
"What the hell is wrong with Okta?" or some similarly colorful variation is the question I've been asked most often in the past year.
I'm not surprised anymore. Okta has had a rough time since their first breach was announced back in March 2022. Tack on several more incidents since then, and it's easy to join the bloodthirsty mob of people counting the days until Okta's imminent demise.
I'm not an Okta apologist, but their situation isn't as dire as some people think. They're going to be fine. Maybe even better than before…eventually.
WHAT?!? How could that be possible after this many problems??!!
Let's start with a freakish comparison between Okta and the most popular tale in human history.
A Cinderella story
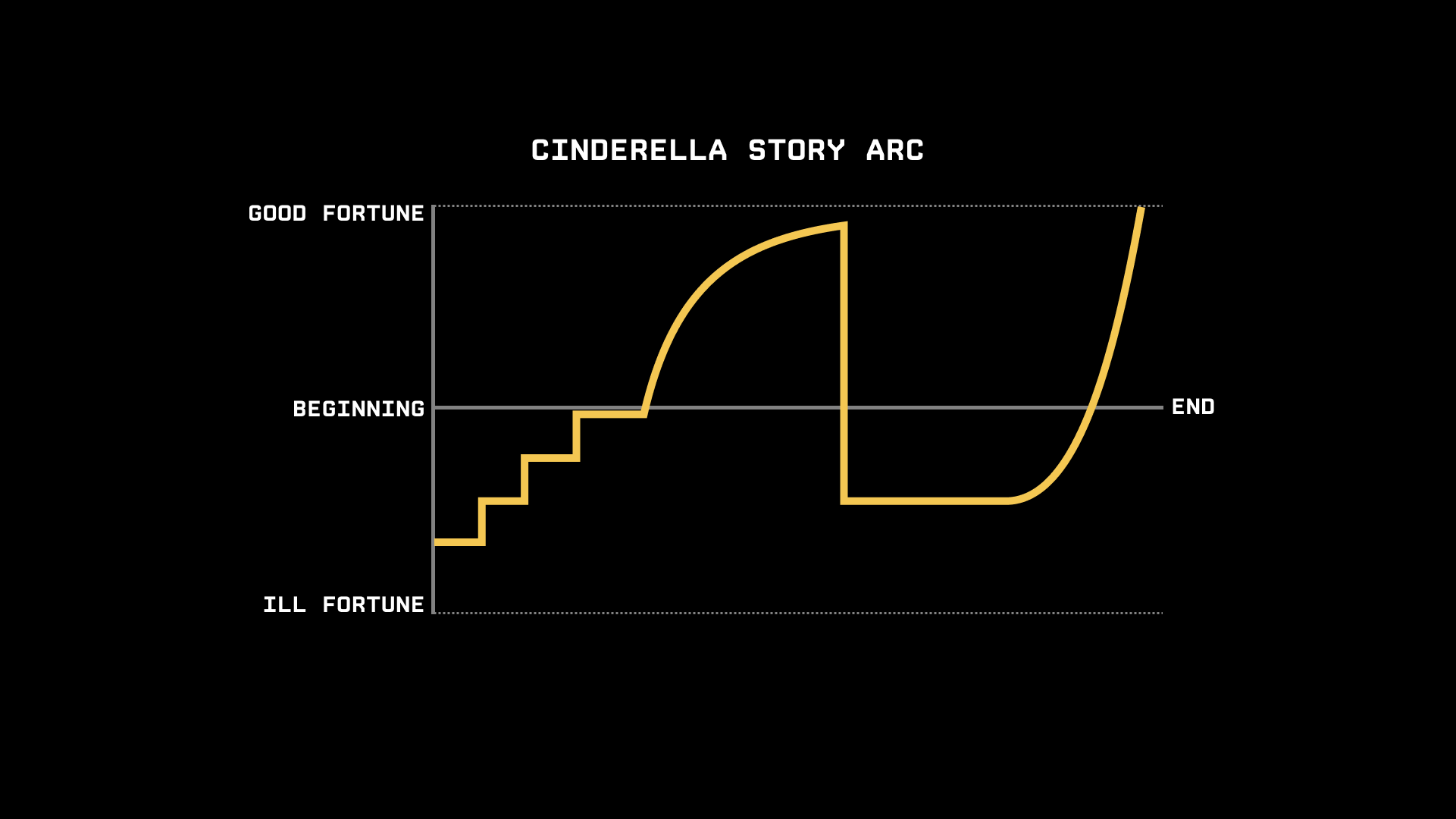
All great stories have an arc. We understand this implicitly because of how we feel when watching a show, reading a book, or seeing a movie. Most of us don't think about the mechanics of a story — it's just something we experience emotionally.
