
Secure Shell Protocol (SSH) has been a cornerstone of cryptography and security since it was de 2023-12-22 10:17:54 Author: blog.qualys.com(查看原文) 阅读量:37 收藏
Secure Shell Protocol (SSH) has been a cornerstone of cryptography and security since it was developed in early 1995. Organizations rely on SSH for secure communications within several popular software products. The recent Terrapin Attack highlights the importance of maintaining full visibility of your attack surface and the urgency required to identify all external-facing instances of the SSH vulnerability that can be exploited by attackers.
In this blog post, we’ll provide context into the SSH vulnerability and show you how Qualys CSAM with External Attack Surface Management can quickly identify ALL assets impacted, including on-prem, cloud, IoT, OT, and external internet-facing—along with the cyber risk context required to prioritize remediation efforts. The vulnerable SSH exposed on the internet poses significant threats to organizations, their subsidiaries, and acquired entities as they are visible to threat actors, and they can exploit CVE-2023-48795 to launch an attack.
Why Are the Terrapin Attacks So Important?
The discovery of CVE-2023-48795 via the Terrapin Attacks highlights how even SSH is vulnerable, underscoring the importance and continued relevance of advanced vulnerability management patching strategies and vulnerability prioritization, especially for hybrid enterprise environments.
Outside of being a staple of near guaranteed security, the ease with which SSH is installed means that SSH runs on a wide array of operating systems, including devices administrators use – and the servers they use to connect to enterprise networks remotely. In simple terms, the Terrapin Attacks signify that SSH, and much of the remote access infrastructure that privileged access administrators rely on to stop sniffing attacks, has been cracked.
What Is SSH Vulnerability CVE-2023-48795?
The SSH transport protocol found in OpenSSH before 9.6 and other SSH software and libraries allows remote attackers to bypass integrity checks such that some packets are omitted (from the extension negotiation message), causing security features to be downgraded or disabled within a client and server connection (a Terrapin Attack). This allows attackers to exploit the SSH protocol, potentially gaining unauthorized access to sensitive information or compromising network security.
In simple terms, the Terrapin method of attack alters SSH data during the handshake between servers and devices, functioning as an adversary-in-the-middle (MITM) between connections that exist between remote administrators and their core, or on-prem, network. While this CVE is classified as moderate because the attack requires an active MITM to intercept and modify a connection’s traffic at the TCP/IP layer, it does allow attackers to delete consecutive messages.
Vulnerable Versions
OpenSSH versions before 9.6 and other software and libraries, including LibSSH, PuTTY, AsyncSSH, Dropbear SSH, Transmit, paramiko and golang-go.crypto are vulnerable.
What Does This Mean for You?
Scope and Impact:
This vulnerability poses a significant risk, particularly for organizations relying heavily on SSH for secure communications, which includes many popular software platforms. The exploitation of this vulnerability can lead to data breaches, system takeovers, and other malicious activities – and they happen fast.
Real-World Implications:
In a real-world scenario, an attacker could exploit this vulnerability to intercept sensitive data or gain control over critical systems using administer privileged access. This risk is particularly acute for organizations with large, interconnected networks that provide access to privileged data. In other words, CVE-2023-48795 affects nearly everyone.
What Should Organizations Do?
Qualys pulled anonymized data from our global customer base to analyze 420 million assets, including 51 million internet-facing assets. Here are the key data points:
- 48.01M (11.4%. of 420M) of all assets have been Detected with SSH service or open TCP port 22.
- 12.4M (25.8% of 48.01M) of total assets have an EOL/EOS version of SSH, indicating elevated risk.
- 6.4M (13.3% of 48.01M) of internet-facing assets have been detected with SSH service or open TCP port 22.
- 344K (0.7% of 48.01M) of external-facing assets have an EOL/EOS version of SSH, indicating elevated risk.
All Assets
| Operating System Category | Assets with SSH service or open TCP port 22 | Assets with EOL/EOS SSH service or open TCP port 22 |
|---|---|---|
| Linux | 24.6M | 12.2M |
| Windows | 36K | 23.3K |
Internet-facing Assets
| Operating System Category | Assets with SSH service or open TCP port 22 | Assets with EOL/EOS SSH service or open TCP port 22 |
|---|---|---|
| Linux | 1.23M | 328K |
| Windows | 1.8K | 1.3K |
Interestingly, over 99% of assets with SSH service are Linux assets as opposed to Windows.
With this context in mind, it is highly likely that your attack surface is exposed to some level of risk from SSH services. Here’s what you can do.
Immediate Actions:
To mitigate this vulnerability, we recommend organizations inventory and scan all systems with vulnerable SSH versions. Organizations must patch their SSH implementations as per the latest security updates. Additionally, reviewing and updating SSH key management practices quickly and often is crucial.
Long-Term Solutions:
For long-term protection, we advocate for regular security audits and adopting a layered security approach. Implementing robust firewalls, intrusion detection systems, and rigorous access controls can significantly reduce the risk of such vulnerabilities.
Take Action With the Enterprise TruRisk Platform
Qualys offers a suite of tools and services designed to identify, prevent, and mitigate vulnerabilities like CVE-2023-48795. With the Enterprise TruRisk Platform, customers can monitor their networks, manage vulnerabilities, and maintain compliance with over industry 240 standards. When it comes to CVE-2023-48795 specifically, here is how Qualys can help:
Inventory SSH with Qualys CSAM
Qualys CSAM provides multiple ways to identify and manage remediation and mitigation for assets containing SSH across your hybrid environment, including cloud, on-prem, IoT/OT, and internet-facing assets. Here are some key examples.
