loose development practices and inattention to software supply chain risks persist, ReversingLabs found.
[Incidents] of malicious packages found on popular open-source package managers have increased by 1,300% over the past three years.
The State of Software Supply Chain Security 2024 is ReversingLabs’ second annual assessment of software supply chain security. The report gives an overview of the 2023 threat landscape, analyzes what has changed since 2022, and anticipates what the industry can expect in 2024.
In assembling the report, the ReversingLabs research team surveyed the software supply chain threat landscape. They not only observed an increase in the number of malicious incidents, but also saw that the bar for carrying out successful supply chain attacks is lowering, as more and different types of malicious cyber-actors incorporate aspects of supply chain attacks into their playbooks and tooling.
Equally concerning: Stakeholders in the software supply chain, such as software developers, application security (AppSec) teams, open-source maintainers, and third-party risk managers are struggling to address the gaps in their software supply chain security, making it less likely that they will successfully mitigate threats.
Here are the important takeaways from the State of Software Supply Chain Security 2024 report.
[ Get the new report: The State of Software Supply Chain Security 2024 | Join the conversation: Webinar: State of Software Supply Chain 2024 ]
Software producers and consumers have a blind spot
In 2023, examples continued to pop up of threat actors going beyond the exploitation of vulnerabilities to carry out software supply chain attacks. In March 2023, for example, voice over IP (VoIP) vendor 3CX disclosed that a version of the company’s 3CX Desktop App software was distributed with malicious code to thousands of customers.
ReversingLabs’ analysis of the incident found that attackers managed to compromise 3CX’s software build pipeline, making modifications to 3CX’s copies of standard open-source files to insert malicious code into the finished 3CX Desktop App package. While there were signs of tampering, 3CX unfortunately failed to detect the evidence of it before it released the software to its customers — and long afterwards as well.
The case of 3CX Desktop App showcases the blind spot that software producers have in the security measures they use to ensure that software releases are secure post-deployment. It also demonstrates how consumers are subject to such third-party malicious threats if they don’t use proper tooling to vet their third-party software providers. Software-producing and -consuming organizations need to choose tools that go beyond detecting vulnerabilities to avoid this security blind spot.
That’s why, in addition to using legacy AppSec tools such as software composition analysis (SCA) and static and dynamic application security testing (SAST and DAST), stakeholders of software supply chains should also opt in to tooling that analyzes raw code and tracks the evolution of compiled software binaries. This technology will help organizations identify unwanted or unknown changes made to a software package, such as malicious tampering.
A lower bar for software supply chain attacks
Software supply chain attacks used to be an exclusive realm for sophisticated, nation state-backed hacking crews. This is changing. Based on data compiled from ReversingLabs, the bar for software supply chain attacks dropped steadily in 2023, and ReversingLabs experts believe that it will continue to decline in 2024.
By scouring common open-source repositories, ReversingLabs researchers discovered a number of open-source software supply chain attacks in 2023 that were delivering malware such as infostealers, backdoors, protestware, and more.
There are a number of reasons for this. First, open-source software repositories, such as npm, Python Package Index (PyPI), and NuGet are growing as attack surfaces. In 2023, ReversingLabs saw a 28% increase from the year before in the total number of malicious packages uploaded to open-source repositories. Those malicious packages are easy to place and open the door to techniques such as typosquatting, repojacking, and other tricks that play on the goodwill (or haste) of developers who rely on open source code and package managers.

The other reason that the barrier to carrying out a software supply chain attack is dropping is that cyber-criminals are embracing supply chain attacks to enhance common, low-level campaigns such as phishing attacks. For example, Operation Brainleeches, discovered by ReversingLabs researchers in July 2023, displayed what may be the first “dual-use” campaign via npm, in which over a dozen malicious packages uploaded to the widely used repository were used to fuel phishing campaigns that targeted Microsoft 365 end users in addition to npm developers — the more typical target of malicious campaigns on these platforms.
The case of Operation Brainleeches targeting two different kinds of victims, as well as the increase in open-source software supply chain attacks this year, showcases how these incidents are becoming easier to pull off and more difficult for security teams to manage.
Big changes, but more of the same, too
While there have been substantial changes in the threat landscape this past year, the goals and tactics of threat actors stayed fairly consistent compared to what was seen in the past.
