December 23, 2023 | by Stefano Lanaro |
Introduction
The Certified Azure Red Team Professional is a penetration testing/red teaming certification and course provided by Altered Security, which is known in the industry for providing great courses and bootcamps.
In this review, I take the time to talk about my experience with this certification, the pros, and cons of enrolling in the course, my thoughts after taking and passing the exam, and a few tips and tricks.
Pros
- At a starting price of $449 USD, it provides great value for your money, especially in the cloud-based pentesting world.
- In terms of beginner-level Azure Active Directory courses, it is definitely the best pretty much your only option to get hands-on experience.
- This was by far the best experience I had when it came to dealing with support for a course. The team would always be very quick to reply and would always provide detailed answers and technical help when required. Keep in mind their support team is based in India so try to get in touch with them between 8am-10pm GMT+5:30, although they often did reply to my queries outside of those hours.
- The teacher for the course is Nikhil Mittal, who is very well known in the industry as a mentor and an exceptional red teamer.
- For almost every technique and attack used throughout the course, a mitigation/remediation strategy is provided in the course which is something that is often overlooked in penetration testing courses.
- The security tools offered by Microsoft to help protect Azure Cloud are explained in detail throughout the course, which is invaluable knowledge for red teamers.
Cons
- Altered Security still isn’t as recognized as other providers such as Offensive Security, so the certification won’t look as shiny on your resume.
- While it’s great to have a cloud environment to practice Azure AD pentesting on, I wish more effort was put into the extra mile CTF, as it felt somewhat rushed and unpolished.
- Some of the things techniques and commands shown during the course may not work as well in the student VM provided and due to the shared nature of the course and CTF cloud environments, these would sometimes have issues due to other students accidentally breaking them.
- The flag system it uses follows the course material, meaning it can be completed by using all of the commands prior to the exercise, I personally would have appreciated if there were flags to capture that simulated an entire environment (in order to give students an idea of what the exam is like) rather than one-off tasks.
Background
I decided to take on this course as I noticed how Azure Cloud, and in particular their Active Directory, was becoming more and more popular among organisations. I was a little worried going into the course as I had no prior Azure experience, although it turned out to be a great decision as the course is very confidence-inspiring and extremely beginner-friendly. Having completed CRTP in the past and knowing the instructor of this course was also Nikhil, I knew this would be an awesome choice.
The course does not have any real pre-requisites in order to enroll, although basic knowledge of Azure Cloud systems is strongly recommended, in order to be able to understand all of the concepts taught throughout the course, so in case you have absolutely no knowledge of this topic, I would suggest going brush up on it first. Additionally, knowledge of PowerShell can also help greatly although it isn’t necessary at all.
The Course

The course provides both videos and PDF slides to follow along, the content walks through various enumeration, exploitation, lateral movement, privilege escalation, and persistence techniques that can be used in an Azure Active Directory environment. The material is very easy to follow, and all of the commands and techniques are very well explained by the instructor, Nikhil Mittal, not only explaining the command itself but how it works under the hood.
The following are some of the techniques taught throughout the course:
- Use of OSINT and unauthenticated enumeration to learn about a target organization and tenant.
- Enumerate existing email addresses within an Azure tenant.
- Azure Active Directory enumeration through scripts, built-in tools etc. to identify useful information.
- Learn concepts like Management Groups, Roles, Subscription, Resource Groups, Resources, ARM, Managed Identity etc.
- Learn to use ARM and MS Graph REST API for enumeration.
- Learn to use tools like ROADRecon and Azure Hound for enumeration.
- Execute Illicit Consent Grant attack for initial access.
- Abuse internet-facing web applications, access tokens, Managed Identities, and insecure storage accounts to get a foothold.
- Execute phishing attacks against a user simulation to get their clear-text credentials.
- Abuse CI/CD to get access to an Azure tenant by compromising a GitHub account
- Enumerate information from Azure AD about users, groups, devices, service principals, applications, roles, Virtual Machines, Storage Accounts, Key vaults, Blobs, Automation Accounts, Deployment Templates, App Services, Function Apps and many more.
- Learn to use Microsoft’s tools like Azure AD Module, Az PowerShell and Az CLI for enumeration.
- Escalate privileges in Azure AD and Azure by abusing misconfigured permissions, service principals, Automation accounts, Key Vaults, Storage Accounts, Deployment History, Custom roles and more.
- Abuse Custom Script Extension and RunCommand privileges to run commands as SYSTEM on Azure VMs.
- Understand Dynamic Groups and abuse the membership rule to get membership of a dynamic group.
- Use several techniques to move laterally between Cloud and on-prem.