Kurt Vonnegut, one of the greatest storytellers of all time, turned the fuzzy, hard-to-quantify concept of story arcs into a science. In his short (and hilarious) lecture on the Shapes of Stories¹, he defined several of the most common patterns great stories follow.
One specific type of arc keeps churning out hit after hit. It's called the "Cinderella story." Here's what it looks like:
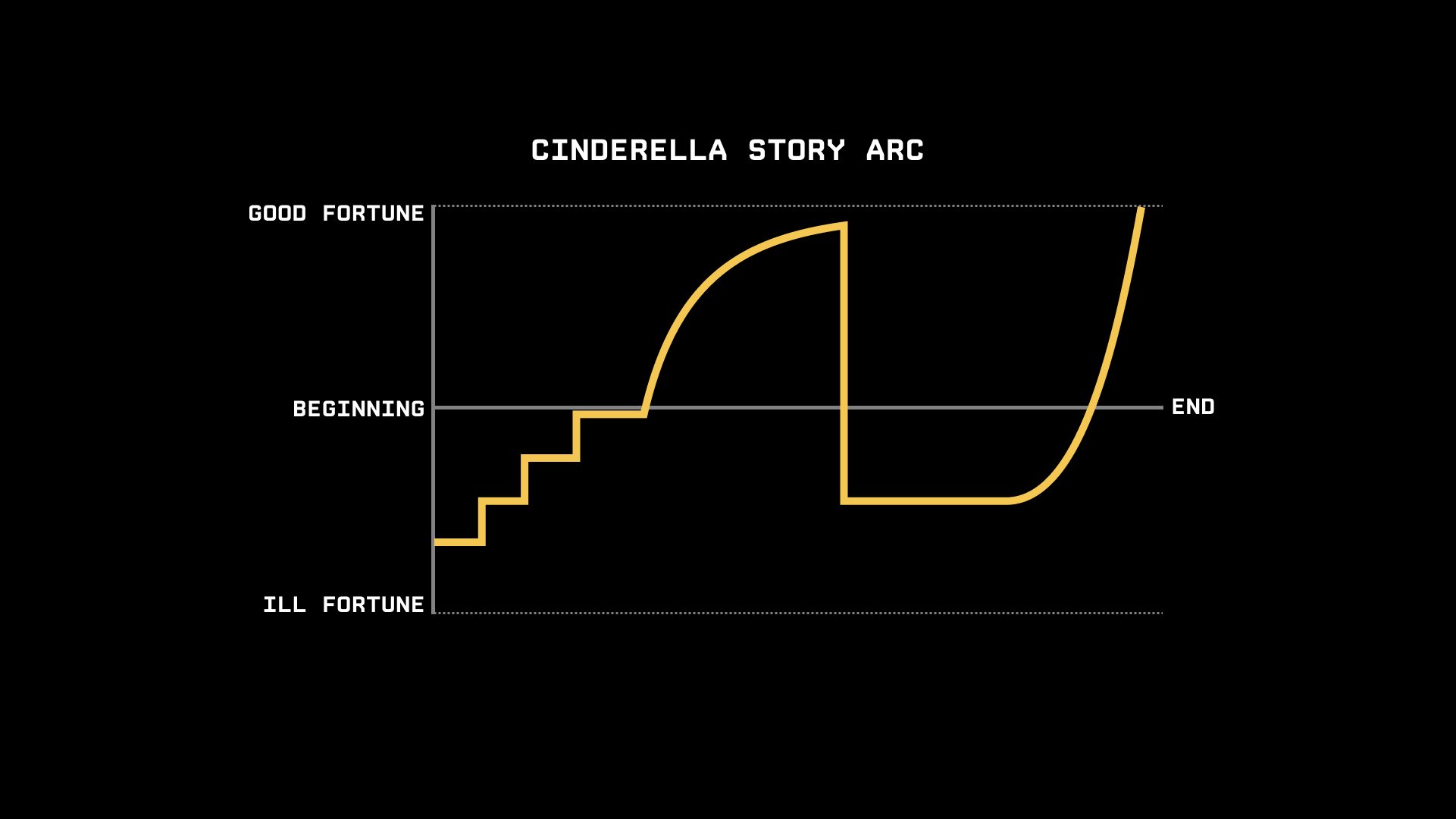
Want to see something wild?