As noted before, ReversingLabs’ new report cites a 28% increase in the number of malicious packages across open-source repositories. That increase is on track with earlier years. However, when breaking down the numbers by each repository, ReversingLabs researchers noted some interesting changes. For instance, there was a 400% increase in the number of packages residing on the PyPI open-source repository in comparison to 2022, yet 2023 saw a 43% decrease in the number of malicious packages on npm, despite it being the primary repository used for the dissemination of malicious packages the previous year.
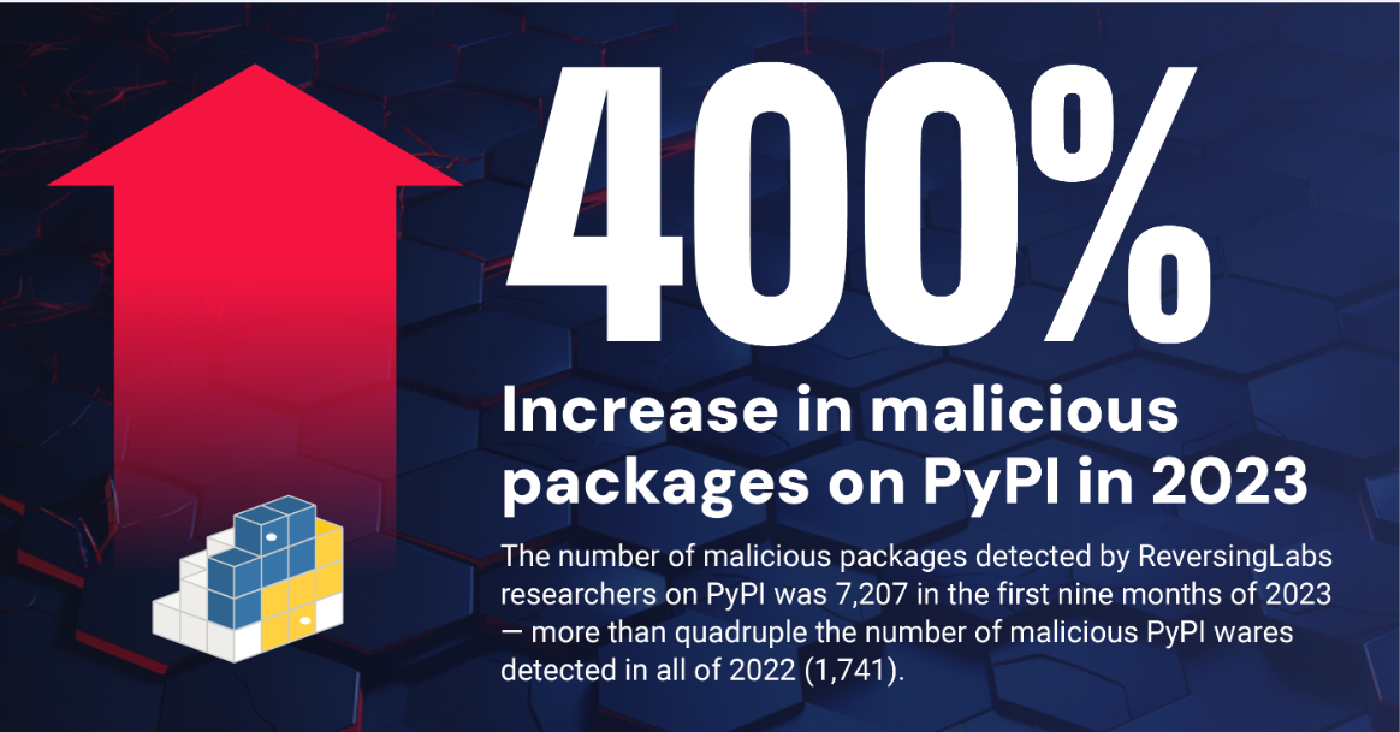
The significance of these changes between npm and PyPI is not clear. It may be due to the growing popularity of PyPI among the developer community. With the increased use of the Python programming language and the PyPI platform, threat actors are seeing it as the more worthy target for malicious packages. Or it may be a momentary fluctuation in malicious supply chain activity that will not be sustained.
