2024-1-12 20:0:0 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
The threat of malware has existed for decades, yet it still poses significant challenges to traditional cybersecurity solutions. Its ability to adapt and evolve – now even more so thanks to the proliferance of generative AI – makes it increasingly difficult for conventional defenses to effectively detect and mitigate such threats.
Data from AV-TEST reveals the alarming rate of malware proliferation: over 450,000 new malicious programs and potentially unwanted applications (PUAs) are registered daily. This staggering statistic underscores the relentless efforts of cybercriminals, and malware’s continuous transformation. That’s why companies can no longer rely on legacy solutions to counter these rapidly emerging and sophisticated digital threats.

This evolving nature of malware is particularly evident in its sophisticated concealment methods. It often hides within seemingly safe files, such as documents, deftly slipping past standard security measures. This stealthy approach allows malware to infiltrate systems unnoticed, causing significant damage before detection. Which means, there’s still a lot to learn.
The Current State of Threat Analytics
Traditional security solutions like Antivirus (AV), Endpoint Detection and Response (EDR), and Sandboxing (SB) are all staples of malware defense, but each has significant shortcomings.
- AV solutions – rely predominantly on signature-based detection and fail to detect novel malware variants and sophisticated attacks.
- EDR systems – despite advanced features like behavioral analysis, grapple with high alert volumes, leading to alert fatigue, and may miss advanced persistent threats (APTs) due to their stealthy nature.
- Sandboxing – designed to isolate and analyze application behavior, faces evasion tactics by advanced malware that recognizes sandbox environments and is resource-intensive and less effective against non-executable attack vectors.
While each of these cybersecurity methods offer benefits in stopping and eliminating malware, none are sufficient enough alone to entirely eliminate modern-day threats.
A Large Problem with Large Consequences
Inadequate malware protection can have dire consequences across multiple domains, including breaches and data loss. Sensitive information such as personal data, intellectual property, and financial records can be compromised, leading to identity theft, financial fraud, and competitive disadvantages for businesses.
These can all result in significant financial ramifications, including:
- Direct theft losses
- Substantial costs in incident management and recovery
- Legal fees
- Regulatory fines due to non-compliance
Operational disruption is another critical impact. Malware, particularly ransomware, can paralyze essential systems and data, forcing businesses to halt operations. This disruption leads to immediate productivity and revenue loss and can have lasting effects on business continuity.
The reputational damage resulting from a malware attack is profound. The erosion of customer trust and negative public perception can have long-lasting effects on customer loyalty and business relationships. These incidents often culminate in extensive indirect expenses from lost business opportunities and a tarnished reputation.
Lastly, there are the legal and regulatory repercussions. Organizations can face lawsuits and hefty fines, especially if deemed non-compliant with data protection regulations.
Finding a Solution in Threat Analytics
For organizations seeking an advanced level of protection beyond what standard detection-response solutions offer, Votiro is a game-changer. Votiro fills the gaps in AV, EDR, and Sandboxing. It delivers actionable insights and offers a deeper, more nuanced understanding of file-based threats.
These insights encompass a range of analyses, from scrutinizing suspicious file content to macro analysis and from examining external actions to true-typing files. Such comprehensive scrutiny ensures that organizations are reacting to threats and proactively safeguarding their digital assets with a more robust, all-encompassing cybersecurity strategy.
The Power of Macro Analysis
In-depth macro analysis is unparalleled by other analytics solutions. Unlike solutions that focus heavily on AI-driven strategies, Votiro delves deeper into true typing, macro analysis, and scrutinizing external actions. This thoroughness gives users insight and detail not typically available in standard analytics tools.
Votiro’s approach transcends the capabilities of traditional detection-based methods and real-time analytics commonly seen in antivirus software and sandboxing techniques. By focusing on a more granular level of analysis, Votiro offers a unique perspective that is both proactive and preventive, allowing users to understand and counter threats with a precision and depth that goes beyond the industry norms.
Gaining Visibility

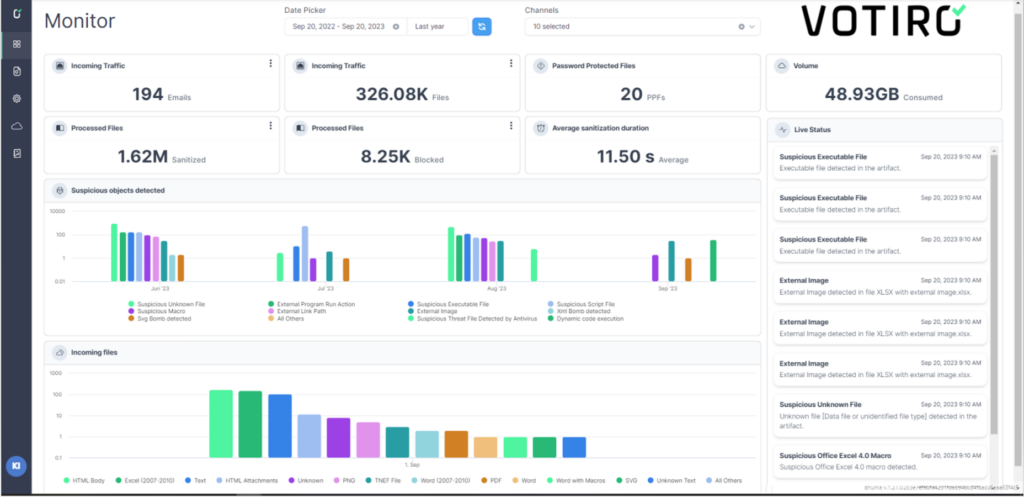
The Votiro Threat Analytics Dashboard (Monitor Mode)
Votiro’s Threat Analytics Dashboard is a cutting-edge solution transforming how Security Operations Center (SOC) teams and cybersecurity professionals approach threat analysis. This powerful tool provides detailed, actionable analytics on known and unknown malicious and suspicious elements hidden within files.
Its strength lies in offering SOC teams the actionable insights they need to efficiently and effectively investigate true positives. By focusing on accuracy and relevance, Votiro’s Threat Analytics Dashboard significantly reduces the number of false positives – a common challenge in cybersecurity that can lead to alert fatigue and distract from genuine threats. This precise identification prevents file-based risks and drastically cuts down the time required to differentiate between false and true positives.
The Threat Analytics Dashboard’s comprehensive interface revolutionizes how IT teams and key stakeholders manage and respond to potential threats, ensuring a more secure and resilient digital environment.
Unlocking the Power of Threat Analytics
Accessing Votiro’s advanced analytics is easy – it’s included as part of the package. You also get to choose how you react to threats – or don’t. Whether you’re interested in learning about your risk surface without taking action or want to start seeing comprehensive analytics and sanitizing malicious content at the same time, Votiro gives you the choice. However, when you’re ready for the full Votiro experience, the Threat Analytics Dashboard ensures you’re protected against known threats and equipped with the tools and insights needed to understand and act on potential vulnerabilities in your environment.
Contact us today to learn how you can take full advantage of real-time, in-depth threat analytics to better protect your endpoints and prepare for future threats.
*** This is a Security Bloggers Network syndicated blog from Votiro authored by Votiro Team. Read the original post at: https://votiro.com/blog/how-votiro-is-redefining-threat-analytics/
如有侵权请联系:admin#unsafe.sh