
2023-12-29 15:45:5 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
If your device suddenly behaves like a re-animated zombie, you might be under a Botnet attack.
Also known as a zombie army, these attacks involve hijacking internet-connected devices infected with malware, controlled remotely by a single hacker. The scale of these attacks is immense, as demonstrated by a cyber assault that exploited 1.5 million connected cameras to overwhelm and take down a journalist’s website.
As the IoT market grows exponentially, reaching 75.4 billion devices by 2025, the need for robust botnet detection and removal becomes critical for digital safety.
How Does a Botnet Attack Work?
A botnet functions as a network of compromised devices, each under the control of a malicious actor. Typically, these devices become infected unknowingly through activities like visiting a malicious website, where malware is automatically downloaded without the user’s awareness. Once compromised, a device becomes part of the botnet, essentially a collective of hijacked devices.
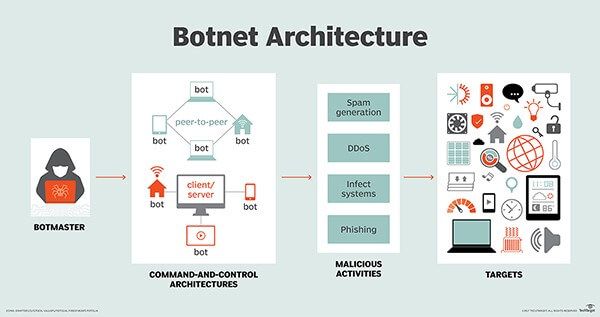
The lifecycle of a botnet involves several key stages:
Infection
The process begins with the initial infection of individual devices. This can occur through various means, such as users unknowingly downloading malware from malicious websites, falling victim to phishing schemes, or exploiting vulnerabilities in software.
One prevalent method involves the mass sending of phishing emails to target systems. These phishing schemes can be challenging to detect, even for vigilant users and advanced alert systems. The insidious nature of malware lies in its ability to infiltrate devices, unpack viruses, and take control, often without the user’s knowledge.
Propagation
Once a device is infected, it becomes part of the botnet and can be used to propagate the malware further. This can involve exploiting known software vulnerabilities, enabling the botnet to rapidly expand its reach by infecting other vulnerable devices.
Command and Control (C2)
The botmaster establishes control over the compromised devices through a command-and-control server (C2). This server serves as the central hub for communication between the botmaster and the infected devices. The botmaster can issue commands to the entire botnet or specific subsets of compromised devices.
Malicious Activities
With control established, the botmaster can deploy the botnet to carry out various malicious activities. This may include launching DDoS attacks to overwhelm targeted websites or applications with traffic, conducting phishing campaigns, infecting systems with additional malware, or generating spam.
How Bad Botnets Affect Your Business?
From dynamic adaptation to global proliferation, the impact extends beyond immediate financial losses, highlighting the need for robust cybersecurity measures for botnet detection and removal.
Dynamic Adaptation
Botnets often employ techniques to adapt dynamically to evade detection and mitigation efforts. This can involve changing communication patterns, utilizing encryption to conceal command traffic, or regularly updating the malware’s code to exploit new vulnerabilities.
Rent-a-Bot Services
Cybercriminals create bot armies to launch DDoS attacks, spam campaigns, and other attacks that can bring your website down and/or steal data. Surprisingly, these types of attacks are easy to carry out, too, with botnet armies available on a rental basis. Full-service attacks are available for as little as $5 per hour, and the interested party can easily stretch their hours with a monthly plan that averages $ 38.
Monetization
Botnets can be monetized in various ways. Cybercriminals may rent out the botnet for specific attacks, sell stolen data collected from compromised devices, or use the botnet to generate revenue through click fraud or cryptocurrency mining.
Global DDoS and Botnet Statistics 2024
Keeping a business application up and running is critical to your brand’s reputation, and hackers want to target this weakness with DDoS attacks. The unpredictability of these attacks makes preparing for them difficult, further incentivizing criminals to act. The following are some examples of bad bots disrupting major businesses recently.
- To execute a DDoS attack, botnets are typically employed to target a single server with requests originating from various locations. Globally, over 15 million “DDoS weapons” or infected IP addresses are circulating for these attacks.
- Mirai is the most common malware used to create DDoS botnets; however, other variants exist.
- In 2023, DDoS attacks surged significantly, with AppTrana WAAP countering over 1.45 billion attacks in Q3—a 67% increase compared to Q2, 2023.
- Notably, Q3, 2023 witnessed a marked rise in low-rate HTTP DDoS attacks orchestrated by botnets.
- The Dark Web Price Index 2022 indicates that a 24-hour DDoS attack with 20-50k requests per second can cost attackers as little as USD 200.
- Botnet maintenance costs, influenced by device infection expenses, impact attackers’ pricing dynamics. For instance, a botnet of 1000 cameras may be more cost-effective due to IoT devices’ often underestimated security vulnerabilities.
