In October 2023, was in Flipper Zero’s unofficial Xtreme firmware implemented functionality tha 2024-1-9 17:1:50 Author: www.mobile-hacker.com(查看原文) 阅读量:19 收藏
![]()
In October 2023, was in Flipper Zero’s unofficial Xtreme firmware implemented functionality that would perform Denial of Service attack (DoS) that resulted in freezing and crashing any iPhones running the latest iOS 17. This bug was fixed in December 2023 by Apple in iOS 17.2. However, if users haven’t updated their iPhones, they could still be targeted by this attack. Based on the Reddit user, this was the case in the beginning of the 2024, where apparently everyone’s iPhone froze and restarted at a coffee shop.
Even though iPhone crash bug was fixed, still iOS, Android and Windows devices could receive annoying Bluetooth Low Energy (BLE) spam notifications. If users don’t want to receive them, they would need to turn off Bluetooth.
Portable Flipper Zero detector
In the end of December 2023, was on GitHub published a new tool called Wall of Flippers, that could detect BLE based attacks, including iOS crash. This tools is written in Python and works on any Linux and partially on Widows machines. Since it is Python, I was able to execute it on rooted Android with NetHunter flashed with custom Kernel. The important thing is, that the Kernel needs to either support built-in Bluetooth chipset or external Bluetooth dongle. You can see a demonstration below.
This portable Flipper Zero and BLE advertisement attack detector, isn’t very convenient, since it requires many prerequisites such as rooted Android, supported custom Kernel and NetHunter.
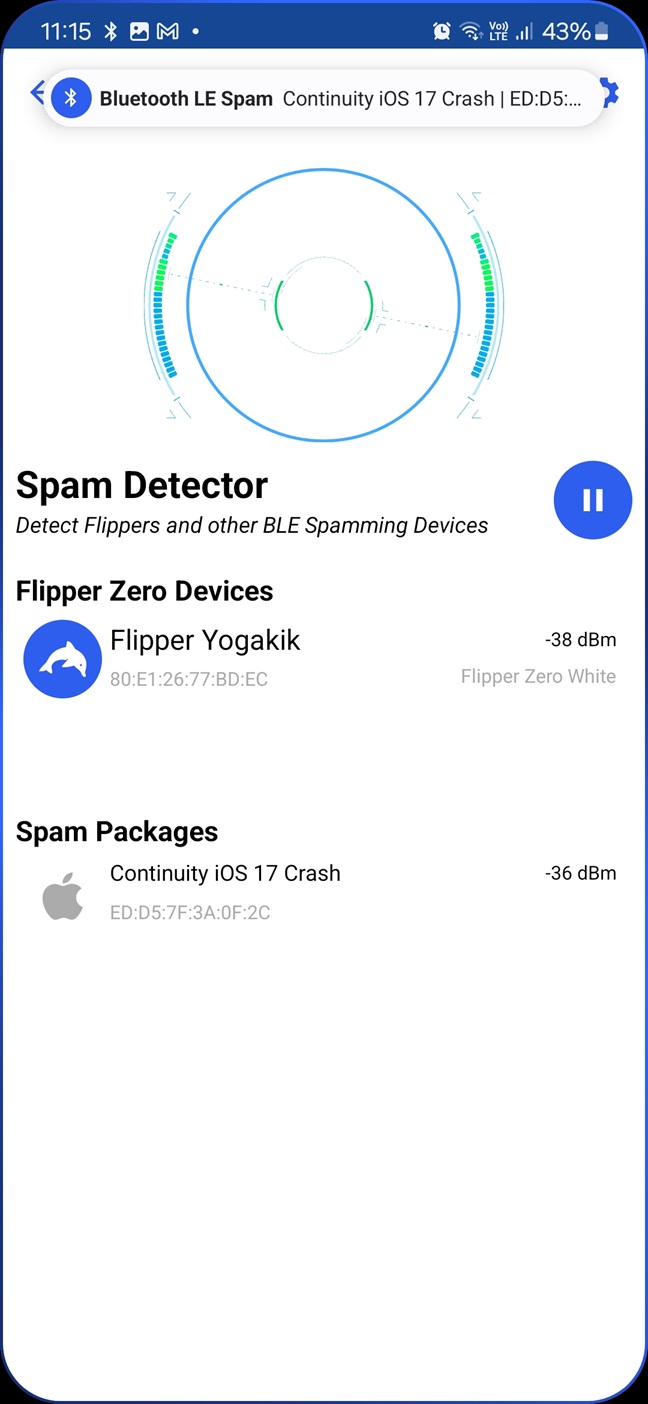
Fortunately, Simon, developer of Bluetooth LE Spam Android I introduced his app in previous post, implemented Spam Detector (see Figure 1) feature that detects nearby spamming devices such as Flipper Zero.
