2024-1-16 14:4:44 Author: securityboulevard.com(查看原文) 阅读量:16 收藏
Isn’t it fascinating that the most expensive consequence of a cyber attack is information loss, which accounts for 43 percent of the overall costs incurred?
The telecom sector, which includes the telephones, internet, cables, and aircraft, are the backbone of global connectivity, allowing each private and industrial communications across several systems. The region which includes satellite TV for internet providers, and cellphone groups are sometimes underestimated yet makes it viable for text, audio, and video to be seamlessly traded globally, strengthens the growth in plenty of sectors. Statista estimates that the total income generated by telecom carriers worldwide is 1,330 billion euros. However, the security landscape changes as the market expands and the younger age grows, leading to a surge in cyber attacks targeted at the telecom sector.
Why Telecom Industry Vulnerable to Cyber Attacks?
The telecom zone is particularly at risk of cyber attacks because of its networked structure and vital characteristic in handling big amount of private information. Below are a few reasons:
Network Intersection
In the telecommunications sector, networks are interlinked, housing extensive customer data and sensitive information. The convergence of these elements creates a scenario where attackers can inflict significant harm with minimal effort. The interconnected networks increase the risk of infiltration, potentially providing access to information across various connected systems.
Outdated Technology
The telecommunications industry continues to rely on outdated technology, exposing it to IP-based threats. Digital advancements are outpacing the migration from insecure legacy systems, leaving businesses exposed.
