

Last months we've been hard at work, making Escape more versatile, reliable, and flexible.
We've added support for Insomnia collections, WP-JSON schema and included additional security tests for your business logic. More than that, you can now start scans, programmatically create applications, and automatically retrieve results through Escape's public API. These improvements are designed to make your operations smoother, enhance security, and boost the productivity of your staff.
Let's take a closer look at these updates and explore how they can benefit your organization.
Insomnia collections & WP-JSON schema support
You can never cater enough to API development needs. Escape now supports a broader range of input formats, adapting to diverse API testing environments.
What's new
- Insomnia collections: Kong Insomnia is a collaborative open source API development platform that makes it easy to build high-quality APIs.
We're now extending our DAST testing capabilities, allowing you to upload Insomnia Collections when you launch a new scan. - WP-JSON schema: Specifically for WordPress users, we now also support WP-JSON Schema. This helps to enhance security testing for WordPress-based APIs.
What's in it for you
- Broader testing reach: Cover a wider range of API design and documentation practices used within your organization
- Ease of integration: Smoothly incorporate these new formats into your existing security workflows, enhancing efficiency without compromising on thoroughness.
How to set this up
When you start a new scan, simply upload WP-JSON schema or an Insomnia collection in the first step:
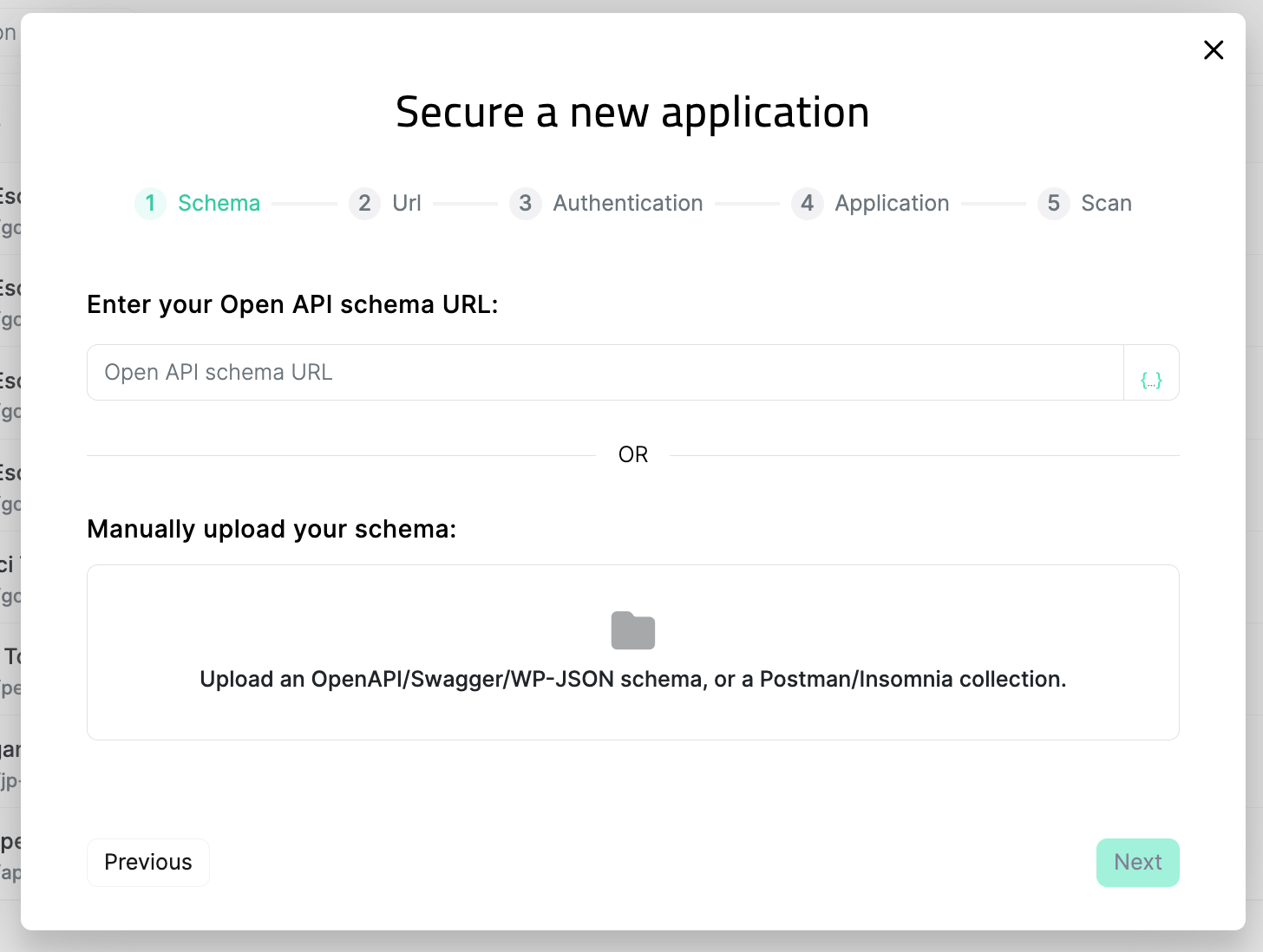
You can also upload WP-JSON schema or Insomnia collection in existing scans. Simply, go to basic configuration page:
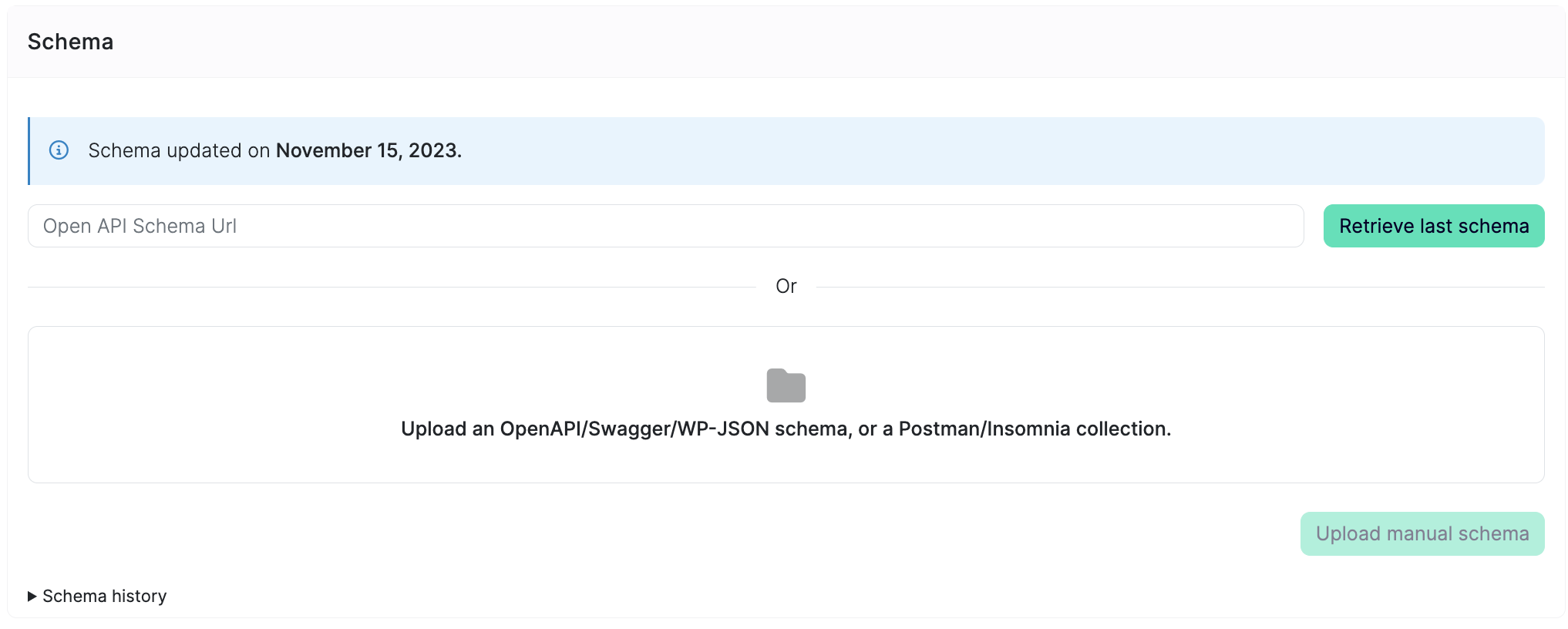
New AI-powered business logic security tests for enhanced access control
We're excited to introduce new advanced AI-powered security tests specifically designed to improve access control in your applications.
