2024-1-3 22:21:45 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
In the modern application landscape, where businesses are constantly under the threat of cyber attacks, one of the most recent to emerge is HTTP/2 Rapid Reset (CVE-2023-44487), a type of Distributed Denial-of-Service (DDoS) attack. This attack is larger than any previously reported application layer (Layer 7) incident, with the largest recorded attack surpassing an alarming 398 million requests per second. As a business, it’s crucial to wonder, “How can we fortify ourselves against such a vulnerability?” The answer lies in the robust protection offered by the Imperva Web Application Firewall (WAF).
What are HTTP/2-based DDoS Attacks?
HTTP/2-based DDoS attacks are a new breed of cyber threats that have primarily targeted Google services and Cloud customers. The main objective of HTTP/2 was to enhance efficiency. However, the very features that make HTTP/2 more efficient for legitimate clients can also be exploited to make DDoS attacks more potent. This is achieved through “stream multiplexing” which allows for higher utilization of each TCP connection, thus making it easier for attackers to launch multiple in-flight requests without managing multiple individual connections.
The HTTP/2 protocol allows clients to indicate that a previous stream should be canceled by sending a RST_STREAM frame. This feature is exploited in the HTTP/2 Rapid Reset attack, where the client opens a large number of streams at once and then cancels each request immediately. This allows each connection to have an indefinite number of requests in flight, creating an exploitable cost asymmetry between the server and the client.
Imperva WAF Protects Against HTTP/2-based DDoS Attacks
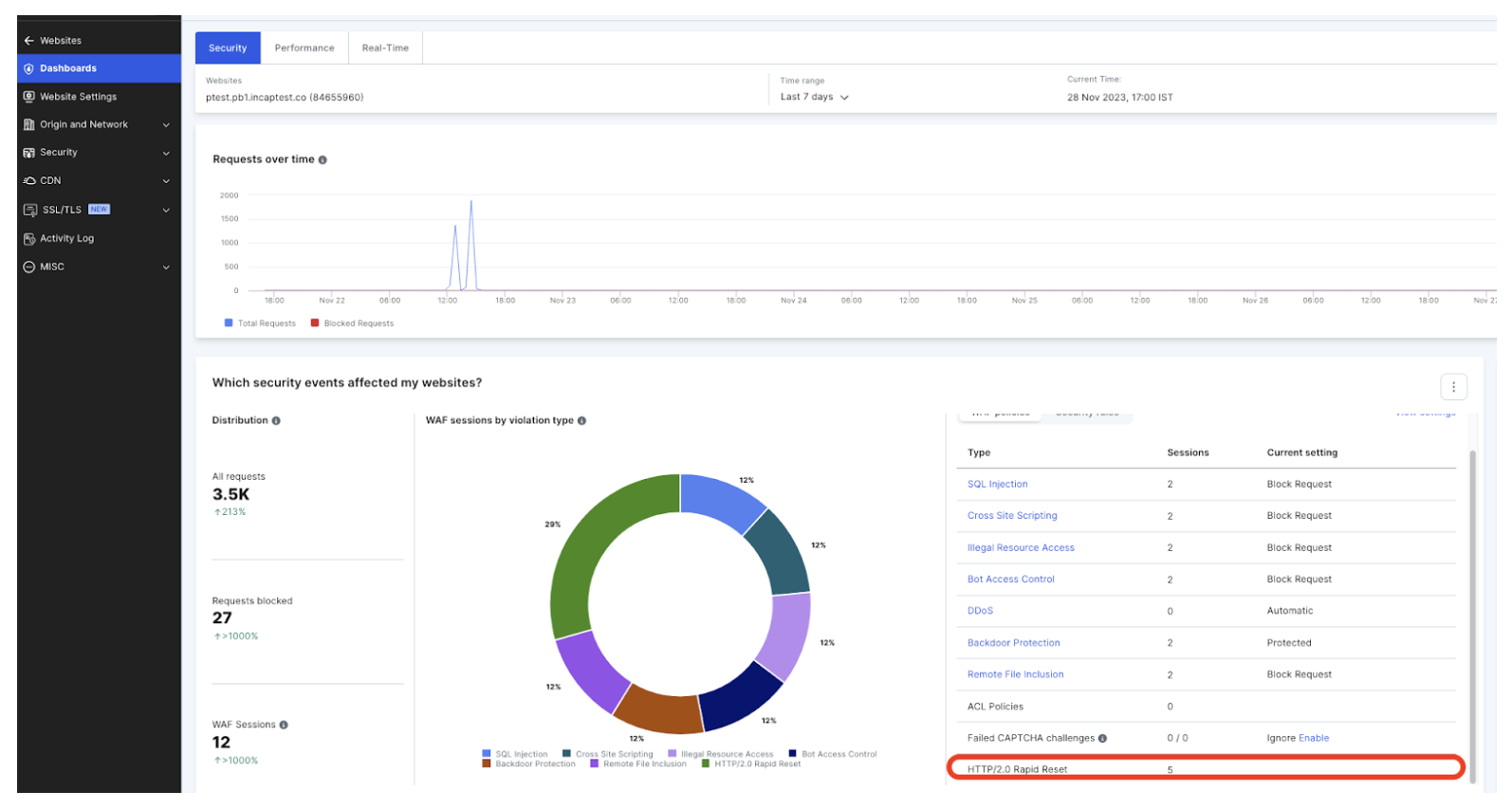
The Imperva Web Application Firewall (WAF) offers a robust defense against a multitude of cyber threats, including the HTTP/2 ‘Rapid Reset’ DDoS attack and provides unparalleled visibility into these attacks. Our WAF’s reporting capabilities offer customers a comprehensive and detailed view of all attack vectors, as illustrated in the dashboard below.