Sensitive Information
Telecom providers store extensive information, including financial details such as credit card information, social security numbers, contact details, etc. This information is valuable for malicious actors to share on the dark web.
Increasing Threat surface
The risk landscape is on the rise, especially with the adoption of advanced technologies like 5G. Embracing innovations expands the threat surface, requiring increased security measures to address potential points of vulnerability.
Lack of Awareness
Insufficient technical knowledge and awareness among the team pose significant challenges. Inadequate password practices and indiscriminate data sharing frequently expose the team to avoidable risks, emphasizing the need for comprehensive education.
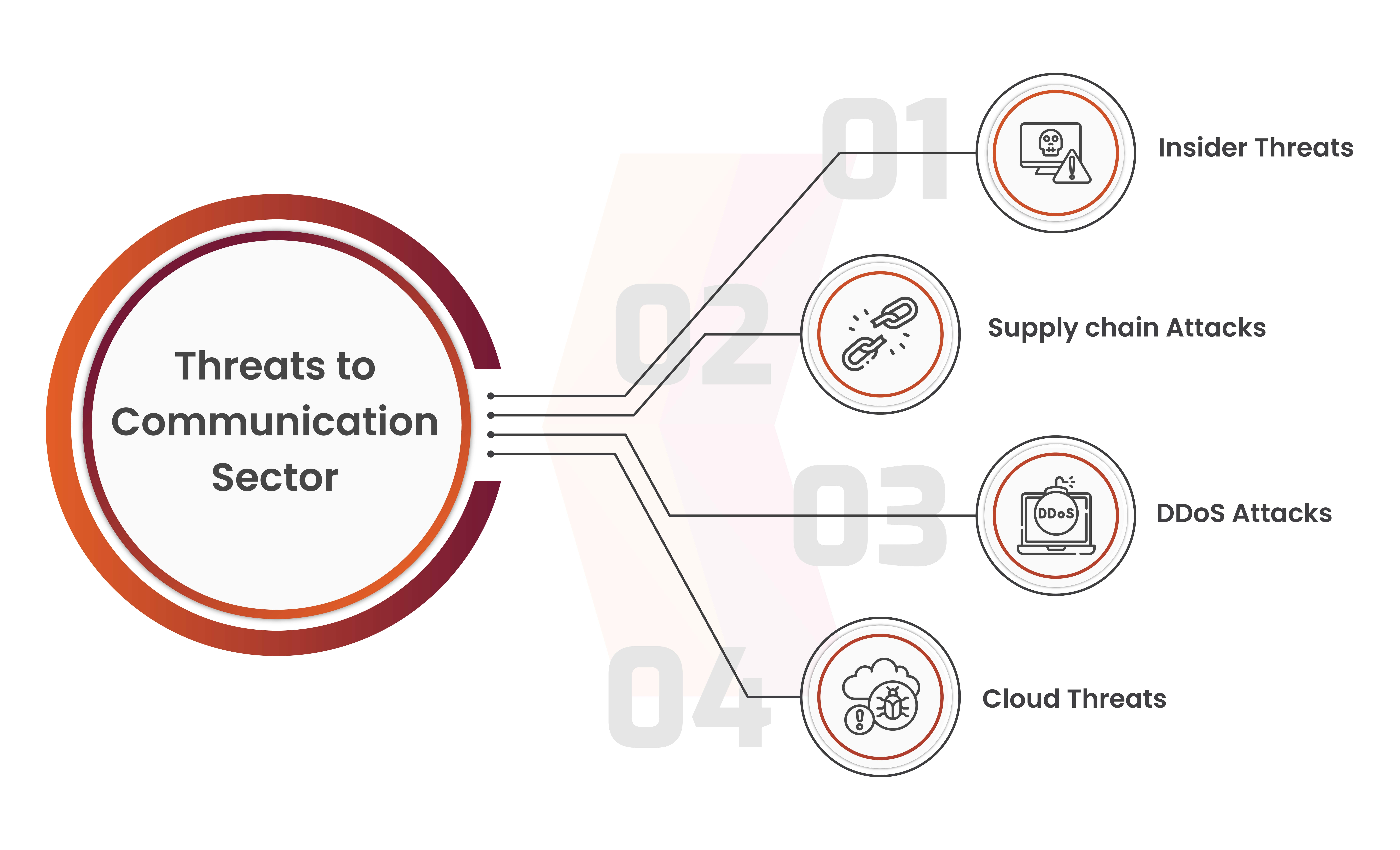
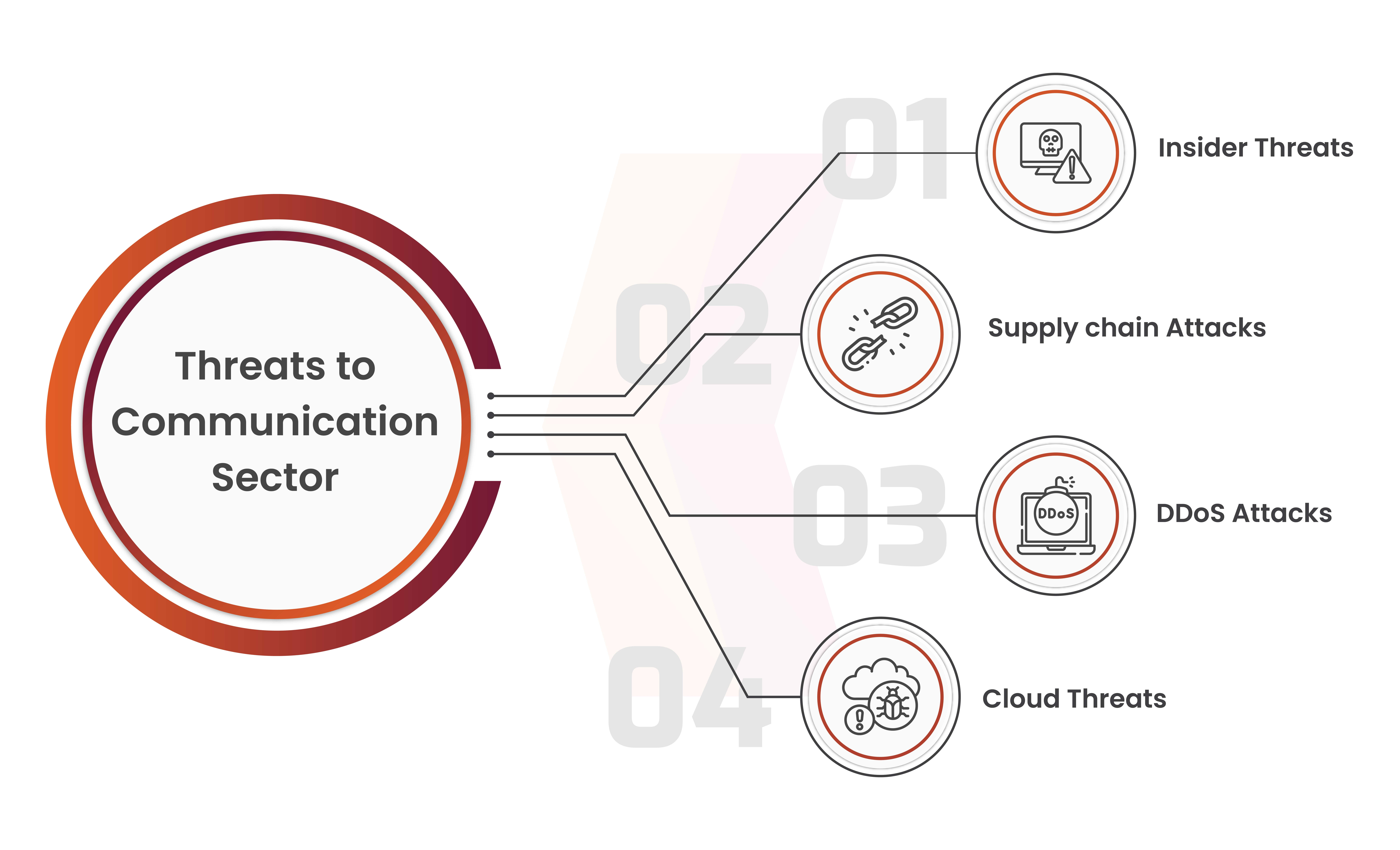
Major Threats to Communication Sector
The communication sector faces a spectrum of threats that jeopardize its operational integrity and the security of sensitive information. Understanding these challenges is crucial for implementing effective safeguards. Here are some major threats to the telecommunications sector:
Insider Threats
Insider threats are extremely risky for the telecom industry because they include both malevolent actions by employees and a lack of knowledge about the risks involved. Cyber threats have increased because of the rise in remote painting styles and connections to unprotected networks. Among these concerns, phishing stands out as a prominent issue, involving cyber attackers sending malicious links through emails or messages.