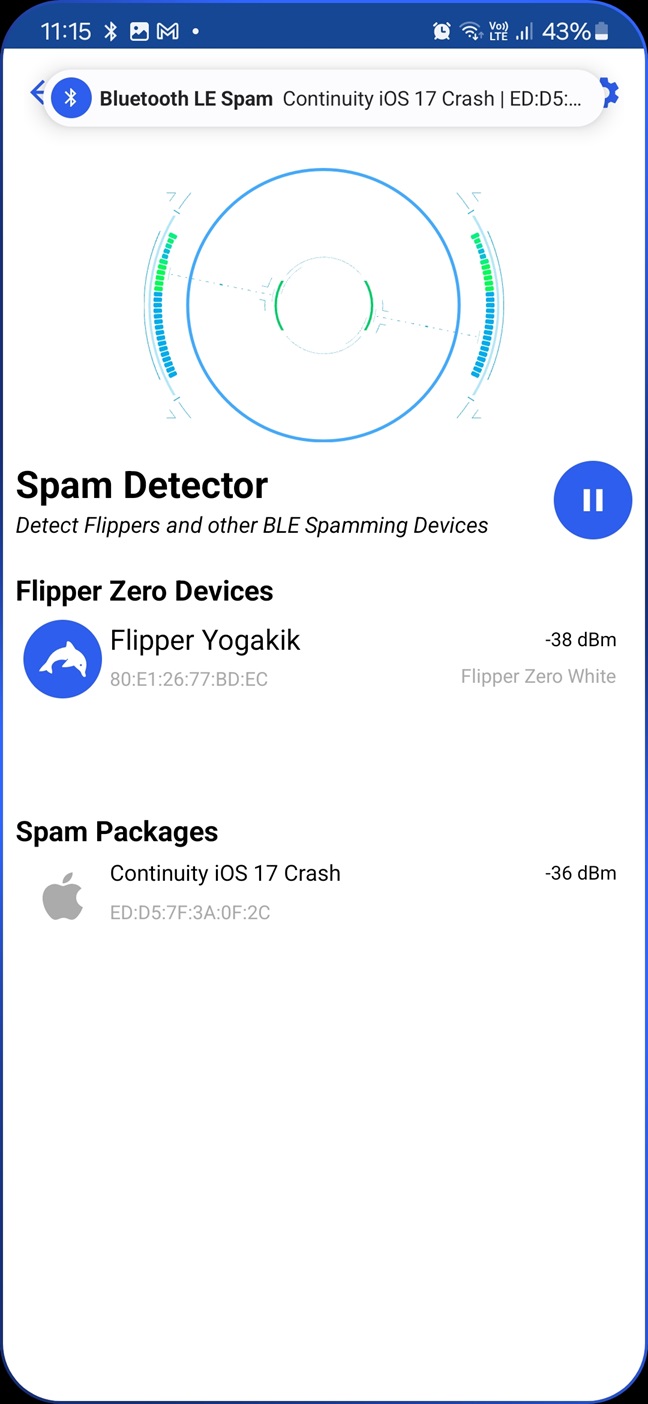
This functionality is based on Wall of Flippers. Because of that, it is possible to detect Flipper Zero and BLE spamming advertisement attacks using any Android smartphone. In the video below, you can see me testing both Wall of Flippers and Spam Detector.
Spoof Flipper Zero
Wall of Flippers detects Flipper Zero devices in the vicinity based on MAC address prefix. Because of that, it is possible to spoof Flipper Zero for example using nRF Connect app and impersonate as many Flippers as you want. Such false positive detections might create harmless chaos on conferences or public places. See video below.
Conclusion
Wall of Flippers is the first tool that is able to detect Flipper Zero devices and BLE spam attacks in the vicinity. This functionality is also implemented in Android Bluetooth LE Spam app, and allows to scan for Flippers to any Android user. Since the scan relies on Bluetooth MAC prefix, it is fairly easy to spoof Flipper Zeros. It is also important to mention that any regular BLE paring would be also identified as attack.
如有侵权请联系:admin#unsafe.sh