- In Q3, 2022, the average duration of a DDoS attack was a brief 390 seconds. These shorter burst-style attacks are employed more frequently to test the victim’s defenses.
- A Ponemon Institute study revealed that during a DDoS attack, every minute of downtime costs $22,000.
- The post-attack restoration of services and operations can cost small or midsize businesses $120,000.
Best Practices and Methods to Combat Botnets
1. Understand Botnet Infiltration
It is important to know precisely how a botnet gets into your system and takes it over for nefarious purposes. Your device can become infected anytime you visit a malicious site, and it automatically downloads malware without you ever noticing.
Or you could download a file from a seemingly trustworthy source directly from your email and later realize it’s malware acting as a trojan.
Another way botnets can infiltrate your systems is by searching for unprotected devices, from video baby monitors to computers, and accessing them through weak passwords.
It’s easy for people to shrug off changing the password for a smart device like a toaster. NPR reported on how quickly a seemingly innocent internet-connected toaster can be infected with botnets, resulting in a massive attack.

2. Identify the Attacks
The first step in identifying a pervasive botnet attack is knowing how the botnet got onto your device in the first place.
Instead of getting hit with a zombie botnet you never saw coming, you can take a few minutes each week to see which botnets have been identified and named by security experts.
In some cases, savvy tech users and programmers will post information about the latest botnets online.
Brush up on your knowledge and learn about the latest botnet attacks through sites like Wired, CNET, or SearchSecurity. Tech publications and forums frequently update their content with the latest attacks. For example, Zeus botnets are a known Trojan horse for Windows created to steal banking information.

3. Look for the Symptoms
It’s not always easy to know if a botnet has taken over your device at first glance. A hacker may lie low and quietly steal information or set up a shop for a future attack while amassing other botnets. You won’t know what’s happening until it’s too late and you’ve lost control of your device.
However, a few clues could alert you to suspicious activity. Pay close attention to the following symptoms:
- Unusual Patterns in Network Traffic:Monitor for unexpected spikes in network traffic, which could indicate a botnet attempting to communicate or execute malicious activities within your business network.
- Unexplained Slowdown in System Performance:If your business systems experience sudden and unexplained sluggishness or a noticeable decrease in performance, it might be a sign of a botnet presence.
- Difficulty in Accessing Specific Business Services:If employees encounter challenges accessing certain business-critical websites or services, it may be due to a botnet affecting network connectivity.
- Reports of Unusual Emails from Business Accounts:Investigate reports of strange emails with links from your business accounts, as this could be a sign of a botnet attempting to disseminate malware.
- Employee Complaints or Concerns:Stay attuned to employees expressing concerns about unusual activities, such as unexpected emails or system behavior, which may indicate a botnet infiltration.
- Unexpected Service Outages:Frequent and unexpected disruptions to your business services or website availability could indicate a botnet overwhelming your infrastructure.
These signs extend beyond mere email spoofing or password updates; they could indicate the presence of a botnet compromising your business operations. Stay vigilant to these symptoms to address potential threats proactively.
4. Reset Your Device
In some cases, a botnet may not be as difficult to remove as it seems, considering all the damage it can do. But despite the potential ease of removal, you should always stay proactive.
Start by backing up your valuable data to the cloud and ensuring you have everything you need before moving on. The next step is resetting your device to factory settings, which will clean your device.
It’s also wise to reset your routers and any wireless equipment. Some botnets like Mirai are often wiped out by using these simple techniques. But you still need to take additional action, like changing your default passwords and proactively monitoring for unusual behavior. Otherwise, the botnet may fall back on a safety trigger to reinstall itself and take over your device again.
5. Restrict Access
Your devices need more protection to mitigate attacks and keep your systems safe. This is especially important for businesses with multiple devices used by employees prone to using public wireless or working in the field. You can increase your web application firewall settings and rules to restrict the malware’s inbound or outbound network traffic.
Businesses that handle sensitive data and regularly connect to the cloud may also need stronger safeguards for internet users to protect their devices. Consider restricting who has access to your company devices, which apps and websites can be accessed with those devices, and what type of internet connection they are allowed to use.
In some cases, it may also be necessary to start mandating workplace-only devices used in the office and ramp up the protocols for internet use.
6. Use Strong Device Authentication
The most sophisticated hackers aren’t necessarily relying on anything other than brute force to break into your devices via weak passwords.
Despite ongoing warnings of the importance of strong passwords, people are guilty of reusing weak passwords or never updating the password defaults that come with their devices. According to reporting by Wired,” 123456″ still tops the list for most popular passwords and, of course, is the easiest to crack with virtually no effort whatsoever.
Even Facebook founder Mark Zuckerberg is guilty of using weak passwords. Business Insider reported that Zuckerberg was hacked when he used the password “dadada.” Strong device authentication is not just a best practice but integral to online security.