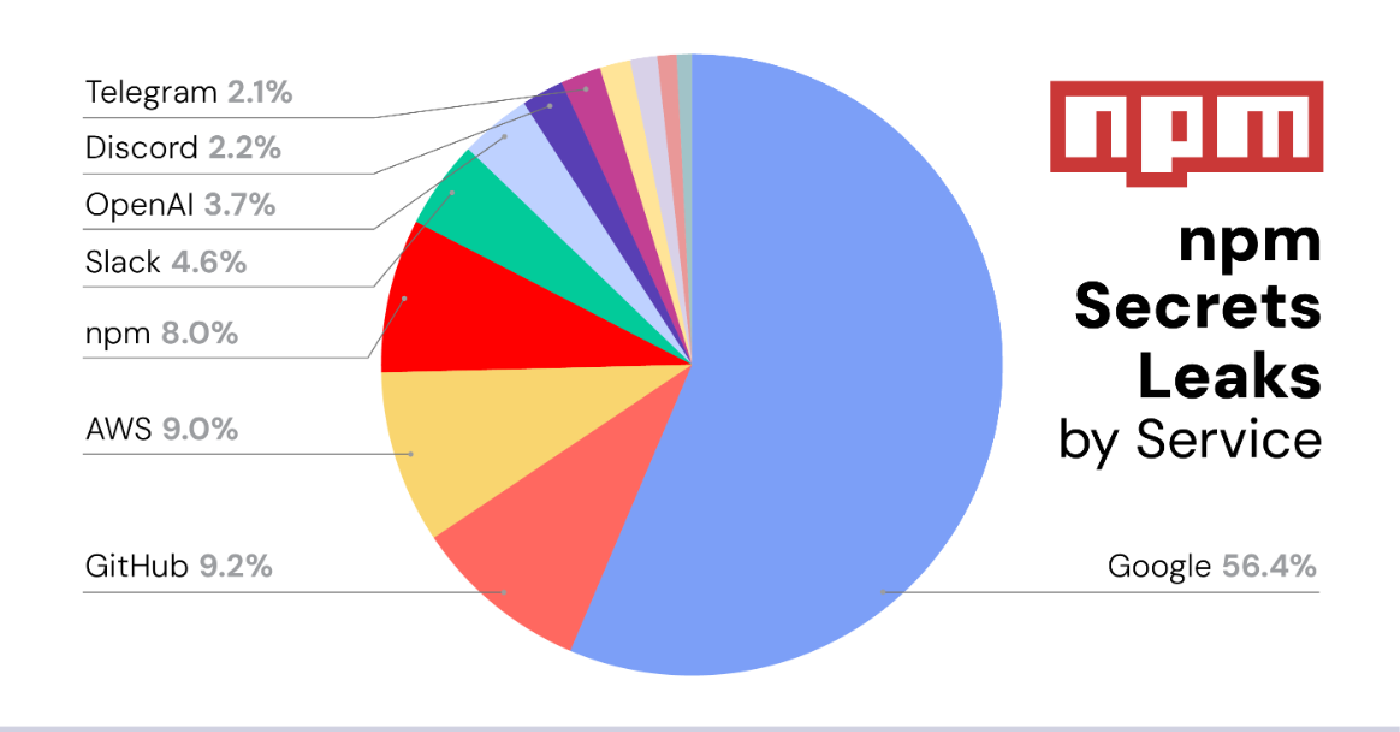
Despite the variability of threat trends, one trend line that continued its journey upward was the amount of software secrets lurking on open-source platforms. ReversingLabs found more than 40,000 secrets spread across four major open-source repositories: npm, PyPI, RubyGems, and NuGet. The total amount found is unsurprising, given how secrets leaks have emerged in recent years as a consistent software supply chain weakness — one rooted in loose application design and modern-day development practices.
