Table of Contents
In recent and alarming cybersecurity developments, Volexity researchers have discovered that attackers are exploiting two distinct zero-day vulnerabilities in a coordinated manner to enable unauthenticated remote code execution (RCE). These vulnerabilities are identified as CVE-2023-46805 and CVE-2024-21887, posing a significant threat when combined. Moreover, their severity has been recognized by the Cybersecurity and Infrastructure Security Agency (CISA), leading to their inclusion in the agency’s Known Exploited Vulnerabilities (KEV) catalog. This addition to the CISA’s Known Exploited Vulnerabilities catalog highlights the critical nature of these vulnerabilities and the urgent need for awareness and action, especially given that both CVEs are actively exploited in the wild.
- CVE-2023-46805: This vulnerability is an authentication-bypass issue, rated with a concerning CVSS score of 8.2.
- CVE-2024-21887: A more severe command injection flaw was found in multiple web components, earning a CVSS score of 9.1.
The critical factor here is the combination of these two vulnerabilities. When CVE-2024-21887 is used in tandem with CVE-2023-46805, the requirement for authentication is effectively bypassed. This loophole offers threat actors an open door to craft malicious requests and execute arbitrary commands on affected systems, significantly elevating these vulnerabilities’ risk and potential impact.
The Impact of Dual Zero-Day Threats in Ivanti Connect and Policy Secure Gateways
These two severe vulnerabilities in Ivanti Connect and Policy Secure Gateways have been exploited with alarming consequences. These vulnerabilities simplify the process for attackers to execute commands on the system. Exploiting these vulnerabilities could lead to a series of critical incidents: sensitive configuration data could be illicitly extracted, existing files on the system could be stealthily altered, remote files could be surreptitiously downloaded, and a covert reverse tunnel could be established from the Ivanti Connect Secure (ICS) VPN appliance, potentially amplifying the severity of an attack.
Vulnerable Versions
These vulnerabilities affect all currently supported versions of the products. Mitigations are already available for immediate implementation. Ivanti is offering these mitigations while developing a comprehensive patch is underway.
Ivanti strongly advises all customers to refer to the KB Article for detailed guidance on implementing the necessary mitigations.
How can Qualys assist organizations, and what actions should these organizations undertake?
Organizations using Ivanti Connect and Policy Secure Gateways must urgently inventory and scan their systems for CVE-2023-46805 and CVE-2024-21887 vulnerabilities. The critical concern arises from the combination of these vulnerabilities. When exploited together, they eliminate the need for authentication, allowing threat actors to execute arbitrary commands on affected systems. These incidents highlight the urgent need for immediate action to mitigate the risk and protect against the high-impact consequences of these vulnerabilities.
Qualys QID Coverage
Qualys has released QIDs, available starting from version VULNSIGS-2.5. 959-2 of the vulnsigs.
| QID | Title | Release Version |
| 731074 | Ivanti Connect Secure (ICS) and Ivanti Policy Secure Gateway Multiple Vulnerabilities | VULNSIGS-2.5.959-2 |
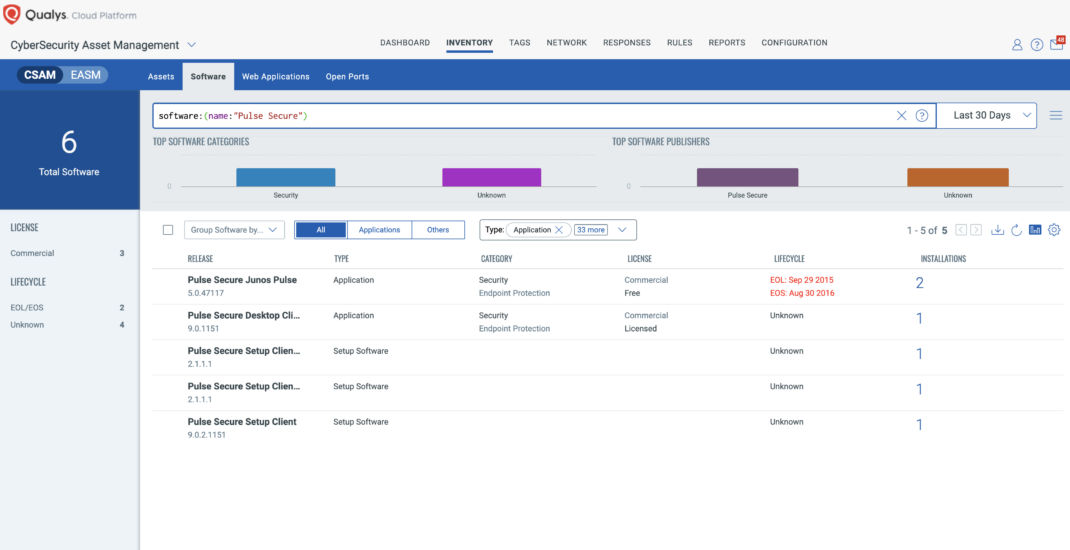
Qualys CSAM Query
Go to CSAM, Inventory, under the Software tab search with the following QQL:
software:(name:"PULSE SECURE")

Conclusion
In summary, the recent discovery of two zero-day vulnerabilities, CVE-2023-46805 and CVE-2024-21887, in Ivanti Connect Secure and Policy Secure Gateways poses a significant cybersecurity threat. Qualys’ comprehensive product suite plays a crucial role in assisting organizations to counter this threat. Organizations are urged to prioritize these vulnerabilities due to their high impact and the ease of exploitation by threat actors. Immediate action is essential to mitigate the risks and protect systems from these severe security threats.
Contributors
- Siddharth Bhatia, Principal Product Manager, CSAM