The chart of Okta's stock price from its IPO in 2017 through today follows almost exactly the same arc:
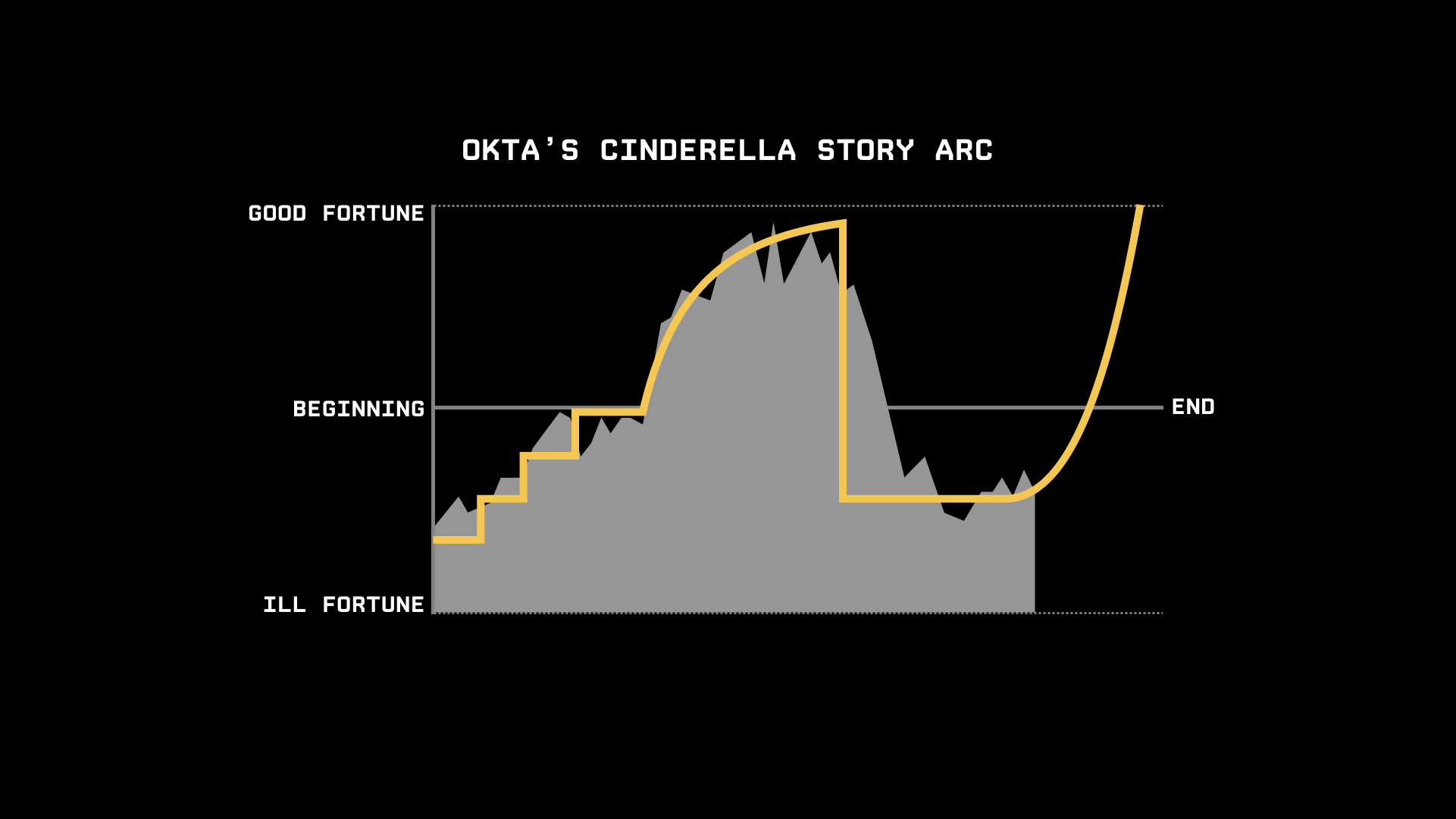
I kid you not. It's uncanny.