We use advanced AI algorithms to generate complex sequences of requests, meticulously uncovering and exploiting business logic flaws and potential attack vectors. This approach allows for detecting intricate vulnerabilities and attack chains that conventional methods might miss.
What business logic tests do we now cover?
- Automated tenant isolation control: When two users are configured, this test ensures strict tenant isolation, preventing unauthorized cross-tenant access.
- Sensitive endpoint brute force: Targets critical endpoints like login and reset-password, protecting against brute force attacks.
- Broken Object Level Authorization (IDOR) checks: Identifies vulnerabilities in object-level authorizations, an essential aspect of access control.
- Enhanced access control checks: Overall improvements in access control validations, providing a more robust security posture.
- Public state altering operation identification: Ensures that operations altering application data (like REST READ, UPDATE, DELETE requests, and GraphQL mutations) are adequately protected by authentication middleware.
Create & scan new applications automatically via Escape's public API
You can now effortlessly access the list of applications associated with your organization, start scans, programmatically create applications, and automatically retrieve results through Escape's public API.
💡
Escape's REST public API can be reached at https://public.escape.tech
Our goal is to help you improve your workflow efficiency and simplify your security testing process.
What can you achieve with Escape's public API?
Basic example to start a new scan for a given application
export APPLICATION_ID=<YOUR APPLICATION ID>
export API_KEY=<YOUR API KEY>
curl -X POST \
-H "Authorization: Key $API_KEY" \
https://public.escape.tech/applications/$APPLICATION_ID/start-scan
A full list of possibilities:
- Retrieve the list of applications bound to an organization
GET /organization/:organizationId/applications- Retrieve a specific scan and its results
GET /scans/:scanId- Start a new scan for the given application.
POST /application/:applicationId/start-scan- Upload an introspection response or schema on Escape for a given application.
POST /applications/:applicationId/upload-introspection- Programmatically create an application on Escape and start a scan.
POST /create-applicationKey features of the API route:
- Flexible application settings: Define your application's specifics, its name, type (GraphQL or REST), and server URL.
- Schema customization: Provide your application's schema as a string or through a public schema URL.
- Adaptable scan settings: Fine-tune your scans with settings like read/write access, customizable for safe production scans.
- Authentication support: Add authentication details for scanning, with options for different user names and authorization headers, or opt for no authentication.
- Optional repeater use: Integrate a repeater if needed for your scanning requirements.
[Enterprise] Fine-Grained Role-Based Access Control (RBAC)
A long-awaited feature for our enterprise customers is the ability to get more granular with specific permissions and assign them to different roles – a more advanced Permission-Based Access Control (RBAC) system.
As some of you might know Policy-Based Access Control (PBAC) was already supported by Escape. Now, you get more flexibility and sophistication.
What are your new benefits?
- Fine-grained control: Assign specific permissions to roles and directly associate these roles with users. This granular approach ensures tighter security and tailored access rights.
