2023-12-7 15:8:52 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
While building products and launching ten many things, security takes a back seat, especially for bootstrap startups where everyone is running multiple projects. The ROI of penetration testing cannot be calculated directly, it can be calculated based on terms of cost of a data breach. Startup leaders may ease up on security measures due to high budget constraints, but they also forgo the fact that not taking enough security and compliance measures also makes them the target of cybercriminals who are waiting to take out on any possible chance to enter into your system. Almost 41% of all data breaches happen to organizations with <1000 employees.
What Does Penetration Testing Mean for Startups and Small Businesses?
Identification of Vulnerabilities:
Penetration testing serves as a proactive approach to identify vulnerabilities within the digital infrastructure of startups and small businesses. This involves simulated cyber-attacks conducted by ethical hackers to pinpoint weaknesses in systems, networks, and applications. By systematically probing for vulnerabilities, penetration testing reveals potential entry points that could be exploited by malicious actors.
Risk Mitigation:
Understanding and mitigating potential risks is a core objective of penetration testing. By actively assessing and identifying vulnerabilities, startups can take strategic measures to address and remediate weaknesses before they can be exploited. This risk mitigation strategy not only protects sensitive data and critical systems but also helps prevent potential financial losses and reputational damage associated with security breaches.
Compliance Assurance:
Adherence to industry regulations and standards such as ISO, SOC2, PCI DSS is important. Penetration testing is often mandated by regulatory frameworks, making it a crucial component for startups and small businesses aiming for compliance. By undergoing penetration testing, organizations can demonstrate their commitment to meeting industry-specific security requirements, thereby avoiding legal repercussions and ensuring a secure operational environment.
Protecting Customer Trust:
Customer trust is invaluable, especially in an era where data breaches are increasingly common. Regular penetration testing signifies a commitment to safeguarding customer information. By investing in proactive security measures, startups can enhance customer trust, reassuring clients that their sensitive information is being handled with the utmost care. This, in turn, contributes to the long-term reputation and success of the business.
Challenges Small Businesses Face with Penetration Testing
As startups grapple with financial constraints, limited in-house IT expertise, and the intricate mesh of diverse technologies, the deployment of robust security measures becomes a delicate balancing act.
Budget Blues
Small businesses often face a wallet squeeze when it comes to allocating funds for penetration testing. Limited financial resources can make it a bit tricky to invest in robust security assessments.
Staffing Snags
Picture this – a small business with a handful of employees wearing multiple hats. Now, throw in the lack of dedicated IT and security personnel into the mix. It’s like trying to juggle a dozen tasks without enough hands, making it tough to manage and tackle security vulnerabilities head-on.
Integration Issues
Integrating penetration testing into existing business processes can be challenging. Small businesses may struggle to seamlessly incorporate testing into their development lifecycle or ongoing operations, leading to potential gaps in security coverage.
Prioritization of Security
Balancing the day-to-day operational needs with long-term security priorities can be a struggle for small businesses. Some may prioritize immediate business goals over-investing in security measures, underestimating the potential long-term impact of a security breach.
When should a startup get penetration testing done?
The timing for when startups should conduct penetration testing can vary based on factors such as the nature of the business, the industry it operates in, and its overall risk profile. However, here are some general guidelines for different stages of a startup:
1. Pre-Launch or Early Stage:
Scenario: The startup is in its early development stages or has not yet launched.
Consideration: While the product is being developed, it’s advisable to conduct security assessments and basic testing to identify and address any glaring vulnerabilities before launch.
2. Post-Launch (Initial Traction):
Scenario: The startup has launched its product or service and gained some initial traction.
Consideration: As the startup begins to handle customer data and transactions, it’s a good time to conduct a comprehensive penetration test to ensure that security measures are in place and effective.
3. Rapid Growth Phase:
Scenario: The startup experiences rapid growth, attracting more users and attention.
Consideration: With increased visibility comes an increased risk of cyber threats. It’s prudent to conduct regular penetration testing during this phase to identify and address vulnerabilities promptly.
4. Fundraising Rounds:
Scenario: The startup is seeking funding through various rounds.