The comparison is a metaphor, of course — but Okta's narrative fits the story arc in a remarkable way.
From ill-fortune to cybersecurity's debutante ball
Okta couldn't have been started under worse circumstances.
In 2008, Todd McKinnon was a mid-30s, up-and-coming exec at Salesforce with a baby daughter and recent Type 1 diabetes diagnoses. The economy was in a free fall.
Financial stability, family, and health were all working against him. He was barely able to convince his wife it was a good idea to start a company.
The company started out as Saasure, a network monitoring product. It didn't get traction. The founders quickly pivoted to cloud identity management and changed the name to Okta.
Okta's cloud access management product steadily grew beyond everyone's wildest expectations. The fairy godmothers at Andreessen Horowitz and Sequoia bestowed a total of $228 million in venture capital upon the company. Okta went public in 2017 at a $1.5 billion valuation.
As a public company, Okta continually produced steady increases in growth and valuation, peaking at an enterprise value of $41.29 billion in September 2021. It was one of the most valuable cybersecurity companies in the world.
That's the quick version of how Okta went from an ill-fated beginning to become one of the darlings of the cybersecurity debutante ball.
The story really starts to get interesting when the clock strikes midnight.
When the clock strikes midnight
Everything changed on March 22, 2022, when LAPSUS$ publicly disclosed it breached Okta through a third-party service provider.
The magic spell wore off. Their Teslas turned into pumpkins, Cotopaxi into rags. A glass Allbirds slipper was the only trace left behind.
The protagonist in Okta's real-life story is Todd McKinnon. He's not exactly in rags, but you'll never find a picture of a more exhausted CEO than this one — taken from an interview at a software industry conference the day after a breach:

We've all heard about the direct and indirect security incidents and PR debacles since then: source code breaches, Rightway Healthcare, Oktapus, MGM, support case management…okay, make it stop.
Right now, it feels like anything Okta does right gets overshadowed by something that's gone wrong.
Why? We're watching Okta's "clock strikes midnight" moment play out in real time.
They were just on top of the cybersecurity world, and now they're not. It's jarring. We're all on the edge of our seats, unsure of how the story is going to end.
What we're thinking and experiencing now is exactly how the arc of a Cinderella story goes. Something horrific happens. Things look dire. Nobody knows if the hero can recover this time.
Here's what happens after the princess vanishes from the ball and her glass slipper gets left behind.
The next Cinderella?
In the movie Cinderella, the prince launches a massive quest to find her after she disappears. Everyone in town tries on the glass slipper to see if it fits. People like the stepsisters pull all kinds of nefarious stunts to jam their foot into the slipper.
This iconic scene is…actually not so different from the time since Okta's clock struck midnight.
There's an important lesson about competition here: when given the chance, a lot of people want to make the glass slipper fit and steal the throne.
Some competitors piled on with "this wouldn't have happened if…" and all kinds of questionable tactics to make Okta look bad and get customers to switch. It's unfortunate, but they probably deserved it.
Could Okta have done a better job with security? Of course.
Did their mistakes put thousands of customers at risk? Absolutely.
Was their initial PR and incident management lacking? #%@& yes it was.
But not all security incidents are the same. Incidents happen all the time. They can also happen to anyone — even security companies. The "why" and "how" matter. Savvy security leaders know that.
Here's the reality: the glass slipper isn't going to fit for most other identity companies.
A founder-led decacorn in its prime is not going to disappear overnight. Okta has used up a lot of karma points, but the collective damage from these incidents is far from the worst we've seen as an industry.
On a practical basis, it's not easy or fiscally responsible for most customers to rip out an identity platform like Okta once it's implemented. Identity platforms are incredibly sticky, especially when they're integrated with most of an organization's apps.
