2023-12-5 12:0:56 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
You may be familiar with the common phishing tactics like fake emails or text messages from a hacker pretending to be someone at your place of work, or maybe it’s someone pretending to be from your bank or credit card company. The latest scam we’ve uncovered now highlights another widespread service used by almost everyone: the postal service. Perhaps it’s not a coincidence that the uptick comes as we turn the corner into the holiday season, emphasized with an increase of ordering and sending packages or items in the mail.
The parcel delivery scam, a phishing campaign initially targeting less tech-savvy individuals with messages about “failed deliveries” or late payments, has significantly evolved since first discovered. As awareness grows, scammers are refining their tactics, shifting from simple misleading messages to more sophisticated methods, like tricking victims to download malicious apps designed to steal banking information.
Bolsters’s Research Team has uncovered a new dimension in these scams. We’ve detected a domain impersonating Walmart, cleverly designed to mimic the appearance of the USPS.com website.
A key feature of this phishing site is its ability to access and integrate IP location data into its delivery tracking process, enhancing its perceived authenticity. The site also employs a geo-fencing technique to avoid detection.
The threat actors have gone beyond just creating typosquat domains. They are exploiting various free hosting services to run these deceptive websites, aiming to maximize their profits through this abuse of freemium dynamic DNS and SaaS providers.
The implication of this new attack avenue
Scammers are using advanced and innovative tactics, making it more challenging to differentiate genuine services from scams. This can mean even tech-savy or cyber-aware consumers might have trouble spotting a scam, and hackers can go unnoticed for longer periods of time.
Increased vigilance and awareness are essential. As we enter another cyber-focused holiday season, cyber criminals are hyper aware that more consumers are looking to spend money online, which includes entering credit card information, scoping out the best deal, and getting all their shopping done fast.
The holiday shopping environment provides a prime setting for hackers pretending to be USPS, due to the higher volume of shipping needs during November and December, making it ever more critical for consumers to be wary of suspicious links and mail scams.
Analysis of the Phishing Campaign
So far, we’ve identified Walmart as the main vein for hackers to mimic as part of this scam attack. There’s no telling if the attackers will use additional brands in the future as attack avenues for this parcel scam.
While writing this blog, the domain walmarts[.]co was active and mimicked Walmart’s domain name, but was predominantly serving content related to USPS delivery tracking. Strategically, it redirects to the genuine USPS portal to evade detection mechanisms.

From our analysis of data spanning the past month, CheckPhish detected more than 3,000 related phishing domains, and most of them utilizing major two phishing-kits, as evident from their shared functional designs.
Specifications of Phishing Sites
By examining a majority of the phishing sites we have found few similarities across the phishing sites:
- All of the phishing websites contain a site title such as USPS.com® – USPS Tracking® Results
- Most of the phishing domains are actively stealing sensitive information like email address, name, phone number, residential address, and credit/debit card information.
- The majority of the hyperlinks present in the phishing pages redirect to legitimate USPS websites, unlike other impersonated websites.
- Few phishing domains redirect to the legitimate USPS site based on the IP location, which is a popular technique to evade detection.
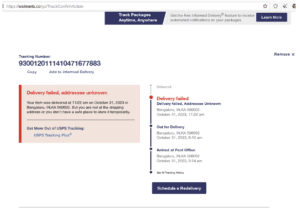
- Another group of phishing sites show the tracking details based on the victim’s IP locations which makes it more authentic to a victim.
- Threat actors are not limited to hosting these phishing sites on a pushed domain, but they have abused the free hosting services.
- Further analysis reveals that while the phishing sites primarily target customers based in the US, they do possess the capability to target customers globally as well.
The method behind these attacks
Modus operandi for this phishing campaign remains the same, where the threat actors utilize SMS or email to distribute phishing links, as seen in the example images below. With the stolen data they gain access to through the scam, hackers could potentially lure victims further using social engineering techniques.


Once a victim’s bank details (like their credit or debit card information and account passwords) are in the hands of attackers, the information can be used to further exploit the consumer. Sometimes hackers use account information to make purchases, transfer money, or otherwise benefit financially from the scam.
In some instances, hackers will use the personal information they’ve gathered from the scam, like your email address, phone number, address, or even your name to send emails or phishing scams pretending to be you. Social engineering attacks, or attacks meant to target a victim’s emotions and sympathy, are more successful when they come from a believable source, so when a hacker has true access to your email, these phishing attacks become more feasible.
The rippling effect of these shipping and mail scams are more impactful than we think.
Abused Free Hosting Services
Threat actors always try to maximize their profit by leveraging various free hosting services. This type of infamous phishing campaign implies that threat actors are always trying to find out new freemium services (SaaS products) and abuse them to evade detection engines.
In this campaign, threat actors used a couple of freemium hosting services to host the phishing sites like:
alviy
alviy.com is a DNS service hosting provider which provides Dynamic DNS Service for completely free. Anyone can create an account with their email and get 3 free host names to set up their sites.

clever cloud
clever-cloud.com: This is a SaaS service that provides tools to host, deploy and maintain applications in operational conditions.
Anyone can host and run web applications using the free trial.
forumz & now dns
forumz.info & now-dns.com are two services that provide similar Dynamic DNS services where anyone can use hostnames based on the availability for mentioned domain names, shown in Fig.3.

What This Scam Means for Businesses Moving Forward
Threat actors are being proactive in terms of using various SaaS services to make their attacks more profitable, including using various freemium services. They are constantly employing various new tools and techniques, like AI-technology, social media phishing, brand impersonation scams, and more to steal or lure customers from profitable, data-rich industries, like financial services, healthcare, and government agencies.
This current USPS scam campaign, like so many major scam campaigns, has an impact on the legitimate business’s reputation, and can create loss of trust with consumers, employees, and partners. Especially during a busy holiday shopping season, the impact of this scam could mean business and consumer financial data and PII are compromised unknowingly, and maybe not identified until months down the road.
In such cases, it can be seen why taking proactive measures to identify similar pre-malicious domains and taking them down manually, or by using an automated takedown service to remove such malicious domains immediately after identification, is critical to protecting your brand reputation.
Bolster provides an expansive suite of threat detection and takedown tools to protect your business reputation from digital threats. With AI-powered internet monitoring, we will cover all fronts when it comes to scam protection, including fake sites spun up to replicate your brand.
For more information on how Bolster can work for your business, you can visit our website, or request a free demo today.
Appendix



*** This is a Security Bloggers Network syndicated blog from Blog – Bolster AI authored by Anshuman Das. Read the original post at: https://bolster.ai/blog/usps-phishing-campaign
如有侵权请联系:admin#unsafe.sh