
2023-12-1 22:0:0 Author: www.tenable.com(查看原文) 阅读量:7 收藏

Looking for guidance on developing AI systems that are safe and compliant? Check out new best practices from the U.S. and U.K. cyber agencies. Plus, a new survey shows generative AI adoption is booming, but security and privacy concerns remain. In addition, CISA is warning municipal water plants about an active threat involving Unitronics PLCs. And much more!
Dive into six things that are top of mind for the week ending December 1.
1 - U.S., U.K. publish recommendations for building secure AI systems
If you’re involved with creating artificial intelligence systems, how do you ensure they’re safe? That’s the core question that drove the U.S. and U.K. cybersecurity agencies to publish this week a joint document titled “Guidelines for Secure AI System Development.”
“We urge all stakeholders (including data scientists, developers, managers, decision-makers and risk owners) to read these guidelines to help them make informed decisions about the design, development, deployment and operation of their AI systems,” reads the guide.
The 20-page document, jointly issued by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Department of Homeland Security (DHS) and the U.K. National Cyber Security Centre (NCSC), focuses on four core areas:
- Secure design, including risk awareness and threat modeling
- Secure development, including supply chain security, documentation and technical debt management
- Secure deployment, including compromise prevention of infrastructure and AI models
- Secure operation and maintenance, such as logging and monitoring, and update management
To get more details, check out:
- The joint announcement “DHS CISA and UK NCSC Release Joint Guidelines for Secure AI System Development”
- The full document “Guidelines for Secure AI System Development”
For more information about secure AI development:
- “Building AI-Enabled Applications: Best Practices for Developers” (CodeMotion)
- “OWASP AI Security and Privacy Guide” (OWASP)
- “How to manage generative AI security risks in the enterprise” (TechTarget)
- “Security threats of AI large language models are mounting, spurring efforts to fix them (Silicon Angle)
- “Data management best practices key to generative AI success” (TechTarget)
VIDEOS
Inside the Race to Build Safe AI (Bloomberg)
Stanford Webinar - Building Safe and Reliable Autonomous Systems (Stanford University)
2 - Survey: Orgs embrace GenAI, as security and privacy worries loom
Enterprises are rushing to adopt generative AI with unprecedented speed, while assessing risks including security vulnerabilities, privacy concerns, and safety and reliability issues.
That’s according to the “Generative AI in the Enterprise” report from tech publishing and training company O’Reilly, which polled more than 2,800 technology professionals primarily from North America, Europe and Asia-Pacific who use the company’s learning platform.
“The adoption of generative AI is certainly explosive, but if we ignore the risks and hazards of hasty adoption, it is certainly possible we can slide into another AI winter,” Mike Loukides, O’Reilly VP of content strategy and the report’s author, said in a statement.
When asked what risks they’re testing generative AI for, respondents ranked these as the top five:
- Unexpected outcomes (49%)
- Security vulnerabilities (48%)
- Safety and reliability (46%)
- Fairness, bias, and ethics (46%)
- Privacy (46%)
Other findings include:
- A whopping 67% of respondents said their organizations are already using generative AI
- The most common usage of generative AI is for programming (77%), followed by data analysis (70%) and customer-facing apps (65%)
- Generative AI adoption is creating a need for AI programmers, data analysts and AI/machine learning operators
- The top constraint impeding implementation of generative AI is the inability to identify appropriate use cases, cited by 53% of respondents
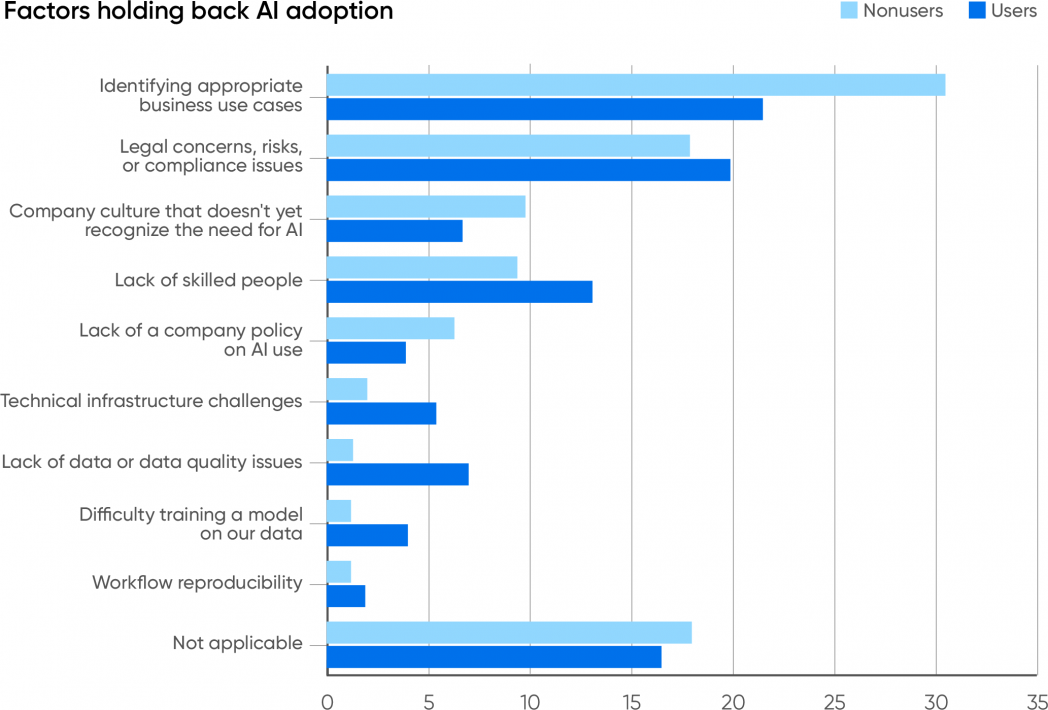
(Source: O’Reilly’s “Generative AI in the Enterprise” report, November 2023)
To get more details:
- Download the report “Generative AI in the Enterprise”
- Check out the report’s announcement “O’Reilly Releases 2023 Generative AI in the Enterprise Report”
- Read the article “Generative AI in the Enterprise”
3 - CISA to water authorities: Beware of Unitronics PLC exploit
Unitronics programmable logic controllers (PLCs) used by water and wastewater operators are being actively breached by hackers, CISA warned this week, while outlining mitigation steps that water authorities should take immediately.
In its alert “Exploitation of Unitronics PLCs used in Water and Wastewater Systems,” CISA mentioned an incident at a U.S. water plant tied to this exploit that prompted the facility to take the affected system offline. There is no known risk to the unidentified municipality’s drinking water.