For a large enterprise, "not easy" means years spent migrating the integrations for hundreds or thousands of applications to the new identity platform. "Not fiscally responsible" means millions or tens of millions in capital expenses, including a big chunk for professional services.
Security leaders are disappointed and annoyed about this repeated string of incidents involving Okta. But frustration is not enough for most of them to cut ties and move on — especially when security budgets are getting tight and dollars are better spent other ways.
Sure, they'll throw a fit and ask for discounts. They'll renew their contracts for shorter periods of time. All kinds of political stunts can happen, but very little of the noise is translating to actual customer churn.
Let's talk about why a few insightful financial metrics mean the glass slipper still fits.
The glass slipper still fits
The evidence doesn't support mass defection of customers or the major implosion some people still believe is imminent.
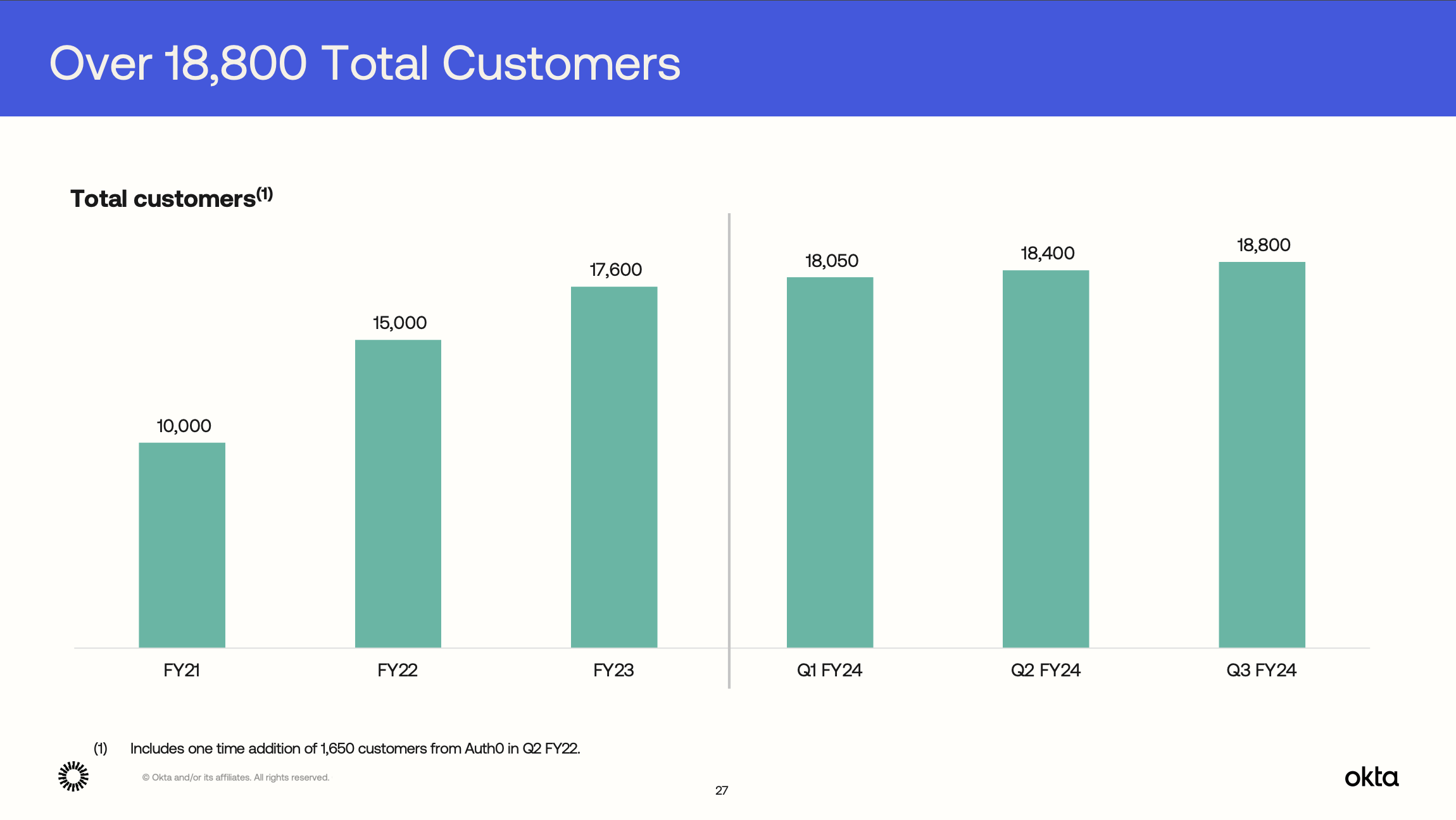
How do we know customers aren't churning? Okta reports customer data in their quarterly earnings reports.