Consideration: Investors often scrutinize a startup’s security posture. Conducting penetration testing before fundraising rounds can help demonstrate a commitment to cybersecurity, potentially instilling confidence in investors.
5. Integration of New Technologies or Features:
Scenario: The startup is integrating new technologies, features, or third-party services.
Consideration: Whenever significant changes are made to the infrastructure or applications, it’s essential to conduct penetration testing to identify and mitigate potential security risks introduced by these changes.
6. Compliance Requirements:
Scenario: The startup operates in an industry with specific compliance requirements.
Consideration: Compliance standards may mandate regular security assessments, including penetration testing. Startups should align their testing schedule with these requirements.
7. High-Risk Periods:
Scenario: The startup is entering a high-risk period, such as launching a new product or entering a new market.
Consideration: Whenever there is an elevated risk due to significant business activities, conducting penetration testing can help ensure that the startup’s security posture is robust.
8. Continuous Testing:
Consideration: While the specific stages mentioned above highlight key points, it’s important to view penetration testing as an ongoing process. Regular testing, ideally integrated into the development lifecycle, helps maintain a proactive and resilient security posture.
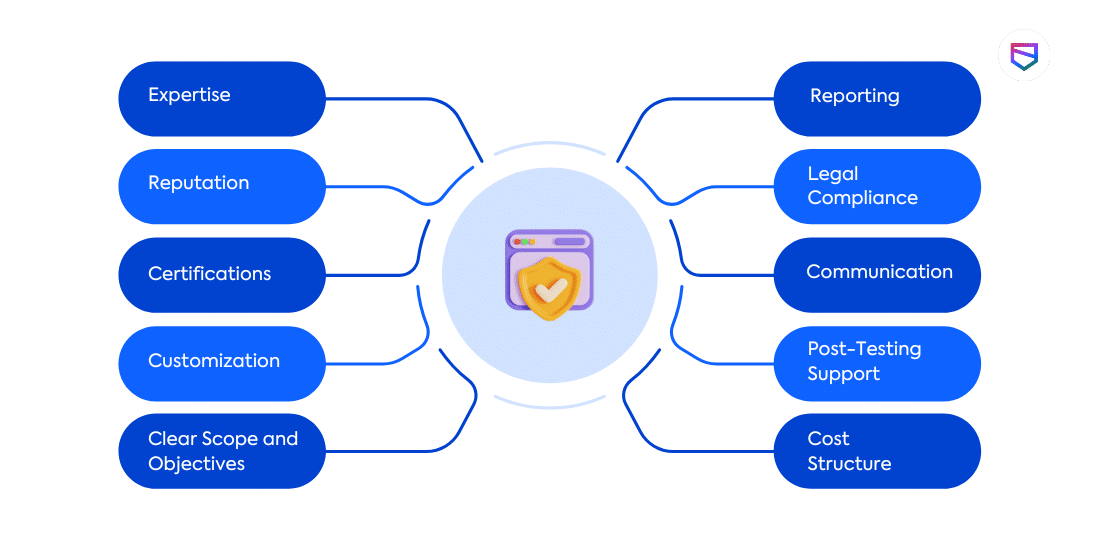
Things to Consider Before Finalizing a Penetration Testing Vendor:
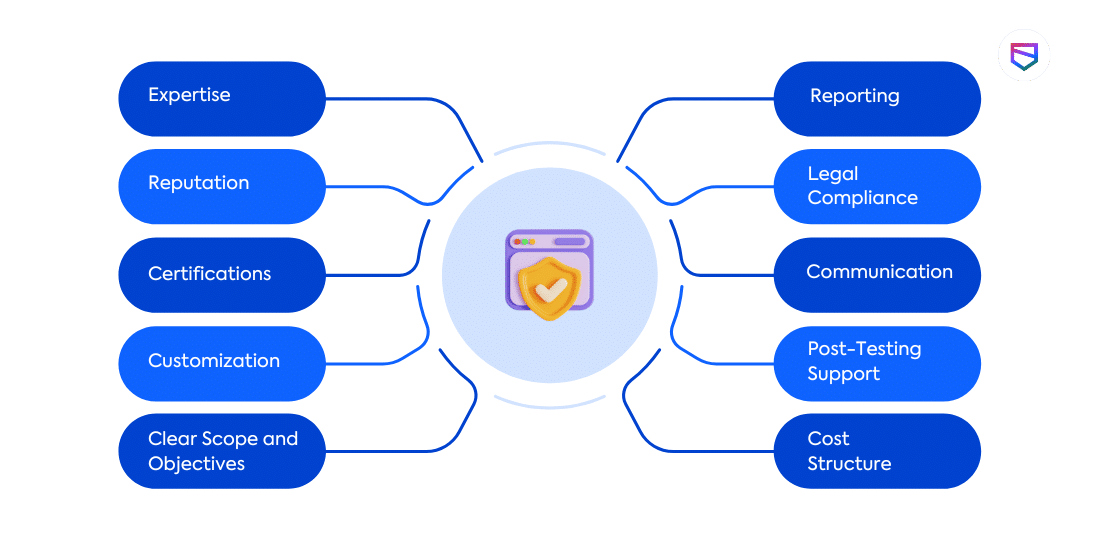
Expertise:
Ensure the vendor has expertise in testing the specific technologies and systems relevant to your business.
Reputation:
Check the vendor’s reputation by reviewing testimonials, case studies, and customer references.
Certifications:
Verify that the testing team holds relevant certifications (e.g., Certified Ethical Hacker, Offensive Security Certified Professional).
Customization:
Seek a vendor who can tailor testing methodologies to the unique needs and challenges of your business.
Clear Scope and Objectives:
Clearly define the scope and objectives of the penetration test, ensuring alignment with your business goals.
Reporting:
Review sample reports to ensure they are comprehensive, easy to understand, and include actionable recommendations.
Legal Compliance:
Ensure the vendor follows ethical and legal standards, obtaining written permission and adhering to relevant regulations.
Communication:
Evaluate the vendor’s communication skills and responsiveness to ensure a smooth testing process.
Post-Testing Support:
Inquire about post-testing support, such as assistance with remediation and addressing identified vulnerabilities.
Cost Structure:
Clearly understand the vendor’s pricing model and ensure it aligns with your budget constraints.
Empowering Startups with WeSecureApp Continuous Penetration Testing
At WeSecureApp our commitment extends beyond mere identification; we collaborate with startups to mitigate potential risks, providing strategic insights to bolster their security posture. WeSecureApp ensures that your business not only meets but exceeds industry standards through penetration testing, safeguarding against legal ramifications, and reinforcing trust with stakeholders.
WeSecureApp’s Comprehensive Penetration Testing Services for Startups Include:
- Source Code Reviews
- API Penetration Testing (REST, GraphQL, and SOAP APIs)
- Mobile App Pentesting (iOS and Android)
- External and Internal Network Pentest
- AWS & Azure Cloud Penetration Test
- Cloud Configuration Security Review
- SaaS/Web Application Security Testing
- Threat Simulation
- Spear-Phishing Exercises
What sets WeSecureApp apart is our tailored approach. Recognizing the unique challenges faced by startups, we customize our penetration testing services to align with their specific needs, budgets, and growth trajectories. By fostering a proactive culture of security, WeSecureApp assists startups in protecting sensitive data and fortifying their digital fortresses against malicious actors. Retesting, if needed, is free of cost within 90 days of the final report. Our reports align with various compliance standards, including SOC 2, GDPR, PCI DSS, HIPAA, ISO 27001, and others, supporting your vendor risk assessments and compliance audits.
Schedule Your Comprehensive Penetration Test for Actionable Security Results – Contact Us
Recommended Reading
Choose the Right VAPT Services Provider
How to Choose a Penetration Testing Vendor Wisely?
The post Penetration Testing for Startups and Small Businesses appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by WeSecureApp. Read the original post at: https://wesecureapp.com/blog/penetration-testing-for-startups-and-small-businesses/
如有侵权请联系:admin#unsafe.sh