
2024-1-11 02:16:20 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Looking ahead to the digital terrain of 2024, it is clear that cybercrime marketplaces are on the brink of a surge, bringing about a transformative shift where every cyber threat transitions into an “as-a-service” model. The term “as-a-service” refers to the provision of specific functionalities or tools as a service, typically offered on a subscription or pay-as-you-go basis. This approach democratizes access to cyber threats, enabling even those with limited technical expertise to deploy sophisticated attacks.
The impact of this shift is particularly pronounced in the realm of bot protection. Traditionally, cybercriminals had to possess specialized knowledge to develop and deploy bots for various malicious purposes, such as account takeovers and credential stuffing. However, the cybercrime-as-a-service (CaaS) model now allows threat actors to easily access pre-built, user-friendly tools and services designed for specific malicious activities.
Because these threat services are not constrained by geographical boundaries, cybercriminals from all around the world can participate.This accessibility significantly lowers the entry barrier for individuals looking to engage in cybercrime.

Bots, once considered the domain of skilled hackers, are now available as turnkey solutions, making them more widely accessible to a range of threat actors. Consequently, organizations face an increased threat landscape, as cybercriminals leverage these readily available “as-a-service” offerings to automate attacks, scale their operations, and maximize their impact.
RECOMMENDED RESOURCE
Foreseeing the Future Threatscape: 2024’s Bad Actor Forecast
Threats Now Available “As-a-Service”
The “as-a-service” model has transformed the landscape of cybercrime, offering various attack vectors through different specialized services. This rise has commodified specific cyber threats of the past and given them new life.
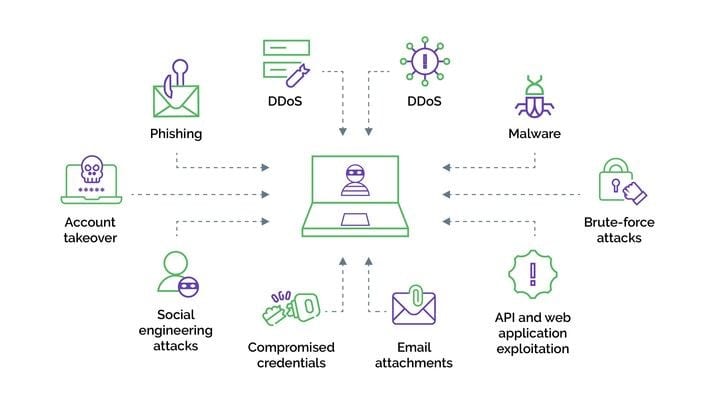
Take Evil Proxy, for example. Evil Proxy as-a-service marks a concerning advancement in the world of cyber threats, as the CaaS model is now able to transform almost any specific threat into a criminal service accessible to regular users. Evil Proxy-as-a-Service, in essence, offers cybercriminals a user-friendly platform to obfuscate their locations, skillfully bypassing security measures. This innovation signifies the transformation of a once-specialized threat into a readily available service, now accessible to anyone. As this service intertwines with phishing activities, it enhances the stealth and efficiency of cyber threats.
While just about any threat, such as Evil Proxy, can be codified into a service, some of the notable attack vectors available through “as-a-service” platforms include:
- Phishing-as-a-Service (PhaaS) is a cybercriminal offering that extends beyond the conventional, allowing individuals not only to access tools and resources for credit card fraud but also to use GenAI to craft sophisticated phishing campaigns with great precision.
- Fraud-as-a-Service (FaaS) is similar to CaaS but not entirely the same. While the CaaS model is a comprehensive concept encompassing a spectrum of cybercriminal activities offered as services in the underground economy, FaaS is a subset that specifically focuses on services facilitating financial fraud, such as credit card fraud, identity theft, and money laundering.
- Carding Services refer to a type of criminal service where individuals can access tools, resources, or expertise for carrying out credit card fraud. This can include various activities such as buying and selling stolen card information, using compromised card data for unauthorized transactions, and even tutorials or guidance on how to conduct carding activities.