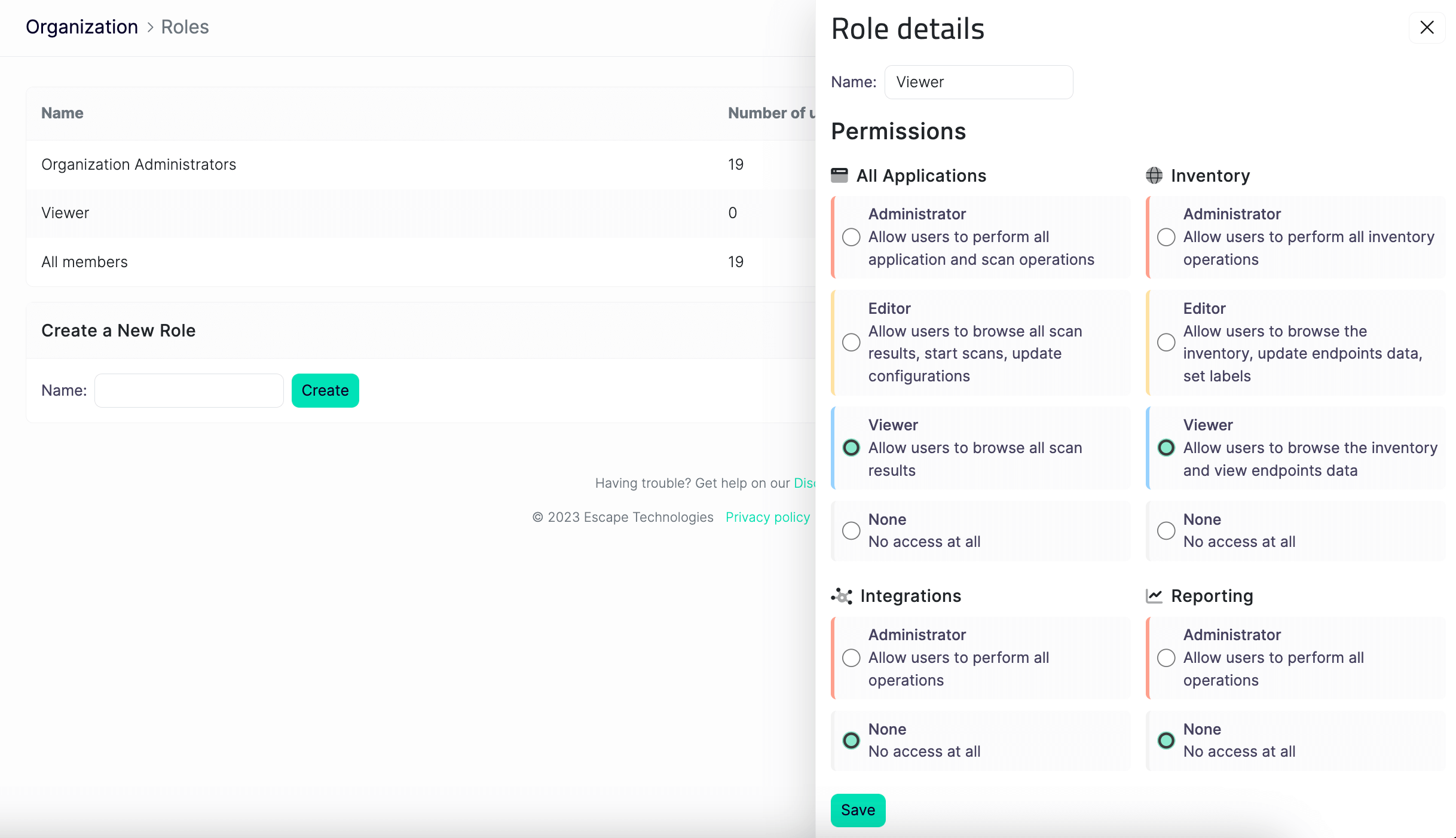
- Detailed feature access: Gain more control over various Escape features, including:
- Organization management: Decide what users get to have top-level priviliges
- Inventory oversight: Keep meticulous track of who can access your API inventory
- Application access: Manage wbo can start all scans and who can only browse the results
- Reporting: Provide or restrict access to all your organization's reports
- Integrations: Decide who can implement new integrations
SSO Integration: The new RBAC system works hand-in-hand with Single Sign-On (SSO), providing a streamlined and secure user experience.
💡 Want to learn more about Escape's product features? Check out the following articles:
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/product-features-update-december/
如有侵权请联系:admin#unsafe.sh