7. Use a Proxy Server
When deflecting botnets, using several techniques simultaneously to safeguard your devices is usually necessary. Changing passwords and remaining diligent about detection is just one part of the process. But you can also use tools like a proxy server.
A proxy server is essentially another device or computer that serves as a hub where your internet requests are processed to add a layer of protection to your IP address. Forcing outbound traffic through a proxy server can help you monitor and control web access and help deflect encounters with botnets. Check out how proxy and reverse proxy work in detail.

8. Install Patches
There’s a reason your device, apps, and operating systems are constantly prompting you to update your system. New patches aren’t just a “nice to have” addition; they’re a necessary part of your digital security.
Hackers frequently pounce on known vulnerabilities and create worms to infiltrate your systems. Or device manufacturers will release a patch update to combat a known hack or botnet that could attack your device.
Take the time to update your devices, software, and apps, and research the latest app vulnerabilities that impact your systems and business. This is also an excellent opportunity to perform vulnerability testing to determine the most accessible entry points for hackers.
9. Get Professional Monitoring
Although you can take your digital security into your own hands, staying on top of the latest hacks and industry news is not always possible. You’re running a business, not working to keep hackers from taking it down.
Depending on how much time you have to allow to keep your systems safe, you may need a professional monitoring service to help detect, deflect, and restore your plans in case of a botnet attack. The service you choose should have a reputation for monitoring specifically for botnets and take a proactive approach to prevention.
10. Leverage Bot Management Software
Bot management software is a proactive defense mechanism integrating advanced techniques to identify, mitigate, and eradicate botnet threats. Bot management software employs a multifaceted approach to detecting and removing botnets, safeguarding digital assets from malicious activities.
- Advanced Anomaly Detection – Bot management software employs sophisticated anomaly detection algorithms to scrutinize network traffic and user behavior. By identifying deviations from established baselines, such as sudden spikes in traffic or abnormal access patterns, the software triggers alerts for further investigation.
- Signature-Based Mechanisms – Utilizing a signature-based approach, bot management software maintains an up-to-date database of known bot signatures and patterns. Regular updates to this signature database ensure the identification of emerging threats, allowing the software to recognize malicious patterns indicative of botnet activities.
- Command and Control (C2) Server Detection – An integral part of bot management involves identifying and blocking suspicious C2 server communication. This includes continuous monitoring of DNS requests, IP addresses, and communication patterns to detect connections to command-and-control servers, disrupting botnet activities at an early stage.
- Behavioral Analysis and Machine Learning – Bot management software leverages behavioral analysis and machine learning to adapt to evolving botnet tactics. Using heuristics and learning from historical data, the software proactively identifies and responds to new threats based on behavioral anomalies. This reduces the chances of misidentifying legitimate traffic as bot-related and mitigates false positives in bot detection.
- Rate Limiting – Enforce rate-limiting measures to control the frequency of requests from specific IP addresses. Unusual spikes in activity can trigger alerts, allowing the system to investigate without immediately flagging the traffic as malicious, reducing false positives.
- Real-Time Monitoring Capabilities – Integral to the software’s effectiveness is its real-time monitoring capabilities. The software enables swift identification and response to potential botnet activities by providing instant alerts and detailed reporting, enhancing situational awareness and proactive threat management.
- Honeypots and Decoys – Strategically deploying honeypots and decoys within the network adds an additional intelligence layer. These virtual decoy systems attract and detect bot activities, providing valuable insights into emerging threats and enhancing the overall threat intelligence of the bot management software.
- User Behavior Monitoring – Enabled by integration with identity and access management systems, user behavior monitoring enhances the software’s ability to identify and respond to potential botnet infiltrations. The software swiftly responds to deviations from normal user behavior by monitoring user access patterns and detecting unusual activities.
Botnet Detection and Removal with AppTrana WAAP
AppTrana WAAP’s bot mitigation solution is the cornerstone, integrating these best practices into a cohesive and proactive defense strategy. Through a synergy of behavioral analysis, machine learning, User-Agent verification, IP reputation checks, challenge-response mechanisms, and rate limiting, AppTrana WAAP creates a robust shield.
This blend of cutting-edge technologies accurately identifies and prevents botnet threats and effectively minimizes false positives. By staying adaptive to evolving attack patterns and incorporating real-time verification measures, AppTrana WAAP offers a holistic solution, ensuring the resilience and security of web applications in the face of dynamic and persistent bot-driven threats.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

The post 10 Botnet Detection and Removal Best Practices appeared first on Indusface.
*** This is a Security Bloggers Network syndicated blog from Indusface authored by Venkatesh Sundar. Read the original post at: https://www.indusface.com/blog/botnet-detection-removal-best-practices/
如有侵权请联系:admin#unsafe.sh



