2024-1-2 14:28:47 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
A recent discovery revealed the presence of malicious software within an NPM package repository. These applications were created with certain features that, once installed on a computer system, would allow them to carry out unlawful acts. These initiatives, which went by names that didn’t seem too serious, were connected to a company called hktalent. Crucially, a sizable portion of these fraudulent apps are still accessible for download, putting consumers at risk. A reverse shell is a way for hackers to gain control. It’s like an invisible door that lets them send commands to a far-off computer. This means they could access private information and even take over the whole system. The package detection is a big deal. It shows how risky it can be to trust from sources like NPM packages. If these packages get into projects, they could cause a lot of damage.
To avoid such threats, developers need to be extra careful about what they include in their projects. Strong security measures and double-checking packages are super important to stay safe. In this blog, we will talk about the unsettling reality behind 48 seemingly harmless NPM packages and their hidden threat to developers.
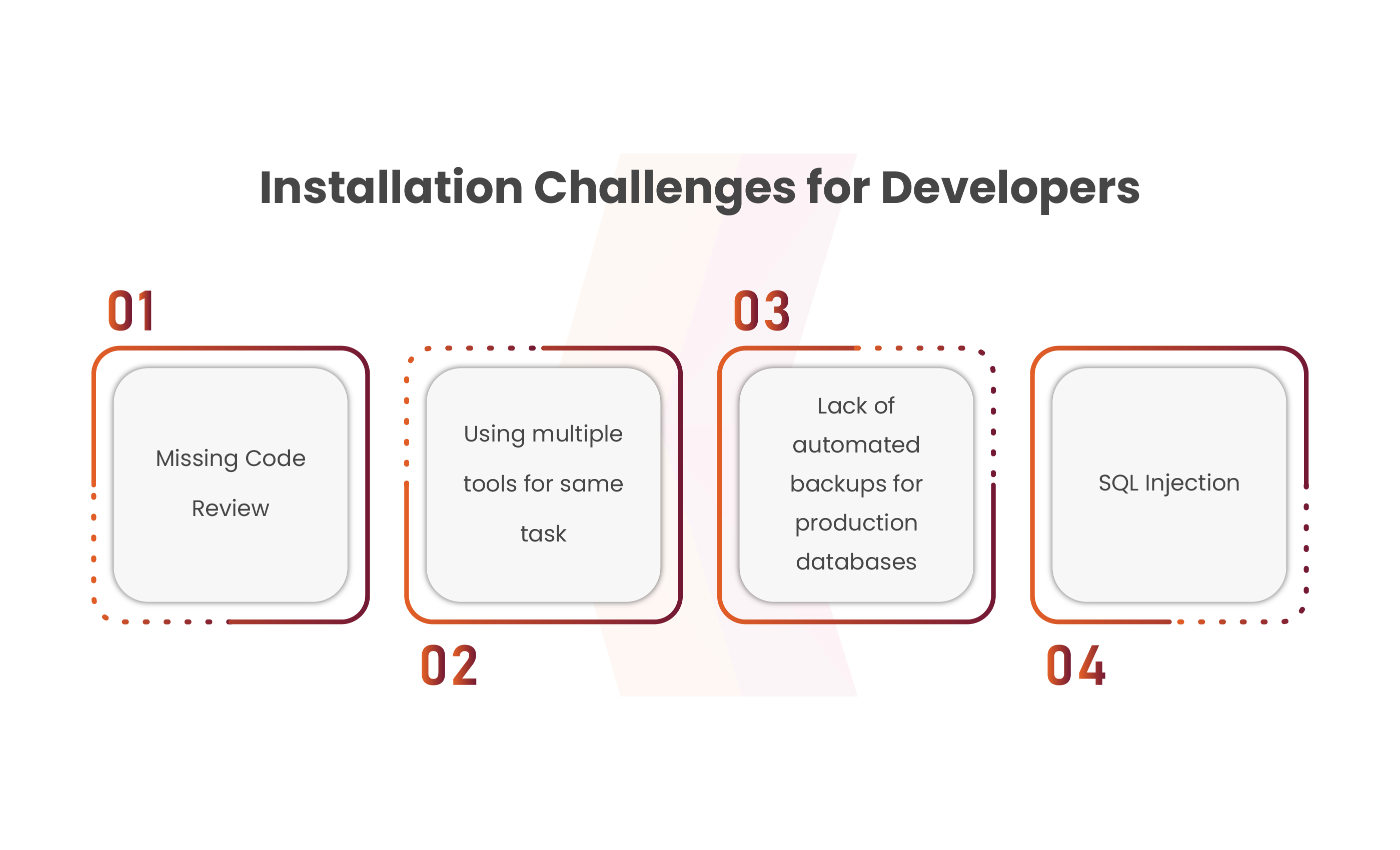
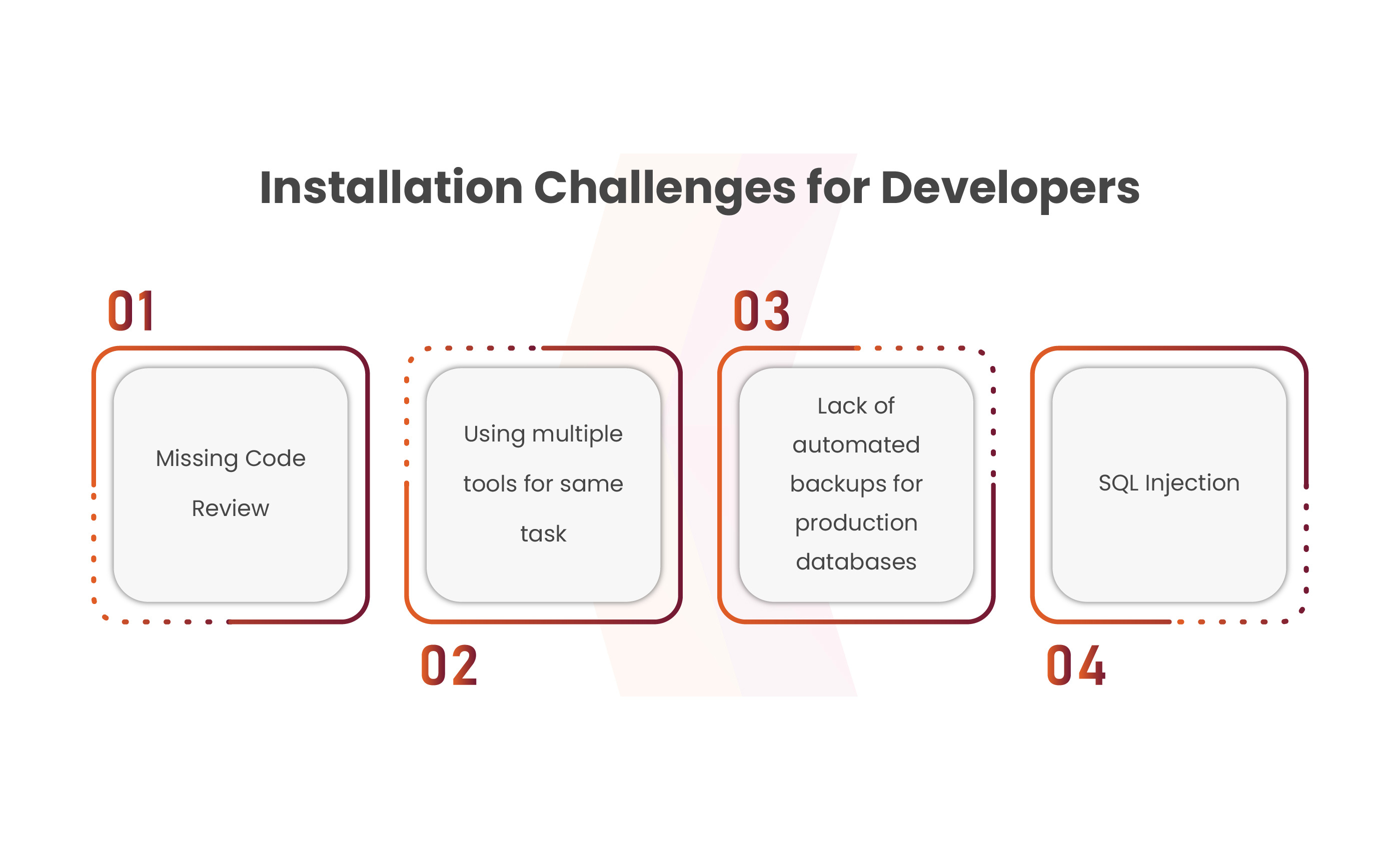
Backend Installation Challenges for Developers
Understanding the backend installation poses significant challenges for developers. From intricate configurations to compatibility hurdles, setting up backend systems demands meticulous attention. Here are key pointers that eliminate the common hurdles and potential solutions in this complex process:
Missing Code Review:
The absence of code review and static code analysis in backend development poses significant risks, leading to inconsistent code practices, vulnerabilities, and overlooked edge cases. To prevent these issues, a meticulous approach involving thorough code reviews before merging, enforced for static analysis, and addressing the previously merged but unreviewed code is crucial. Overcoming challenges like time zone differences or accidental direct pushes into default branches requires strategies such as involving relevant developers from other projects. Ultimately, a proactive approach focusing on code scrutiny and process refinement mitigates the adverse effects of these backend development pitfalls.
Using Multiple Tools or Methods for the same task:
Backend development progress on consistency in technology choice and approach for tackling specific problems. While occasional variation is acceptable for experimentation, maintaining a uniform set of technologies and patterns across a project is crucial. Deviations lead to complexities in maintenance, increased risk of errors due to varied dependencies, and slower installations. To counter this, enforcing consistent technology use and conducting thorough code reviews are pivotal. Fixing inconsistencies means picking the best tech and updating code for smoother backend development.