- Credential Stuffing Services enable attackers to use services that automate the testing of large sets of username and password combinations on various websites to gain unauthorized access. Bad actors employ credential stuffing to rapidly input credentials, exploiting the tendency of users to reuse passwords across multiple platforms.
- Exploit Kits-as-a-Service provides cybercriminals with pre-packaged tools and exploits to target vulnerabilities in software and systems.
- Social Engineering Services allow criminals to hire services for social engineering attacks, manipulating individuals or organizations to divulge sensitive information.
- Scraping-as-a-Service provides web scraping capabilities on a commercial or subscription basis. While not inherently malicious, scraping-as-a-service can be used for illicit purposes like copyright infringement, unauthorized data access, and competitive espionage.
- Ransomware-as-a-Service (RaaS) enables attackers to rent ransomware services, allowing them to launch ransomware attacks without extensive technical expertise.
- Malware-as-a-Service (MaaS) is malicious software, including trojans, viruses, and other malware, that can be obtained or rented through these services.
- Distributed Denial of Service-as-a-Service (DDoSaaS) helps cybercriminals hire DDoS attacks on-demand to overwhelm a target’s network, causing disruption or downtime.
- Traffic Distribution Systems (TDS) are services that help cybercriminals distribute malicious traffic efficiently, redirecting victims to various exploit pages.

RECOMMENDED NEWS
Disrupting the Gateway Services to Cybercrime
Threat Intelligence Confirms Escalating “As-a-Service” Trend
Global threat intelligence data sourced from our recent Bot Abuse Analysis provides compelling evidence of the escalating trend of “as-a-service” threats in the digital landscape of 2024. We observed a surge in cybercriminal activities utilizing ready-to-go solutions from marketplaces, highlighting the growing accessibility and appeal of “as-a-service” offerings. From automated bots facilitating account takeovers to streamlined tools for phishing to a rash of GenAI-based scraping attacks, our data underscores the ease with which threat actors are adopting various CaaS-based services.
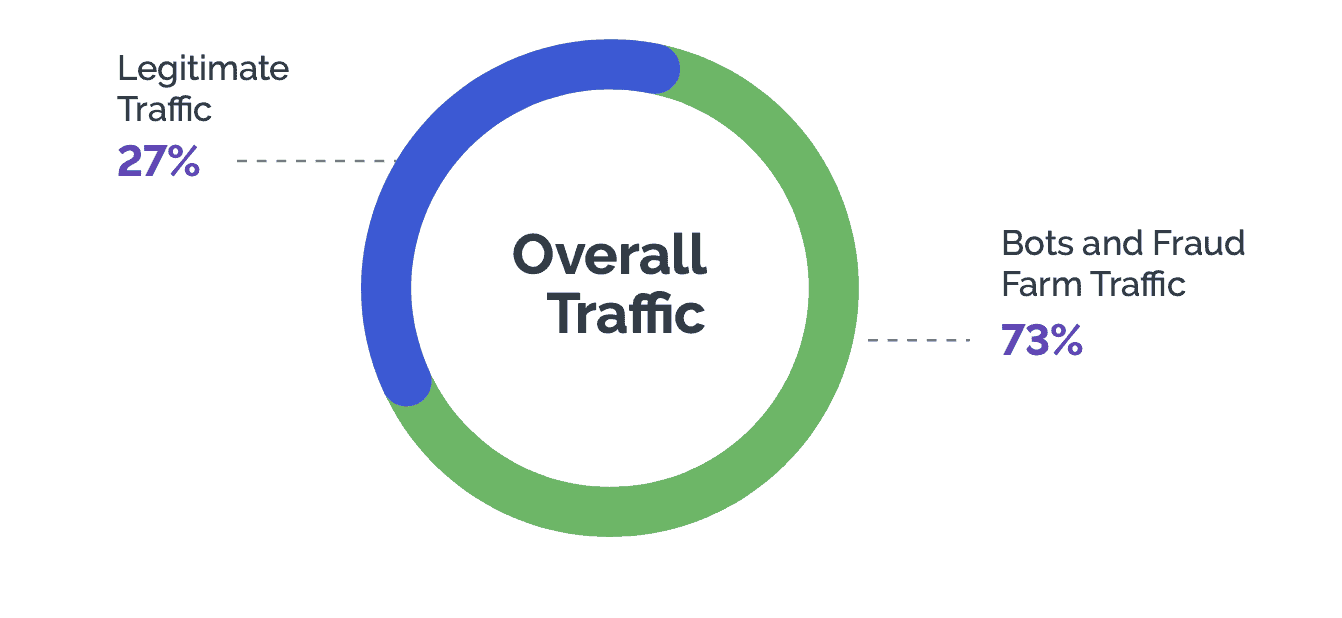
In an era where 73% of all internet traffic is currently (Q3, 2023) composed of malicious bots and related fraud farm activities, online businesses need accurate threat analysis to understand the digital terrain ahead—and the rising tide of “as-a-service” threats.
Our analysis revealed a staggering 167% surge in bot attacks during the initial six months of 2023. This surge was primarily driven by a remarkable 291% increase in the prevalence of intelligent bots, capable of executing intricate, context-aware interactions. Notably, these attacks weren’t confined to bots alone. The research uncovered a compelling trend—when efforts to thwart fraudster bots were successful, threat actors seamlessly transitioned their tactics to human fraud farms, resulting in a noteworthy 49% uptick from Q1 to Q2 of 2023.
This threat data highlights the evolving tactics employed by cybercriminals, specifically in the context of bot attacks. The significant increase in intelligent bots, capable of sophisticated and context-aware interactions, indicates a more advanced and adaptive approach to cybercrime. The fact that fraudsters are now pivoting to human fraud farms when faced with obstacles in bot attacks underscores the dynamic nature of these cybercrime operations. This tactical shift demonstrates a level of organization and flexibility unseen until now, all characteristics of “as-a-service” models.
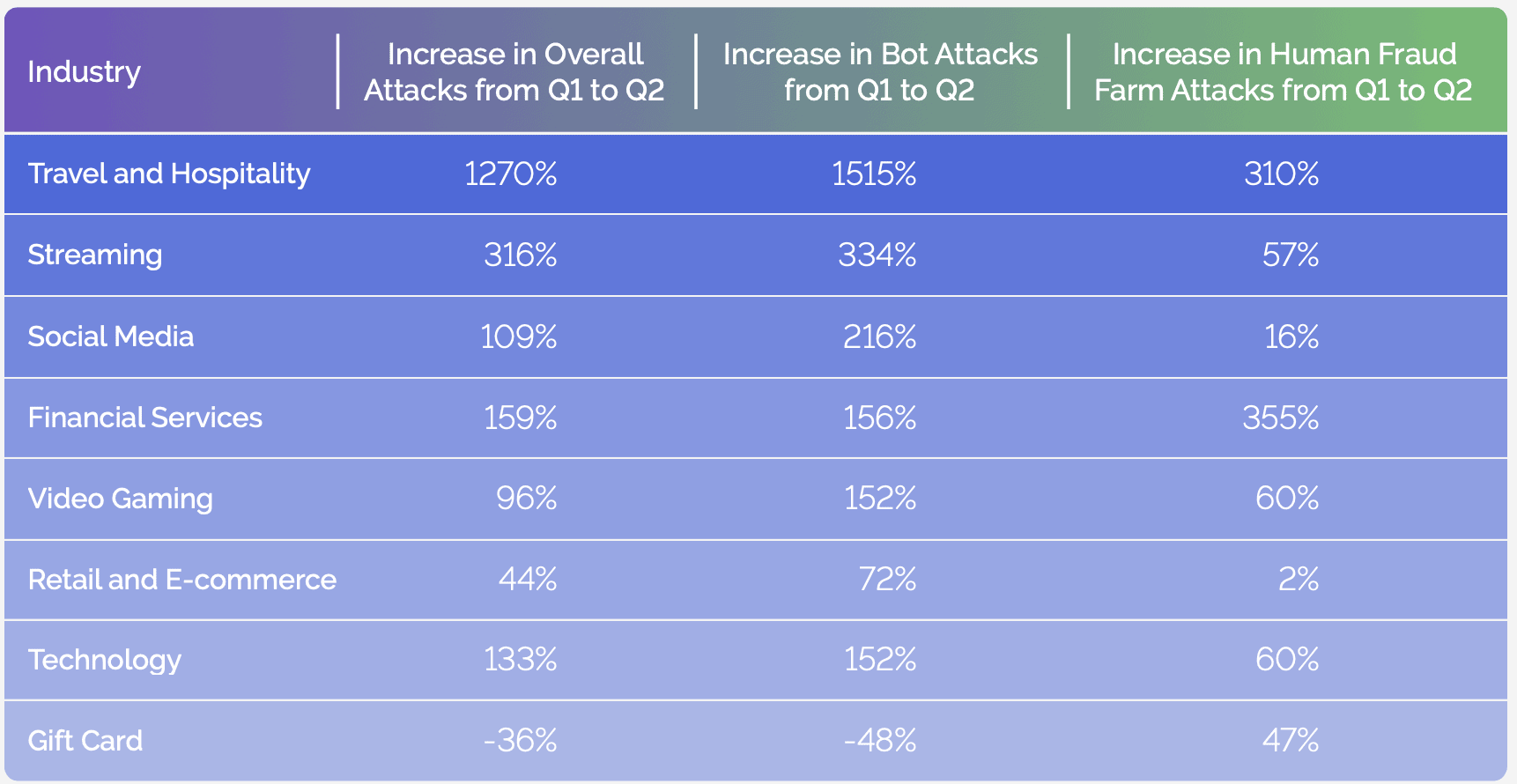
