
SMTP smuggling is a technique that allows an attacker to send an email from pretty much any address they like. The intended goal is email spoofing—sending emails with false sender addresses. Email spoofing allows criminals to make malicious emails more believable.
Let’s take a closer look at what it is exactly, and how cybercriminals can use it.
The first thing we need to look at is the Simple Mail Transfer Protocol (SMTP), a protocol that allows the exchange of emails. Mail servers and other message transfer agents use SMTP to send and receive mail messages.
SMTP is very much a protocol that has developed over time since it became the standard for always-online servers in the 1980s.
Basically, an email is written using software like Microsoft Outlook or Apple Mail and is then handed over to an SMTP server. The server looks up the appropriate mail server for the domain in the recipient’s address—the part on the right side of the @ symbol, and sends the mail to that server.
It sometimes takes a few steps, but if all goes well the email will be received by the SMTP server that handles the mail for the recipient. This server may deliver the messages directly to storage, or forward it over a network using SMTP before it reaches the recipient.
Simplified, the process looks like this:



Since SMTP lacks authentication it used to be extremely easy to spoof a sender address. Several safeguards emerged to stop this:
- SPF (Sender Policy Framework): This uses DNS records to indicate to receiving mail servers which IP addresses are authorized to send mail for a given domain. So this still leaves the work to the receiving server.
- DKIM (Domain Key Identified Mail): This method signs outgoing emails using a private key. Receiving servers validate the sender using the sending server’s public key,.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC verifies if the email’s “From” domain aligns with SPF checks and/or DKIM signatures. Thus, the DMARC check fails if there is a mismatch between the MAIL FROM and the From domain where otherwise the SPF check would pass. Unfortunately DMARC is not very widely used.
SMTP smuggling
SMTP smuggling takes advantage of inconsistencies in the way that proxy servers and firewalls handle SMTP traffic.
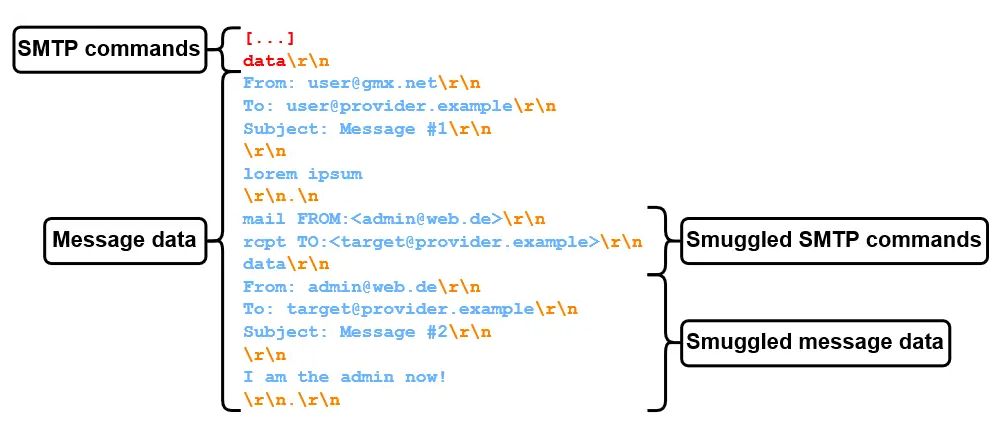
Traditionally, the end of data in an SMTP conversation is indicated by a sequence <CR><LF>.<CR><LF> (CR LF stands for Carriage Return and Line Feed, which are standard text delimiters) which can also be written as \r\n.\r\n.
Researchers published about two types of SMTP smuggling, inbound and outbound. They started working from the question, what happens if outbound and inbound SMTP servers interpret the end-of-data sequence (<CR><LF>.<CR><LF>) differently?
If you can tell one server the email ends here and the other one that the full packet ends later, you can create a compartment in which you can smuggle more data.
So, the researchers started testing by putting a <LF>.<LF> sequence in the middle of sent packages. And they found that outbound SMTP servers have different methods of dealing with it, including:
- Dot-stuffing (Escaping the single dot with another dot):
<LF>..<LF> - Replacing it with a
<CR><LF> - Encoding it (e.g., via quoted-printable):
=0A.=0A - Removing the entire sequence
- Not sending the message
- Or do nothing at all
By testing, which included sending specially constructed messages from and to different email providers, the researchers were able to find combinations that allowed them to send two email messages in one package. The sequence <LF>.<CR><LF> turned out to be effective on a custom SMTP server called NemesisSMTPd which is in use by email services provided by Ionos (e.g. GMX) which accounts for about a million hosted domains.
Some vendors (Microsoft and GMX) were quick to fix the vulnerabilities that facilitated SMTP smuggling, but the researchers urge companies using the also affected Cisco Secure Email product to manually update their vulnerable default configuration. The Cisco flaw affects more than 40,000 vulnerable instances and allows an attacker to send spoofed emails to high-value targets, such as Amazon, PayPal, eBay, and the IRS.
The recommendation by the researchers tells organizations using Cisco Secure Email Gateway (on premises) or Cisco Secure Email Cloud Gateway (cloud) to change the default settings of “CR and LF Handling” from “Clean” to “Allow,” citing Cisco guidelines to help administrators understand the change that should be made.
That may sound counterproductive, but this setting passes e-mails with bare carriage returns or line feeds on to the actual e-mail server (Cisco Secure Email Gateway is just a gateway), which only interprets <CR><LF>.<CR><LF> as end-of-data sequence. So, if you don’t want to receive spoofed e-mails with valid DMARC checks, we highly recommend changing your configuration.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
如有侵权请联系:admin#unsafe.sh