Absence of Automated Backups for production databases:
The absence of automated backups for the production database poses a critical risk, as the loss or corruption of production data is often irreversible and can significantly impact system users. Unlike code, which can be recreated, production data represents the efforts of numerous application users and can’t be easily replaced. This absence not only jeopardizes user work but also potentially leads to legal repercussions in terms of damages. Implementing automatic backup solutions like MongoDB Atlas, coupled with regular checks, is crucial. If backups weren’t previously configured, immediate setup is necessary. Without backups, retrieving data from logs or manual backups is the only option, underscoring the importance of proper database management.
SQL Injection:
SQL injection, a risk prevalent among backend developers, poses a significant threat by allowing unauthorized execution of database queries through user input, potentially leading to data exposure or manipulation. This vulnerability extends beyond SQL, encompassing other query languages like AQL or GraphQL, along with risks from functions like eval or system commands. Preventive measures involve precise queries, limited string combinations, thorough code reviews, strict string validation, varied database and user utilization for risk reduction, and automated backups for recovery. Swift deployment of these preventive steps to production serves as the treatment strategy against such security loopholes.
Malicious Open-Source for NPM Packages
A recent discovery of 48 malicious NPM packages in the NPM repository has raised concerns regarding software supply chain security. Deceptively named packages from the NPM user hktalent contained blur JavaScript, triggering a reverse shell on installation. The attack, executed via an install hook in package.json, establishes a connection to rsh.51pwn[.]com. This incident follows similar revelations in the Python Package Index (PyPI), where packages called localization-utils and locute were discovered to sensitive data and system information to an actor-controlled Telegram channel. These incidents underscore the escalating interest of threat actors in open-source environments, posing significant supply chain risks, and emphasizing the criticality of trust in dependencies within open-source ecosystems. This leads to a supply chain attack.
The recent supply chain attack happened on 29th March 2023. In this attack, Falcon OverWatch, a cybersecurity company, identified unusual malicious behavior stemming from 3CXDesktopApp, an authentic softphone application created by 3CX. The cyber attack used multiple stages, exploiting 3CX app vulnerabilities, using encrypted icons from GitHub, and IconicStealer data miner.
Mandiant’s investigation revealed the entry point through a compromised version of X_TRADER software downloaded from Trading Technologies’ website. The attackers employed encryption tools like SIGFLIP and DAVESHELL, compromising the 3CX build environment and executing lateral movement through the network using tools like Fast Reverse Proxy. The attack highlighted vulnerabilities in the X_TRADER website, weak endpoint security, and the use of open-source security tools by threat actors. Steps like multi-factor authentication, shorter certificates, improved endpoint security, and thorough security assessments could have lessened the attack’s impact. This incident underscores the critical need for robust security measures, proactive threat intelligence, and enhanced user awareness to thwart complex supply chain attacks.
Book a Free Consultation with our Cyber Security Experts

Identifying Malicious Code and Preventing it from Entering SDLC
The risk of malicious NPM packages demands demand proactive steps for risk reduction. Here are key strategies developers can implement:
- Double-check the legitimacy and trustworthiness of the package. Watch out for suspicious accounts or impersonations and confirm the package’s source before installation. Ensure the accuracy of both package names and URLs to steer clear of fake or potentially harmful packages.
- Inform the NPM security team about any suspicious packages or activities encountered. Work with developers, and exchange reviews as well as insights, to protect the NPM ecosystem from harmful packages that pose a threat to its capabilities.
- Software Bill of Materials (SBOM) is essential for guarding against supply chain intrusions. This extensive list of open-source additions guarantees security, compliance, and first-rate code. It lists licenses, versions, and patch status—protecting against threats, including those from malicious packages.
- Stay informed about newly identified malicious packages, malware, and disclosed vulnerabilities within open-source components. Seek out newsfeeds or recurring advisories that offer actionable guidance and detailed information regarding issues affecting the items listed in your SBOM.
Solution for Hidden Risks with NPM Packages
The recent discovery of hidden risks within NPM packages highlights the serious threat that deceptive software poses to developers. The intricate landscape of backend installation adds further challenges, demanding meticulous attention to mitigate risks like code vulnerabilities and data loss. The rise in supply chain attacks stresses the urgent need for stronger security and proactive tactics in open-source environments. Developers must prioritize security, double-check package legitimacy, collaborate with security teams, and stay informed about potential risks. This emphasizes the importance of robust security practices and continuous vigilance to safeguard against evolving cyber threats in software development.
Kratikal, a CERT-In empanelled auditor, provides extensive cybersecurity solutions designed to shield businesses from various cyber threats. Our primary emphasis is on safeguarding web applications to proactively mitigate risks. Partnering with Kratikal enables businesses to identify and address security vulnerabilities early on, preventing potential exploitation by malicious attackers.
Ref: https://thehackernews.com/2023/11/48-malicious-npm-packages-found.html
The post 48 NPM Packages Detected: Deploying on Developers’ Systems appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/48-npm-packages-detected-deploying-on-developers-systems/
如有侵权请联系:admin#unsafe.sh