You can identify assets with a known vulnerable version of OpenSSH with this query:
Software Query: software:(name:OpenSSH and version < 9.6)
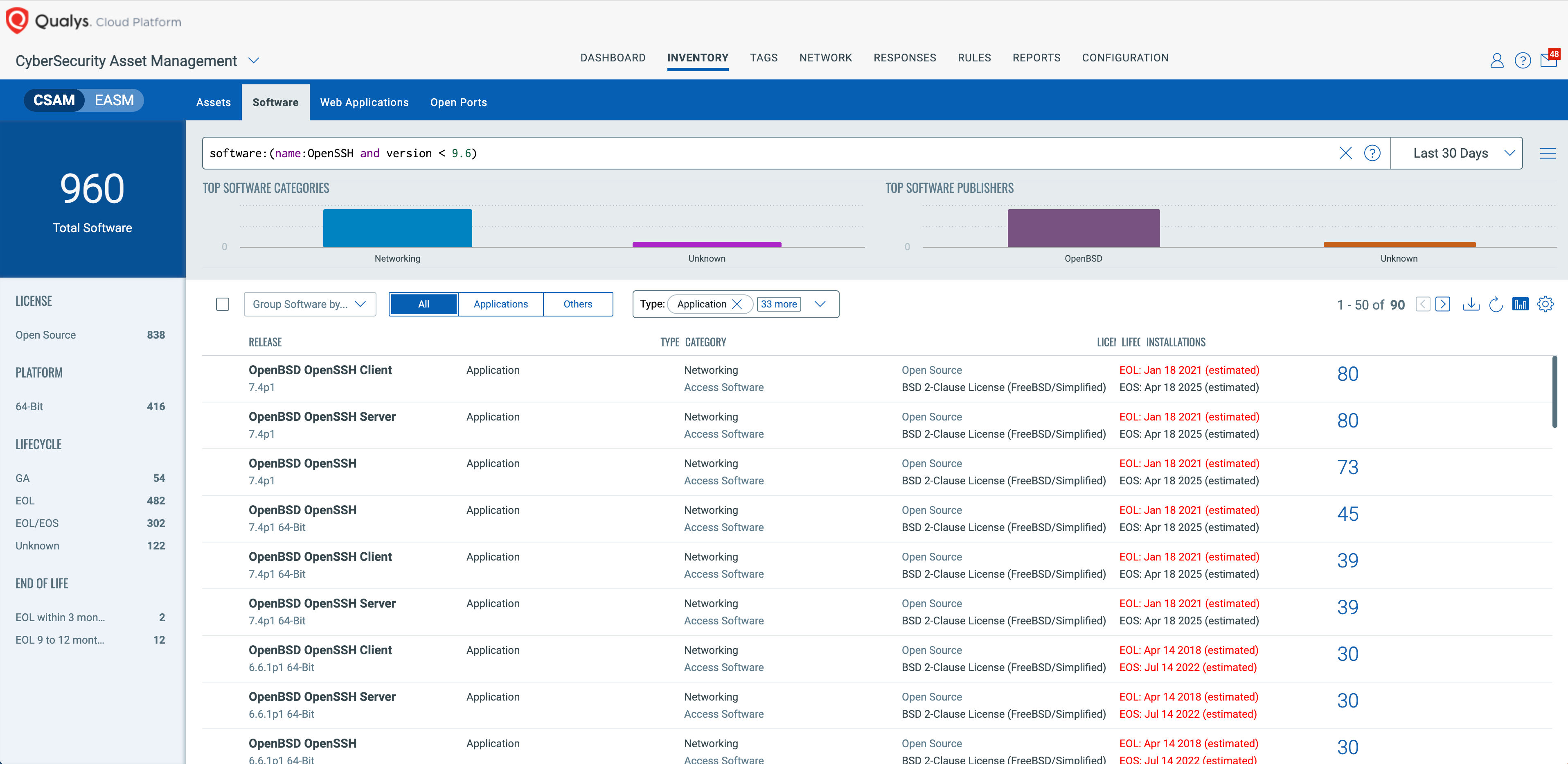
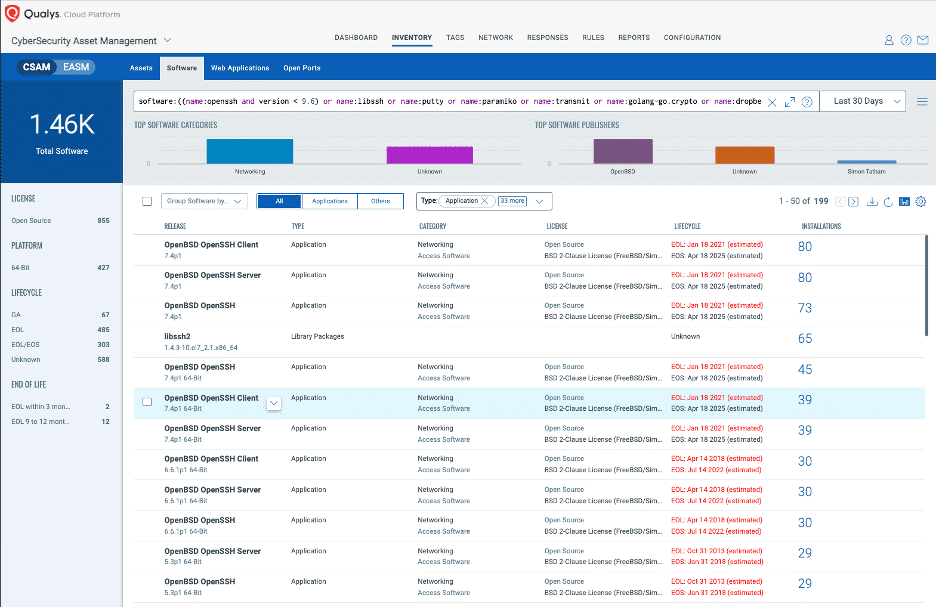
Knowing that OpenSSH is not the only software vulnerable with this CVE, you should consider adding similar software name tokens to the query to find other potentially vulnerable software such as libssh, libssh2, putty, etc., especially as new information on vulnerable software is updated by researchers.
Software Query: software:(name:openssh or name:libssh or name:putty or name:paramiko or name:transmit or name:golang-go.crypto or name:dropbear)
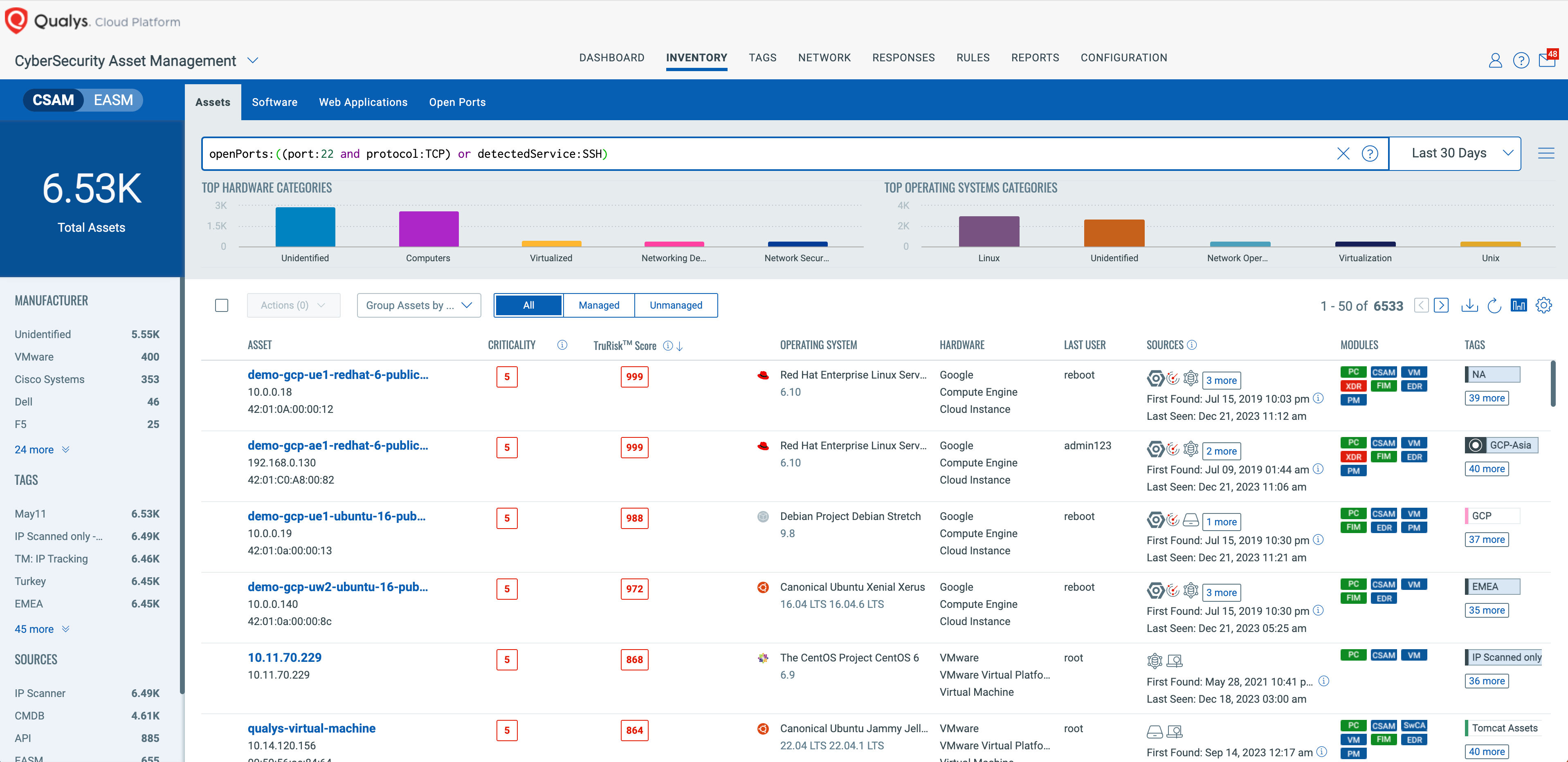
If you have compute assets that do not have the necessary Qualys Agent or have not had an authenticated scan that discovers software, you can still query for any SSH servers using port and service tokens.