CISA recommendations include:
- Change the Unitronics PLC default password
- Require multi-factor authentication for all remote access to the OT network
- Unplug the PLC from the open internet, and should remote access be necessary, control it using a firewall and virtual private network (VPN)
- Use a different port from TCP 20256, which attackers are actively targeting
To get more details, read the alert “Exploitation of Unitronics PLCs used in Water and Wastewater Systems” and check out CISA’s “Water and Wastewater Cybersecurity” page.
For more coverage about this alert:
- “CISA warns of attacks on Unitronics tool used by water utilities, wastewater systems” (The Record)
- “Hackers breach US water facility via exposed Unitronics PLCs” (BleepingComputer)
- “Pennsylvania water facility hit by Iran-linked hackers” (CyberScoop)
- “Federal government investigating multiple hacks of US water utilities” (Politico)
4 - A prioritization plan for new CISOs
After CISOs start a new job, especially if it’s their first time as the cybersecurity chief, it’s critical that they clearly delineate their most important priorities. A new checklist from IANS Research published this week aims to help.

The “New CISO Priority Checklist: Ensure a Fast, Successful Start” document outlines priorities for the first 30 days on the job; the first six months; and the first year. Here’s a sampling of entries.
For the first 30 days:
- Review security policies, standards and procedures, making sure they’re clear, current and comprehensive
- Verify that a risk register exists, and that it contains the most significant risks; that it has executive buy-in; and that risk ownership and accountability are clear
- Define and document the information that needs protection
For the first 60 days:
- Establish key performance indicators and metrics, and make sure they reflect risks and mitigation measures
- Assess third-party risk management capabilities
- Review the organization’s security incidents, as well as security audit findings
For the first year:
- Identify and address the main organizational complaints about the security team
- Enhance relationships with other departments, such as human resources and finance, and ensure you have continuous communication with them
- Review the software development lifecycle, and ensure security is part of the process from the early stages
View the full checklist here.
VIDEOS
Do You Really Want to Be a CISO? Spencer Mott, Booking.com CISO (Security Weekly)
Becoming a CISO: Leading Transformation (SANS Institute)
5 - CISA to vendors: Boost security of your web management interfaces
Software vendors should make their web management interfaces secure by design, instead of putting the onus on their customers. So says CISA in its new “Secure by Design Alert: How Software Manufacturers Can Shield Web Management Interfaces from Malicious Cyber Activity” document.

CISA’s recommendations for software vendors include:
- Disable your products’ web interfaces by default, and list the risks involved when loosening this default configuration
- Consistently enforce authentication throughout your products, especially on administrator portal interfaces
- Be radically transparent and accountable regarding your products’ vulnerabilities
To get more details, read the 2-page guide.
For more information about vulnerabilities in software management interfaces:
- “CVE-2023-20198: Zero-Day Vulnerability in Cisco IOS XE Exploited in the Wild” (Tenable)
- “Juniper web management interface open to RCE” (IT News)
- “CVE-2023-38035: Ivanti Sentry API Authentication Bypass Zero-Day Exploited in the Wild” (Tenable)
- “Serious Vulnerability Exposes Admin Interface of Arcserve UDP Backup Solution” (Security Week)
- “Using the Service Location Protocol (SLP) to Find Exposed Management Interfaces” (Tenable)
6 - California to regulate AI systems
If your organization is using AI for business operations, here’s yet another AI regulation to keep tabs on.
This week, the California Privacy Protection Agency published a draft of proposed rules governing “automated decision-making technology” (ADMT) systems, including those that use AI.
The draft regulations define new protections related to businesses’ use of ADMT, including customers’ rights to opt out of these systems and to access information about how businesses are using them. The draft rules would also require businesses to inform consumers via “pre-use notices” how they intend to use ADMT.
The California Privacy Protection Agency’s board will offer feedback on the draft regulations in December. The agency expects to begin “formal rulemaking” in 2024.
To get more details, check out:
- The agency’s announcement of the draft rules
- The 17-page draft document
For more information about AI regulation:
- “AI regulation remains unclear one year after ChatGPT launch” (Yahoo Finance)
- “EU lawmakers pass landmark artificial intelligence regulation” (CNBC)
- “AI Regulation is Coming: What is the Likely Outcome?” (Center for Strategic & International Studies)
- “The three challenges of AI regulation” (The Brookings Institution)
- “Artificial Intelligence 2023 Legislation” (National Conference of State Legislatures)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Internet of Things
- Risk-based Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Formerly Tenable.io
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Formerly Tenable.io Web Application Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Formerly Tenable.sc
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Formerly Tenable.ot
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Formerly Tenable.ad
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Formerly Tenable.asm
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Try Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh