2024-1-9 14:17:8 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
The Digital revolution has transformed our world, and its impact is particularly evident in the realm of Operational Technology (OT), from Industrial Control Systems to power grids and water treatment plants. They all have very critical infrastructure and cyber-attacks on OT industries such as the same has increased in the past few years but how does the attacker get into the Critical environment, how does OT malware work, and what are the possible ways for attackers to get into the OT environment, and how to be protected from the OT attacks? There are many other questions when it comes to Operational technology attacks. So, let’s find the answer to all the questions by looking into some history of OT attacks and malware.

Table of Contents
We systematically categorize the attacks into direct and indirect vectors. Direct attacks are those that target OT systems through the exploitation of inherent vulnerabilities within the OT devices and protocols themselves. Indirect attack, on the other hand, involve entry points through connected IT systems, supply chain compromises, or human vectors such as phishing or insider threats, so seeing some previous examples of OT malware and how they got into the OT network let’s understand the possible ways the attacker or malware can get into the critical environment.
OT MALWARES
Our analysis begins with an examination of the infamous Stuxnet incident, Stuxnet is the first infamous OT malware which was discovered in 2010, It was designed to target Industrial control systems, even though Stuxnet is not actively spreading still it is considered a significant threat as it was complex and advanced malware. It was able to compromise systems with infected USBs, once the system gets infected Stuxnet attempts to update its code from the internet, it was also able to bypass firewalls and it was continuously spreading through the local communications network of SCADA systems, even if the compromised device does not have direct access to Internet Stuxnet could update itself. Once the targeted controller gets infected the malware changes its operation,
PLC rootkit modifies the controller code to perform an attack and record received data. Once the data has been recorded for some time, the malware starts sabotaging the physical systems. While the malware changes the control signal sent to actuators, it also hides the damage by feeding the previously recorded data to SCADA’s monitoring system.
INDUSTROYER
Industroyer is a type of OT Malware designed to target Industrial control systems used in electrical substations, it supports four critical industry protocols listed below:
- IEC 101
- IEC 104
- IEC 61850
- OLE for Process Control Data Access.
The Threat Actor who developed the Industroyer seems to have a very good understanding of Critical Infrastructure and has built the backdoors depending upon the organization, the backdoor is designed to work only in one specific organization. It was first seen in 2016 when it attacked Ukraine’s power grid and after some years again in 2022 the second variant of Industroyer came to light when it attacked operational technology supporting power grid operations in Ukraine.
Let’s see some technical analysis of INDUSTROYER and Its Variants:
INDUSTROYER
The attacker first installs the Main Backdoor which connects to a remote Command and control server using HTTPS to receive commands from threat actors and they also use the proxy address.
The command-and-control server used by the backdoor uses the Tor software and Once It is connected to its remote C&C server, the Backdoor component sends the below-mentioned data in POST-request:
- the globally unique identifier (GUID) string for the current hardware profile retrieved via GetCurrentHwProfile.
- the version of the malware
- the hardcoded ID of the sample
- the result of any previously received command.
Once an attacker gains administrator privileges, they upgrade the main backdoor to execute as a window service, it is achieved by replacing the ImagePath registry value of an existing, non-critical Windows service with the path of a new backdoor binary. The attacker also makes some changes in the system like inserting malicious code in Windows Notepad so that each time the application is launched the malicious code will also execute. The inserted malicious code is obfuscated but once the code is decrypted it connects to the Control and command server which is different from the C&C server linked to the main backdoor and then it downloads the payload which is in the form of shellcode that is loaded directly into memory and executes.
How to get started with OT security
The New Backdoor helps in maintaining persistence and allows the threat actor to regain access if the main backdoor got disabled or detected. Now the two threads are created, one is responsible for loading a payload DLL and another one is responsible for loading the Data wiper.
Industroyer 2
On the other hand, the Industroyer variant uses Logic bomb functionality, It was deployed to the targeted machine as a Windows executable, and execution is scheduled. It is written in C++ and uses only IEC- IEC 60870-5-104 (IEC 104) protocol to modify the state of the Remote terminal unit.
Sandworm, The Russian state-sponsored advanced Persistent threat group was behind the Industroyer attacks, The threat group has been active since 2007, and here are the techniques used by Sandworm for Industroyer2:

Fig:1
In Addition to carrying out the attack on Ukraine’s Electrical substation Sandworm has used some other malware such as CaddyWiper, AWFULSHRED, SOLOSHRED, and ORCSHRED, where CaddyWiper and Industroyer2 were used for ICS network and ORCSHRED SOLOSHRED and AWFULSHRED was used for Linux and Solaris network, it was deployed as single executable “108_100.exe” file via scheduled task,
The new variant of this malware shares some similarities with its older version as they both are built using the same source code of payload 104.dll of the IEC 104 protocol. INDUSTROYER2 is highly configurable and hardcoded, it stores the configuration in separate. INS file and it can communicate with multiple devices at once. Before connecting with the victim system, it terminates the legitimate process and renames the application by adding the extension .MZ.
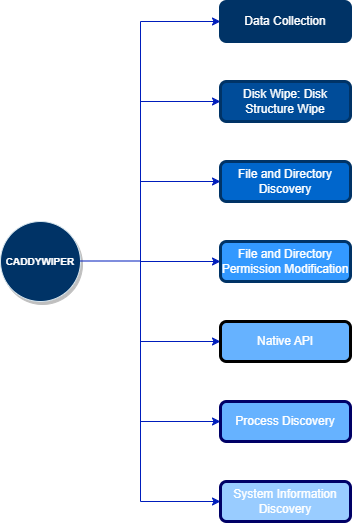
In Coordination with the deployment of Industroyer 2 within the Industrial control system network, the attacker introduced an updated variant of CaddyWiper malware. It is a destructive data wiper that is used to wipe the data in of ICS network and the technique that is used for this malware is mentioned below in Fig:2.

Fig:2
Some Pointers to be noted for CaddyWiper.
- It takes ownership of the compromised system and overwrites the files.
- It obliterates information about the physical drive’s partitions, including the Master Boot Record, GUID Partition Table, and Partition entries.
- It lists all the files and directories on the infected host.
- It modifies access control list (ACL) entries to seize ownership of files.
- It can resolve and utilize APIs, including “SeTakeOwnershipPrivilege” which is important for taking ownership of system objects.
- It gathers a list of currently running Processes.
- It can use “DSRoleGetPrimaryDomainInformation” to determine the role of the infected machine within a network.
CosmicEnergy
CosmicEnergy is the latest example of specialized operational technology malware that targets Industrial control systems and mainly focuses on disruption in electrical grids, it shares some similarities with Industroyer and its variants by interacting with IEC-104 protocol to cause electric power disruption same as INDUSTROYER and issues IEC-104 ON/OFF commands to interact with RTUs.
CosmicEnergy malware does not have built-in functionality to autonomously reconnaissance, discover, and identify target systems in the network, due to this limitation the attacker must conduct prior reconnaissance, like gathering the IP address of the MSSQL server and target IEC-104 device and credentials, identifying critical systems and their vulnerabilities, etc. CosmicEnergy malware potentially involves using an MSSQL server as a gateway to access OT systems and once the attacker gains access, they can manipulate power line switches and circuit breakers, leading to power disruptions. Malware achieves this by using PIEHOP AND LIGHTWORK.
PIEHOP
- It is a Python-based disruption tool that complies with PyInstaller.
- Its primary function is to connect with the specific remote MSSQL server for uploading files and issuing remote commands to an RTU.
- It uses LIGHTWORK to execute IEC-104 commands “ON” and “OFF” to the remote system and then self-deletes to cover its track.
LIGHTWORK
- LIGHTWORK is a disruption tool written in C++ that is designed to manipulate the state of RTUs over TCP using the IEC-104 protocol.
- It generates a configurable IEC-104 Application Service Data Unit (ASDU) to change the state of RTU Information Object Addresses (IOAs) to ON and OFF.
- The tool operates through command line arguments for the target device, port, and desired IEC-104 command.
Here is an attack path Diagram based on the analysis:

Fig:3
Some Techniques and tactics used by CosmicEnergy Malware:

Fig:4
Common OT Attack Entry points:
Since we now have an idea of how OT malware works let’s see the possible ways, they get the initial access/entry into the network:
Phishing emails and attachments
This remains the top entry point, where attackers send malicious emails to employees with malicious attachments to deliver malware into the network.
Unpatched Software Vulnerabilities
OT systems, their software or applications often run on older, less supported software which has a high chance of having unpatched vulnerabilities. Threat actors exploit these vulnerabilities to gain access to the network.
Remote Access Protocol
Unsecure remote access protocols such as RDP can help the attacker with a backdoor into the OT network.
Poorly Configured Devices
Devices with weak configurations, default credentials, or unnecessary enabled services can be easily exploited by attackers.
Removable Media
External hard drives, USB drives, or other removable media can be used by attackers to transfer malware into an OT network.
Supply Chain attacks
Attackers can spread through an OT network by compromising the supply chain of a vendor or service provider. This can involve introducing malware into software updates, hardware components, or other products used in Critical networks.
Lateral Movement
Once the malware has gained access to one system, the Attacker will use various techniques to move laterally throughout the network and infect other systems.
MITIGATION
- Updated and Patched Software, firmware, and OS.
- Conducting time to time Risk assessment and Gap analysis.
- Proper Network segmentation and Isolation
- Security Monitoring and Logging
- Implementing OT Intrusion Detection systems
- User Access Control and Authentication
- Secure Configuration Management
- Physical security measures
- Training and Awareness of Employees
REMEDIATION
- Containment and Isolation
- Digital Forensic Investigation
- Post-Incident Review and Improvement
- Review and update security measures
- System Restoration
IOCs
- b834ebeb777ea07fb6aab6bf35cdf07f
- 7a4e2d2638a454442efb95f23df391a1
- f67b65b9346ee75a26f491b70bf6091b
- fc4fe1b933183c4c613d34ffdb5fe758
- 11a67ff9ad6006bd44f08bcc125fb61e
- 7c05da2e4612fca213430b6c93e76b06
REFERENCE
https://www.cisa.gov/news-events/ics-advisories/icsa-10-272-01
https://www.welivesecurity.com/2022/06/13/industroyer-cyber-weapon-brought-down-power-grid/
https://attack.mitre.org/groups/G0034/
https://www.mandiant.com/resources/blog/industroyer-v2-old-malware-new-tricks
https://www.mandiant.com/resources/blog/cosmicenergy-ot-malware-russian-response
This blog has been attributed to Dipanjali Rani from Sectrio’s threat research team.
*** This is a Security Bloggers Network syndicated blog from Sectrio authored by Sectrio. Read the original post at: https://sectrio.com/analysis-of-ot-cyberattacks-and-malwares/
如有侵权请联系:admin#unsafe.sh