2024-1-6 00:54:20 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Mimecast this week announced it has acquired Elevate Security as part of an effort to make it simpler to apply cybersecurity controls based on actual end-user behavior.
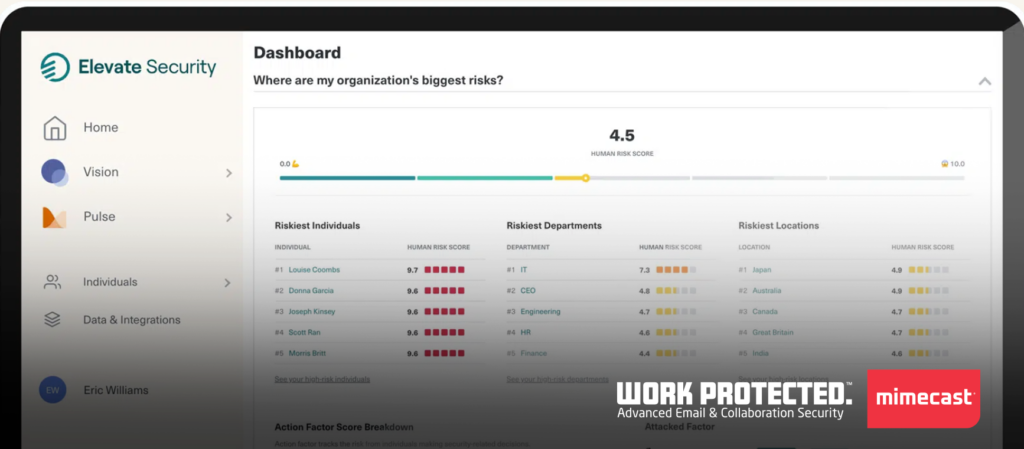
David Raissipour, chief technology and product officer at Mimecast, said Elevate Security, a provider of a platform for assessing cybersecurity risk levels, will advance an ongoing effort to enable cybersecurity teams to personalize cybersecurity in an era where cyberattacks are increasingly aimed at individuals based on the role they play with an organization.
The bulk of those attacks are launched via email and collaboration services that Mimecast already protects, so the addition of Elevate Security will make it simpler for organizations to apply cybersecurity policies more narrowly, said Raissipour.
Otherwise, cybersecurity teams are enforcing policies that punish all end users equally despite the level of care they take when, for example, accessing external Web sites or opening attachments, he added.
In general, the weakest link in any cybersecurity strategy is individuals who, no matter how much they are trained, are still liable to make mistakes, especially as social engineering tactics and techniques become more sophisticated because cybercriminals are now leveraging generative artificial intelligence (AI) tools to craft them. It may not be practical to fire employees for falling victim to these attacks, but if cybersecurity teams are aware of which employees are engaging in the riskiest behavior, it becomes possible to apply controls more granularly, noted Raissipour.
Each organization will, of course, need to determine what level of end-user training should be provided based on the roles and responsibilities of employees, but as organizations embrace zero-trust IT architecture, cybersecurity will revolve around verifying the identities of end users, applications and machines. Applying cybersecurity policies based on risks that are determined using predictive AI tools is a natural extension to any identity-centric approach to maintaining cybersecurity, added Raissipour.
It’s not clear how targeted attacks will become in the next year, but given the previous year, it’s clear cybercriminals are moving beyond attacks based on spray-and-pray tactics. Instead, cybercriminals are leveraging stolen credentials to insert themselves into workflows to, for example, redirect invoice payments. Most of those attacks can be traced back to some initial engagement with an employee that involved some type of request to download a document or click on a URL that brought them to a malicious website. Most cybersecurity teams are not able to issue edits to prevent that behavior, but they can monitor the online behavior of end users that, from a cybersecurity perspective, are known to be problematic.
One way or another, cybersecurity teams, as part of any forensic effort that occurs after a breach is discovered, will need to trace the origin of a cyberattack back to a specific root cause. Most of the time, that will involve identifying an end user that inadvertently engaged in an activity that created an exploit that cybercriminals could exploit. The challenge and the opportunity now is to proactively identify the probability of such events occurring in a way that either prevents them from occurring or, at the very least, minimizes the potential damage inflicted.
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