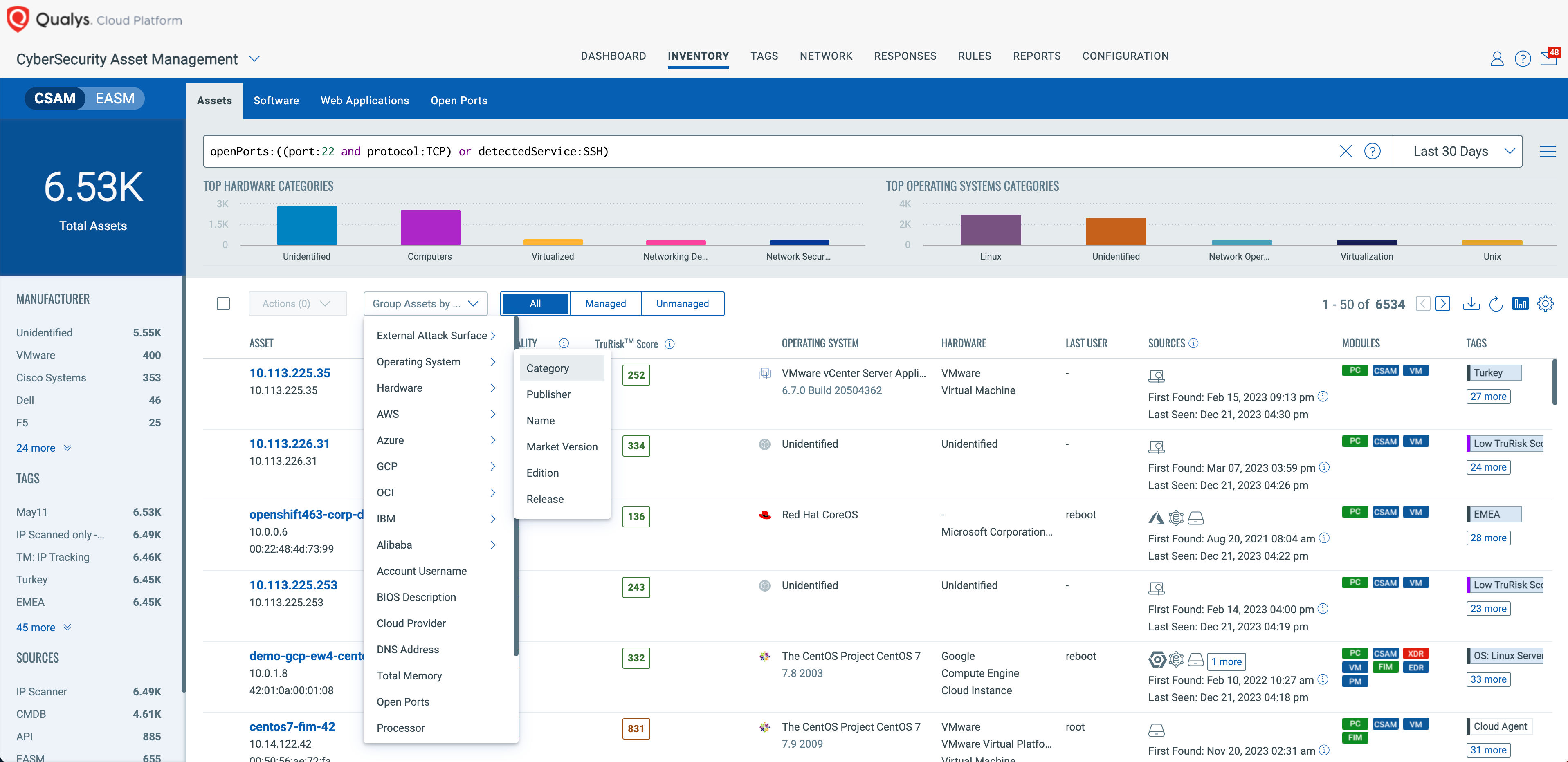
Asset Query: openPorts:((port:22 and protocol:TCP) or detectedService:SSH)
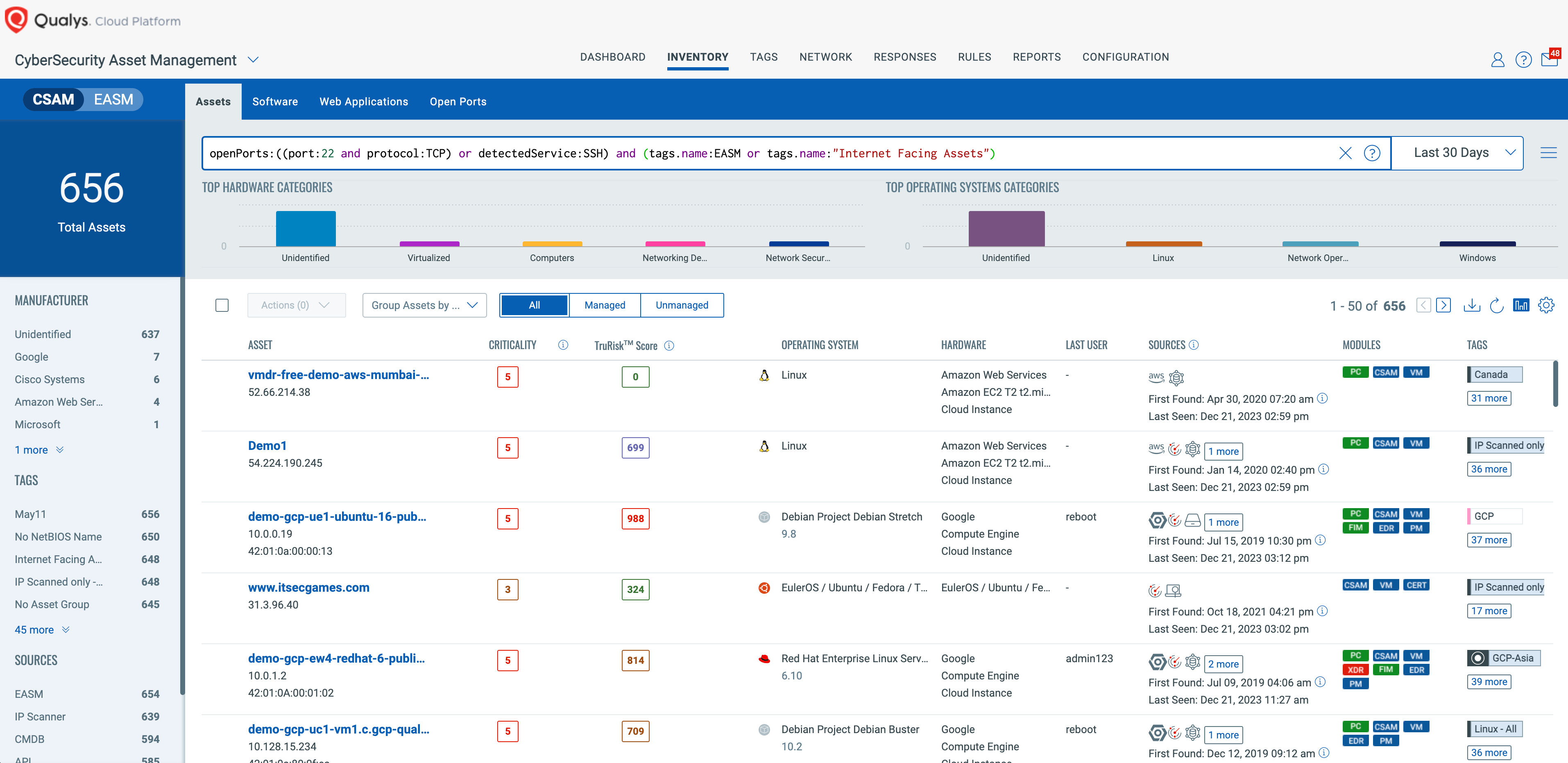
You can further focus that query on internet-facing assets exposing SSH by adding appropriate tags to the QQL.