- Understand the persistent opportunities when a hybrid identity is used.
- Learn how to abuse AZUREADSSOACC, Azure AD Connect, Skeleton key in the cloud, and the Golden SAML attack to establish persistence.
- Understand the persistence opportunities for Azure resources like storage accounts, applications and service principals, consents and permissions, Azure VMs and NSGs, Custom Azure and Azure AD roles etc.
- Extract secrets from Key vaults, deployment history, Azure workstations and blob storage.
- Understand defense guidance from Microsoft in different categories.
- Get in-depth knowledge of Conditional Access Polices, Privileged Identity Management, Azure AD Identity Protection, Microsoft Defender for Cloud and its features like Just-in-time access, Adaptive Network Hardening, Adaptive Application Control and File Integrity Monitoring
- Learn the most widely used Conditional Access Policies and practice their bypasses.
- Practice opsec to avoid detections by Azure AD Identity Protection.
- Understand the methods that can be used to bypass MFA.
- Bypass Cloud Workload Protection by Microsoft Defender for Cloud like JIT, ANH, NSGs and Azure Firewall to access VMs.
Throughout the course, at the end of certain chapters, there will be learning objectives that students can complete to practice the techniques taught in the course in a lab environment provided by the course, which is made of multiple Azure tenants, to be able to replicate all of the necessary attacks. From my experience, pretty much all of the attacks could be run in the lab without any major issues, and the support was always available for any questions.
Throughout the material, the course also teaches what information is logged and what attacks may be prevented by Microsoft’s security tooling, how to avoid raising too many alarm bells, and how to prevent most of the attacks demonstrated to secure an Azure Active Directory environment.
I really enjoyed going through the course material and completing all of the learning objectives, and most of these attacks are applicable to real-world penetration testing.
The course lightly touches on using pentesting tools to enumerate Azure AD, such as AzureHound, although I would have appreciated it if these tools had been covered in more detail, as it isn’t always practical to use command-line tools during a real engagement and it is best to automate enumeration as much as possible.
A lot of the attacks and information present in the course can also be found on HackTricks.
The Exam
The exam consists of a 24-hour hands-on assessment (an extra hour is also provided to make up for the setup time which should take approximately 15 minutes), the environment is made of 5 Azure resources, 2 Azure AD Users, and 2 Enterprise Applications which are spread across two tenants. You get access to a VM and that VM doesn’t count as a valid target. The goal of the exam lab is to compromise all the resources and capture the final flag.
After the exam has ended, an additional 48 hours are provided to write up a detailed report, which should contain a complete walkthrough with all of the steps performed, as well as practical recommendations. The entire lab can be reverted, which will bring it back to its initial state.
The initial machine does not come with any tools so you will need to transfer those, I personally did this using RDP. Unlike Offensive Security exams, it is not proctored and you do not need to let anyone know if you are taking a break.
I started my exam on the 11th of November 2023 at about 11:30 am Sydney time, and in about three hours I had compromised all of the required resources within the two tenants in scope. I did not find any major blockers and was able to make progress through most of the exam.
I honestly did not expect the exam to be that easy and I had to email support to make sure I hadn’t skipped anything. After receiving confirmation from them I started writing up the report which took me about two hours to complete and ended up being only about 17 pages. I simply added an executive summary at the beginning which included overall background, results, and recommendations, as well as detailed information about each step and remediation strategies for each vulnerability that was identified.
If you are worried about being able to pass the exam, and as long as you understood the concepts explained in the course you shouldn’t have any issues clearing it.
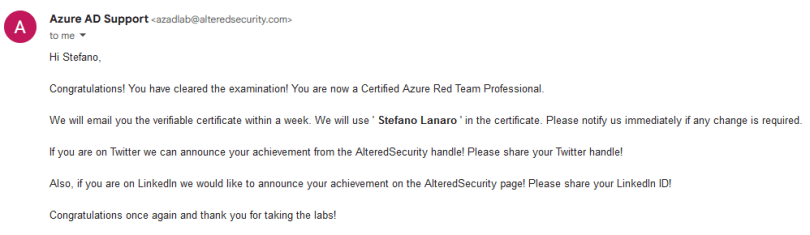
After finishing the report I sent it to the email address specified in the portal, received a response almost immediately letting me know it was being reviewed, and about 3 working days after that I received the following email:

I also received the digital for it on Accredible a couple of days later.
Conclusion
Overall this was an extremely great course, I learned a lot of new techniques and I now feel a lot more confident when it comes to Azure Active Directory engagements. This is a relatively new area and being proficient in it can give you an edge over the competition. I am sure that even seasoned pentesters would find a lot of useful information in this course.