2023-12-18 11:34:13 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
I. Background of xorbot
In November 2023, NSFOCUS Global Threat Hunting System detected that a type of elf file was being widely distributed and accompanied by a large amount of suspected encrypted outbound communication traffic. However, the detection rate of mainstream antivirus engines on this file was close to zero, which aroused our curiosity. After further manual analysis, we identified a novel botnet family with strong occultness. Given that the family uses multiple rounds of xor operations in encryption and decryption algorithms, NSFOCUS Research Labs named the Trojan xorbot.
Unlike a large number of botnet families secondary developed based on open source code, xorbot was built from scratch with a brand-new architecture. Developers attached great importance to the concealment of Trojan horses and even sacrificed propagation efficiency for better concealment effect. The latest version of Trojan horse added a large amount of garbage codes on the basis of the initial version, which increased the file volume by more than 30 times. On the traffic side, it also took painstaking efforts to randomly generate data sent during the initial online interaction stage, and introduced encryption and decryption algorithms to encrypt and store key information, thus invalidating the method of detecting character features in communication traffic.
II. Sample Analysis of xorbot
Version change
Shortly after the initial propagation version of xorbot, which first appeared in November 2023 with a file size around 30 KB, NSFOCUS Global Threat Hunting System detected another variant of the Trojan that soared nearly 30-fold to close to 1200 KB.
Through further analysis, we confirm that the xorbot Trojan communicates in the new version by introducing _libc_connect() and _libc_recv() series functions of the libc library, but the core function modules remain unchanged.
Trojan developers have added a large amount of invalid code to mask malicious branches, making the current antivirus engine detection rate close to zero. Although junk code can oversize files and affect their propagation efficiency, these codes seem normal, thus enhancing the occultness of Trojans. In recent years, more and more attack groups have mastered independent communication tools, which makes the spread of Trojan horses controllable to some extent. It takes a certain time cost to build a brand-new architecture of botnet Trojan horses. Under this circumstance, attackers pay more attention to the concealment of Trojan horses.
Encryption and decryption algorithms
Xorbot developers use a set of encryption and decryption algorithms that borrow Mirai source code. When interacting with C&C, they will encrypt the data to be sent before sending it. After receiving the command from the server, it will also be decrypted by this algorithm before use.
In addition, some sensitive string information in the file is also stored in encryption mode, which needs to be decrypted by this algorithm before use. In addition, many junk codes that will not be used are embedded in the Trojan, which also makes the strings in the file look normal and reduces the probability of exposure.
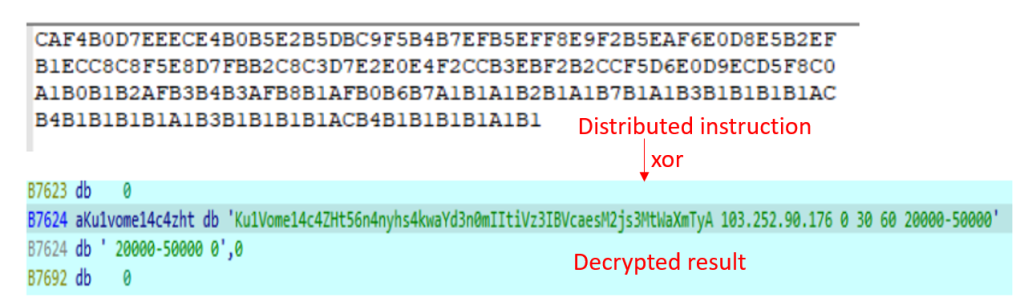
The encryption and decryption algorithm is implemented by multiple exclusive OR operations. Take decryption as an example. During decryption, the data to be decrypted is taken out byte by byte, and then the table_key (0x89F16) hard-coded in the file is split into 4 bytes (0x16, 0x9F, 0x08, 0x00), followed by multiple rounds of exclusive OR operations. Finally, the decryption result is obtained after splicing. In this version, the actual effect is equivalent to the overall exclusive OR 0x81.
Persistence
Xorbot maintains persistence by adding crontab. The character information involved is encrypted and stored, and written after being decrypted during Trojan running.
It also better hides itself by disguising the malicious file name as “ld-unixdev.so.6” (similar in name to a system dynamic library).
Communication and C&C Instructions
Unlike most traditional botnet families, xorbot is not eager to actively send packets after establishing a connection with the server, but passively waits for a reply from the server. The data sent by the server for the first time is randomly generated.
After receiving the data returned by the server, xorbot will decrypt it first and then divide the decrypted string into multiple substrings with space as a separator. Usually, the packet length returned by the server in the first round is 0x62, 0x68, 0xAC or 0x40. The data obtained after decryption does not have spaces and only has a string. Then, the controlled terminal will generate a random string of indefinite length and feed it back to the server, and continuous interaction is required to maintain the connection until an attack instruction is received.
The interaction process is as follows:
When the packet length received by the bot is 0x5B, the bot will choose to exit or upload system data in combination with the received content, wherein the collected system information data is organized in json format and then encrypted for transmission.

In another case, the Trojan will launch DDoS attacks in different ways according to the number of substrings divided by spaces and the length of the first substring based on the received data. The DDoS attack methods supported by the current version are as follows:
Table 1 DDoS attack modes supported by xorbot
| GRE_F | gre_flood |
| UDP_F | udp_flood |
| tcphandshake | tcp_flood |
| TCP_SYNF | syn_flood |
| TCP_ACKF | ack_flood |
Each DDoS instruction consists of a fixed-length random string and target information separated by spaces. Monitoring data show that xorbot is in the early stage of development, and its primary purpose is still to obtain enough bots. Its controllers are more inclined to use gre_flood and TCP_flood to launch DDoS attacks on targets. The attack targets are mainly selected from European and United States countries.

Compared with the traditional botnet-like family, xorbot is unique in the design of communication flow and instruction format. Although it does not choose strong concealment such as tunneling or tor proxy, it seems to know well about the idea of botnet monitoring and tracing, and every detail of its design creates certain obstacles to instruction tracing. On the one hand, encrypted instructions make Trojan communication traffic highly concealed; on the other hand, passively sending online packets and randomly generating online data packets with variable length also make it difficult for analysts to extract traffic features based on character information.
III. Conclusion
Xorbot is a fast-growing new botnet family. The current version covers various CPU architectures such as x86, MIPS, Renesas SH and ARM. Although there is no built-in propagation module in the current version of this Trojan, it is not difficult to speculate that there is a professional attack group behind it from the countermeasures shown by malicious samples and their huge number of propagations, which is very likely to have independent propagation tools. In addition, the attacker pays great attention to the concealment of malicious samples and adopts many technical means to make the Trojan have a high concealment effect on both the file side and the traffic side. By the time of publication, the detection rate of mainstream antivirus engines on the Trojan is still close to 0, which is worthy of our vigilance.
IV. IOC
203.55.81.214
073202212CCF6A58EBC04E33D5B90833
598E8D8D2AEBA46DDBD9155480FEA972
The post xorbot: A Stealthy Botnet Family That Defies Detection appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/xorbot-a-stealthy-botnet-family-that-defies-detection/
如有侵权请联系:admin#unsafe.sh










