2023-12-18 01:45:15 Author: securityboulevard.com(查看原文) 阅读量:14 收藏
Welcome to the high-stakes world of GitHub, where your code isn’t just a collection of functions and classes, but a treasure trove brimming with secrets — the VIPs of your digital soiree. But here’s the twist: without the right security, they’re more like sitting ducks at a carnival game.
Enter the world of GitHub secrets scanning tools, the vigilant sentinels of your digital gala. These tools are not just about uncovering secrets; they’re about guarding them with the vigilance of an elite security team, ensuring that no intruder can slip through the cracks unnoticed.
So, are you ready to turn every stone in your GitHub repositories? Let’s roll up our sleeves and dive deep into the world of secrets scanning tools, where every line of code is a potential lead in this cybersecurity detective story.
The dualities of GitHub secrets scanning
Secrets scanning in GitHub is anchored by two fundamental strategies: proactive prevention and reactive detection, each serving a critical function in safeguarding code repositories. Let’s look at what they mean and some best practices.
Proactive prevention in development phases
The proactive aspect emphasizes the interception of secrets during the development phase. This is achieved by integrating scanning solutions within the CI/CD workflows. The goal is to identify and resolve potential secret exposures before the code reaches the public domain, essentially nipping the problem in the bud.
In GitOps practices, early secrets detection is key. Scanning tools play a vital role in this, aligning with the GitOps methodology to enhance security in automated workflows.
Reactive detection for ongoing vigilance
Conversely, the reactive strategy focuses on the retrospective analysis of repositories. It scans for GitHub repository secrets that may have slipped past initial defenses or been introduced after deployment. This method is crucial for maintaining the integrity of repositories over time, ensuring that any latent or newly emerged vulnerabilities are quickly identified and rectified.
By combining these two strategies, GitHub secrets scanning offers a robust defense mechanism, blending early intervention with continuous oversight.
In-depth look at GitHub secrets scanning tools
Now, let’s dive into the toolbox of GitHub secret scanners, where we’ll uncover a diverse range of tools designed to detect and protect the secrets hidden in our code repositories.
Entro
Entro emerges as a revolutionary tool in the landscape of GitHub secrets security and management, offering a unique blend of comprehensive discovery, context-rich analysis, and non-intrusive operation.

Source: Entro
Entro excels not only in detecting secrets but also in securing secrets for repository, ensuring that sensitive secret keys are effectively handled, rotated, and safeguarded throughout the entire secret lifecycle.
Unlike traditional secret scanning tools, Entro provides an in-depth understanding of each secret, including its usage, associated cloud service, owner, and necessary privileges. This level of detail enables organizations to make informed decisions about secret rotation and management. Entro’s out-of-band operation ensures that it functions without interfering with R&D workflows, making it a seamless addition to any development process.
Pros:
- Secrets inventory and Comprehensive discovery: Entro excels in discovering secrets across various platforms, not just within GitHub repositories. This includes vaults, secrets stores, collaboration tools, communication tools, cloud, and CI/CD pipelines, offering an unparalleled breadth of coverage. Entro creates a secrets inventory so you will be able to know how many secrets you have and where they are. This is especially useful if you’re dealing with issues around secret sprawl.
- Secrets classification and Contextual analysis: Each secret is enriched with valuable metadata, such as ownership, creation time, and associated services. This enrichment provides a deeper understanding of the secrets, facilitating more effective management and security practices.
- Machine learning for anomaly detection: Entro employs advanced machine learning algorithms to continuously monitor secrets usage, alerting teams to any abnormal behavior or when it’s found that secrets have been exposed, which is crucial for proactive security.
- Vaults protection and misconfiguration: Entro integrates with any secrets vault your organization uses (bring your own vault). Vaults are great at creating and storing, but not securing secrets. Entro enhances a vault’s capabilities by providing end-to-end monitoring of all activity around secrets stored in the vaults.
- Over permissive secrets: Entro scans all secrets in your organization and finds those that have excessive permissions that are unused. It alerts you to revoke those secrets, or reduce their privileges.
- Public and Darkweb leakage: Entro has the technology to scan the dark web looking for exposed secrets. This is an ongoing effort as new leaks occur globally on a daily basis. Entro checks to ensure your organization’s secrets are not exposed in those incidents.
- Automated remediation response: As the world moves towards AI, Entro is finding ways to use AI for automated real-time response to secret exposures. These are still early days for AI, but Entro already has AI as part of its feature set.
Cons:
- Focused feature set: Entro’s specialized focus on secrets security and management that is completely out of band and does not interfere with the R&D work. So it doesn’t provide secrets storage/vault with features like encryption or fine-grained access control, which some organizations might require as part of their security strategy. However, Entro integrates with any vault, security tool or cloud platform you use, making it extremely flexible and powerful.
TruffleHog
If your focus is on Developers only TruffleHog is a great tool to get started with GitHub secrets scanning. It focuses on unearthing secrets hidden within code, making it a valuable asset for developers but not for security teams since it’s generating a lot of false positives and you can’t work with it on scale. TruffleHog operates by scanning code repositories for secrets, using only regular expressions to detect potentially sensitive information.