Their literal count of customers² isn't dropping:
Nor are the big, $100k+ accounts people were saying would leave:
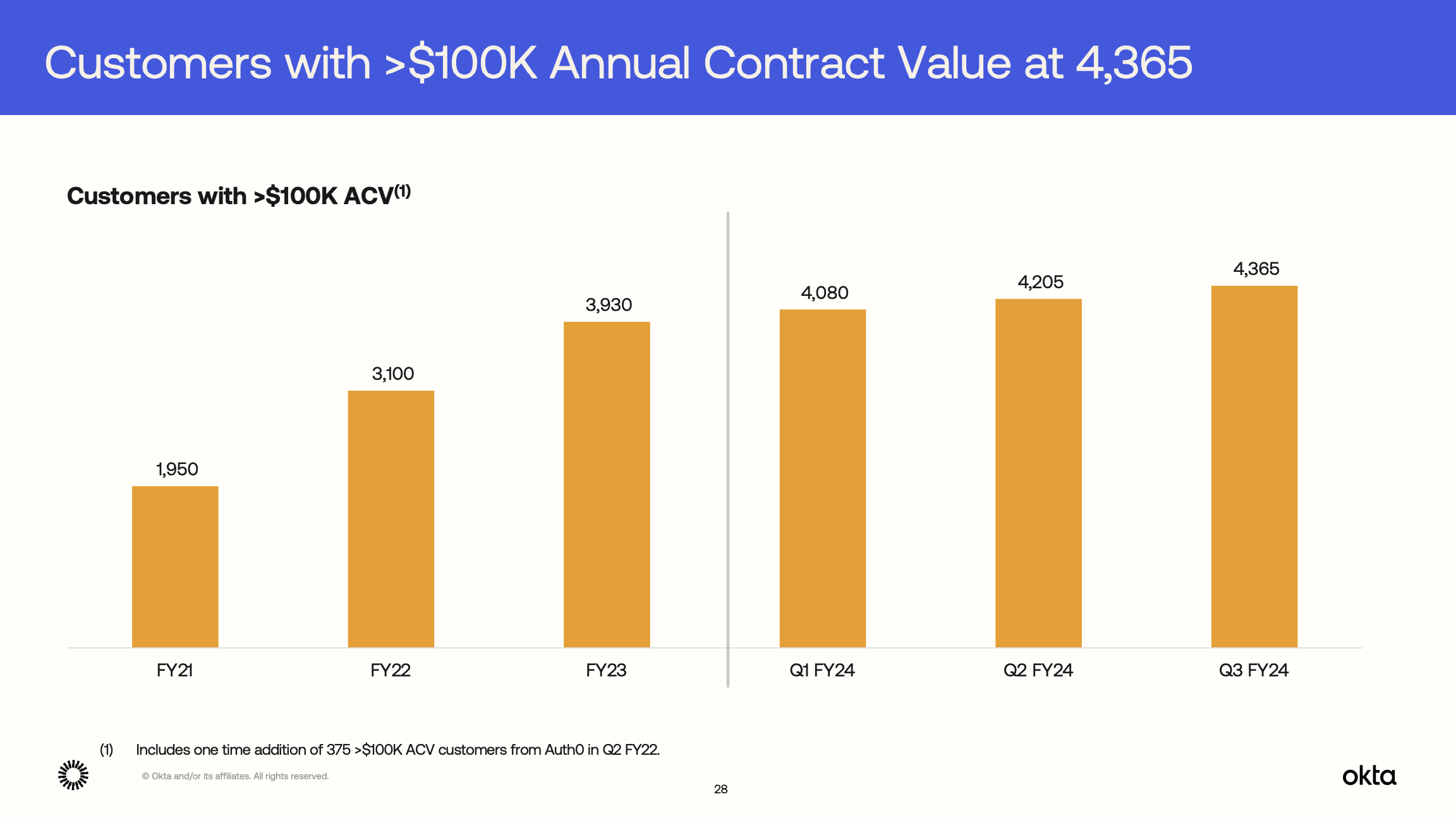
Okta's customers are not running for the hills. In fact, they have 435 more $100k+ customers since the first breach.