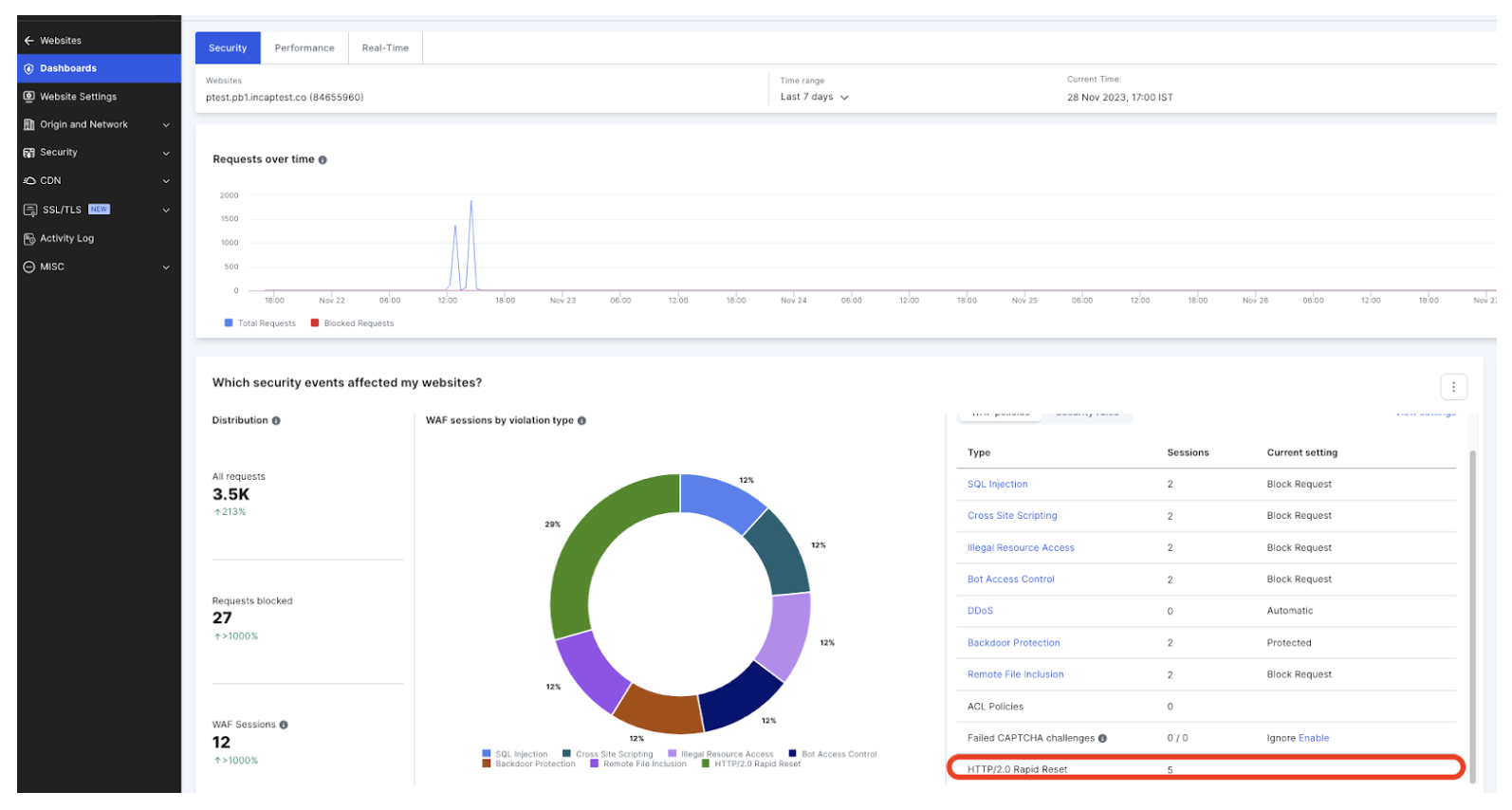
The extensive visibility extends to the intricacies of each attack, revealing patterns and trends that can inform future security strategies. With Imperva WAF, you are protected against DDoS attacks and empowered with the knowledge to proactively mitigate future threats.
Imperva Helps Mitigate DDoS Attacks
While HTTP/2-based DDoS attacks pose a significant threat, Imperva WAF is designed to protect a business from all forms of DDoS attacks. It leverages a global network of scrubbing centers to absorb large volumetric attacks, and its advanced algorithms accurately identify and mitigate application layer attacks.
In addition to its robust protection features, Imperva WAF also provides integrated Attack Analytics that correlate DDoS and related critical events to focus on what truly matters. This allows your business to quickly adjust security policies on the fly based on recommended actions to stop attacks in their tracks.
As stated in a previous blog post past, as a member of the security community, Imperva values its collaborations with companies such as Google and Fastly. Our world is more secure when our industry collaborates to tackle complex security challenges.
Additional Resources:
If you’re a customer in need of support, please contact us through the Imperva Support Portal.
If you need protection from HTTP/2-based attacks, contact us.
The post HTTP/2 Rapid Reset Mitigation With Imperva WAF appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Luke Richardson. Read the original post at: https://www.imperva.com/blog/http-2-rapid-reset-mitigation-with-imperva-waf/
如有侵权请联系:admin#unsafe.sh