Asset Query: openPorts:((port:22 and protocol:TCP) or detectedService:SSH) and (tags.name:EASM or tags.name:”Internet Facing Assets”)
Tag Potentially Vulnerable Assets With CSAM
In addition to identifying all assets with SSH installed, using dynamic tags and tagging the assets will allow for swifter remediation actions and clearer reporting as you mitigate the threat.
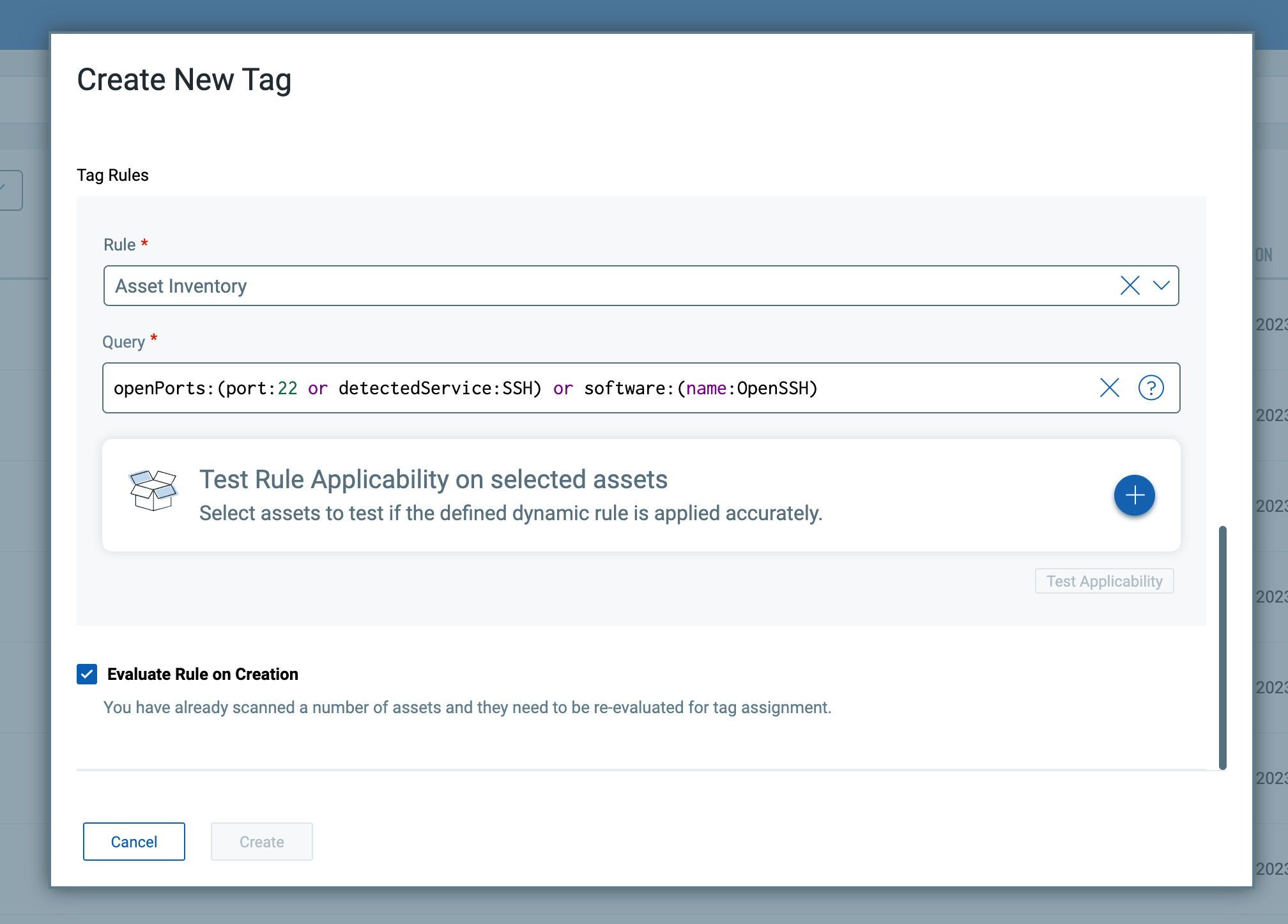
Port Rules To Manage Authorization of SSH Servers and Inform TruRisk Score
CSAM also recently introduced the ability to create port authorization rules in Rules > Open Ports. You use tags to select which assets are unauthorized to have the open port(s) and assign a QDS score to each open port to inform the TruRisk Score of the asset when the unauthorized open port is detected.