Revenue isn't crashing, either. Their revenue has grown 25.26% year-over-year.³ The CAGR from FY21 (before the first breach) through the end of FY24 is 39%:
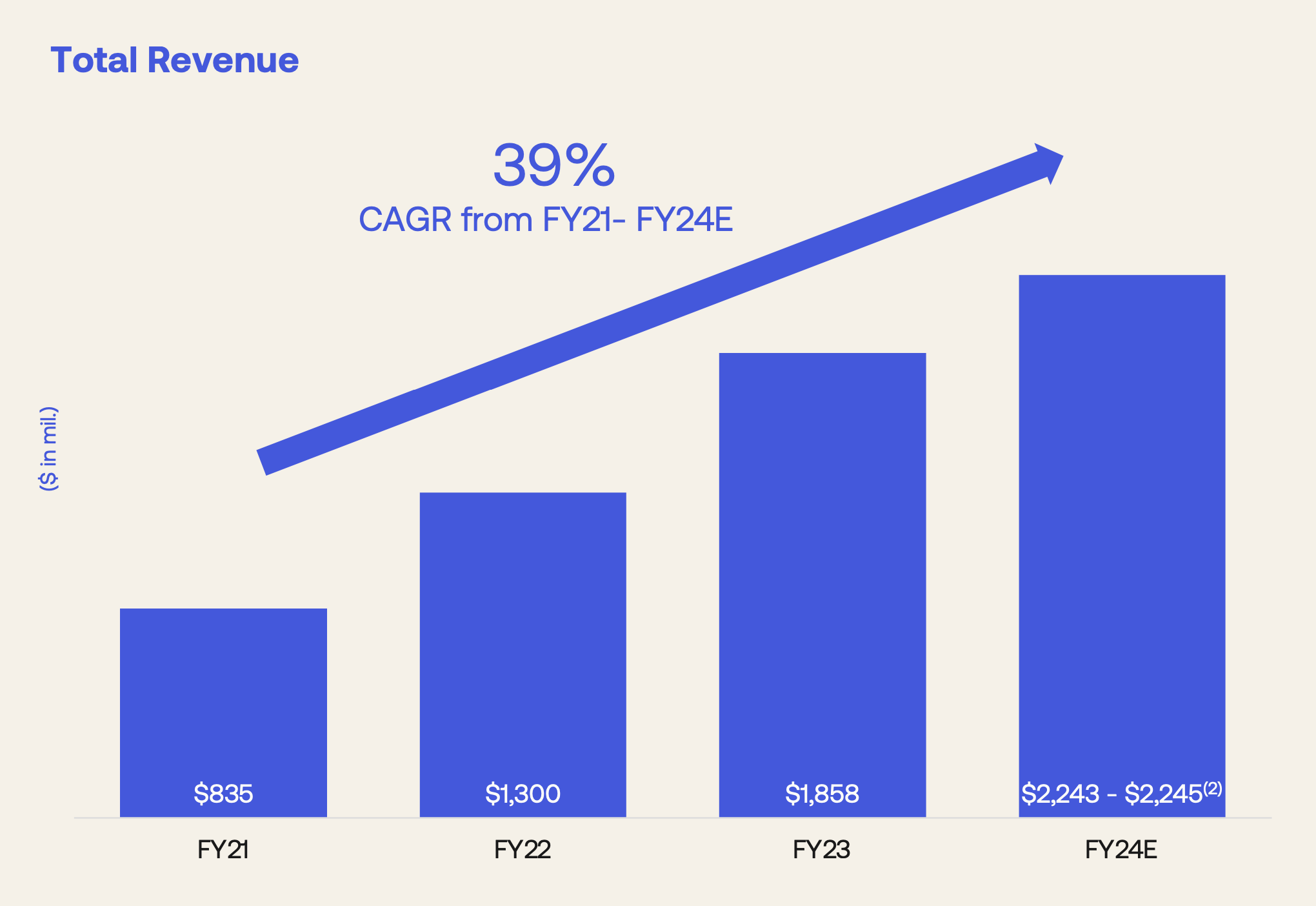
By the way, they're more profitable than ever now — scheduled to clock in at a 12% (non-GAAP) operating margin at the end of this fiscal year.