Supply Chain Attacks
The telecom sector faces cybersecurity risks from interactions with third-party entities like carriers, internet hosts, data control products, managed service providers, and partners. Flaws in those third-party vendors’ cybersecurity maturity can act as a backdoor access point for hackers into the telecom network, emphasizing how important a strong supply chain is.
DDoS Attacks
Service continuity is essential in the telecommunications industry. DDoS attacks, which aim to interfere with services, can affect millions of users, stop companies from operating, and cause large losses in terms of money.
Cloud Threats
Telecom networks are progressively adopting cloud computing for operational support. While considered more secure than on-premise infrastructure, a cloud network isn’t entirely immune it poses its own security challenges. A successful attack on the cloud network can simultaneously affect multiple virtual machines, posing a significant risk.
A Brief about the Incident
The cyber attack on Kyivstar, Ukraine’s largest telecom operator, stands out as a highly impactful and unprecedented incident. Unfolding over several days starting on December 12, the attack disrupted services for around 24 million users, destroying the core infrastructure – a first-of-its-kind destructive cyber assault on a telecoms operator. Illia Vitiuk, the Head of SBU’s cybersecurity, disclosed that the hackers known as the Russian military unit Sandworm had a dual objective. Their goals encompassed delivering a psychological blow, gathering intelligence, and potentially stealing personal information through diverse communication channels.
The response to the attack involved a collaborative effort between the SBU and Kyivstar to restore systems swiftly, preventing further damage. The incident underscored the significant impact on Ukrainians, with disruptions like ATM and air-raid siren malfunctions. It highlights the critical interconnectivity of infrastructure and the urgent need for enhanced cybersecurity measures. The Kyivstar intrusion highlights the need for preemptive steps to guard against similar future occurrences and serves as a sobering reminder of the constantly changing and persistent cyber threats faced by multinational locations.
Book a Free Consultation with our Cyber Security Experts

How Pentesting Could Have Prevented this Attack?
The Kyivstar attack serves as a reminder of how vital robust Pentesting services are to protecting businesses against evolving cyber threats. To find shortcomings in an employer’s cybersecurity posture, VAPT involves mimicking real-world worldwide attacks and methodically evaluating systems for vulnerabilities. The Kyivstar attackers exploited numerous device vulnerabilities, evading detection for an extended period. This emphasizes the importance of regular pentesting to proactively identify and block potential access points for malicious actors.
Thorough pentesting in the Kyivstar incident could have identified and fixed access points exploited by Sandworm, reducing the cyberattack’s severity and preventing damage to the middle telecom infrastructure.
The increasing importance of enterprises on digital infrastructures and networked technologies means that investing in pentesting becomes a crucial component of a holistic cybersecurity strategy. Routine testing not only uncovers vulnerabilities but also keeps firms ahead of evolving cyber threats.
Conclusion
The cyber attack on Kyivstar, Ukraine’s largest telecommunications operator, emphasized the substantial cost of data loss, accounting for 43% of the total expenses. SBU’s cybersecurity head, Illia Vitiuk, revealed exclusive details, issuing a warning to Ukraine and the broader Western world. The attack in December revealed vulnerabilities in the IT infrastructure, leading to severe disruptions. The telecom sector is vulnerable because of its historical background, interconnected communities, and ignorance. Some examples of cyber risks include DDoS attacks, cloud-related issues, insider threats, and flaws in the delivery chain. The incident highlights the pivotal role of pentesting in defending against cyber attacks. It also emphasizes the necessity of adopting proactive cybersecurity measures to ensure resilience.
Kratikal a CERT-In empanelled auditor plays a crucial role in bolstering security. Leveraging our unparalleled experience, we offer insightful analysis and robust defense against the persistent threat of cyberattacks. Partnering with Kratikal enables proactive identification and resolution of security flaws, thwarting malicious hackers’ attempts to exploit vulnerabilities.
Ref: https://therecord.media/russians-infiltrated-kyivstar-months-before
The post Cyber Attack on Telecommunications Company appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/cyber-attack-on-telecommunications-company/
如有侵权请联系:admin#unsafe.sh