In a broader context, the data implies that cybercriminals are not only leveraging automated tools (bots) but also integrating human resources to carry out fraudulent activities. This aligns with the CaaS concept, where malicious actors may purchase or rent various components of their operations, creating a more scalable and efficient model for carrying out today’s attacks.
Defenders, including cybersecurity professionals, law enforcement agencies, and organizations, face the challenge of combating not just individual threats but an entire ecosystem. The need for a comprehensive and collaborative approach to bot prevention has never been more critical.
Arkose Labs’ Take on the Cybercrime Marketplace
Arkose Labs disrupts the financial incentive driving bot attacks, offering a comprehensive solution for long-term bot mitigation and account security. Focused on safeguarding global companies at critical user touch-points like account login and registration, we go beyond traditional measures. Our approach involves uncovering hidden attack signals and dismantling attackers’ return on investment (ROI), all while maintaining a smooth user experience.
In the face of the evolving “as-a-service” phenomenon, Arkose Labs stands as a stalwart defender. Our innovative bot detection and mitigation platform, Arkose Bot Manager, goes beyond conventional protection. It scrutinizes data from user sessions, assessing context, behavior, and past reputations to classify traffic by risk profile. By presenting enforcement challenges to suspicious traffic, we effectively differentiate between legitimate users and fraudsters, ensuring businesses are shielded against the dynamic landscape of “as-a-service” threats.
Beat the bots and book a demo!

RECOMMENDED RESOURCE
From reCAPTCHA to Arkose Labs: Companies that Switched and Won
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Jenn Jeffers. Read the original post at: https://www.arkoselabs.com/blog/cybercrime-marketplaces-soar-in-2024-all-threats-now-available-as-a-service/
如有侵权请联系:admin#unsafe.sh