They're also still a leader in the 2023 Gartner Magic Quadrant for Access Management for, oh…just the seventh straight time. They're not the clear leader this time around — mainly because of Microsoft's investments in identity and Thoma Bravo's rejuvenation of Ping and ForgeRock, not Okta's series of unfortunate events.
Growing this fast as a ~$2 billion company under any circumstances is incredibly difficult. Okta has done it in the face of a bad macroeconomic environment and a level of noise and scrutiny no cybersecurity company other than SolarWinds has ever faced.
Analyst ratings and financial metrics aren't an adequate measure for the pain and frustration Okta's customers and security practitioners feel because of the security incidents. But, they're correlated.
If customers were dumping Okta to buy other identity products, rankings, revenue, and retention metrics would be tanking by now. None of them have.
I know things still seem dire right now, but Okta's story can have a happy ending. It won't be easy, but it's possible — just like all good Cinderella stories.
Okta's story can still have a happy ending
At this point, a happy ending for Okta is definitely not destiny. It's still possible if they do all the right things.
The biggest concern CISOs and investors both have is: Are there going to be more security incidents?
Maybe. The "O" in Okta might as well be a giant bullseye for attackers right now. The fairy godmother isn't going to rescue them. It's going to take massive effort to change the narrative.
There's an Icarus story arc, too. It's a moral lesson about the dangers of hubris and overambition.
A kid escapes capture by building wings made of wax, gets overconfident and flies too close to the sun, then drowns after the wings melt.
What Is Okta doing to make sure their story has a happy ending? A few things.
They need to handle any incidents they do have perfectly. They're out of karma. CISOs are going to move from mild frustration to mutiny if Okta can't figure this out fast, so they've been working on it.
Then, go on offense: make security a clear priority and address the high-impact issues. This is exactly what Project Bedrock (the internal project name) is about. 90 days of focus isn't going to fix everything, but it's a nice start.
Right now, Okta doesn't need more products. It needs more security.
If Okta can fix its security, both in reality and perception, they're going to be fine.
Fixing security is fixing growth.
The noise will fade. The spotlight will turn elsewhere. Customers will notice the progress.
Keeping the madness at bay is the best growth strategy for Okta right now.
Why? Okta has plentyyyyyyy of products with growth potential in the pipeline. Its Identity Governance and Privileged Access Management (PAM) products have both hit General Availability (GA). Early momentum is promising — especially in a world where three of their biggest competitors were taken private and other legacy products fade into the oblivion of data centers gone by.
The stakes couldn't be higher. If Okta lives up to its Cinderella story, they're cemented on the Mount Rushmore of winners in the identity market.
Ironically, it's security that will dictate Okta's future: will it be a tale of Icarus's fall or Cinderella's fortune?
Footnotes
¹Seriously, you should watch Vonnegut's lecture. It's pithy. Totally hilarious. I promise it will be the best four minutes of your day.
²The count of total customers can get a bit muddled because of how Auth0's product-led growth (PLG) model works. Without knowing the breakdown, you could speculate Okta's core workforce platform is churning, but Auth0 nets it out by adding super tiny customers to the total count. It's possible, but this scenario seems unlikely because of Okta's strong $100k+ account growth and Net Revenue Retention (NRR) metrics post-breach.
³On a TTM basis as of Okta's Q3 FY24 earnings report. Put differently, they're still growing a lot — long after the first breach was disclosed.
*** This is a Security Bloggers Network syndicated blog from Strategy of Security authored by Cole Grolmus. Read the original post at: https://strategyofsecurity.com/oktas-cinderella-story/
如有侵权请联系:admin#unsafe.sh