After using tags to select the asset scope, you can then define the unauthorized ports and the QDS score to use:
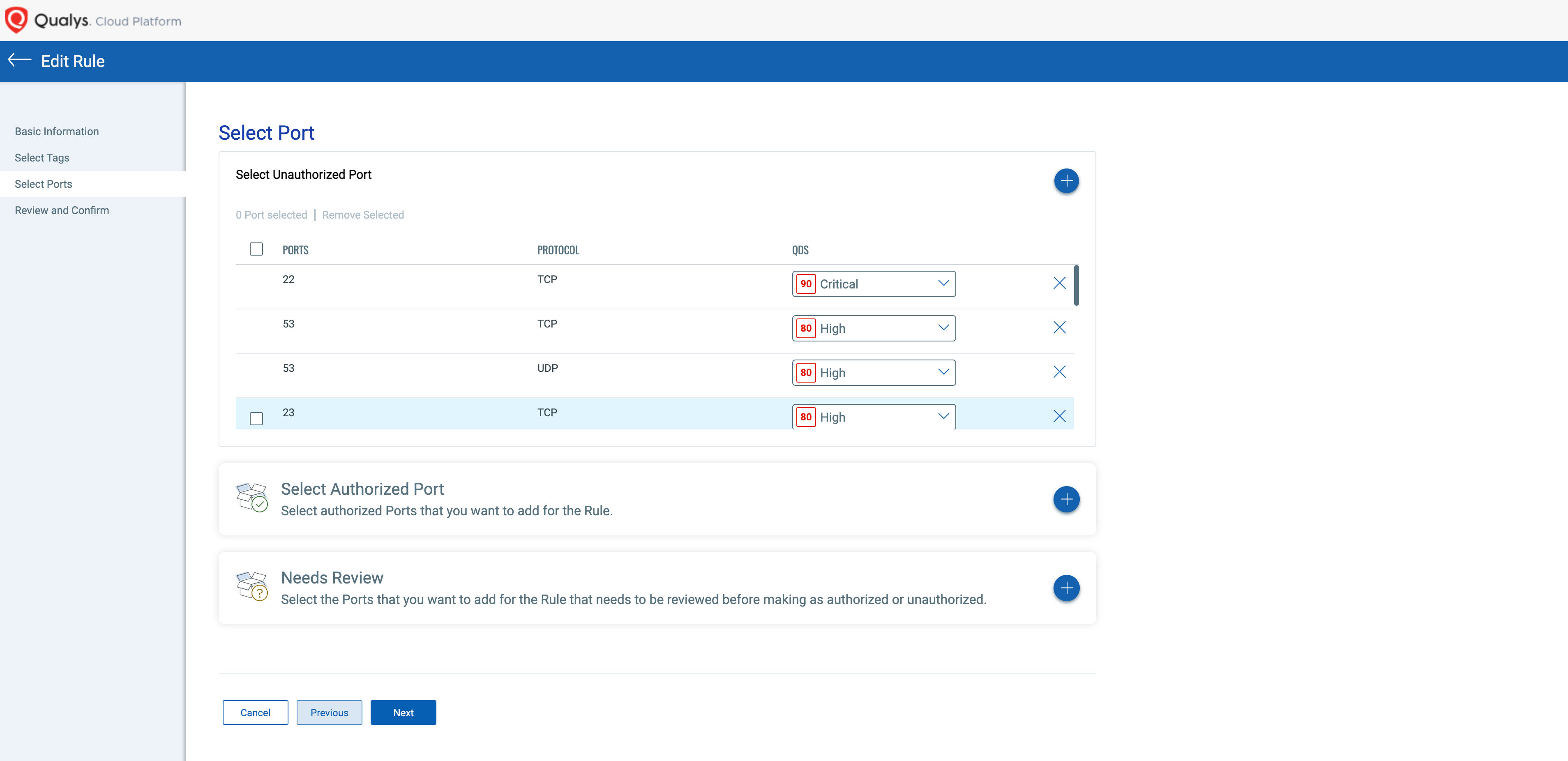
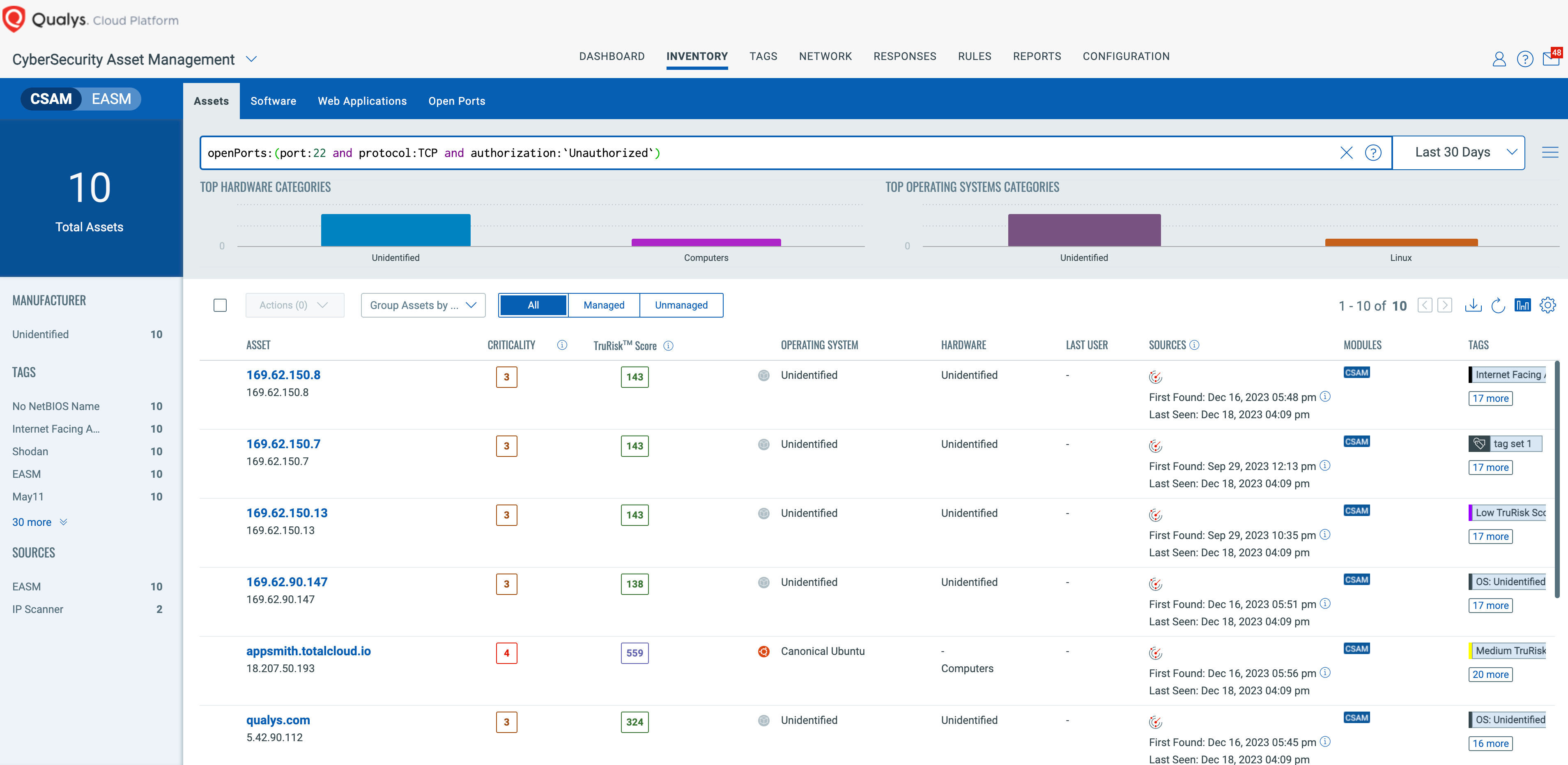
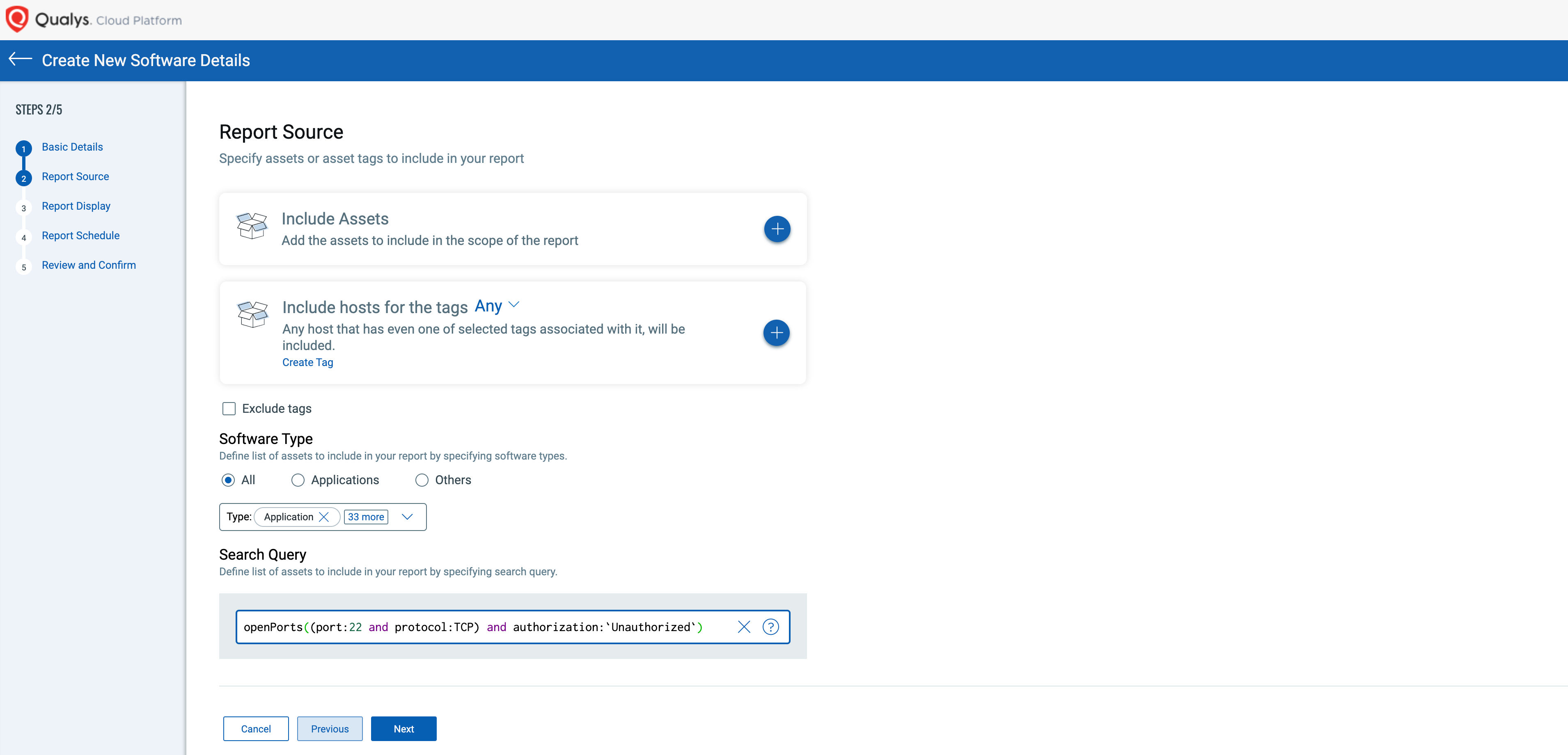
Port Rules will then assign an openPorts:(authorization:) attribute to any assets with an unauthorized