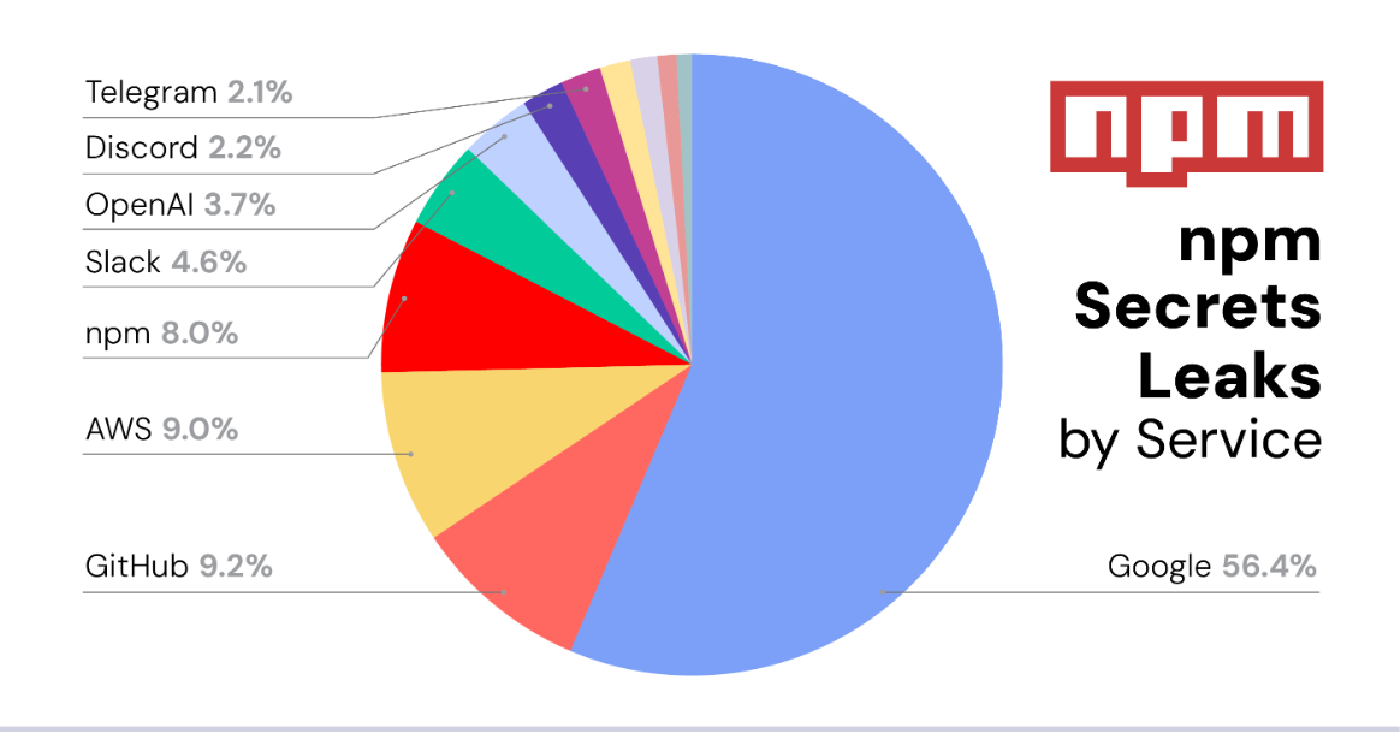
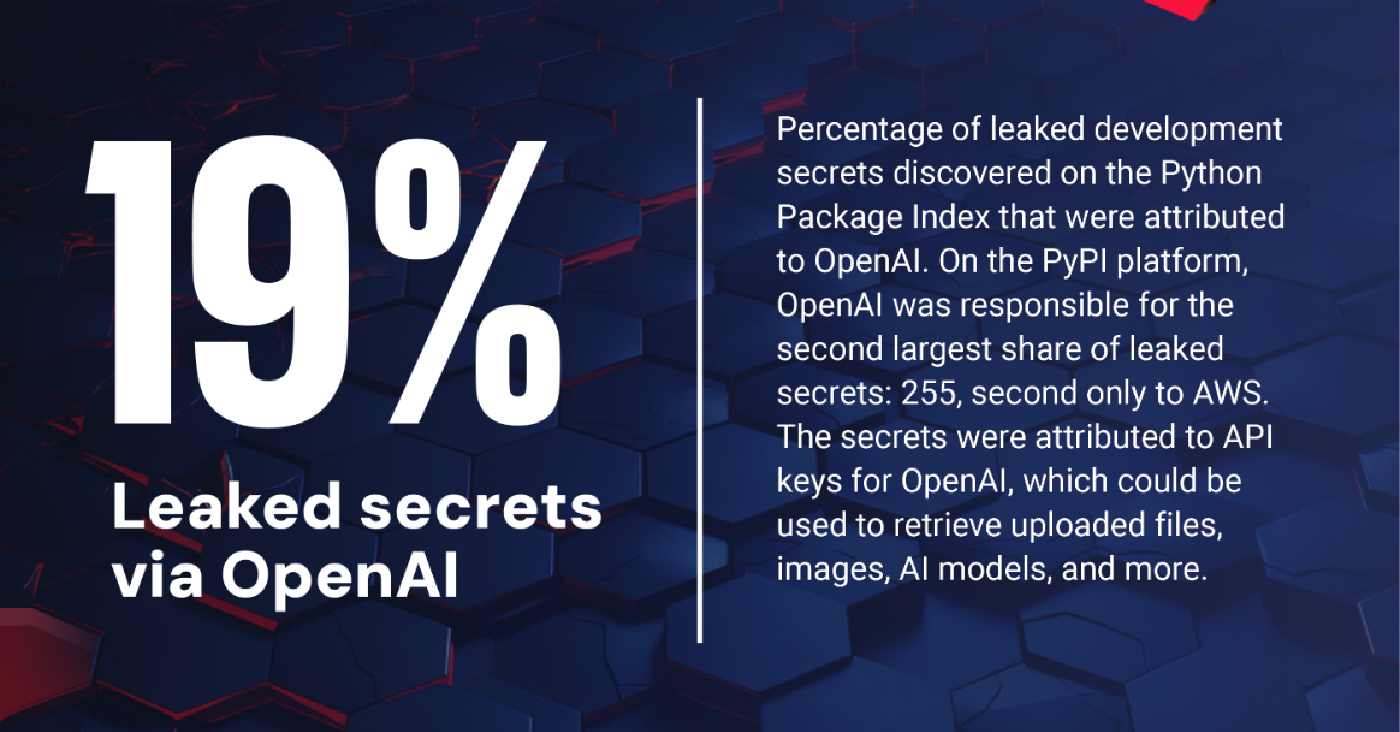
Typically, secrets are attributable to a number of sources, such as API keys, security tokens, credentials, and more that provide access to resources such as Google, GitHub, and AWS. That was the case again this year, with one notable addition to the list of top sources of leaked secrets: OpenAI, the artificial intelligence start-up behind ChatGPT. OpenAI alone accounted for 19% of all leaked secrets on the PyPI platform in 2023, as well as 18% on the RubyGEMS platform, ReversingLabs researchers discovered. Leaked OpenAI API tokens accounted for almost all of that, reflecting the growing use and popularity of OpenAI’s ChatGPT AI chatbot. As with the discovery of more than 1,500 leaked API tokens on the Hugging Face machine-learning platform, the leaks of OpenAI’s API tokens could expose sensitive files, images, and AI models for organizations with leaked tokens, according to ReversingLabs.
These changes and consistencies in the threat landscape underscore the need to continue taking software supply chain security seriously — in particular, open-source threats and secrets leaks. And while the number of threats changed this past year, the fundamentals of what needs to be protected has largely stayed the same since 2022.
Read the full report to learn more
Many of the trends identified in 2023 are likely to continue or deepen in 2024 as policymakers wrestle with the fallout of attacks such as the Clop gang’s campaign against users of Progressive Software’s MOVEIt secure file transfer application and contemplate ways to hold private-sector software producers accountable. That, along with growing scrutiny by both governments and industry regulators, means that software publishers are under growing pressure to devote resources and time to shoring up the security of their development organizations.
ReversingLabs’ new report explores that trend for 2024, as well as others, including:
- Changes in the cyber-underground
- A higher regulatory bar for incident disclosure and software supply chain security efforts
- The evolution of federal government guidance on software supply chain security
![]()
*** This is a Security Bloggers Network syndicated blog from ReversingLabs Blog authored by Carolynn van Arsdale. Read the original post at: https://www.reversinglabs.com/blog/the-state-of-software-supply-chain-security-2024-key-takeaways
如有侵权请联系:admin#unsafe.sh