Source: TruffleHog
TruffleHog comes in open-source commercial versions.
Pros:
- Continuous scanning: Unlike tools that perform point-in-time assessments, TruffleHog runs continuously, providing real-time alerts for detected secrets.
- Automatic updates: The tool stays up-to-date with the latest regular expressions for secrets detection, those regular expressions are maintained by the open-source community which makes them very prone to mistakes.
Cons:
- False positives: TruffleHog is a pattern scanner and as such generates many false positives, like many scanning tools, requiring additional manual review to confirm actual risks.
- Maintenance and usability challenges: TruffleHog presents challenges in maintenance and usability, especially in complex, large-scale environments where custom configurations and ongoing management can demand substantial time and expertise.
- Code cloning: TruffleHog clones all your code which somewhat expands the attack surface if an attacker can access the cloned copy of the code.
- Limited contextual information: While effective in detecting GitHub repository secrets, TruffleHog may not provide as much context about the secrets.
- Open-source version is limited: While the open source version is good enough to dip your toes in the world of secrets scanning, it falls short of the best secrets tooling in areas such as scanning policies, RBAC, alerting and more.
GitHub’s own secrets scanning tool: tailored for GitHub repositories
GitHub’s own secrets scanning tool is a native feature designed specifically for GitHub repositories, offering a seamless integration for users within the GitHub ecosystem. This tool automatically scans repositories for known types of secrets, like API keys and other credentials, helping to prevent accidental exposure of sensitive information. It supports a range of secret patterns from various service providers, ensuring broad coverage. When a potential secret is detected, GitHub alerts the repository owner.
While GitHub’s native tool is a solution for many, exploring alternatives to GitHub secret scanning can offer additional layers of security and flexibility, especially for projects spanning multiple platforms or requiring more customizable features. Nonetheless, here are the tool’s pros and cons:
Pros:
- Seamless integration: Being a native GitHub feature, it integrates flawlessly with GitHub repositories, enabling users to effectively scan GitHub repos for secrets, and ensuring a user-friendly and efficient scanning experience.
- Automatic alerts: GitHub automatically notifies repository owners when secrets are detected, facilitating prompt action to secure the exposed data.
Cons:
- Limited to GitHub repositories: Its functionality is confined to GitHub, making it less versatile for organizations using multiple platforms or repositories outside GitHub. This is especially restricting as secrets aren’t just found in code, but also in other locations like S3 buckets, databases, file storage, chat conversations, emails, and more. GitHub’s secrets tool is unable to reach those locations.
- Scope of scanning: The tool primarily focuses on public repositories and may have limitations in scanning private repositories or other areas within the GitHub ecosystem.
- Dependence on secret patterns: The effectiveness of the tool is reliant on the defined secret patterns, which may not cover all types of sensitive information, potentially leading to missed detections.
Gitleaks
Gitleaks shines as an open-source champion in the arena of secrets scanning, honing in on detecting and preventing hardcoded secrets such as passwords, API keys, and tokens within git repositories. This tool is a comprehensive solution, skilled in uncovering secrets from both historical and current code. Its versatility is evident in its various installation options, including Homebrew, Docker, or Go, and binary form availability for diverse platforms and operating systems.
Pros:
- Flexibility: Its compatibility with multiple installation methods and platforms ensures it fits various development workflows.
- Real-time protection: Using Gitleaks as a pre-commit hook adds a layer of real-time security, helping to catch secrets before they are committed.
Cons:
- Open-source limitations: Being an open-source tool, it might lack dedicated support and continuous updates with commercial solutions.
- Complex configuration: For users new to secret scanning tools, setting up and configuring Gitleaks to suit specific needs might be challenging.
Git-secrets
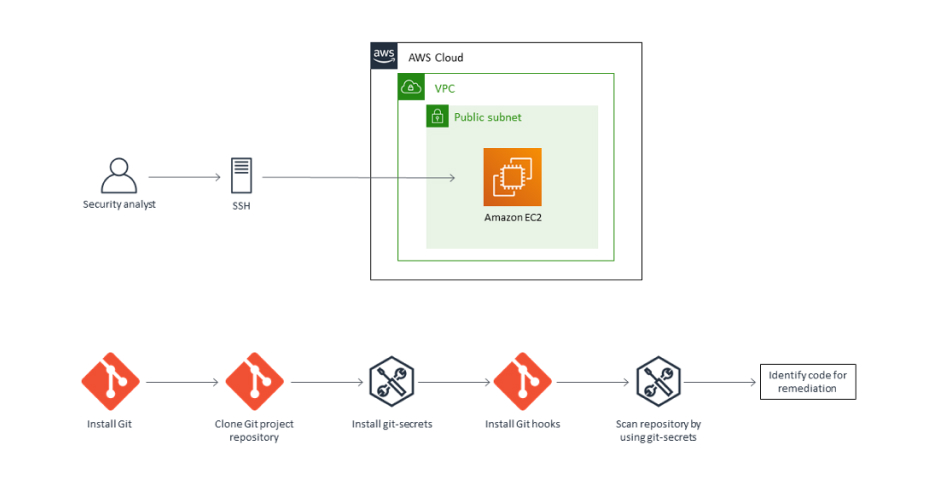
Git-secrets is a tool developed by AWS Labs, specifically designed to prevent the accidental commit of secrets into git repositories, including those on GitHub. It works by installing hooks in git repositories that scan for specified patterns indicative of secrets, such as API keys or passwords, before a commit is made.