port. You can then focus on assets with unauthorized exposure of the default ssh port using a query like:
Asset Query: openPorts((port:22 and protocol:TCP) and authorization:`Unauthorized`)
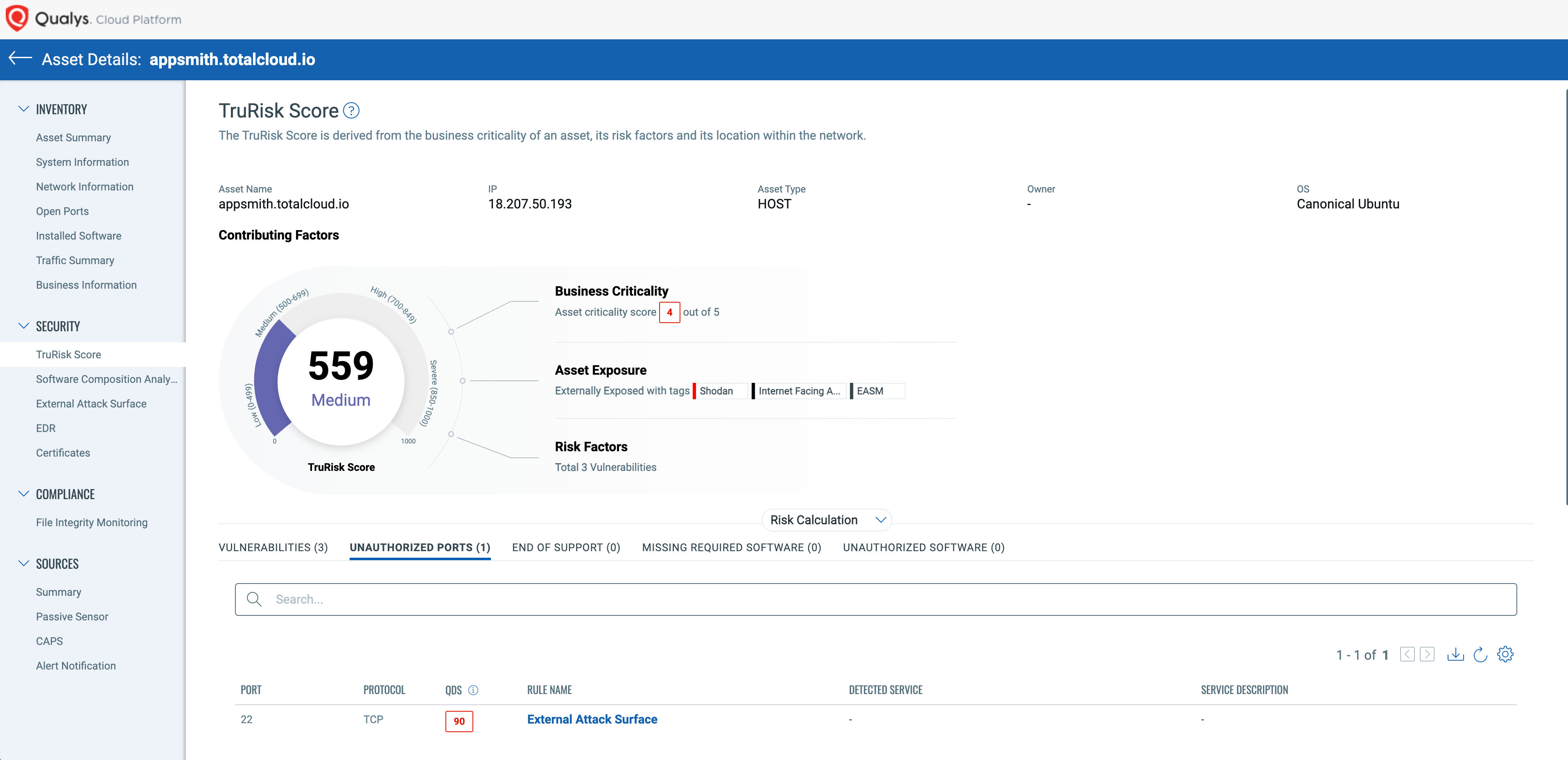
You can see the TruRisk contribution from the unauthorized port in Asset Details > TruRisk Score.
