2023-12-12 20:30:14 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Yamaha Motor Philippines Inc. (YMPI), a wholly owned subsidiary of Yamaha Motor Co., Ltd., a global leader in the manufacturing of motorcycles, marine products, power products, and others fell victim to a ransomware in mid-November 2023, and the threat actor involved published the exfiltrated data on a Darkweb forum.
Table of Contents
The Perpetrator
A Ransomware group named INC Ransom claimed to have attacked Yamaha Motor Philippines Inc on 15 Nov 2023. The ransomware attack encrypted all their data and vital systems before demanding a ransom payout in exchange for the decryption key.
Who is INC Ransom?
INC Ransom is a Ransomware group which has been active since Aug 2023. They claimed to have attacked 30+ organizations of which, Yamaha Motor Philippines is also one of them. The extent of this attack has reached the depths of a dark web forum where the breached information can easily be sought after. The breached information contains essential employee data, IPs and internal email, and customer information
Dissecting the cyber kill chain:
According to Bleeping Computer, INC Ransom gained access to their target networks via spear phishing (A technique of sending targeted deceptive emails to specific individuals within an organization), and as per SentinelOne, they have also been observed using Citrix NetScaler that is known to have pre-existing vulnerabilities and exploits namely – cve-2023-3519 exploits.
After gaining access to the network, the group traverses laterally to identify, harvest, and download the sensitive information including the backups. At this point, the group deploys the ransomware payload to encrypt and compromise systems and information.
Analysis of the group‘s Darkweb forum:

Fig-1: A snapshot of the groups’ Darkweb presence – A space where the group publishes updates, breached data, and a list of ransomware victims as a trophy shelf for everyone to see.

Fig-2: A Means of Communication with the group to provide feedback and engage in negotiations and data deletion.

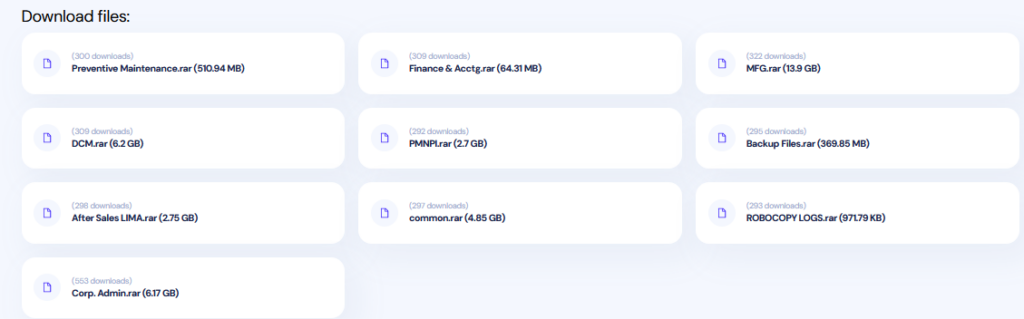
Fig:3 – A brief of the victim on INC Ransom

Fig:4
In Figure 3 and Figure 4, the group has published a treasure trove of information on their latest victim, Yamaha Motors. This 37 GB + size of vital information is currently publicly available for download on their site.
Who are their victims? According to our analysis, the primary target appears to be Manufacturers based out of the US, followed by the Netherlands and Australia. A common trend is that all their victims are medium to large enterprises with an IT-OT ecosystem.

Fig:5 – This chart shows the key target countries that INC Ransom has attacked in their past attacks

Fig:6 – This chart shows the most targeted industries by INC Ransom
What’s next for Yamaha Motors, Philippines?
Yamaha Motors, Philippines has no end in sight for their upcoming woes. Here are a few reasons why their current problems are expected to be only the beginning of a series of unfortunate events:
- A vital information set of 37 GB is publicly up for grabs. This treasure trove of information contains information about its networks, critical mail communications, credentials, and much more. This alone is a motivating factor for many budding threat actors to initiate subsequent breaches and network access attempts.
- Increased Attack surface: While the information breach is of vital importance, this attack on Yamaha motors still lingers with its current supply chain and could only be a matter of days or weeks until a second wave of attacks emerges from dormant and stealthy malwares hidden in their networks and supply chain. Remedial actions and further sanitization of their network and impacted system are crucial.
A teardown of the INC Ransomware Attack
As per Team Huntress, the APT (Advanced Persistent Threat) group INC starts with the initial access with reconnaissance and credential compromise, followed by lateral movement, data collection, and malware payload execution.
Here is a breakdown on INC Ransom’s attack pattern:

Fig:7 An image indicating a 7-day playbook that INC Ransom commonly follows to compromise the targeted victim’s
Indicator of compromise (IOC)
- Ransomware Executable PDB string: C:\source\INC Encryptor\Release\INC Encryptor.pdb
- Ransom Note file name: *.inc-readme.txt, *.inc-readme.html
- Encrypted File Extension: *.inc
- Use of native tools (net.exe, nltest.exe, WordPad/Notepad/MS Paint, Internet Explorer, Windows Explorer, mstsc.exe, msdt.exe)
- Use of additional tools (7-Zip, MEGA Sync, Advanced IP Scanner, Putty, lsassy.py, PS Exec)
TTPs (Tactics, Techniques, and Procedures)
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Credential Access
- Discovery – Domain Trust Discovery
- Lateral Movement – Remote Services
- Collection – Archive Collected Data
- Impact – Data Encrypted for Impact
Mitigation and Remediation
- Regular Backups
- Conduct regular security training and awareness sessions for employees.
- Update and Patch Systems.
- Implementation of Advanced Endpoint detection and Response solutions.
- Proper Network Segmentation
- Email Security Solutions
- Incident Response Plan
- Risk Assessment and Gap Analysis
References
- https://www.bleepingcomputer.com/news/security/yamaha-motor-confirms-ransomware-attack-on-philippines-subsidiary/
- https://www.huntress.com/blog/investigating-new-inc-ransom-group-activity
- https://global.yamaha-motor.com/news/2023/1116/corporate.html
*** This is a Security Bloggers Network syndicated blog from Sectrio authored by Sectrio. Read the original post at: https://sectrio.com/inc-ransom-breaches-yamaha/
如有侵权请联系:admin#unsafe.sh