When discussing authentication security, Multi-Factor Authentication (MFA) has been widely touted a 2023-12-5 21:51:36 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
When discussing authentication security, Multi-Factor Authentication (MFA) has been widely touted as a linchpin for securing digital assets. However, as recent trends and reports suggest, MFA, while significant, is not the panacea it’s often perceived to be. Drawing from extensive research and industry reports, we will dissect the myths surrounding MFA and shed light on building a robust authentication framework that stands resilient in the face of targeted attacks.
Understanding MFA’s Role in Cybersecurity
MFA demands two or more verification factors for accessing a resource, which include a password (something you know), a hardware token or mobile device (something you have), or biometric verification (something you are). While this approach marks a leap in authentication methods, it’s critical to scrutinize its efficacy and limitations.
Reports like Verizon’s DBIR and IBM’s Cost of a Data Breach reveal a startling trend: MFA, although advanced, is not invincible. The persistence of compromised credentials as a primary entry vector for data breaches is a testament to this vulnerability. It’s akin to having a state-of-the-art security system in a house but leaving the door unlocked. When one factor, like a password, is weak, MFA’s defense is considerably diminished.
The Illusion of Impenetrability
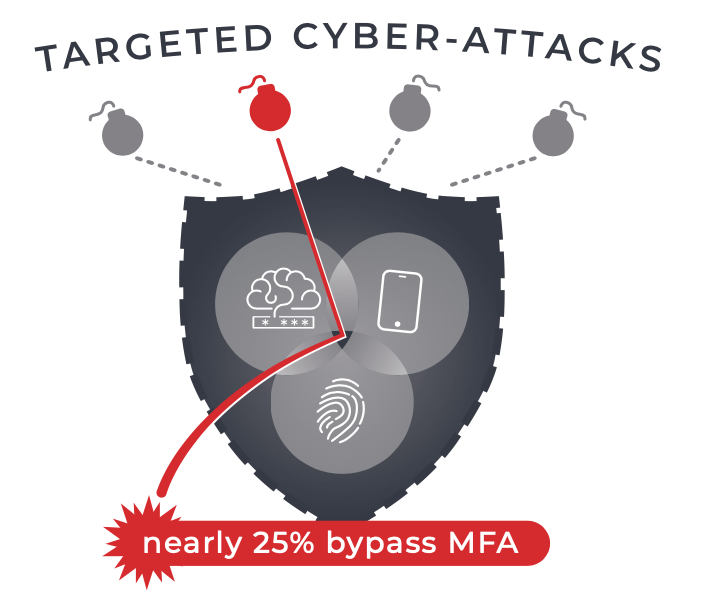
Microsoft’s 2023 Digital Defense Report initially suggests that MFA is highly effective, blocking 100% of automated bot attacks and 96% of bulk phishing attempts. Yet, its success rate drops to 76% against targeted attacks, indicating that MFA isn’t impervious. This gap in security is further highlighted by Google’s finding that account compromises decrease by only 50% even with two-step verification.
MFA’s vulnerabilities are manifold, encompassing traditional hacking methods like SIM jacking, SIM swapping, and Man-in-the-Middle attacks. These strategies allow unauthorized access to sensitive information by exploiting telecom network protocols or intercepting communications.
Advanced tools such as reverse proxy Muraena and ‘headless’ web-browser NecroBrowser have simplified launching MitM attacks, widening the threat spectrum. Additionally, leniencies in authentication based on time or location can inadvertently provide extended access to attackers, highlighting the need for consistent and robust application of MFA.
An overdependence on MFA can lead organizations to neglect other essential security protocols, particularly around credential security. In certain operational contexts, MFA application might be challenging or even impractical, thus limiting its effectiveness. The critical takeaway is that while MFA adds layers of verification, it cannot replace the need for securing credentials directly.
Strength in Every Factor
To maximize MFA’s efficacy, organizations must secure each factor comprehensively. This includes actively monitoring and updating compromised credentials. Regularly cross-checking databases with against an updated list of compromised credentials can significantly reduce unauthorized access risks. Moreover, considering the frequency of data breaches and ransomware attacks, securing every individual factor within MFA is paramount.
MFA should be seen as a crucial component within a broader security strategy, not a standalone solution. Its integration with other security measures is vital for expanding an organization’s defense against targeted threats. The true strength of MFA lies in its synergy with a holistic security approach.
Key Takeaways
The cybersecurity landscape is a complex and dynamic arena where no single solution offers absolute protection. MFA, while a valuable tool in the cybersecurity toolkit, is not immune to weaknesses. Understanding its limitations and integrating it with other robust security measures is crucial for building a truly resilient defense mechanism. Organizations must constantly re-evaluate and reinforce their cybersecurity strategies, ensuring that every aspect, including MFA, is as strong as the overall security posture. Only then can we hope to stay a step ahead of attackers and stay safe from data breaches, account takeover, and privilege escalation.
Read the “MFA Misconceptions” white paper.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Marketing Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.
The post Debunking MFA Myths: How to Stay Secure appeared first on Enzoic.
*** This is a Security Bloggers Network syndicated blog from Blog | Enzoic authored by Josh Parsons. Read the original post at: https://www.enzoic.com/blog/debunking-mfa-myths/
如有侵权请联系:admin#unsafe.sh