Group Asset by Attributes When Remediating
With any of the queries above, you can also use the Group Assets By option in CSAM Inventory screens to get the list of assets with specific criteria/attributes, such as External Attack Surface domain, cloud providers, operating system category, etc. This is very useful if you have different teams focused on different types or deployment locations of assets.
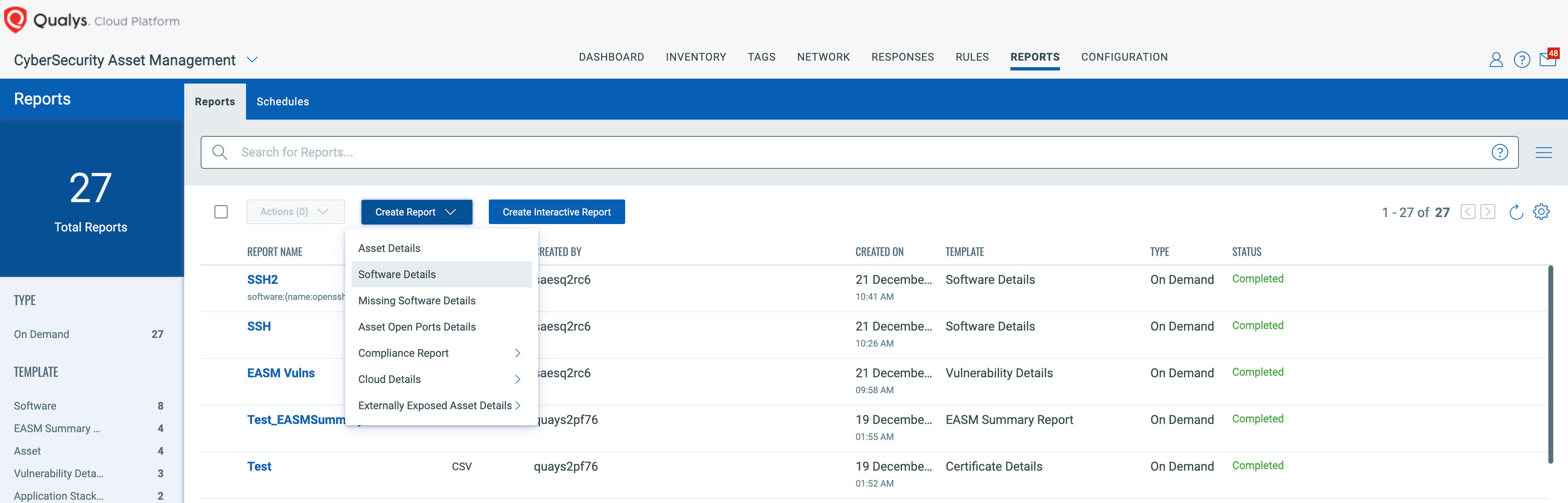
CSAM Reporting
Lastly, using CSAM’S Report options, you can generate CSV reports using queries and/or tags to provide a list of assets and/or software to remediation teams.
Discover Vulnerable Instances Using Qualys VMDR
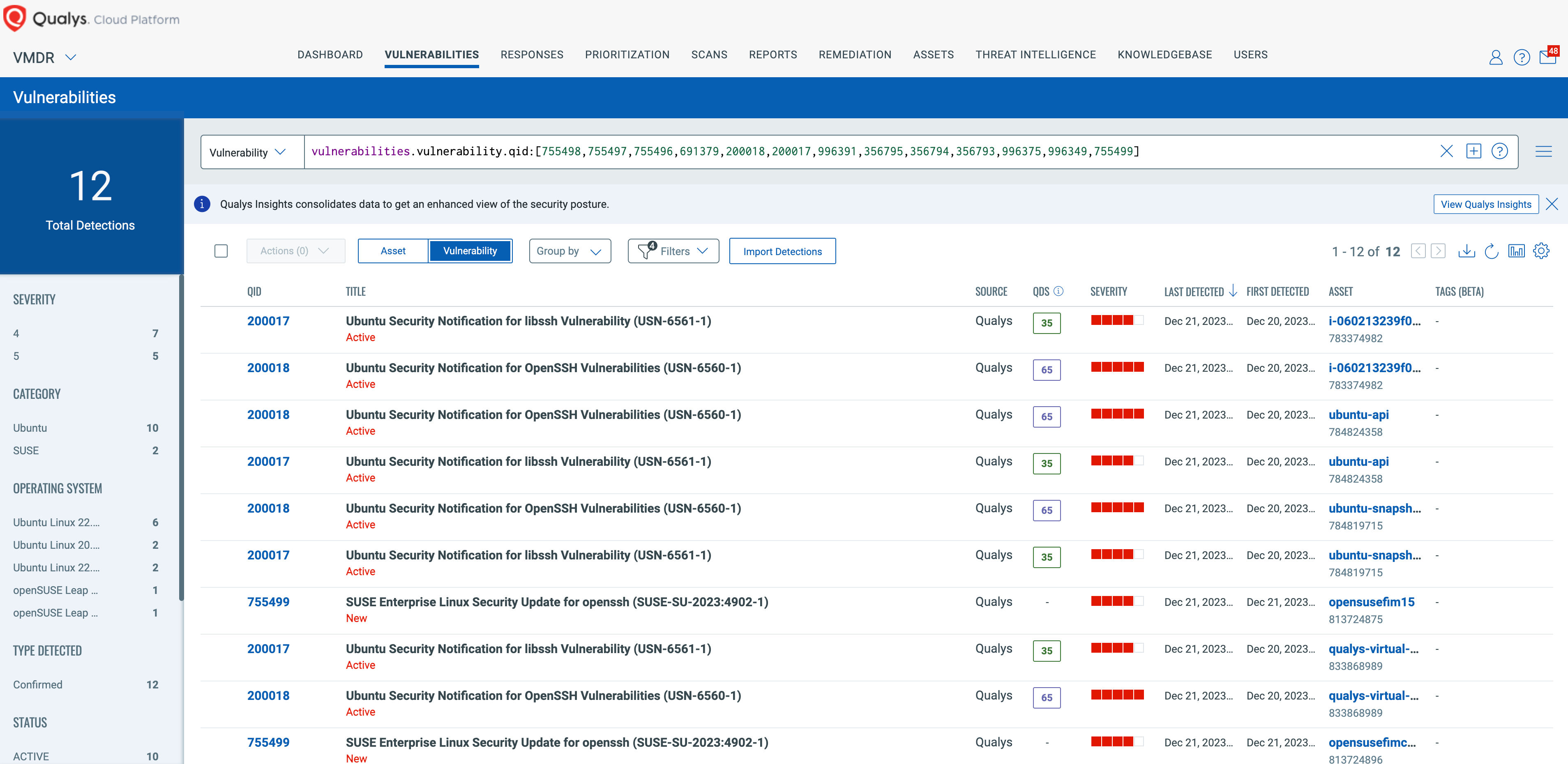
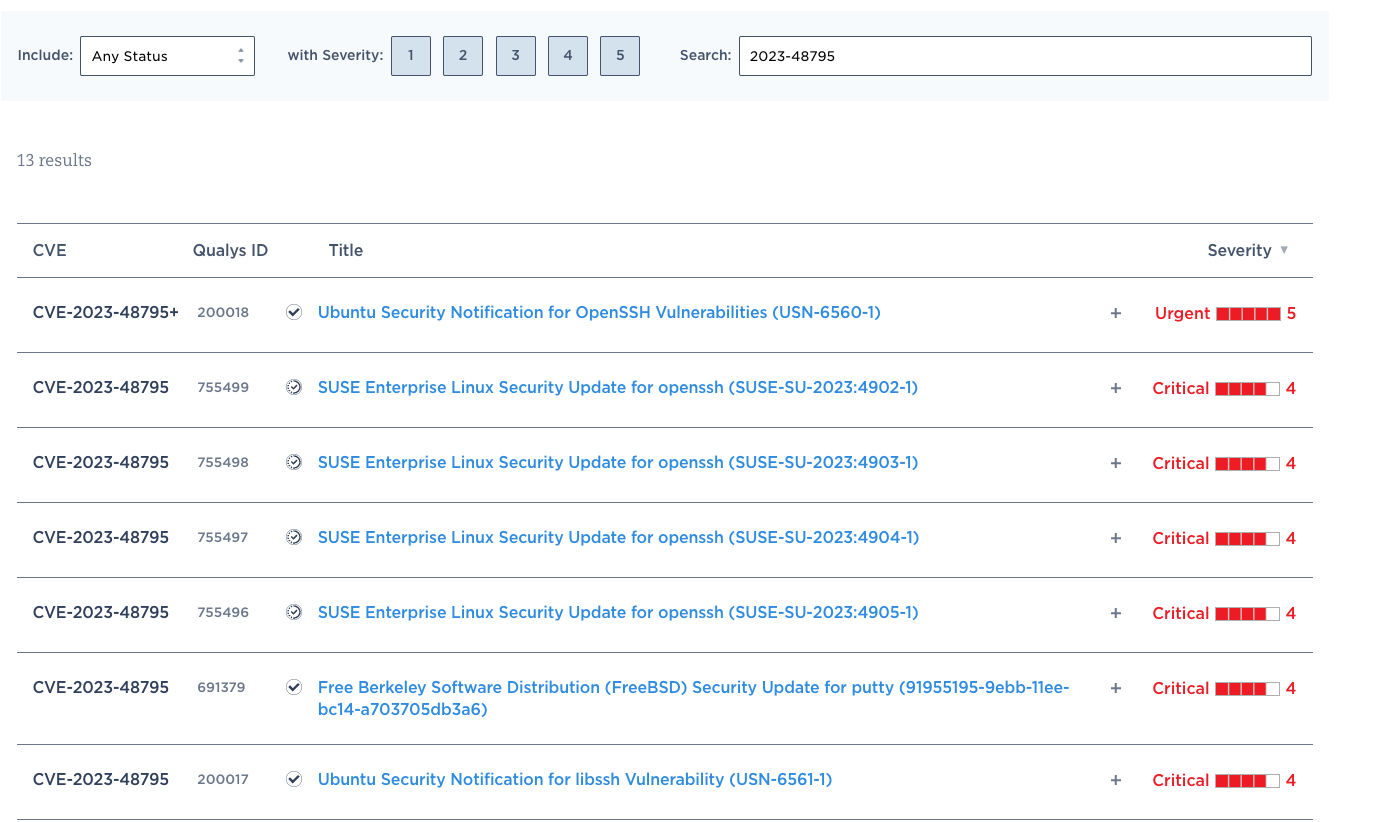
Search the following QIDs within your VMDR subscription to find vulnerable instances of SSH in your environment:
| QID | Title |
|---|---|
| 755498 | SUSE Enterprise Linux Security Update for openssh (SUSE-SU-2023:4903-1) |
| 755497 | SUSE Enterprise Linux Security Update for openssh (SUSE-SU-2023:4904-1) |
| 755496 | SUSE Enterprise Linux Security Update for openssh (SUSE-SU-2023:4905-1) |
| 691379 | Free Berkeley Software Distribution (FreeBSD) Security Update for putty (91955195-9ebb-11ee-bc14-a703705db3a6) |
| 200018 | Ubuntu Security Notification for OpenSSH Vulnerabilities (USN-6560-1) |
| 200017 | Ubuntu Security Notification for libssh Vulnerability (USN-6561-1) |
| 996391 | Python (Pip) Security Update for golang.org/x/crypto (GHSA-45×7-px36-x8w8) |
| 356795 | Amazon Linux Security Advisory for openssh : ALAS-2023-1898 |
| 356794 | Amazon Linux Security Advisory for openssh : ALAS2023-2023-462 |
| 356793 | Amazon Linux Security Advisory for openssh : ALAS2-2023-2376 |
| 996375 | Rust (Rust) Security Update for golang.org/x/crypto (GHSA-45×7-px36-x8w8) |
| 996349 | GO (Go) Security Update for golang.org/x/crypto (GHSA-45×7-px36-x8w8) |
