2023-12-15 22:0:54 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Every company wants to have a good security posture, and most are investing in security tooling. According to Gartner, worldwide spending on security is forecast to grow 11.3% in 2023 to reach more than $188.3 billion. However, despite all this spending, there are certain areas where problems are only getting worse, such as secrets sprawl. Reports now say over 50% of cyberattackers gained their initial foothold by exploiting compromised credentials. No organization wants to go through an indecent like Samsung or Nvidia or repeat Uber’s unfortunate experience.
So what can we do? First, we must admit that secrets management tools alone cannot save the day.
A Good Lock Alone is no Guarantee of Security
An intricate deadbolt on your front door serves little purpose if the door is carelessly left ajar. Even the sturdiest lock is ineffective if someone neglects to lock it or leaves the key lying around.
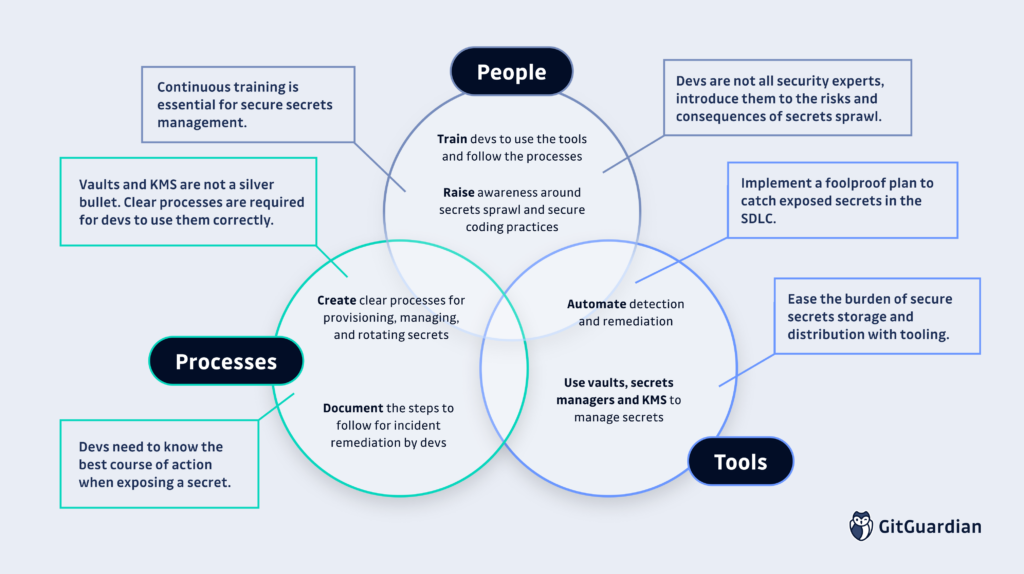
Good secrets management requires three fundamental pillars:
People – Kept aware of the issues and properly trained on the tooling and processes.
Processes – Clear documented procedures for creating, storing, accessing and rotating secrets.
Tools – Credentials storage and management, as well as detection and leak remediation.
People Need Training to Use Tools and Fix Issues
Each security challenge involves a human dimension. If your team lacks awareness regarding the specific security issues being addressed and how to leverage the security tools available, then it is unlikely your security posture will improve.
There are two major components to keep in mind when thinking about education:
Awareness – Explain the issue, what risks it brings, and what can be done to address it.
Training – How to use the specific tools that are available to solve the issue.
These components are the “why” and the “how” which are both needed for success. If you explain the problem but present no solutions, all you do is make people anxious. If you only list a set of ‘how-tos’ for any tool without explaining the larger context, you will not likely get the tool used at the right time or at all. It is critical to get everyone on the same page, especially across team boundaries throughout your organization.
Raising awareness across all teams is at the heart of many security champion programs. OWASP has published a free Security Champion Playbook that can get you started. and we would also recommend checking out Snyk’s Security Champions guide. You can hear more about security champions from Tanya Janca on The Security Repo podcast.
Consistent Processes Make for Consistent Results
Achieving better security relies on the establishment and communication of good procedures. No matter the task, there likely is a recommended and secure method to accomplish it that everyone should follow..
Using a whiteboard to create flowcharts can be a great way to think through processes. If you turn these charts into Kanban or flow diagrams, they can be an excellent basis for written procedures. No matter how you create or think of your processes, they are only good if you effectively communicate them, meaning good documentation and training.
Consistency is Vital For any Tool
Of course, you need tools to get the job done, but tools require proper and consistent usage for reliable results. For example, secrets managers are the bedrock of secrets management strategies. Technologies such as Vault by HashiCorp or Doppler or platform-based vault systems like Azure Key Vault or AWS Secrets Manager bring extensive benefits. Those benefits only become available when an org uses them consistently. Developers who implemented their own separate secrets managers, away from the security team’s oversight, or who rely entirely on `.env` files are inviting issues.
Just as important as storage is secrets detection. The act of running a scan alone does not do much. Executing an action plan once an incident is identified is vital. Having a spreadsheet of results you will get around to dealing with someday means you will not likely put a stop to this issue.
Tools, People and Processes Determine Your Security Posture
Achieving a good security posture extends beyond the acquisition of tools alone.
While secrets sprawl remains a persistent challenge, the good news is that with a holistic approach, we can all get there. Good security thrives on three core pillars: People, processes and tools. These components work in concert to fortify an organization’s security posture.
Source: secrets–kristina-flour-BcjdbyKWquw-unsplash
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