Source: AWS
Git-secrets aligns well with GitOps framework, enhancing security in git-based workflows. Its pre-commit scanning feature becomes especially crucial in GitOps environments, ensuring that no secrets slip into repositories during the fast-paced cycles of continuous deployment and updates.
This tool is particularly effective at enforcing a proactive approach to GitHub secrets management, ensuring that sensitive data is never exposed in the first place. Git-secrets allows for custom configuration, enabling users to define their own prohibited patterns and secrets providers, enhancing flexibility and adaptability to different project needs.
Pros:
- Pre-commit scanning: Git-secrets operates at the commit stage, preventing secrets from being committed to the repository, which is a crucial proactive security measure.
- Customizable patterns: Users can define custom patterns for secrets, making the tool adaptable to various types of sensitive data.
- Integration with AWS: It offers specific features for AWS, such as scanning for AWS credentials, making it an excellent choice for projects using AWS services.
Cons:
- Setup complexity: The initial setup and configuration of git-secrets can be complex, especially for users unfamiliar with git hooks and regular expressions.
- Pattern updates: Git-secrets requires frequent updates to its patterns, demanding ongoing maintenance.
- Integration challenges: It may face complexities in integrating with diverse CI/CD environments.
SpectralOps
SpectralOps presents itself as a cutting-edge solution in the realm of secrets scanning, offering a developer-first approach to cloud security. This tool is designed to monitor, and protect codebases from the exposure of sensitive data like API keys, tokens, and credentials. It stands out with its ability to integrate seamlessly into various CI/CD environments, automating the process of secrets protection at build time. SpectralOps is not just limited to scanning code; it extends its capabilities to assets and infrastructure, identifying high-risk security misconfigurations and exposed secrets across multiple data sources in a single platform.
Pros:
- Comprehensive scanning: SpectralOps provides a broad scope of code scanning, covering code, configuration, binaries, and more, ensuring thorough secrets detection.
Cons:
- Complexity for non-developers: The tool’s developer-first approach might make it less accessible or intuitive for non-technical team members.
- Potential overhead in CI/CD pipelines: While designed for efficiency, integrating SpectralOps into CI/CD pipelines might introduce additional complexity or overhead.
- Dependence on AI accuracy: The reliance on AI and machine learning for detection means the effectiveness of SpectralOps may vary based on the accuracy and comprehensiveness of its algorithms.
GitGuardian
GitGuardian emerges as a comprehensive solution when you have to scan GitHub repo for secrets. GitGuardian’s strength lies in its automated, battle-tested detection engine, which boasts a high efficiency in scanning thousands of git repositories. This tool is not just limited to GitHub; it can integrate with various CI/CD pipelines, enhancing its utility in diverse development environments.
Pros:
- Broad detection capabilities: GitGuardian can detect a wide array of secret types, offering comprehensive coverage for secret scanning.
- Integration flexibility: GitGuardian’s ability to integrate with various code and CI/CD systems and platforms makes it a versatile tool for development workflows.
Cons:
- Complexity in configuration: Setting up GitGuardian for specific needs might be challenging, especially for teams new to secrets scanning tools.
- Potential alert fatigue: While high-fidelity alerts are beneficial, the volume of alerts generated could potentially overwhelm teams without proper alert management strategies.
Parting thoughts
If you’re about to configure your GitHub secrets scanning tool, know that each tool offers unique capabilities – from TruffleHog’s multi-platform scanning to GitHub’s own tool’s seamless integration. These tools not only cater to a spectrum of needs but also play a crucial role in identifying and mitigating GitHub vulnerabilities, balancing proactive prevention and reactive detection in securing code repositories.
Amidst these options, an end-to-end secrets security solution like Entro stands out.
Entro, with its holistic approach to secrets management, excels in providing detailed context for each secret, operates non-intrusively, and offers advanced features like anomaly detection. Entro’s unique capabilities, such as BYOV (bring your own vault) and its focus on the principle of least privilege, make it a standout choice for comprehensive secrets management in modern cloud environments. Out of all the tools above, Entro scans more places, goes deeper and is the only solution to classify secrets, alert on secrets’ abnormal behavior, protects vaults and much more.
Discover how Entro can elevate your secrets management. Schedule a demo today and explore a new horizon in GitHub secrets scanning for enterprise.
The post Securing the code: navigating code and GitHub secrets scanning appeared first on Entro.
*** This is a Security Bloggers Network syndicated blog from Entro authored by Itzik Alvas. Co-founder & CEO, Entro. Read the original post at: https://entro.security/blog/securing-the-code-navigating-code-and-github-secrets-scanning/
如有侵权请联系:admin#unsafe.sh