| 755499 | SUSE Enterprise Linux Security Update for openssh (SUSE-SU-2023:4902-1) |
Patch Vulnerable Systems
Qualys customers have several ways to expedite remediation for vulnerable applications.
You can use Patch Management to patch vulnerable applications as patches are released. There are already patches issued for many commonly used applications containing SSH. With Patch Management, Qualys customers can quickly apply patches using both Windows and Linux.
In addition, Qualys CSAM can consolidate across teams through direct integration with Configuration Management Database (CMDB) and IT Service Management (ITSM) ticketing tools. IT tickets can even be automatically assigned by owner or group based on Qualys tagging, saving significant time in triaging ticket assignments. When it comes to exploitable vulnerabilities, every second counts—which is why it is critical to remove technology silos.
Additional Resources
Please stay tuned for more updates. Qualys Research team will be regularly updating the blog as more details become available. In the meantime, please leverage the Vulnerability Detection Pipeline to track developments and the status of new vulnerabilities.
- About the Qualys Vulnerability Detection Pipeline
- Internal + External Attack Surface Management with CSAM
- Qualys Vulnerability Management New QID Development, Prioritization, and New QID Feature Request Process
- Qualys Vulnerability Detection (QID) Recurring Vendor and Product Support Index
- Qualys Customer Service Portal (CSP) | Vulnerability Management New QID Feature Request Case Creation Process
Contributors
- Chris McManus, Senior Product Marketing Manager, Qualys
- Bob Beliveau, Principal SME, CyberSecurity Asset Management, Qualys
- Kunal Modasiya, Vice President, Product Management, CyberSecurity Asset Management, Qualys
如有侵权请联系:admin#unsafe.sh